Security operations · 6 MIN READ · BRITTON MANAHAN, SIMON WONG AND HIRANYA MIR · FEB 17, 2022 · TAGS: MDR
We’re often asked about the biggest threats we see across the incidents we investigate for our customers. Where should security teams focus their efforts and budgets?
To answer these questions, we’re sharing monthly reports on the top attack vectors, trends, and resilience recommendations identified by our security operations center (SOC). Our goal is to translate the security events we’re detecting into a security strategy for your org.
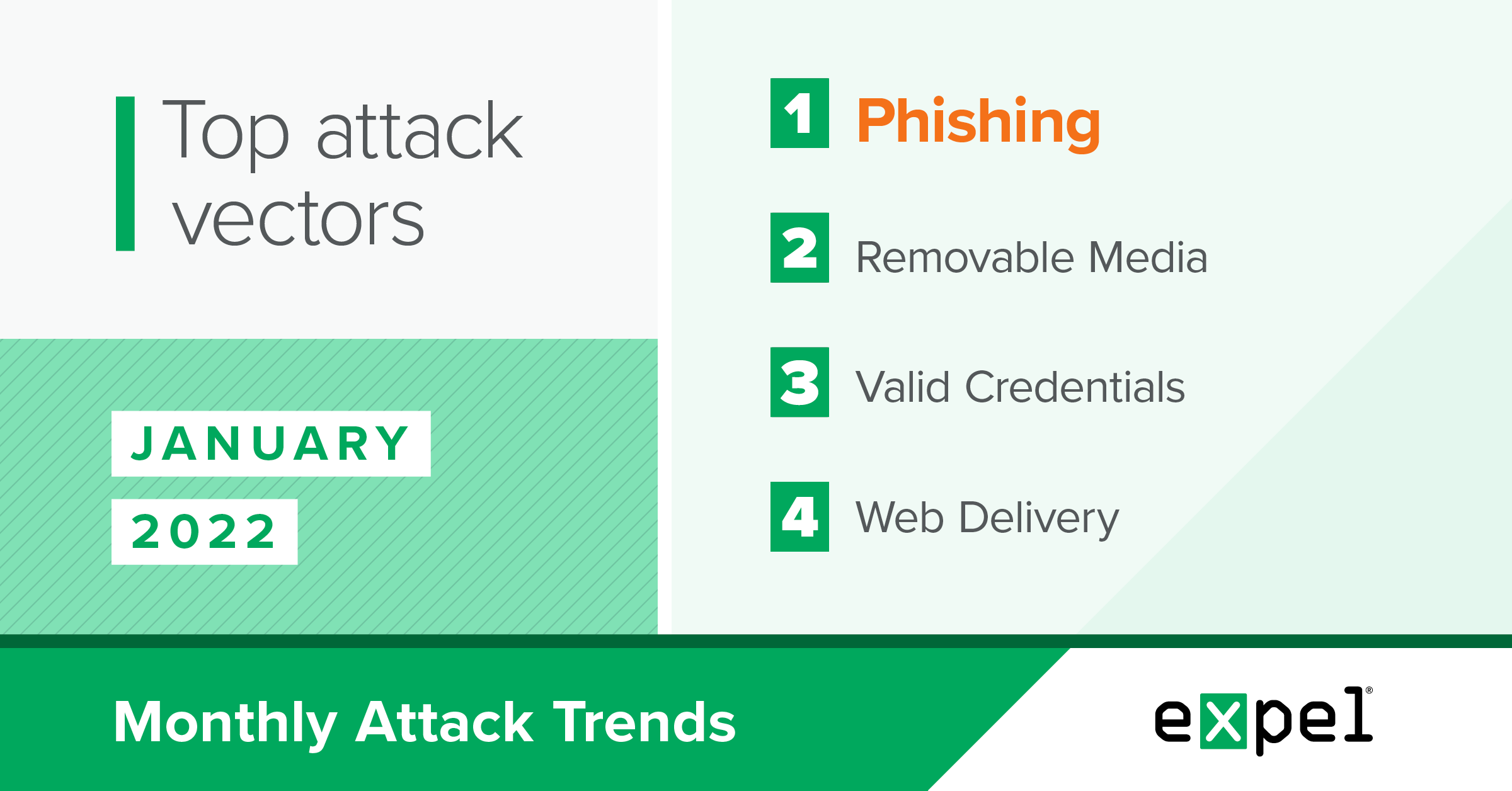
For this report, our SOC analyzed the incidents we investigated in January 2022 to determine the top attack vectors used by threat actors. Here’s what stood out this month:
- USB flash drives continuing to pose a malware threat
- Threat actors taking advantage of the wide range of malware at their disposal
- Phishing attempts using fake antivirus invoices and CEO impersonation
Keep reading for details and our tips for what to do about all the above.
