Tech tools
Engineering | 1 min read
New Expel Workbench integrations: defend against identity threatsOur latest Integrations with 1Password, Snowflake, Auth0, and Crowdstrike Falcon Identity Protection help protect against identity threats.
Expel insider | 1 min read
Meet us at Infosec 2023Infosecurity 2023 is around the corner and we’re thrilled to be making our debut on the showfloor. Connect with Expel at Stand G90!
Security operations | 2 min read
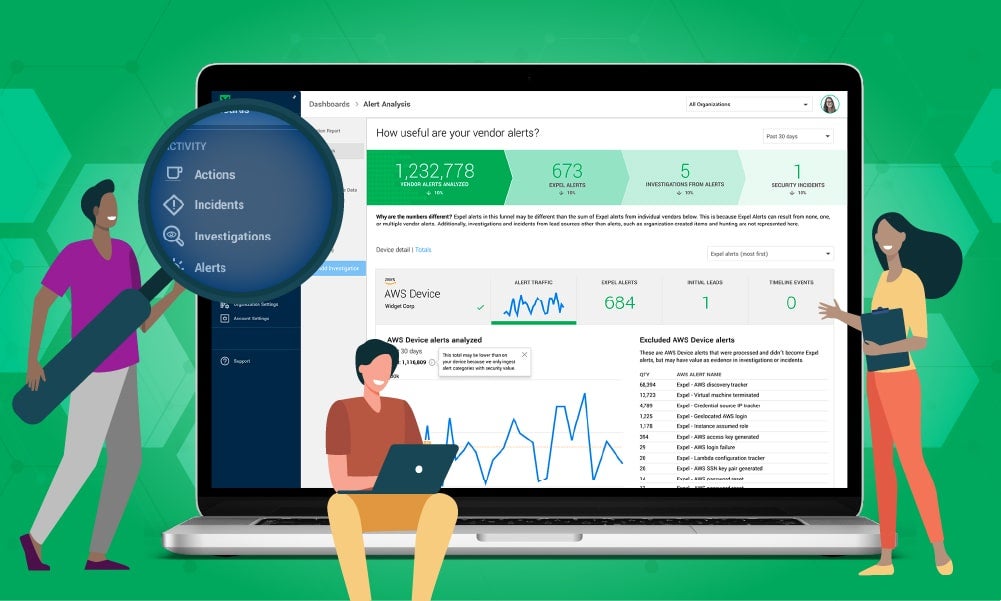
Add context to supercharge your security decisions in Expel WorkbenchDefenders need so much information to make good security decisions in the SOC. Adding Context to Expel Workbench is one way to make faster and better decisions.
Expel insider | 3 min read
We’re definitely stronger together: top 3 takeaways from RSA Conference 2023Another RSA Conference is in the books. Take a look at what jumped out to us most from the event, and how we as defenders are all “Stronger Together.”
Expel insider | 1 min read
#RSAC round 2: Expel heads back to MosconeExpel is headed back to RSA Conference as an exhibitor for the second time. Stop by our booth to meet the crew, snag some swag, and let us show you security that makes sense.
Engineering | 8 min read
Instrumenting the “big three” managed Kubernetes offerings with PythonWhat’s the best way to securely access the Kubernetes API for managed offerings like GKE, EKS, and AKS? Each has its own middleware, best practices, and hurdles to clear. In this post, we’ll give you the tools you need to do it yourself.
Security operations | 4 min read
An easier way to navigate our security operations platform, Expel WorkbenchOur security operations platform, Expel Workbench, got a makeover to make it easier for defenders to get what they need to protect their orgs even more quickly and intuitively.
Engineering | 3 min read
Integrations roundup: new integrations to manage overall business riskExpel has always used a bring-your-own-tech approach to security operations. Now our integrations are expanding beyond the sphere of cybersecurity and into some of today’s most popular business apps.
Security operations | 2 min read
How we spotted it: A Silicon Valley Bank phishing attemptWe’re starting to spot counterparty fraud attempts in the wake of SVB’s collapse. Learn how we spotted one attempt through a custom detection.
Engineering | 1 min read
So long, 2022! Our year in reviewTo mark the end of 2022 and the beginning of 2023, we’ve curated some of our favorite blog posts from the past 12 months.
