tech stack
MDR | 3 min read
Stop counting integrations. Start counting what matters.With integrations and security, quantity is not the same as quality. Integration counts are a vanity metric that make you less secure.
Product | 2 min read
Email coverage expansion: Sublime Security integration now liveExpel MDR for Email now integrates with Sublime Security for enhanced threat visibility across your inboxes.
MDR | 3 min read
Getting real value from your Palo Alto investment: how Expel MDR transforms security operationsExpel MDR reduces Palo Alto alert noise by 87% with 17-minute response times. Expert 24x7 analysis maximizes your security investment ROI.
Rapid response | 1 min read
Security alert: Ivanti zero-day vulnerabilityIvanti disclosed a critical zero-day vulnerability impacting multiple products. Address it immediately to prevent unauthenticated remote code execution.
Rapid response | 2 min read
Security alert: Christmas Day Chrome extension compromiseAt least five Chrome extensions, including the Cyberhaven extension, were targeted on Christmas Day. Here's what you need to know.
MDR | 4 min read
Part III: How MDR can transform your SIEM investmentThis is part three of a three-part blog series on how MDR can transform your SIEM investment by augmenting and optimizing its capabilities.
MDR | 4 min read
Part II: How MDR can transform your SIEM investmentThis is part two of a three-part blog series on how MDR can transform your SIEM investment by augmenting and optimizing its capabilities.
MDR | 4 min read
Part I: How MDR can transform your SIEM investmentThis is part one of a three-part blog series on how MDR can transform your SIEM investment by augmenting and optimizing its capabilities.
Rapid response | 1 min read
Security alert: Fortinet zero-day vulnerabilityFortinet has disclosed a zero-day vulnerability that needs to be patched immediately, or the protocol connection to the internet should be disabled.
Rapid response | 2 min read
Security Alert: CrowdStrike Windows OutageAn issue in a CrowdStrike Falcon Sensor update rendered Microsoft’s Windows OS inoperable. Here’s what happened and how you can address it.
MDR | 3 min read
Making sense of the seismic shifts in the SIEM worldHere's answers to pressing questions about what's happening in the world of SIEM, and what to do if you're asking yourself these questions.
Rapid response | 1 min read
Security alert: Palo Alto Networks PAN-OS GlobalProtect Command Injection VulnerabilityPalo Alto Networks disclosed that attackers are exploiting a vulnerability in PAN-OS for GlobalProtect. Here's what you need to know.
Rapid response | 1 min read
Security alert: XZ Linux utility backdoorResearchers identified a backdoor into the XZ Linux utility, via supply chain compromise. Here’s what you need to know.
Current events | 1 min read
GKE/Gmail vulnerability: notes and tipsSecurity researchers have discovered a new Google Kubernetes Engine misconfiguration. Here’s what you need to know.
Cloud security | 3 min read
New mind maps & cheat sheets: Azure & KubernetesOur new Kubernetes mind map/cheat sheet show you which API calls are associated with different MITRE ATT&CK tactics in K8 environments.
MDR | 6 min read
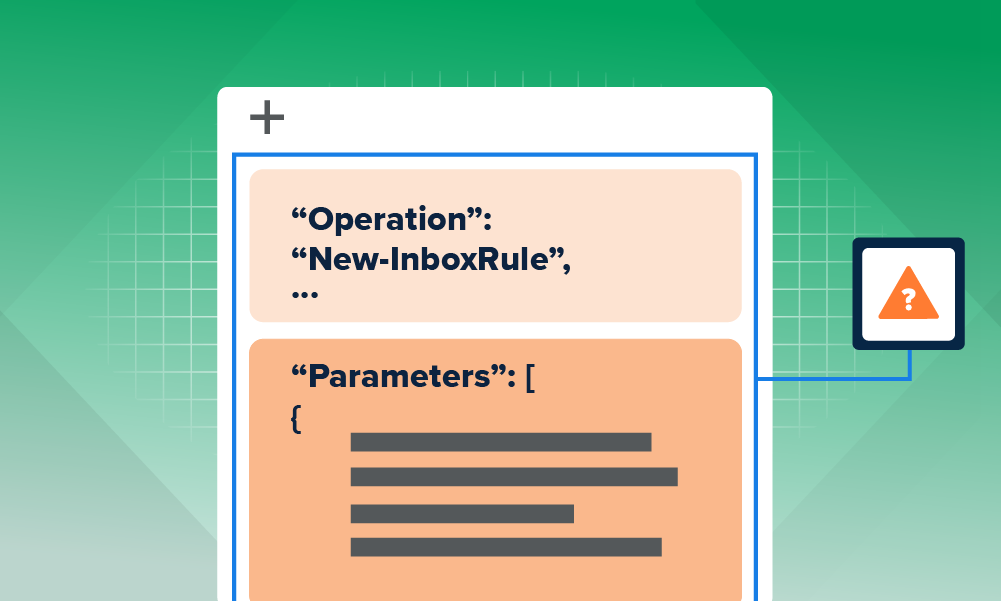
Assessing suspicious Outlook rules: an exerciseOutlook Inbox rules are used for legitimate and malicious reasons. Use these case exercises, tips, and tricks on how to analyze them.