Removable media remains a threat
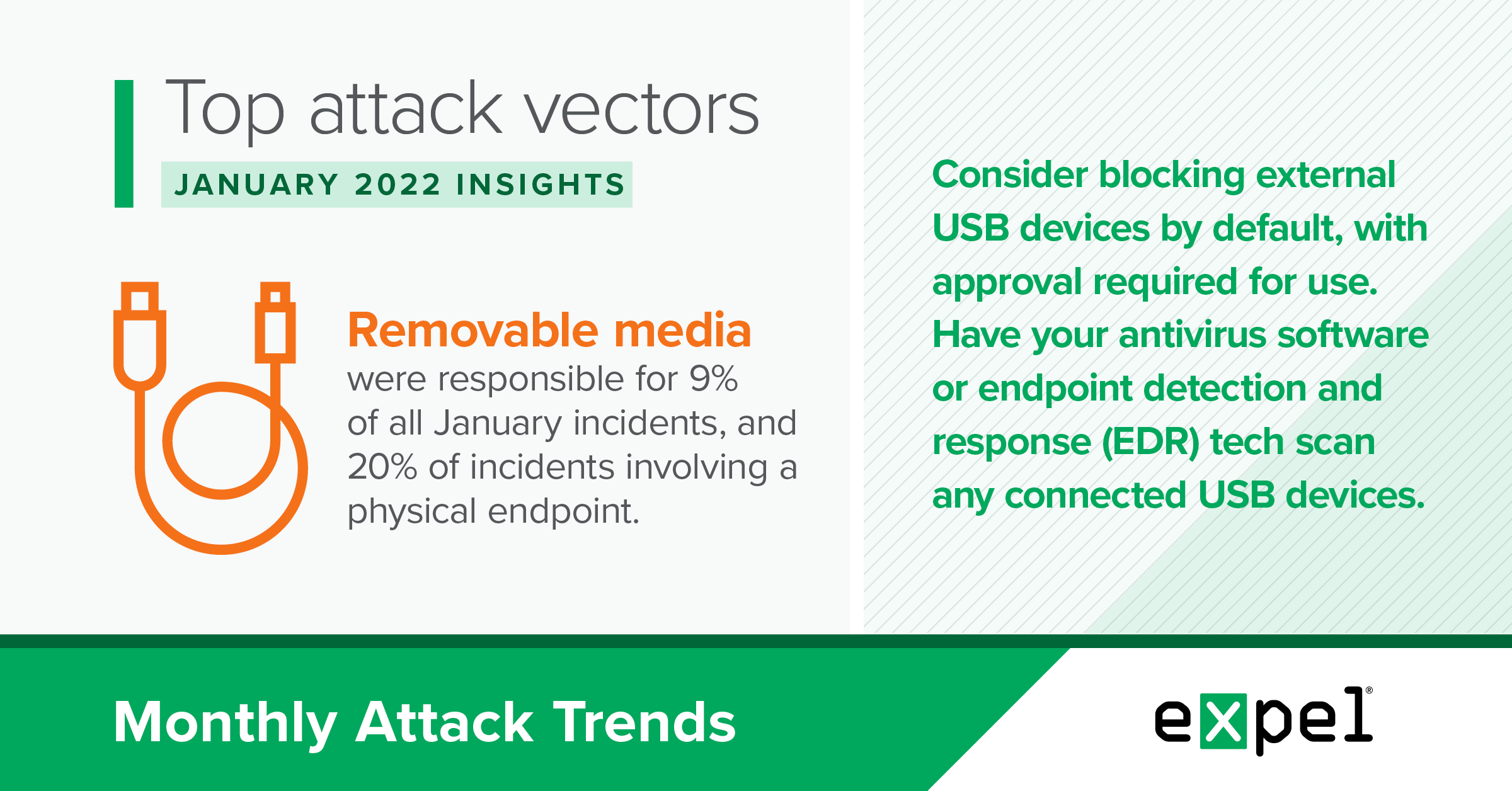
TL;DR: Removable media, in particular USB-based storage devices, are still a relevant threat to your environment.
