Keep your tools (and your sanity).
An MDR built for you.
For operators by operators. Human-led, AI-supported,
and built to work with your environment and team.
Trusted by top performing security teams












RECOGNIZED BY INDUSTRY EXPERTS
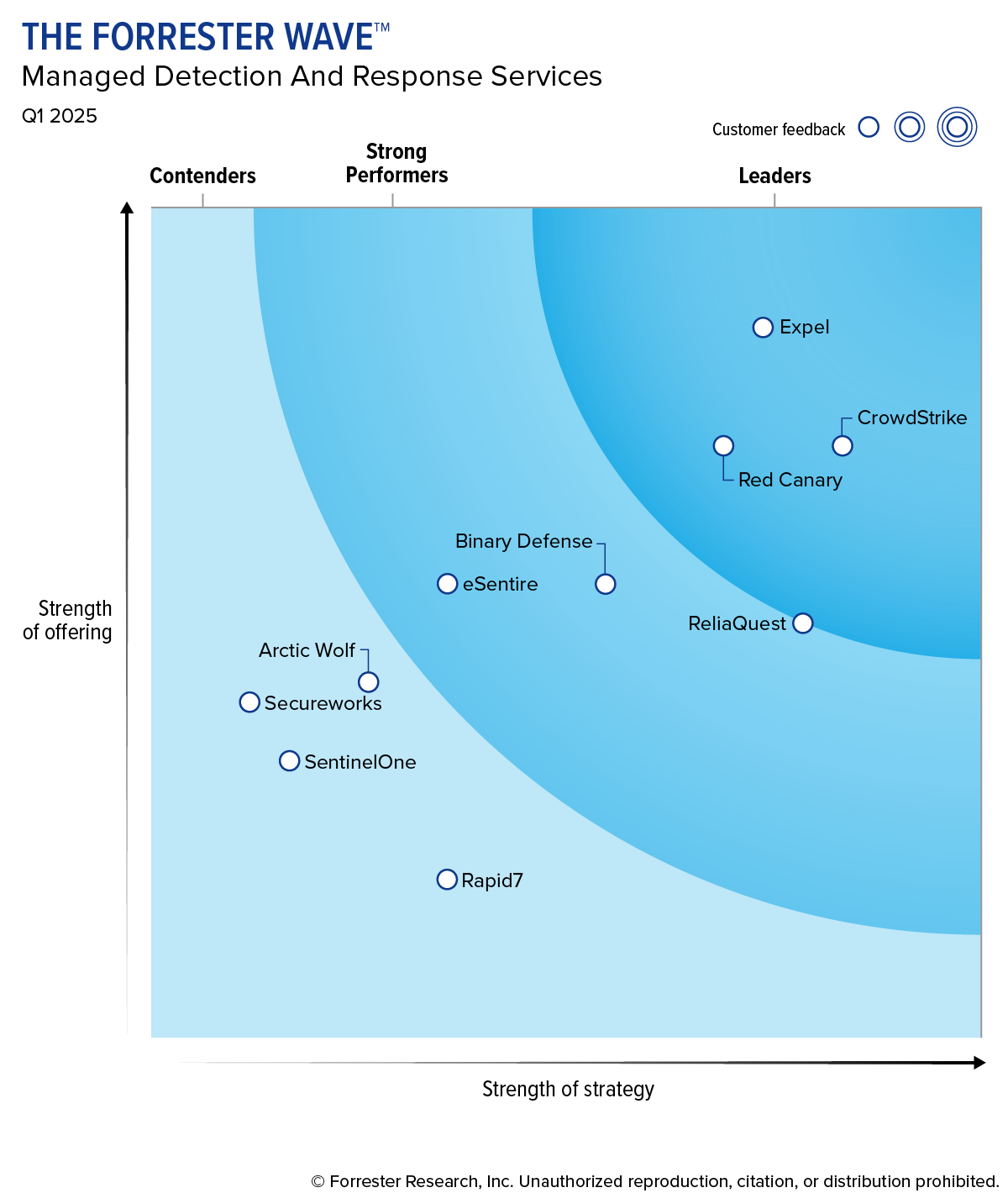
Leader. Rinse. Repeat.
Expel is a Leader in the Forrester Wave™ MDR Services, Q1 2025. Achieved 5/5 in 15 of 21 criteria, including detection surface: cloud, detection surface: identity, dashboards and reporting, metrics, roadmap, and more.1
WE GET YOU
Cyber strain wasn’t in
the job description.
You’re chasing endless alerts, hunting threats, tuning tools (that promised to tune themselves), and fighting against your MDR vendor.
WE’VE BEEN THERE
So we built the MDR we always wanted.
No agents to deploy. No forced tool swaps. Just experienced SOC analysts doing detection and response in your environment—whatever you’re running.

