Security operations · 5 MIN READ · HIRANYA MIR, JOSE TALENO AND SIMON WONG · MAR 24, 2022 · TAGS: MDR / Tech tools
As the Russian invasion of Ukraine continues, many people around the world are looking for opportunities to donate to Ukrainian relief efforts. For scammers, this presents an opportunity to prey on people’s well-intentioned desire to help.
Recently, we’ve seen an increase in phishing emails masquerading as Ukrainian cryptocurrency and charitable apparel organizations. In this post, we’ll show you what these emails look like and how to spot the tell-tale warning signs to ensure your donations are going to help those in need.
It’s both unsurprising and horrible that there are people out there trying to take advantage of the situation. We are not discouraging anyone from donating but, since there are bad actors at play, we do encourage people to verify their donations are going to a legitimate place to help those in need.
Crypto scam emails
If you’re thinking about donating cryptocurrency to help victims in Ukraine, it’s important to be aware of potential scam techniques before you hit “send.” Especially if you’re prompted to donate via email solicitation, rather than seeking out a public wallet address associated with donation efforts.
If you receive an email claiming to represent a charitable organization accepting crypto donations, there are some key clues to indicate whether it’s genuine or not.
The email below is a recent example of a crypto scam email:
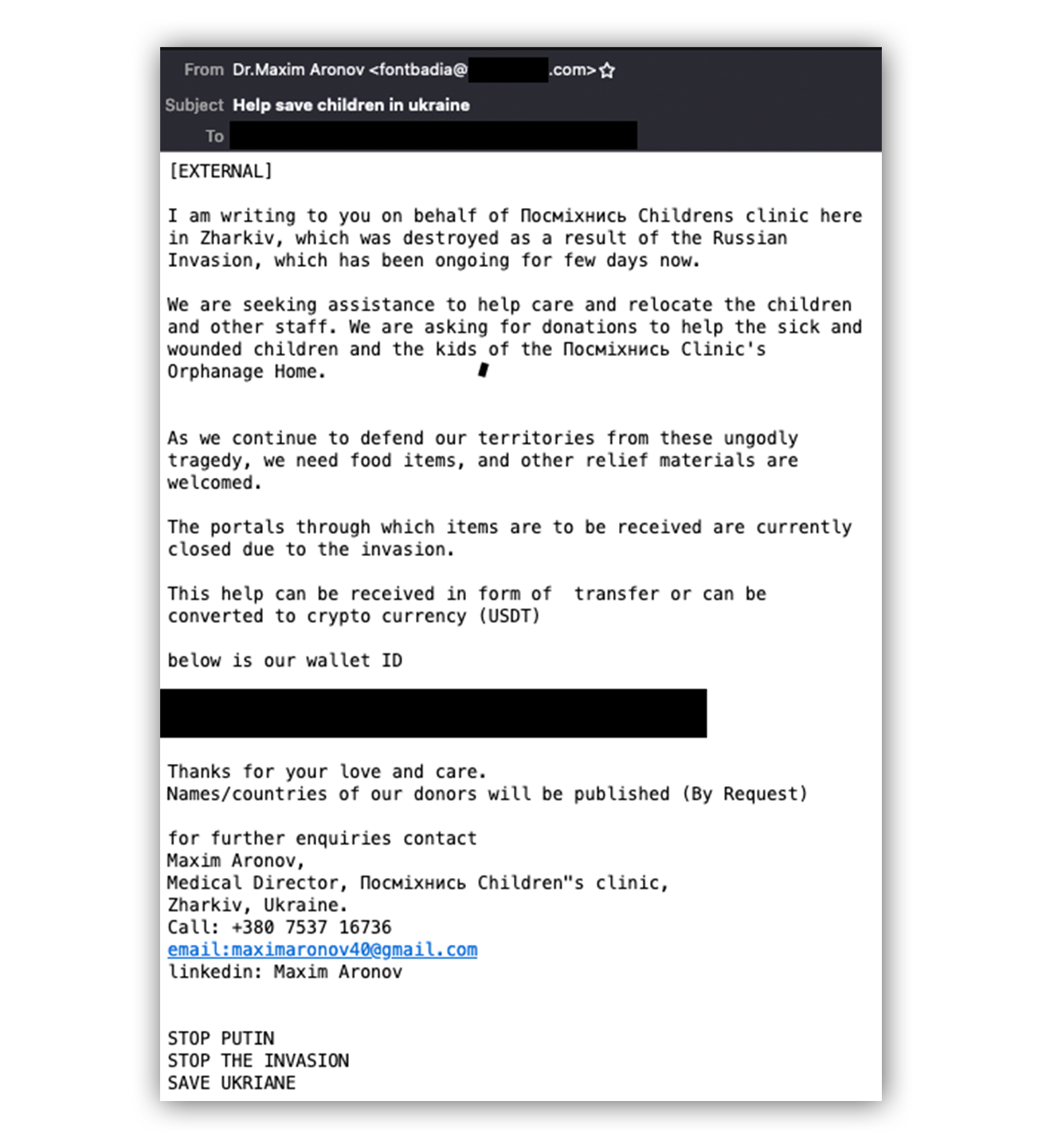
Our first clue that things are amiss? The name and address listed in the “From” field.