In January 2022, removable media were responsible for nine percent of all incidents we responded to. That increases to 20 percent for incidents where the initial infection vector involved a physical endpoint (in other words, removing incidents involving a cloud-based service).
While security awareness training has focused on USB devices for years and some orgs require approval per-device before connecting them to a company-owned asset, these devices continue to be used in business environments because of their convenience.
And usage doesn’t just apply to known and trusted USB devices. In fact, a 2016 study examining what people would do if they found a USB in a parking lot showed that nearly 50 percent of people would plug an unknown USB device into their computer. While human curiosity and impulse is likely just as high in 2022, maybe we can hope the rise of remote work has made the discovery of office parking lot USBs less likely?
With that said, even trusted USB devices are often infected with malware variants that search for external storage devices connected to a victim host to infect them and spread further. This risk is much greater for endpoint users who can transfer USB devices from personal devices to business assets.
In January 2022 alone, we saw the AsyncRat, Valyrian, Gamarue, Agent Tesla, and Forbix malware families attempt to spread through USB storage devices. We also saw additional generic malicious worms including one deployed as a hidden VBScript script file on the device.
It’s highly likely that these malware variants would have tried to infect any other external USB storage devices attached to these systems had they achieved their initial infection without detection.
Resilience recommendations:
- Consider blocking external USB storage devices by default in your environment, with approval required for use.
- Make sure your security awareness training includes sections on the dangers of external USB storage devices.
- If supported, have your antivirus software or endpoint detection and response (EDR) tech scan any externally-connected USB storage devices.
- If possible, disable the AutoRun feature for USB flash drives in Windows-based operating systems. The AutoRun feature allows staged malware on USB devices to execute without additional interaction as soon as the device is plugged in.
A variety of variants
TL;DR: Threat actors are deploying a wide range of malware variants, frequently with the common goal of achieving remote system access.
In January 2022, no single malware variant dominated the landscape of identified payloads among incidents we responded to. Here’s a list of malware variants we identified, with no variant making up more than 15 percent of the total:
- Agent Tesla
- AsyncRAT
- ChromeLoader
- Conflicker
- CryptoWall
- Forbix
- Gamarue
- Gootkit
- Gozi
- Socgholish
- Valyrian
In addition to these malware families, we also observed:
- A generic VBScript and PowerShell-based script used for command and control that we weren’t able to attribute to a particular malware family.
- A legitimate crypto miner deployed for cryptojacking.
- Legitimate remote access software deployed for remote interactive desktop access.
- Two instances of a malicious Chrome extension (ChromeLoader) being installed.
- A ransomware sample.
This wide variety of malware and payloads demonstrates the abundance of malicious software and tooling at threat actors’ disposal. The continual economic incentives of cybercrime guarantee that malware families and their variants will continue to evolve.
Most of the malware samples listed above established a connection to a remote command and channel, though they took different obfuscated paths and stages to reach that point in their execution. Regarding initial infection vectors, we also observed a variety of techniques to deploy these malware variants, including:
- Removable media
- Web delivery
- JavaScript file
- Phishing
- Macro-enabled Microsoft Office doc
To sum it up: the info in this section shows that defenders need to make sure they don’t hyperfocus on any particular malware variant or specific tool or technique used by threat actors, but rather focus on a layered approach to security that can detect and prevent the varied and continually evolving malware landscape. Regarding identification of samples you may encounter, open source intelligence (OSINT) tools for malware are a great way to identify a malware family without needing a full-time malware reverse engineer on your staff.
