Security operations · 2 MIN READ · EVAN REICHARD AND IAN COOPER · JUL 15, 2022 · TAGS: MDR / Tech tools
Flash back to your days in the SOC. An alert shows up and your investigative habits kick in (OSCAR, anyone?). It takes a few minutes, but you eventually determine that this alert is benign network traffic and not, in fact, command and control (c2) traffic to attacker-controlled infrastructure. Can you remember what information you used to reach that conclusion? (Of course not, but maybe remembering a particular third-party open source intelligence (OSINT) tool or query is enough to generate a sense of nostalgia for you.)
At Expel, we arm our analysts with the best OSINT available to quickly and accurately spot benign or false positive alerts. This creates space to tackle suspicious activity head-on.
More signal. Less noise.
Enter the Greynoise RIOT (Rule It Out) API.
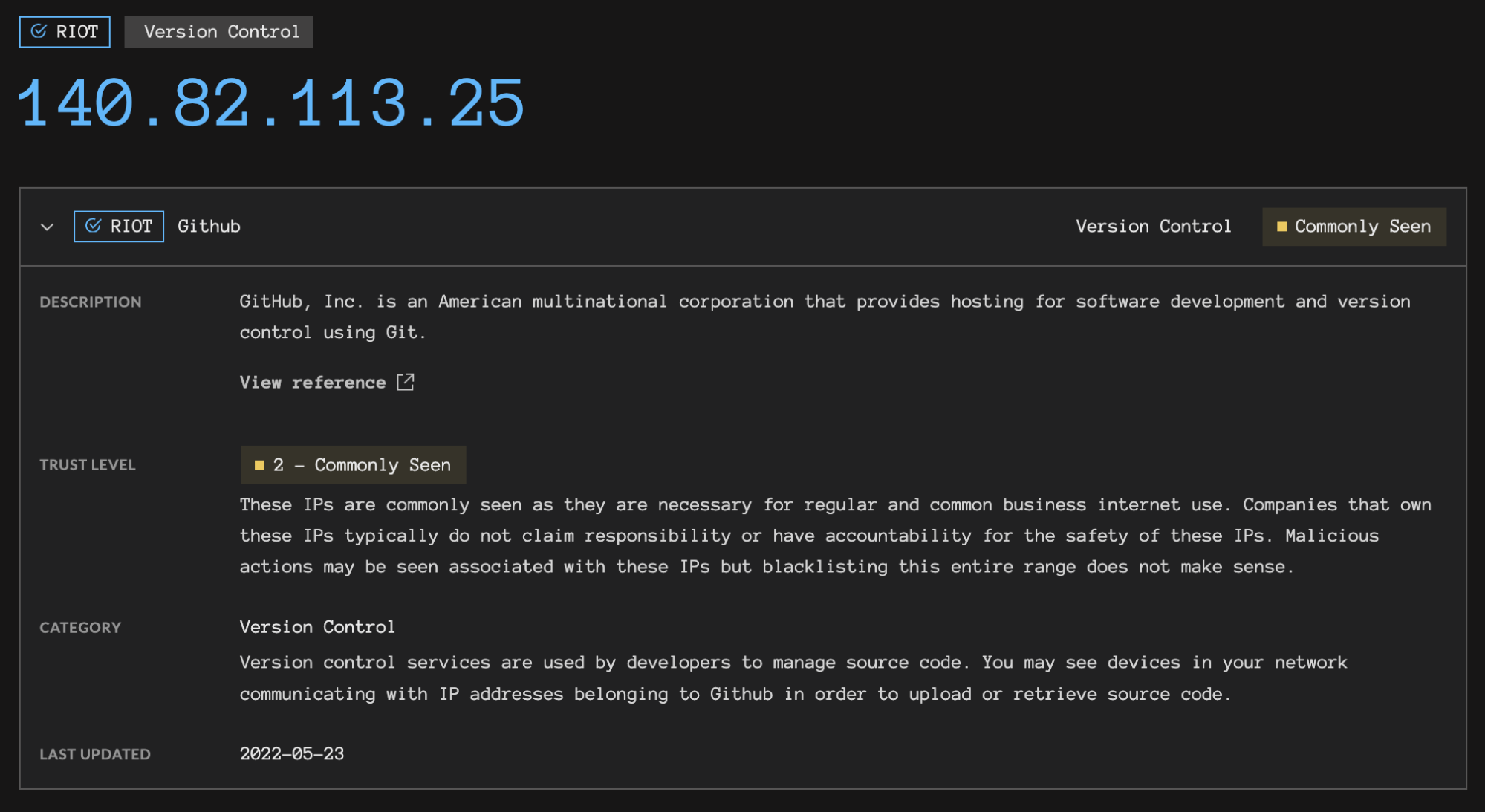
To paraphrase the Greynoise team, RIOT adds context to IPs observed in network traffic between common business applications like Microsoft Office 365, Google Workspace, and Slack or services like CDNs (content delivery networks) and public DNS (domain name system) servers. These business applications often use unpublished or dynamic IPs, making it difficult for security teams to keep track of expected IP ranges. Without context, this benign network traffic can distract the SOC from investigating higher priority security signals.