Current events | 7 min read
Attackers are expanding access through Amazon CognitoImproperly configured AWS Cognito web portals can allow attackers to gain direct access to your AWS control plane. Here's how.
Current events | 2 min read
Our top five cybersecurity predictions for 2024Here are our top five cybersecurity predictions for 2024 from Expel experts and leadership based on trends and current events.
MDR | 4 min read
What frameworks and tools drive security maturity?New research by the SANS Institute, commissioned by Expel, outlines the frameworks, tools, and techniques that drive security maturity.
Rapid response | 2 min read
Security alert: Okta “support user” data theftOkta recently determined an attacker stole user support system info in October 2023. Here’s what Okta customers need to do right now.
Current events | 4 min read
Suspicious Outlook rules: high-fidelity patterns to watch forInbox rule manipulation is hard to accurately alert on. Here’s some tips on how to spot high-fidelity inbox manipulation tactics.
Rapid response | 1 min read
Security alert: privilege escalation vulnerability in Confluence Data Center and Server, CVE-2023-22515Here's how to mitigate a Confluence Data Center and Server vulnerability that lets attackers create admin accounts on external-facing servers.
Rapid response | 1 min read
Security alert: zero-day vulnerability CVE-2023-4863 in libwebp (WebP) libraryCVE-2023-4863 is a zero-day vulnerability in libwebp, which can result in arbitrary command execution when exploited. Here’s why it matters and what to do.
MDR | 7 min read
How to identify when you’ve lost control of your SIEM (and how to rein it back in)See if these four telltale warning signs get your head nodding. If so, learn how to get started on regaining control.
Cloud security | 3 min read
In the age of innovation, does security hold the key?A new report by the CSA showcases the results of research on getting a deeper understanding of areas of innovation and cloud use trends.
Rapid response | 1 min read
Security alert: critical Fortigate remote code execution vulnerabilityGet a clear breakdown of the critical Fortigate Firewall vulnerability's impact and steps you can take to reduce your risk.
Rapid response | 2 min read
Security alert: 3CXDesktopApp supply chain attackA supply chain attack on 3CXDesktopApp can turn installers into malicious tools. Learn the steps you can take to mitigate the risk.
Cloud security | 1 min read
Understanding the 3 Classes of Kubernetes RiskThe first step toward securing Kubernetes environments is understanding the risks they pose and identifying the ways in which those risks can be mitigated.
Rapid response | 5 min read
Incident report: stolen AWS access keysLearn what happens after AWS access keys are stolen. Our teams collaborated on a real-world incident. Read how we responded to the attack.
Rapid response | 3 min read
Emerging Threat: CircleCI Security IncidentA security incident at CircleCI requires immediate credential rotation. Learn what happened, why it matters, and the steps to take to mitigate the risk.
Data & research | 5 min read
45 minutes to one minute: how we shrunk image deployment timeWe recently figured out how to reduce Kubernetes image deployment time from 45 minutes (way too long) to one minute (really fast). Here’s how we did it.
Rapid response | 2 min read
Security alert: high-severity vulnerability affecting OpenSSL V3 and higherTwo new security flaws affect OpenSSL v3.0 and later. Learn about the vulnerabilities and why you should upgrade to v3.0.7 as soon as it's reasonable.
MDR | 4 min read
Who ya gonna call (to make the most of your SIEM data)?Import your SIEM into Expel Workbench and turn hours of development into custom rules. Find out why you might not need a SIEM at all.
Cloud security | 5 min read
Understanding role-based access control in KubernetesUnderstanding authorization is critical to securing Kubernetes. Learn how RBAC works and the rules that govern your access control.
Cloud security | 3 min read
Three Kubernetes events worth investigatingMonitoring your Kubernetes environment? Learn what to look for and how to use audit logs to secure your production workloads.
Cloud security | 3 min read
Kubernetes: the whale in the roomMore than half of our cloud customers use Kubernetes (k8s) to ship software faster and cut costs with elastic infrastructure.
Rapid response | 2 min read
Emerging Threats: Microsoft Exchange On-Prem Zero-DaysA new zero-day vulnerability affects Microsoft Exchange Server. Until a patch is issued, here are the steps you can take to mitigate risk.
Rapid response | 2 min read
Emerging threat: BEC payroll fraud advisoryOur SOC observed BEC attacks targeting Workday to commit payroll fraud. Learn how to protect your human capital management systems.