Let’s zoom in a bit more…
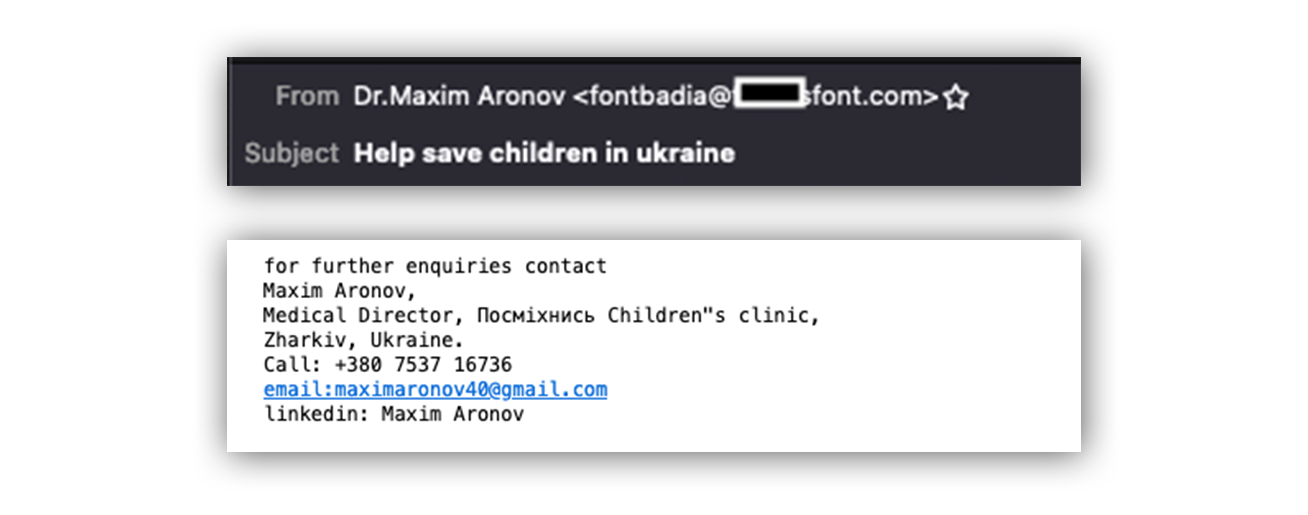
The doctor’s name listed on the “From” field (Dr.Maxim Aronov), doesn’t match the email address listed on the “From” field (fontbadia@). Also, the email address provided in the signature field, maximaronov40@gmail[d]com, isn’t associated with the children’s clinic.
If we look up the email reputation for maximaronov40@gmail[d]com we can see that this address isn’t linked to any social media profiles on major services like Facebook, LinkedIn, and iCloud. While this could also mean this is a new email address, it’s also suspicious.
Next, let’s inspect the public wallet address listed in the email body. (We’ve hidden the wallet address but for anyone wondering, it was an Ethereum public address.)