We use the RIOT API, plus several other enrichment sources, to help our analysts quickly recognize IPs associated with business services and dispatch network security alerts that don’t require further investigation. Ruxie™, our ever-inquisitive security bot, uses these APIs to collect enrichment information and parse the results for human consumption.
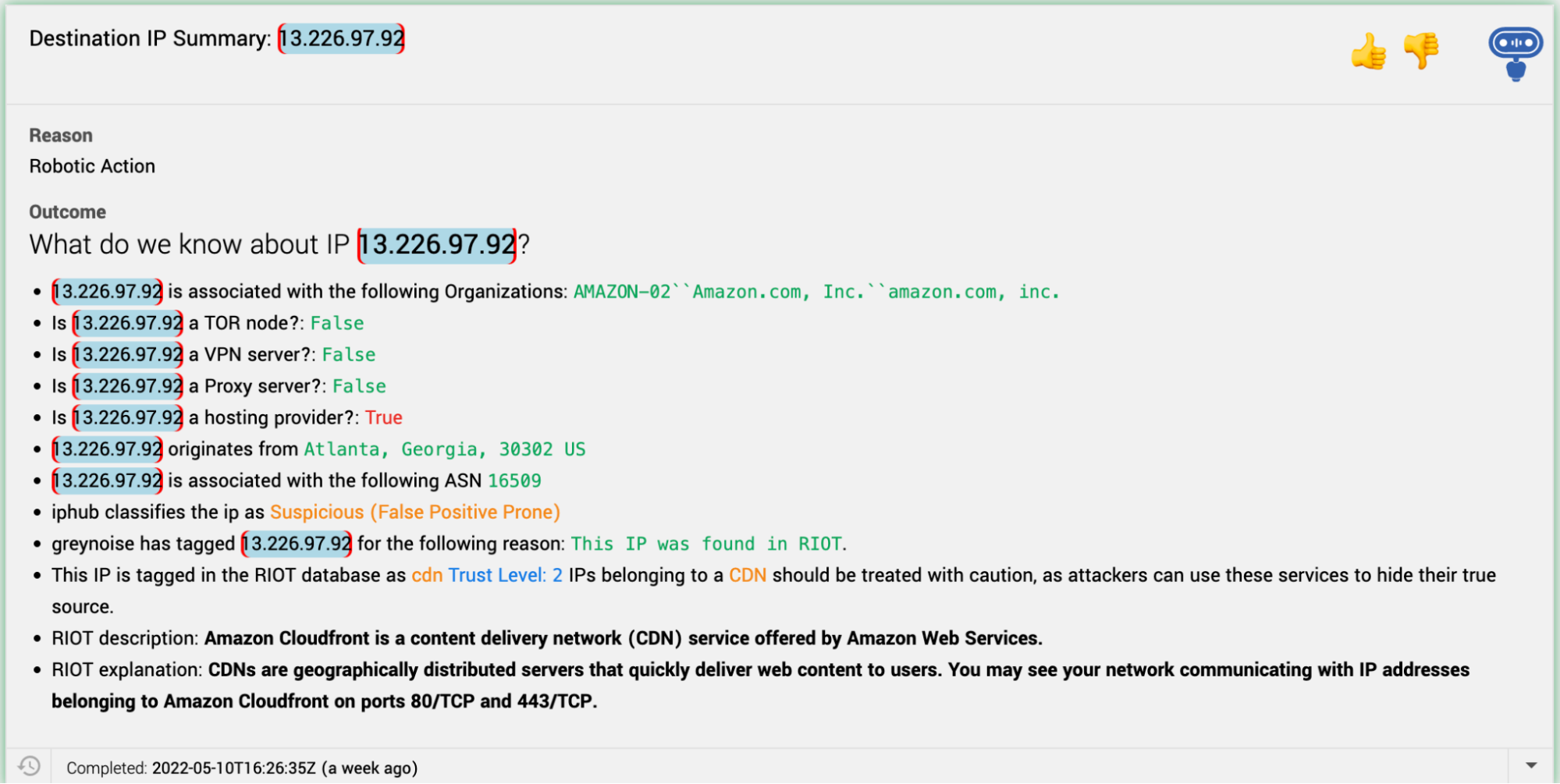
RIOT info guides analysts as they orient themselves with alerts. A color-coded enrichment workflow helps them identify noteworthy details. For example, RIOT recognizes the above IP as trust level 2, but it’s classified as a CDN. Attackers can use a CDN to obfuscate their true source via domain fronting. IPs tagged as trust level 1 are more likely to be associated with an IP that’s managed by a business or service, rather than a CDN.
CSI: Cyber – “All I got is green code”
Ruxie also enriches other pieces of network evidence, like domains. Analysts can immediately see the date a domain was registered: a recently registered domain should be treated with additional scrutiny since they’re often associated with recently built attacker infrastructure. Malicious domains tend to be promptly taken down, forcing attackers to start over from scratch. More advanced attackers are known to buy and hold useful domain names for extended periods prior to an attack.
RIOT arms our analysts with a simple, colorized tool for surfacing enrichment details so the SOC can quickly spot and dispatch non-threat activity. This means that when Josie™ (our detection engine) and Ruxie (our orchestration bot) have decided an alert is worthy of review, the SOC can get to work on a triage knowing they’re not wasting their time.