Engineering | 5 min read
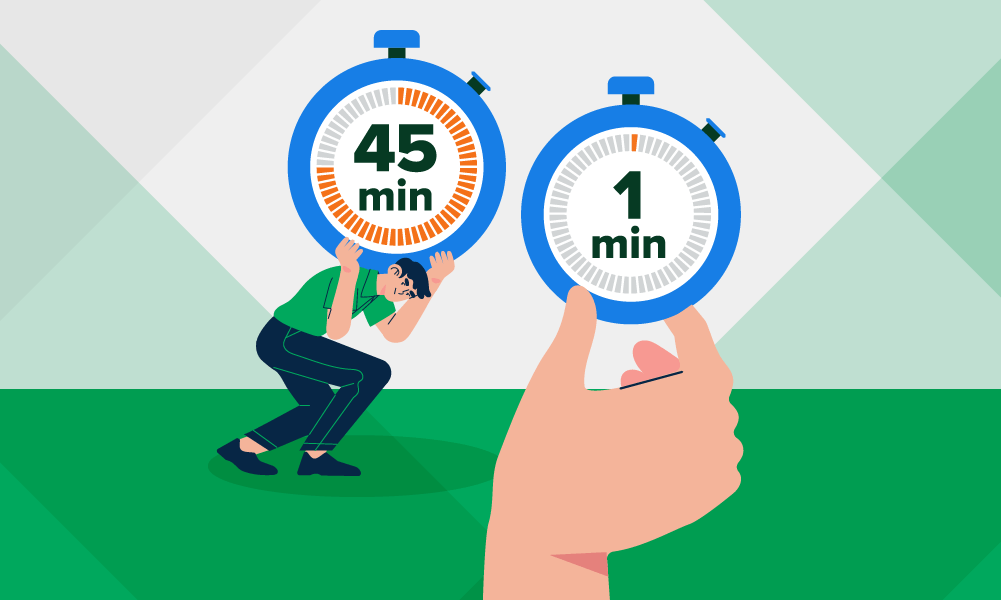
45 minutes to one minute: how we shrunk image deployment timeWe recently figured out how to reduce Kubernetes image deployment time from 45 minutes (way too long) to one minute (really fast). Here’s how we did it.
Expel insider | 3 min read
Touring the modern SOC: where are the dials and blinking lights?SOC tours at Expel aren’t about showing off blinking lights and racks of equipment. Instead it's a discussion about mission, mindset, operations management, results, and demos that make our SOC “go”
Security operations | 3 min read
Expel Quarterly Threat Report Q3: Top 5 takeawaysOur third quarterly (Q3) threat report is here and it’s overflowing with cybersecurity data, trends, and recommendations to help you protect your organization. Here are our top five takeaways from Q3.
Engineering | 3 min read
Connect Hashicorp Vault and Google’s CloudSQL databases: new plugin!Expel is excited to open source a new Hashicorp Vault plugin that brokers database credentials between Hashicorp Vault and Google’s CloudSQL DBs.
Security operations | 7 min read
How we built it: Alert SimilarityOur Alert Similarity tool lets us teach our bots to compare similar “documents” and suggest or recommend a next step, freeing up our analysts. Here’s a walk-through of how we developed it.
Security operations | 3 min read
Top 5 takeaways: Expel Quarterly Threat Report Q2Our second quarterly (Q2) threat report is here and its chock full of cybersecurity data, trends, and recommendations to help you protect your organization. Here are our top five takeaways from Q2.
Security operations | 4 min read
How Expel’s Alert Similarity feature helps our customersWe process millions of alerts each day, and many look similar to one another. We asked ourselves: is it possible to teach our bots to compare similar “documents” and suggest or recommend a next step? (Spoiler alert: YES!)
Security operations | 2 min read
Cutting Through the Noise: RIOT Enrichment Drives SOC ClarityCutting Through the Noise: RIOT Enrichment Drives SOC Clarity
Security operations | 5 min read
Detecting Coin Miners with Palo Alto Networks NGFWWith cryptojacking on the rise, we walk through why we’ve found Palo Alto Networks next-generation firewall is great at detecting it, and some actions we’ve integrated into our detection bot to help.
Expel insider | 3 min read
Top 3 takeaways from RSA Conference 2022It was four days of excitement as we made our exhibitor debut at #RSAC. Now that we’ve had time to reflect on this year’s conference, here are three of the big takeaways from our time at Moscone.