Crypto transactions are stored on the blockchain — leaving us a nice digital footprint of transaction activity associated with a public wallet address. You can review the transaction history of a public address using block chain explorer sites like blockchain.com and Polkascan.
Below is the transaction history of the public wallet address listed in the email body:
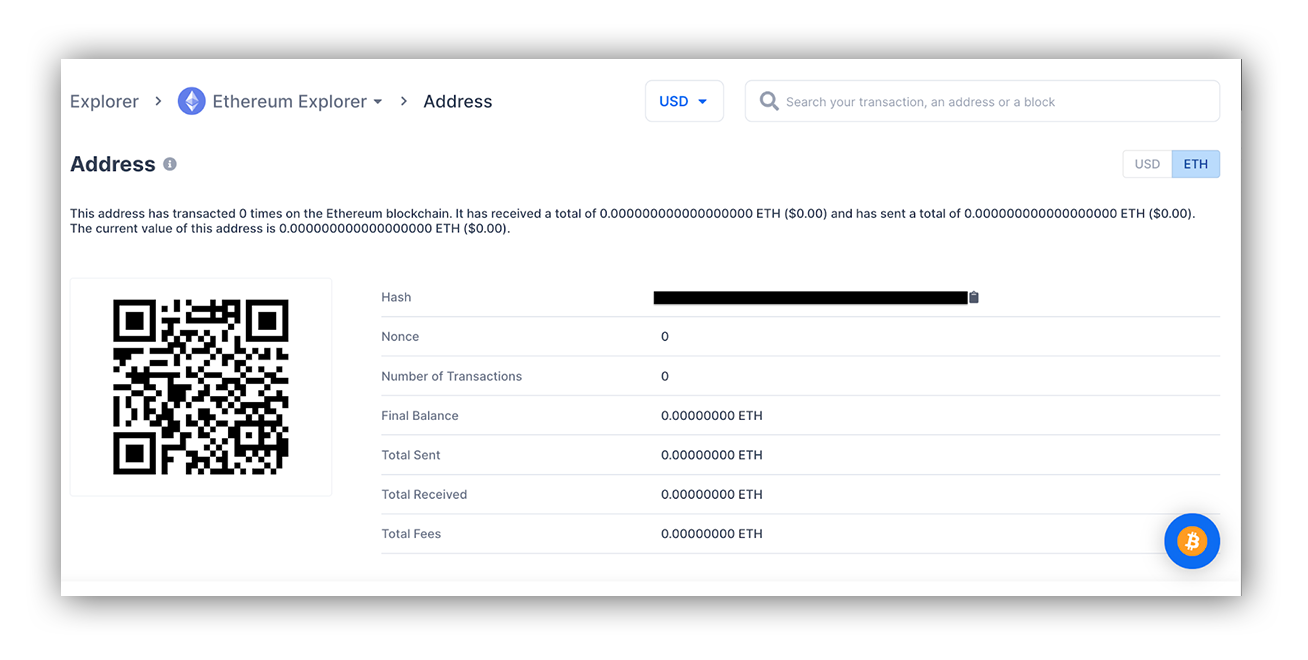
What stands out? This public wallet address has recorded zero transactions. When donating crypto to Ukrainian relief efforts, be wary of public addresses with minimal transaction history and low balances. Would you buy an expensive watch from a seller on Ebay with zero transaction history? Probably a red flag, right? The same applies to crypto donations.