Humans + AI
We believe that AI makes SOC analysts better, not obsolete.
Fast & flexible
We believe in complete coverage using tools you already have.
Expertise & partnership
We believe the best security requires partnership, not transactions.

Transparency
We believe transparency means direct SOC access, not sanitized updates.
REVIEWS ARE IN
99% of customers agree Expel
is a vendor they trust.
Trust isn’t built through sales decks. It’s earned by doing the work and not disappearing after the contract is signed.

90%
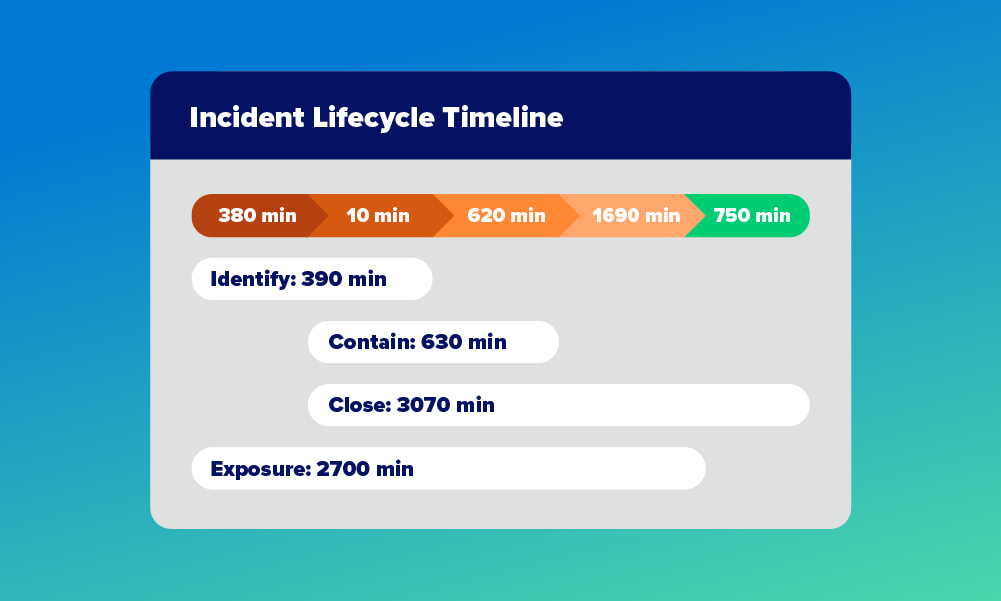
Time savings containing incident and improved MTTR by 64%
“Having Expel allowed us to beat our mean time to remediate (MTTR) by more than 60%. And more importantly, since Expel has eyes on alerts, our team had the flexibility to get out the alert queue and focus on maturing our security capabilities.”

$180K
Saved in security FTE costs per year
“Without Expel, we’d probably need another two or three people on the team. By keeping our team small, we can be better stewards of our donations.”
50%
Fewer investigations
“Our engineers manage 50% fewer investigations than they previously handled, allowing them to focus on higher-value work.”

$1M+
Saved annually
“Numerous alerts are seen as a benefit, but those alerts come with a lot of false positives. With Expel MDR, we could reduce the alert noise and focus on those alerts that would reduce our risk and improve our security posture.”
1 Forrester does not endorse any company, product, brand, or service included in its research publications and does not advise any person to select the products or services of any company or brand based on the ratings included in such publications. Information is based on the best available resources. Opinions reflect judgment at the time and are subject to change. For more information, read about Forrester’s objectivity here .