Cloud security | 3 min read
GCP Incident report: Spotting an attacker in Google CloudOur guide details a GCP incident, from initial attacker access to resolution. Learn our key takeaways for securing your cloud environment.
Rapid response | 6 min read
Incident report: From CLI to console, chasing an attacker in AWSWe detected and stopped unauthorized access in a customer's AWS environment. Learn how we spotted it, what we did, and key takeaways for your security.
Current events | 8 min read
Top Attack Vectors: February 2022Stay ahead of the latest threats. Our report on February 2022 incidents reveals top attack vectors and recommendations to protect your org.
Current events | 6 min read
Top Attack Vectors: January 2022Get the top attack vectors and trends from our SOC's January 2022 incident investigations. Learn our key recommendations to protect your org.
Cloud security | 3 min read
5 pro tips for detecting in AWSCloud security is complex, but start with the basics. Get pro tips to help focus your lens for detecting threats in AWS effectively.
Cloud security | 4 min read
Attack trend alert: AWS-themed credential phishing techniqueAttackers are phishing with fake AWS log-in pages. See how our crew identified and triaged a malicious email to protect a customer.
Current events | 7 min read
Top attack vectors: December 2021Get the top attack vectors and trends from our SOC's December 2021 incident investigations. Learn our key recommendations to protect your org.
Current events | 7 min read
Top attack vectors: November 2021Stay ahead of the latest threats. Our report on November 2021 incidents reveals top attack vectors and recommendations to protect your org.
Current events | 6 min read
Top attack vectors: October 2021Get the top attack vectors and trends from our SOC's October 2021 incident investigations. Learn our key recommendations to protect your org.
Current events | 5 min read
Top attack vectors: September 2021Get the top attack vectors and trends from our SOC's September 2021 incident investigations. Learn our key recommendations to protect your org.
Product | 4 min read
How we use VMRay to support Expel for PhishingSmart people and great tech tackle phishing. See how our analysts use VMRay to triage and analyze malicious emails from customers.
Current events | 5 min read
Top attack vectors: August 2021Get the top attack vectors and trends from our SOC's August 2021 incident investigations. Learn our key recommendations to protect your org.
Data & research | 6 min read
Swimming past 2FA, part 2: How to investigate Okta compromiseYou know how to spot an Okta compromise. Now read our investigation walkthrough and get five tips to strengthen your security defense.
Current events | 5 min read
Top Attack Vectors: July 2021Get the top attack vectors and trends from our SOC's July 2021 incident investigations. Learn our key recommendations to protect your org.
Rapid response | 5 min read
Incident report: Spotting SocGholish WordPress injectionOur SOC stopped a ransomware attack that compromised WordPress CMS to deliver a RAT. Get our recommendations to secure your site now.
Current events | 3 min read
Attack trend alert: REvil ransomwareA new REvil campaign trend is here. Find out what's new about the attack, how our SOC spotted it, and what you can do to protect your org.
Cloud security | 6 min read
Supply chain attack prevention: Three things to do nowCan’t trust the internet? Supply chain attacks like SolarWinds are not new. Get actionable tips to prepare and guard against similar attacks.
Current events | 3 min read
The SolarWinds Orion breach: 6 ideas on what to do next and whyGet our early observations on the SolarWinds Orion breach. Learn what to do next to detect related activity and better protect your org.
Cloud security | 8 min read
Terraforming a better engineering experience with AtlantisMake cloud provisioning easy. Learn how Expel leveraged Terraform and Atlantis to build a platform for simple, self-service infrastructure.
Product | 7 min read
Managed Detection & Response for AWSLearn how Expel detected and responded to an Amazon Web Services access key crisis with Amazon GuardDuty & CloudTrails logs securing cloud insecurities.
Product | 6 min read
Exabeam: an incident investigator’s cheat codeWe love EDR tools too, but here are our best tips and tricks for combining EDR data with other (equally) important security signals.
Product | 3 min read
Where does Amazon Detective fit in your AWS security landscape?Running workloads on AWS? Get up to speed on the latest and greatest AWS-native security tools in our newest post.
Product | 8 min read
Using JupyterHub for threat hunting? Then you should know these 8 tricks.Jupyter Notebook gave us the freedom to rethink the way we analyzed hunting data. Here are some tips and tricks you can use in your own analysis.
Cloud security | 5 min read
Making sense of Amazon GuardDuty alertsRunning AWS workloads? You need GuardDuty. Get our pro tips on what it is and how to make sense of all its security signals.
Product | 5 min read
Better web shell detections with Signal Sciences WAFIs Signal Sciences WAF part of your tech stack? Then you’ve got an amazing webshell detection method right at your fingertips.