For a comparison, the Ukraine government’s (verified) Twitter account shared three cryptocurrency wallet addresses — a Bitcoin wallet address, Ethereum wallet address, and Polkadot address. Below is the transaction history for the Bitcoin public address 357a3So9CbsNfBBgFYACGvxxS6tMaDoa1P:
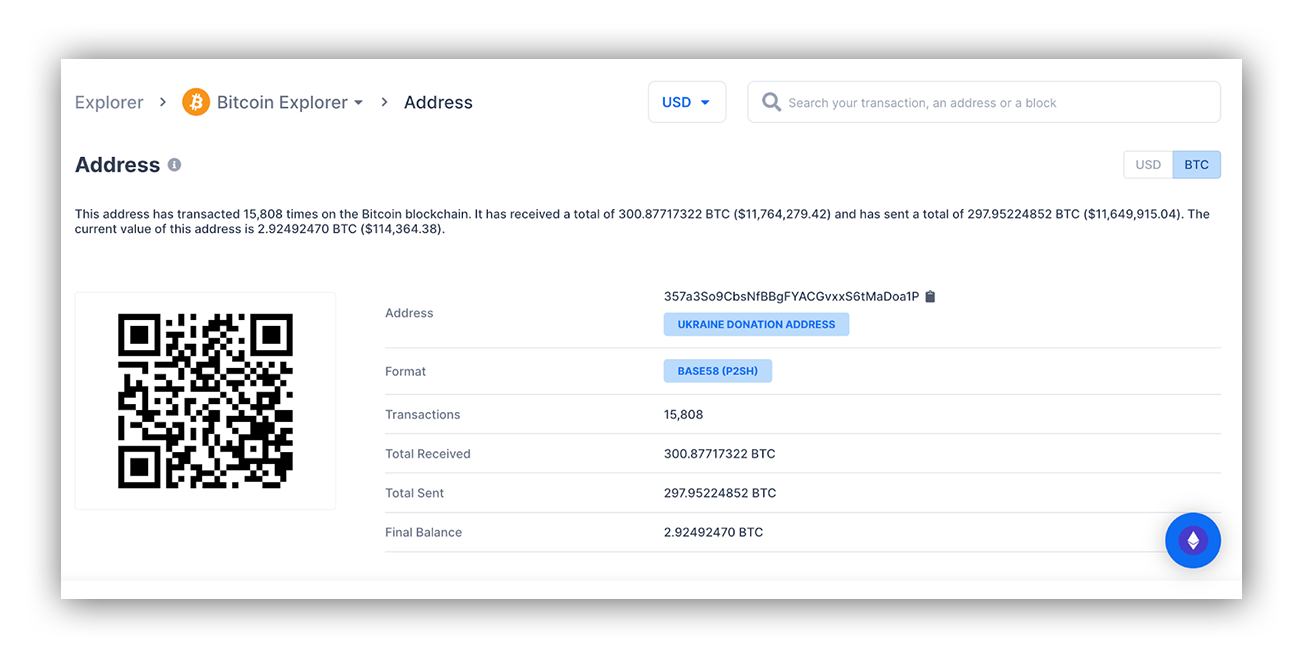
This public wallet address has recorded tens of thousands of transactions and is labeled as a “Ukraine Donation Address.” This is a stark contrast to the transaction history of the Ethereum public wallet address listed in the email body.
The bottom line? If you’re thinking about donating crypto, double-check the public address and transaction history before hitting “send.” You can review the transaction history of a public address using block chain explorer sites like blockchain.com and Polkascan. Be wary of public addresses with minimal transaction history and low balances. Also, perform a quick Google search of the public address. If it’s not linked to Ukraine crypto donation efforts, that’s a tell-tale sign that something is wrong.
Fake charitable apparel emails
Scammers don’t just target people wanting to donate. They also target people looking to “show” their support. If you’re thinking about buying apparel to support Ukraine, here are a couple of things to lookout for before you hit “buy it now.”