Expel insider | 3 min read
RSA Conference Day 3: Impressions From the Show FloorDay three of the conference was full of interesting conversations with long-time industry folks who are no stranger to RSA. Here are some of our favorite takeaways and observations.
Expel insider | 2 min read
RSA Conference Day 2: Inclusivity is the GoalAnother day at RSA full of interesting speakers, lessons learned, and (of course) cool swag — but one session stood out to us the most. Here are some of our main takeaways from day two.
Expel insider | 3 min read
RSA Conference Returns: Day 1 Keynote SummaryThat’s a wrap on day one of #RSAC and we’re still reeling from excitement. From beatboxers to keynote speakers, here are some of our takeaways from the first day at Moscone.
Threat intelligence | 3 min read
Expel Quarterly Threat Report: Cybersecurity data, trends, and recs from Q1 2022Top takeaways from our first quarterly report, filled with patterns and trends we identified from Q1 2022. Our goal? Help translate the events we detect into a security strategy for your organization.
Expel insider | 2 min read
Meet us at Moscone… Expel makes its #RSAC debut!For the first time, Expel is headed to RSA Conference as an exhibitor! Stop by our booth to meet the crew, snag some swag, meet Josie and Ruxie, and let us show you that security can be delightful.
Security operations | 5 min read
Attack trend alert: Email scams targeting donations to UkraineAs more people look to donate to Ukrainian relief efforts, bad actors are taking advantage. Lookout for these phishing scams to ensure your donations are actually going to help those in need.
Tips | 5 min read
Helpful tools for technical teams to collaborate without meetingsLooking to reduce the meeting load on your technical teams while maintaining effective communication and collaboration? Learn the tools and tips that our CTO uses to improve his team’s “meeting mojo.”
Security operations | 5 min read
Evaluating MDR providers? Ask these questions about their onboarding processLooking for an MDR provider? Make sure you understand their onboarding process. Here are the questions you should ask when you’re evaluating MDRs. Bonus: learn how we do onboarding here at Expel.
Tips | 3 min read
5 pro tips for detecting in AWSCloud-based infrastructures can be confusing, but sometimes building a better security program starts with the basics. Try these pro tips to help focus the lens for detecting threats in AWS.
Security operations | 4 min read
Attack trend alert: AWS-themed credential phishing techniqueThey’re at it again. This time attackers are phishing for credentials by sending fake AWS log-in pages to unsuspecting users. Find out how our crew identified and triaged a phishing email.
Engineering | 5 min read
Threat hunting: Build or buy?Not sure if you should build your own hunting capability or get a hunting partner? Check out this post to discover your options and the things you should consider (yes, we break down cost for you).
Security operations | 4 min read
How we use VMRay to support Expel for PhishingHow does Expel tackle phishing? Smart people and great tech. Learn how VMRay helps our analysts triage and analyze potentially malicious emails submitted by our managed phishing service customers.
Security operations | 6 min read
Swimming past 2FA, part 2: How to investigate Okta compromiseFirst we showed you how to spot an Okta compromise in this two-part blog series. Now we’ll walk you through our investigation and share five tips on how you can strengthen your security defense.
Security operations | 6 min read
How Expel goes detection sprinting in Google CloudBuilding detections in Google Cloud Platform (GCP) but not sure where to start? Time to get strategic. Our detection and response engineers demystify the process for building detections in the cloud.
Security operations | 9 min read
Well that escalated quickly: How a red team went from domain user to kernel memoryA red team recently swooped in and showed off some new tactics. What started as a PowerShell download cradle quickly turned into a custom rootkit download. Find out how we spotted the crafty red team.
Security operations | 7 min read
Come sea how we tackle phishing: Expel’s Phishing dashboardWant a tour of Expel’s Phishing dashboard? Get a behind-the-scenes look at how one of our senior UX designers developed the Phishing dashboard for Expel’s managed phishing service customers.
Security operations | 4 min read
Someone in your industry got hit with ransomware. What now?We’re noticing a trend in ransomware attacks. But that doesn’t mean it’s time to go into panic mode. Find out what you need to know and get some tips on how you can keep your org safe.
Security operations | 8 min read
How to measure SOC qualityYou can scale your SOC and improve quality. Seems impossible? Not if you know how and what to measure. The crew that helped build Expel’s SOC explain how they pulled it off – and how you can too.
