Security operations · 2 MIN READ · HIRANYA MIR, JOSE TALENO AND CHRISTINE BILLIE · MAR 24, 2023 · TAGS: MDR / Tech tools
As we wrote recently, we expected the failure of Silicon Valley Bank (SVB) to open the door to counterparty fraud attempts. Our CISO Greg Notch explained:
An increased volume of bank account switching presents a massive opportunity for payment counterparty fraud. If an attacker is able to deceive someone into altering a few account and routing numbers, they can direct money to themselves, rather than your vendor or into your own accounts. Often this begins with compromised or forged emails resulting from business email compromise (BEC). Depending on the size of your environment, this may go unnoticed for some time. By the time you detect the attack, you could be out a significant amount of money—and you’ll still owe your vendor.
As expected, it wasn’t long before we saw our first fraud attempt via phishing attack. Since we knew our customers would likely be targets of SVB phishing attempts, our security operations center (SOC) analysts were on it before the customer could even submit the suspicious email to our phishing team. Here’s how we did it.
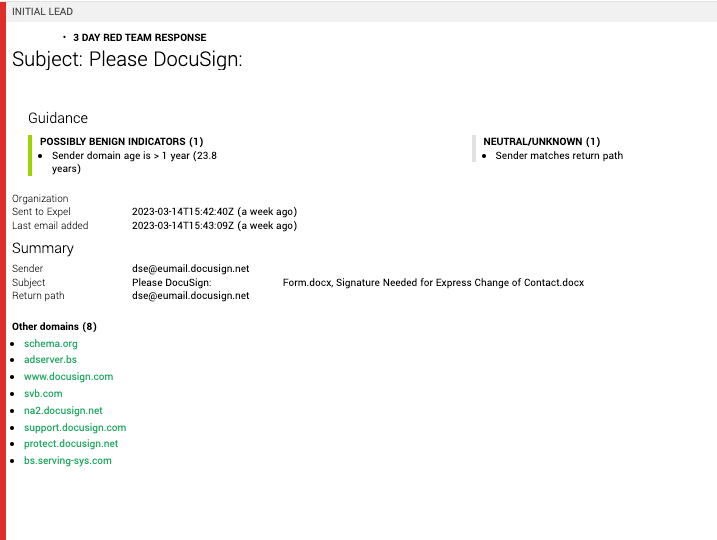
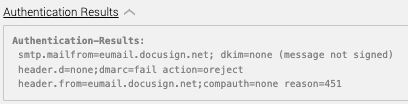
First, our analysts created a YARA rule to help identify any emails with affiliated keywords or domains, automatically adding them into our high-priority investigation queue. As it turns out, this is exactly how the attack began (see step 1 in the below graphic). A rule match increased the severity of the alert in our queue in order to get eyes on it ASAP, and we noted that the email headers displayed signs of possible spoofing. (When we see the “spf=fail” value, we’re immediately suspicious.) From there, we saw that the sender’s IP address wasn’t affiliated with DocuSign, so there were red flags popping up all over.
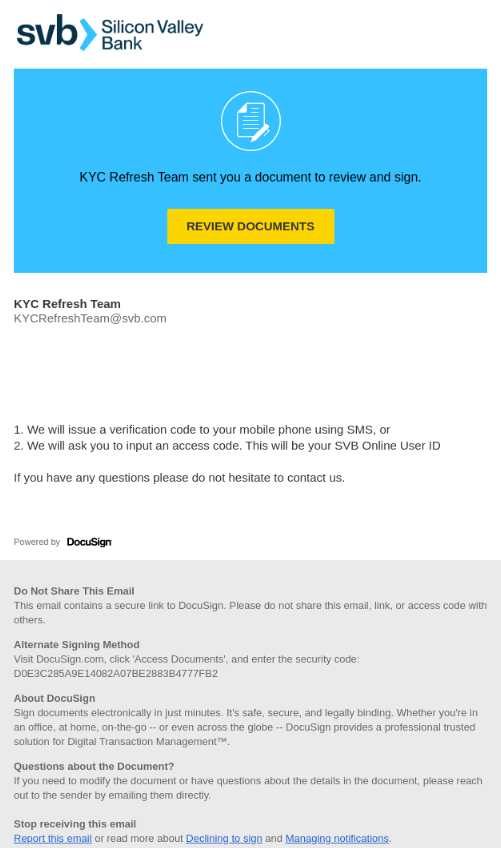
In step 2, we examined the body of the email. The email address—kycrefreshteam@svb.com—is the sender posing as an SVB employee. It’s important to note this email did not actually come from anyone at SVB. However, the attacker is impersonating an employee to masquerade as a legitimate party. At first glance, the email looks legitimate. There are no obvious spelling, grammar, or punctuation errors. However, given the circumstances surrounding the collapse of the bank and the red flags identified in step 1, we’re closer to knowing for sure that this is a phishing attempt.
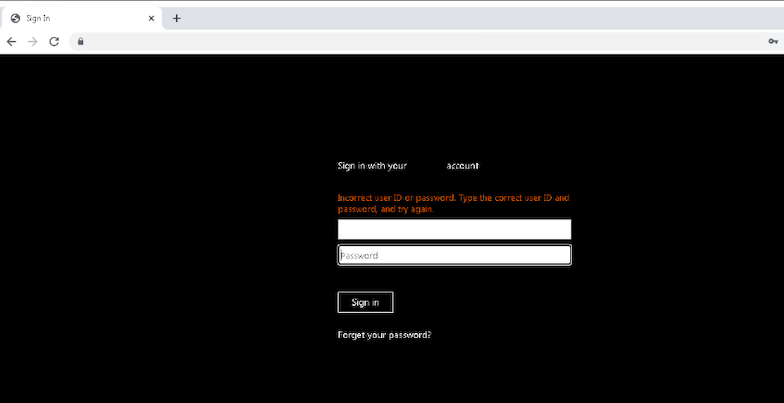
It’s standard practice in our SOC to double-check any risks associated with action requests within an email, which we see in step 3. The “review documents” button in the email leads to an illegitimate customer login page, spoofed to mimic a page on the customer’s website, which asks users to submit their SVB account credentials.
In this case, our custom YARA detection rule—set up to flag specific malicious domains for SVB—flagged the phishing attempt for additional urgency and scrutiny, but we essentially go through the same sort of investigation for any suspicious email that customers submit to our phishing team.
Unfortunately, we expect to see more of this sort of activity in the coming days and weeks, especially as the banking industry navigates some choppy waters.
If you’re interested in our phishing offering, click here to learn more.