Here’s a recent phishing email investigated by our SOC:
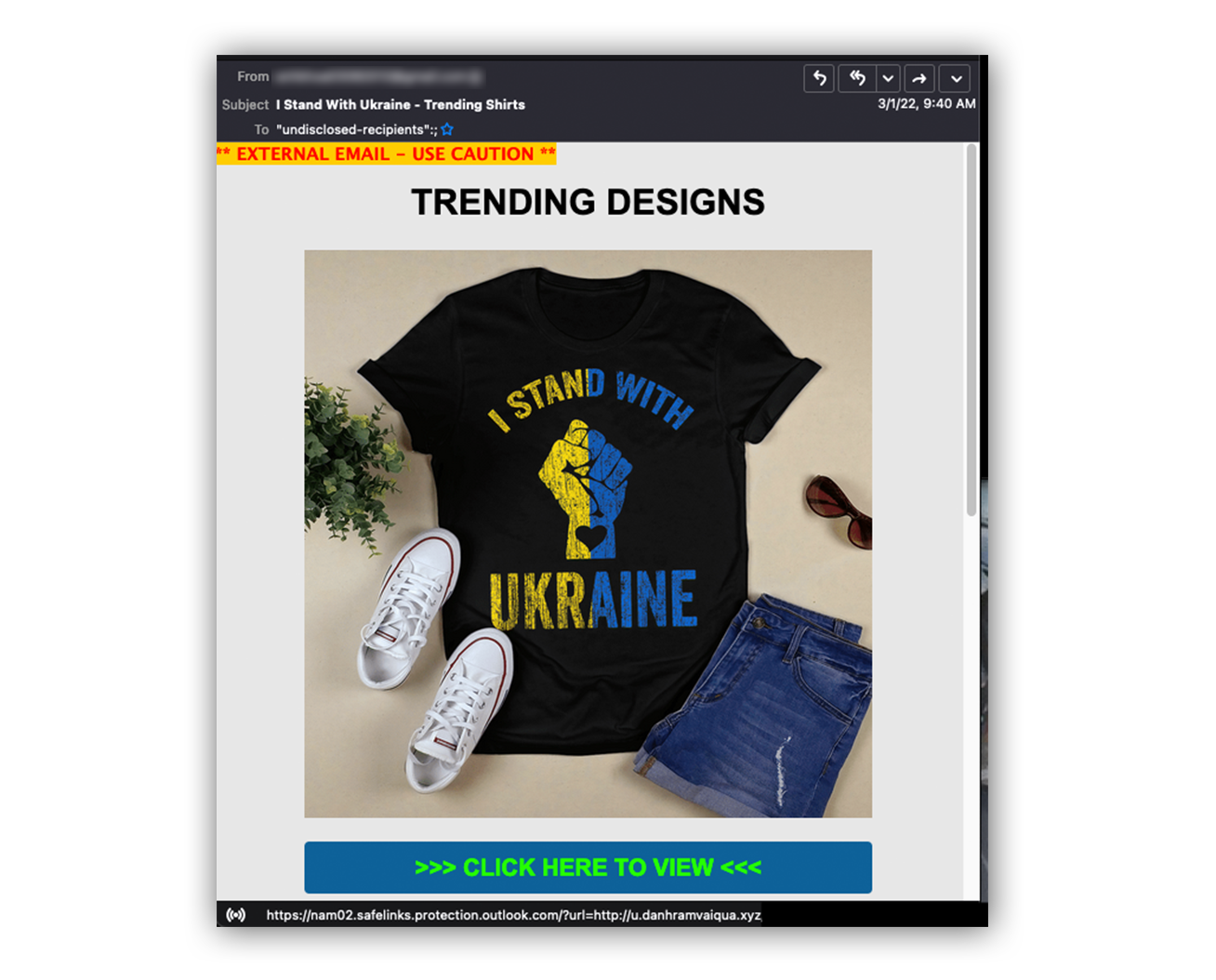
Our first clue that something just doesn’t feel right? The email address listed in the “From” field has no online presence according to our friends at EmailRep.
Now focusing on the email body, if we were to click the “Click Here to View” hyperlink, that would connect our web browser to a domain hosted at u.danhramvaiqua[d]xyz.

For some quick context, the .xyz top-level domain has a history of domain abuse. We’re in no way saying that all websites using the .xyz top-level domain lead to bad things, but used in this way — it’s certainly enough to grab our analyst’s attention.
Let’s take a look at the website reputation for u.danhramvaiqua[d]xyz. Reviewing a website’s reputation is a great way to understand if a specific IP, URL, or domain name has a negative reputation or if it’s been categorized as malicious. There are a number of free resources you can use. Submit the domain and review the results. It’s that easy. Here are a couple of our favorites:
Webpulse Site Review classified the u.danhramvaiqua[d]xyz domain as phishing.
