Security operations · 3 MIN READ · JON HENCINSKI AND MICHAEL BARCLAY · FEB 17, 2021 · TAGS: MDR
Over the past week, Expel detected ransomware activity targeting law firms attributed to REvil, a Ransomware-as-a-service (RaaS) operation.
In this post, we’ll share more about REvil, how we detected this latest attack and what you can do to make your own org more resilient to a REvil attack.
What is REvil?
REvil is a well-known ransomware group operating a Ransomware-as-a-Service (RaaS) program since early 2019.
Given that initial access to a target organization is the job of RaaS affiliates contracted by the core REvil group, the delivery and initial infection vectors vary. But they’ve been known to include phishing, the exploitation of known vulnerabilities in publicly accessible assets and collaboration with botnet owners who sell existing infections to REvil affiliates.
In recent REvil campaigns, attackers deployed a modified version of Cobalt Strike’s BEACON agent to compromised systems before escalating privileges and moving laterally in the target environment.
Once REvil has administrator-level privileges inside an organization, they’ll deploy REvil ransomware, aka SODINOKIBI or BLUECRAB.
What’s new about this particular REvil campaign?
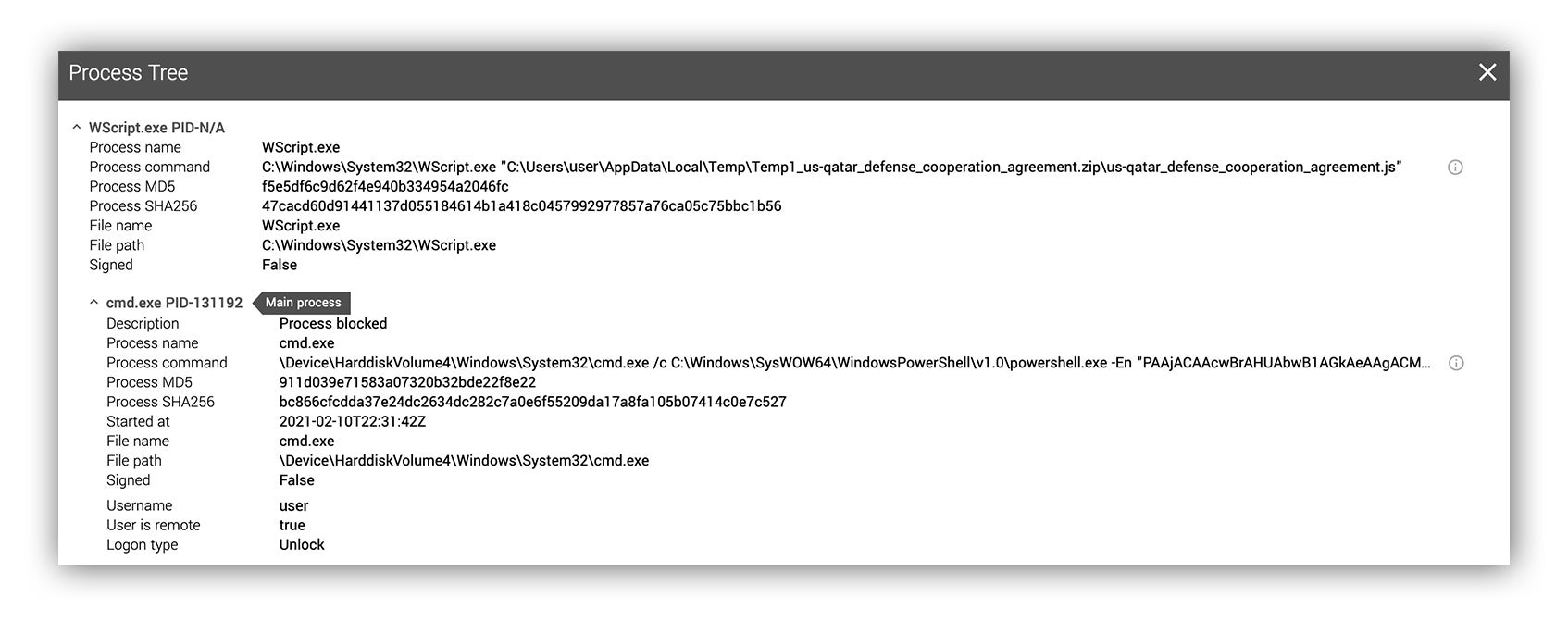
This most recent campaign is similar to activity we saw in fall 2020, where users visit a number of compromised yet legitimate third-party websites and are redirected to a Question & Answer (Q&A) forum instructing them to download a ZIP file that contains a malicious JScript file.