Cloud security | 7 min read
Generate Strong Security Signals with Sumo Logic & AWS CloudtrailLooking to get more or better security signals from AWS Cloudtrail? Learn how with Expel.io. See how we use the Sumo Logic SIEM for actionable data.
Data & research | 8 min read
Our journey to JupyterHub and beyondUsing JupyterHub? Get our configuration tips, tricks, and learn how we use it to make technical research and security analysis easier.
MDR | 6 min read
How to make your org more resilient to common Mac OS attacksGot Macs in your org? Here are a few recent Mac OS attack trends and how you can become more resilient to ‘em.
MDR | 7 min read
How to choose the right security tech for threat huntingDeciding which tech to use for your threat hunt? Get pro tips on when and how to use different security technologies for your mission.
MDR | 4 min read
Does your MSSP or MDR provider know how to manage your signals?How well is your MSSP or MDR going to manage your fleet of security signals over time? Here’s how to figure out whether they’re up for the challenge.
Cloud security | 7 min read
How to build a useful (and entertaining) threat emulation exercise for AWSWant to test your analysts’ detection skills in the cloud? Here are our tips and tricks for building your own threat emulation exercise in AWS.
Data & research | 6 min read
Five tips for improving your data ingestion and auditing processYou’re processing loads of data every day...but are you catching it all? Here are tips from our pros for rocking your data auditing.
MDR | 9 min read
12 ways to tell if your managed security provider won’t suck next yearWill your service quality improve over time? Our COO Yanek Korff shares tips for making sure you choose a service provider that will last.
Cloud security | 8 min read
How to find Amazon S3 bucket misconfigurations and fix them ASAPWhy do Amazon S3 bucket breaches happen? Get the AWS pro tips you need to protect your org from making this costly mistake.
Product | 6 min read
Evaluating GreyNoise: what you need to know and how it can help youBoost analyst efficiency! Learn why GreyNoise is a key technology used behind the scenes to enhance Expel Workbench and our analysts' work.
MDR | 9 min read
12 revealing questions to ask when evaluating an MSSP or MDR vendorWe’ve heard lots of interesting Qs as prospective customers evaluate which MDR provider is right for them...here are the 12 you should be asking.
MDR | 10 min read
Seven ways to spot a business email compromise in Office 365Protect your Office 365 from BEC scams. Learn what Business Email Compromise is and get examples of mailbox rules for prevention.
MDR | 8 min read
Why we love threat emulation exercises (and how to get started with one of your own)If your team doesn’t have lots of incident response practice under their belt (yet!), a threat emulation exercise is the perfect way to help them flex.
MDR | 4 min read
How to start a cybersecurity program (or restart one that lapsed)Stuck with a legacy security program? Get quick steps to take when you have less, to get your cybersecurity efforts back on track.
Cloud security | 3 min read
Three tips for getting started with cloud application securityIf you're feeling like your SaaS security knowledge is a bit cloudy, these three pro tips will get you started on the right path.
SOC | 6 min read
How to get the most out of your upcoming SOC tour: making your provider uncomfortableVisiting an MSSP's SOC? Learn how to prepare for your visit to get the best sense of the service you're really buying.
MDR | 5 min read
How to hunt for reconnaissanceUse the hunting process to find attackers performing reconnaissance, through actions that aren’t things most users typically do, in your system.
Cloud security | 12 min read
A common sense approach for assessing third-party riskWalk through our lightweight third-party assessment process. Download the exact questionnaire and emails we use to vet vendors now.
Product | 10 min read
Investigating Darktrace alerts for lateral movementLearn how Darktrace works and read an Expel review and features guide for Darktrace to decide if this AI cybersecurity platform is right for you.
MDR | 3 min read
How to disrupt attackers and enable defenders using resilienceSo…what is resilience? We’ll cover that and also how it works in this post. We’ve even thrown in a couple examples to get you started.
MDR | 5 min read
Managed detection and response (MDR): symptom or solution?An uncommonly clear review of what managed detection and response (MDR) is, where it came from and what it can/can't do for you.
MDR | 3 min read
What’s endpoint detection and response (EDR) and when should you care?We cut through the hype to explain what Endpoint Detection and Response (EDR) tools can do for you.
MDR | 7 min read
Warning signs that your MSSP isn’t the right fitLook out for these 5 indicators that it's probably time to start considering alternatives to your managed security services provider (MSSP).
Rapid response | 1 min read
Heads up: WPA2 vulnerabilityA (very) quick overview of the reported WPA2 weakness. The TL;DR is “don’t flip out" because this an example of bug marketing.
MDR | 3 min read
Get your security tools in order: seven tactics you should knowGet your work right. Learn seven things to consider to bring harmony to your security toolchain and get the equipment you need to succeed.
MDR | 7 min read
How to triage Windows endpoints by asking the right questionsThe three parts of the investigative mindset and how to apply them when you triage Windows endpoint alerts.