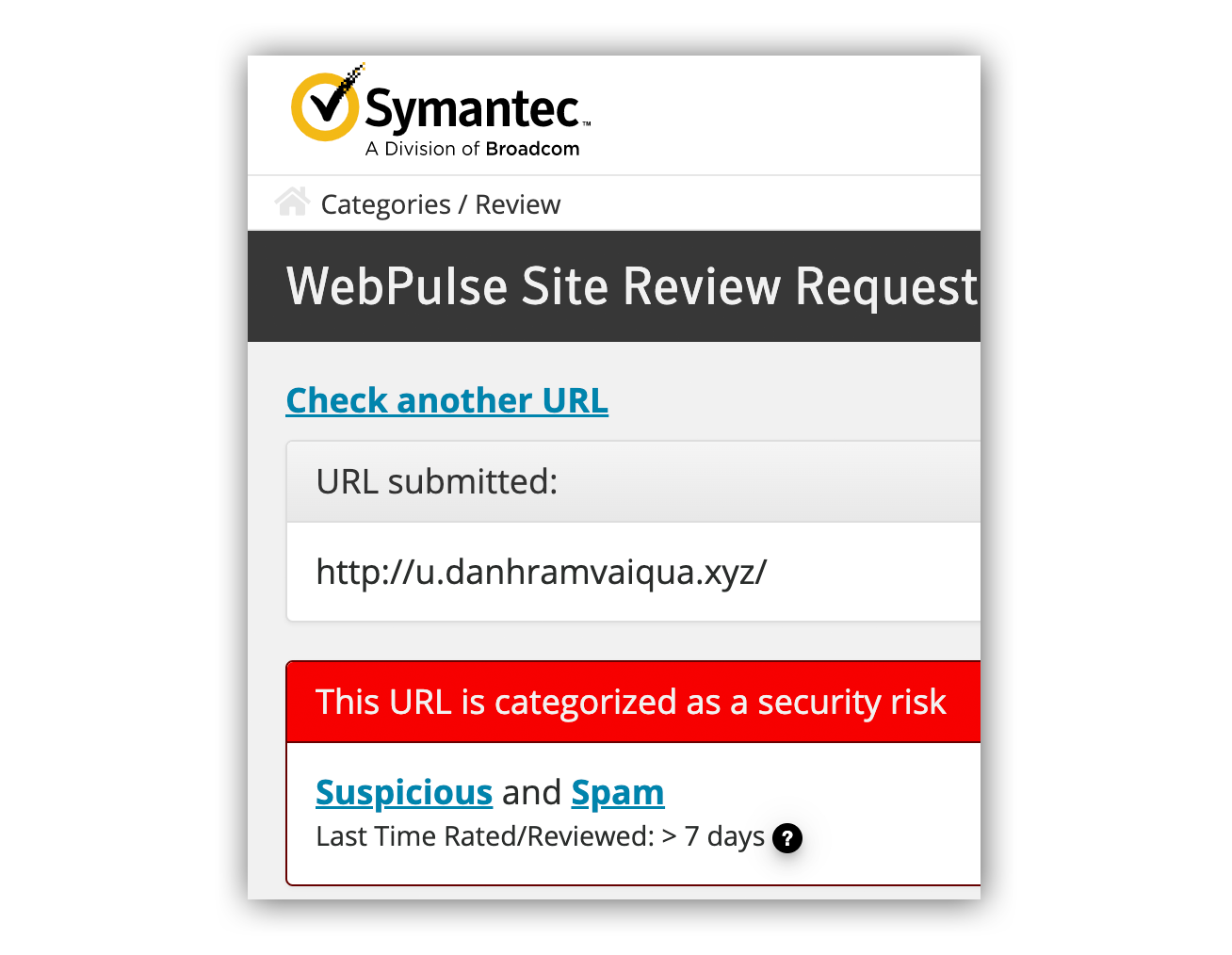
So far, we have an email address with no digital presence sending an email with a hyperlink that points to a .xyz domain that has a reputation of phishing. This is enough evidence to make the decision to either delete the email in question or forward it on to your IT team for further review.
But for folks looking to go an additional step, let’s take a look at what happens when we load the “u.danhramvaiqua[d]xyz” page in a sandbox and browse the URL as if a user visited that page. We’ll use URLScan — another free online resource.