Resilience recommendations:
- Confirm your endpoint detection and response (EDR) coverage across all of your endpoints.
- Implement layered security controls across your environment to detect and prevent evolving threats.
- Perform a penetration test against your environment to evaluate your current security posture.
- Subscribe to OSINT feeds to stay up-to-date on malware trends and leverage this intelligence in your deployed security tech.
Phishing
TL;DR: We saw an increase in fake Norton invoices and CEO impersonations emails in January 2022.
We reviewed over five thousand potentially malicious email submissions in January 2022, and identified two phishing trends using the following techniques:
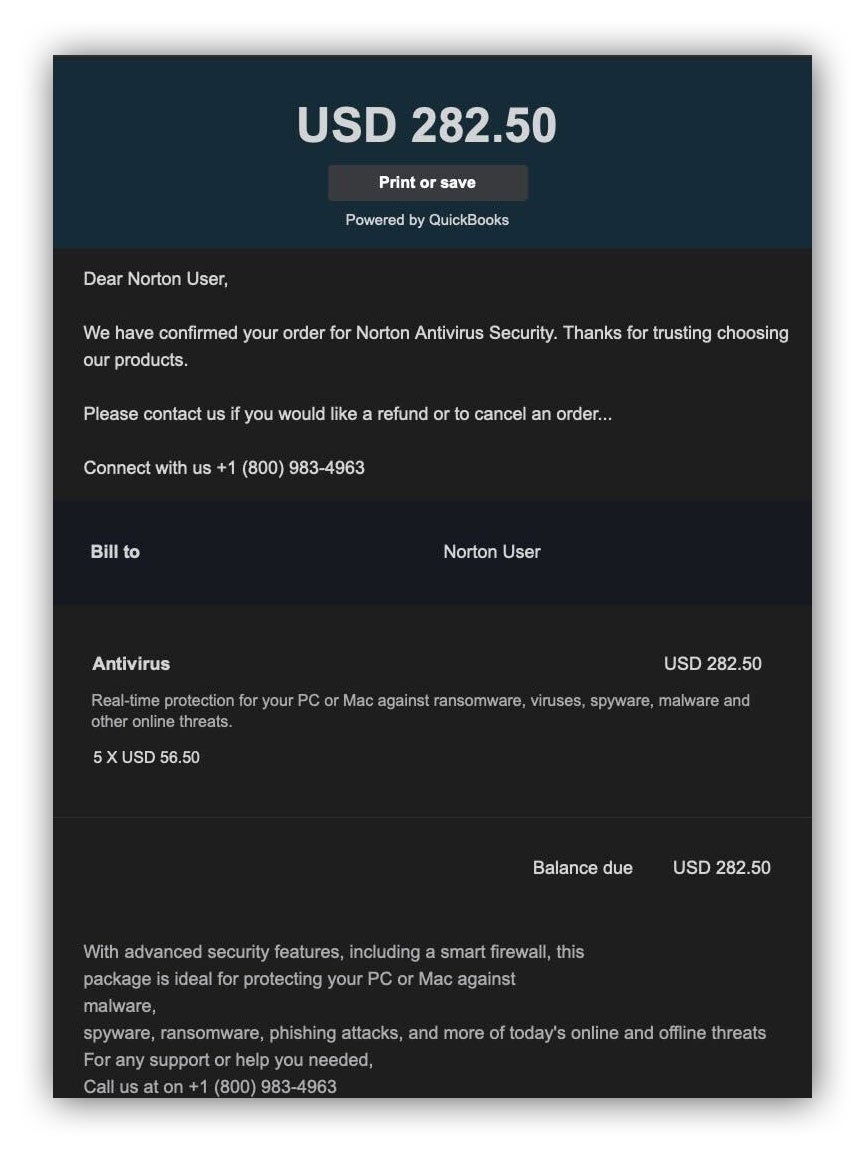
Fake Norton invoices
We noticed an increase in the number of emails containing bogus Norton invoices for Norton Antivirus software purchases.