Security operations | 7 min read
Cloud attack trends: What you need to know and how to stay resilientWe shared the top attack trend spotted during the pandemic and what to keep an eye out for looking ahead. But how do you remediate and stay resilient against these attacks? Our crew shares some tips.
Security operations | 6 min read
Performance metrics, part 3: Success storiesOur team shares some success stories in creating efficiency and reducing analyst burnout. They end this three-part series with a gift from our SOC – a downloadable resource to measure performance.
Security operations | 3 min read
Expel Hunting: Now in the cloudWe’ve added something new to Expel Hunting: cloud hunts. Find out how our crew’s newly developed hunting techniques can help you spot visibility gaps in your cloud (and give you some peace of mind).
Engineering | 11 min read
Migrating to GKE: Preemptible nodes and making space for the Chaos MonkeysFind out how Expel’s internal teams collaborated to migrate our core infrastructure from a legacy environment to GCP, with no downtime (while also making sure they were prepared for a little chaos).
Engineering | 6 min read
5 best practices to get to production readiness with Hashicorp Vault in KubernetesFlying blind when it comes to running Hashicorp Vault in Kubernetes? We’ve got you covered. Accelerate your path to production without compromising on security with these tips and best practices.
Engineering | 8 min read
Containerizing key pipeline with zero downtimeMigrating to Kubernetes as Expel’s core engineering platform with zero downtime – and without interfering with our analysts’ workflow – is a tall order. But our engineers pulled it off. Find out how.
Engineering | 12 min read
Behind the scenes: Building Azure integrations for ASC alertsFind out how Expel’s internal teams built an integration on top of Azure signal – creating a new detection strategy for ASC that provides more context around alerts and improves customer visibility.
Expel insider | 2 min read
Introducing Expel Workbench™ for Amazon Web Services (AWS)We’re excited to announce the launch of our first SaaS product! It automates the investigation of AWS alerts and logs – allowing your team to spend less time finding and fixing security issues.
Security operations | 1 min read
Got workloads in Microsoft Azure? Read thisGot Microsoft Azure? Running Microsoft products in your org? Then you might want to get a free copy of our all-new Azure guidebook.
Engineering | 7 min read
Plotting booby traps like in Home Alone: Our approach to detection writingFind out how Expel’s D&R engineers think about detection writing, and how this process helps our SOC analysts make smart decisions and gain a deeper understanding of our customers’ environments.
Threat intelligence | 6 min read
Supply chain attack prevention: 3 things to do nowWhat do you do when you can’t trust the internet? Supply chain attacks like the SolarWinds Orion breach are not new. Here are some things you can do to help prepare and guard against similar attacks.
Security operations | 7 min read
Enhancing phishing protection: analyst & customer securityDiscover how Expel's robust phishing protection measures safeguard our analysts and customers against email threats, providing utmost security and peace of mind.
Security operations | 3 min read
The SolarWinds Orion breach: 6 ideas on what to do next and whyHere are some of our early observations on the SolarWinds Orion breach, plus our ideas on what to do next to detect related activity and better protect your org.
Security operations | 8 min read
How to investigate like an Expel analyst: The Expel Workbench managed alert processEver wonder about how Expel’s analysts investigate alerts? Our SOC team created a workflow called the Expel Workbench managed alert process. Read on to find out how it works and how it can help you.
Security operations | 4 min read
The CISO in 2020 (and beyond): A chat with Bruce PotterIt’s impossible to sum up a year that felt like 1000 in a single blog post. But we did gather some topline takeaways on security trends and the evolving role of the CISO from Expel’s Bruce Potter.
Engineering | 2 min read
Announcing Open Source python client (pyexclient) for Expel WorkbenchWe’re open sourcing a python client in the Expel Workbench! This labor of love will allow our customers to take advantage of our APIs. Find out what the release of the pyexclient project includes.
Security operations | 9 min read
Performance metrics, part 2: Keeping things under controlIn this second post in our three-part series on all things metrics and SOC leadership, our team dives into details of what metrics and techniques are used to protect the SOC against volatility.
Security operations | 8 min read
Why don’t you integrate with [foo]?You’ve heard that Expel integrates with your tech. But not YOUR tech. What gives? Well, sometimes it doesn’t always make sense. Expel’s COO explains why and what this means when working with us.
Tips | 9 min read
3 steps to figuring out where a SIEM belongs in your security programHow can a SIEM help you address your business needs? Do you even need a SIEM? Here are some tips to help you make a decision that works best for you.