URLscan provided us the effective URL (where the domain is pointing to), provided us screenshots by loading the page (which it does if the page is active), and even let us know Cloudflare issued a TLS certificate for the site on February 28, 2022. The biggest takeaway is that if a user were to click the “Click Here to View” hyperlink, they’d be redirected to www[d]mimoprint[d]shop.
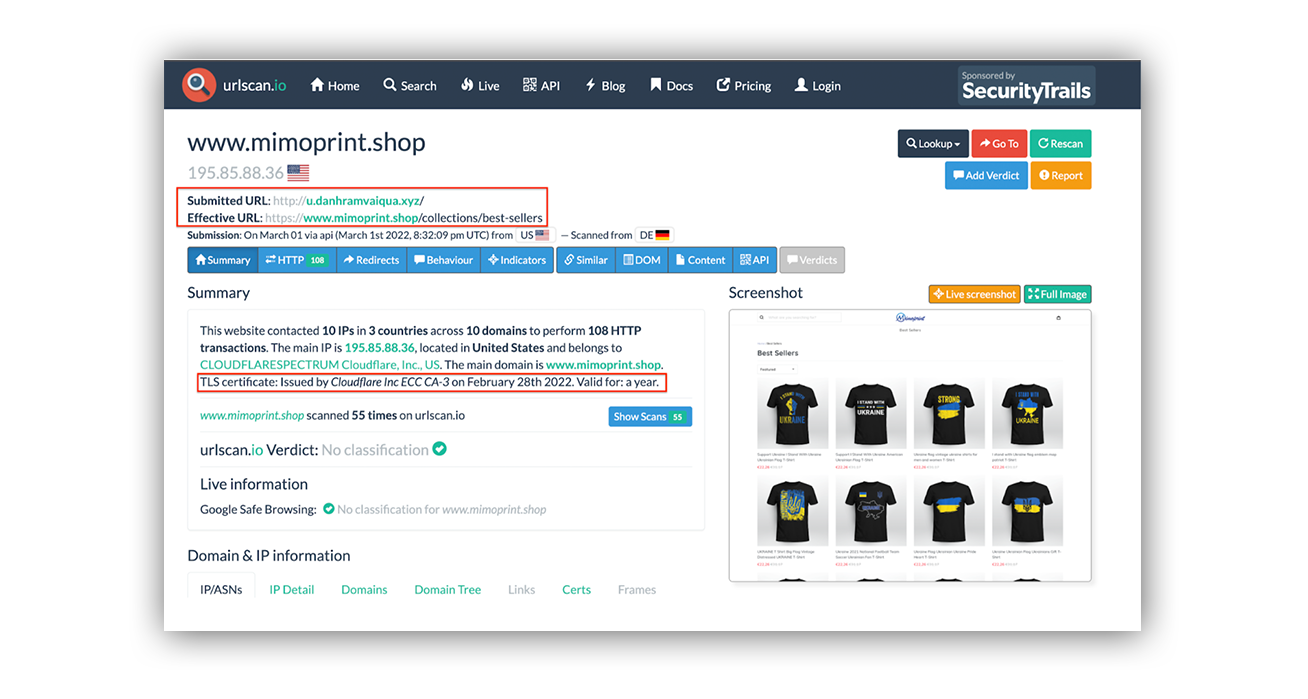
You may be asking, should I look up the website reputation for www[d]mimoprint[d]shop? Absolutely! Spoiler: It’s got a bad reputation.
If you’re considering a donation to support victims of the crisis in Ukraine, be aware of the prevalence of scams at play to make sure your donations are actually going to help those in need. We strongly recommend using official channels to make donations and researching your options before you hit “send” or “buy it now.”
Things you can do to spot potential scam emails
- Before clicking on hyperlinks, hover over them and check where that URL may lead you.
- Report suspicious emails to your security team and avoid interacting with any unsolicited emails.
- Ensure your org conducts frequent security awareness training sessions and that they’re adapted to current events that might be used to mislead your end-users.
- Make sure your org has a good security email gateway product in place for protection.
Have questions about scams like these, or want to learn more about the Expel Phishing team? Reach out any time.