The invoices generally include a phone number to call if you have questions about your recent transaction. These emails usually come from spoofed sender addresses that appear as if they’re from Norton Security or other legitimate businesses that sell Norton Security products, like GeekSquad. We’ve also seen threat actors use the QuickBooks platform to give the email legitimacy.
Threat actors aim to persuade recipients to call the phone number provided, then plan to scam victims out of money by requesting a payment method for the invoiced amount. They also may try to make recipients install third party remote tools that grant access to their computers.
CEO impersonation
Because info about CEOs is usually widely available online, CEO impersonation is a common occurrence and effective tactic for attackers. Most CEO impersonation email submissions convey a sense of urgency in the email’s body and subject.
Here are a few phrases that we’ve come across:
Email subject:
- “URGENT”
- “Confidential”
- “available ?”
- “Quick Response”
Email body:
- “Do you have some spare time to handle a quick task?”
- “Email me on here once you get this”
- “I need a task done ASAP and look forward to my text”
- “Your immediate response will be highly appreciated”
Impersonation emails also tend to spoof an external account to make it seem like the email is coming from the organization’s CEO. Attackers then often like to move the conversation away from email to lower the chance of being discovered. Asking for cell phone numbers allows them to use calls or texting for further interactions. Threat actors will usually ask victims to purchase gift cards and send pictures of the redemption codes.
Resilience recommendations
- Conduct regular security awareness training for employees, including phishing simulations.
- Don’t click on any links in a potentially suspicious email.
- Double check the sender’s address and return path for suspicious emails.
- Use open source tools to verify if a provided phone number is actually associated with the supposed sender.
- Block access to malicious websites.
- Use a verified internal channel (for example, a phone call to a verified company phone number or a message on your company’s internal messaging platform) to confirm if the communication/request in the email is legitimate and expected.
- Remove the email from a user’s inbox if it’s determined to be a phishing attempt.
Takeaways
Phishing remained in the top spot for infection vectors in January, but we also saw a wide variety of malware and an old friend – the USB flash drive threat – make a return.
While many of us may assume the days of bumping into a random flash drive in the office parking lot are over, these devices remain a target for threat actors. It’s important to remember that USB devices allow threat actors to use a variety of malware families to gain access to additional systems. Many malware variants can continually search an infected system for connected external USB storage devices and infect them, as well. Companies should have security controls in place to block endpoint users from inserting USB flash drives previously connected to personal assets into company assets, and only allow approved storage devices for company assets.
Speaking of malware, we also saw a range of malware families this month, identifying 11 families across payloads for incidents we responded to. And no single family made up more than 15 percent of the total number of malware samples. We also identified a malicious Chrome browser extension and artifacts from a ransomware sample. With such a variety of tools at their disposal, attackers are clearly deploying a variety of tactics to achieve their goals.
While these malware families used different obfuscation and payload stages, the most common end goal was establishing a command and control network communication channel back to the attacker. Companies should make sure that they have complete coverage of their endpoint security controls across all of their devices, and consider subscribing to OSINT malware feeds.
Phishing remains as effective of a tactic as ever, with two particularly notable trends in January. Threat actors are sending convincing Norton Antivirus invoices to trick users into paying them. This social engineering scheme continues over the phone after users who received the email call the number provided, when threat actors will typically request payment information.
Threat actors are also sending fake emails appearing to come from a company’s CEO. These emails rely on urgency to hopefully prevent targeted employees from taking the time to verify features of the email that would point out it isn’t legit. It’s essential to regularly conduct security awareness training for employees to help them identify indicators of a phishing attempt.
We’ll be back with insights on February’s top attack vectors. In the meantime, have questions about this month’s data or what it means for your org? Drop us a note.