It appears as though users weren’t directed to these fake forum posts via phishing emails, but instead through their own Google searches. This suggests that the attackers responsible for this campaign invested considerable effort into boosting these malicious pages higher in Google result rankings.
Many of these pages align with themes related to legal topics, while others talk about international defense agreements or even cover letter samples.
In short, there’s a wide range of topics being showcased on these various sites.
The JScript file, when run, deploys a BEACON stager to the system.
So far we’ve seen REvil targeting users in Germany and in the United States.
How to detect REvil activity in your own environment
There are a few activities you can alert on in an effort to detect REvil activity:
- Alert when you see wscript.exe or cscript.exe execute a .vbs, .vbscript or .js file from a Windows user profile. If this generates too many false positives, try adding the condition where the wscript.exe or cscript.exe process also initiates an external network connection.
- Alert when wscript.exe or cscript.exe execute a .vbs, .vbscript or .js file from a Windows user profile and the process spawns a cmd.exe process.
- Alert when you see Windows PowerShell execute a base64 encoded command and the process initiates an external network connection.
REvil process example
How to remediate if you think you’re affected
#1: Contain the host(s)
Isolate the host in question to remove attacker access.
#2: Start the re-image
Attempting to manually clean the fileless persistence mechanism used by this campaign may lead to re-infection on startup if not done properly. That’s why re-imaging is critical.
#3: Scope the environment for additional infections
The PowerShell command executed as part of this activity occurs at the time of initial installation as well as at startup after persistence is established. This means that it’s extremely important to determine when the initial download of the zipped JScript file occurred and compare that to the timestamp associated with the detected PowerShell activity.
Network traffic destined for known command and control domains also provides a good way to timeline activity related to this campaign in your environment. If you discover that this infection persisted in your environment for more than a short period of time, it’s possible that attackers already moved laterally within your environment and/or escalated their privileges within your Active Directory Domain. RaaS actors typically wait until they have the privileges necessary to deploy ransomware to a large portion of your environment at once before moving on from the persistent implant portion of the attack lifecycle and actually deploying ransomware.
How to protect yourself against a REvil ransomware attack
There are actions you can take in your environment today to better protect your org against a REvil ransomware attack:
Configure Windows Script Host (WSH) files to open in Notepad
Prevent the double-click of evil JavaScript files. Configure JScript (.js, .jse), Windows Scripting Files (.wsf, .wsh) and HTML for application (.hta) files to open with Notepad.
By associating these file extensions with Notepad, you mitigate common remote code execution techniques. Pro tip: PowerShell files (.ps1) already open by default in Notepad.
Enable PowerShell Constrained Language mode
Constrained Language mode mitigates many PowerShell attacks by removing advanced features that these attack tools rely on such as COM access and .Net and Windows API calls. The language mode of a PowerShell session determines which elements can be used in the session.
Don’t expose RDP directly to the internet
Don’t expose RDP services directly to the internet. Instead, consider putting RDP servers or hosts behind a VPN that’s backed by two-factor authentication (2FA).
Create and test backups of data
Consider creating and testing backups of data within your org as part of your IT policy. Regularly creating valid backups that aren’t accessible from your production environment will minimize business disruptions while recovering from ransomware attacks or data loss.
Want to find out when we share updates from our SOC on attack trend alerts just like this one?
Subscribe to our EXE blog to get our latest posts sent directly to your inbox.