Get technical
Product | 5 min read
How we use the Autotune algorithm in API pollingAutotune optimizes API data ingestion to improve polling efficiency and speed, resource consumption, and network request performance.
Threat intel | 4 min read
Expel Quarterly Threat Report, Q3 2025: Q3 by the numbersPart I of our Quarterly Threat Report summarizes key findings and stats from Q3 of 2025. Learn what to focus on right now.
Threat intel | 17 min read
The history of AppSuite: the certs of the BaoLoader developerWe're tracking the malware BaoLoader and their fraudulent code-signing certificates via AppSuite-PDF and PDF editor campaigns.
Threat intel | 5 min read
Expel Quarterly Threat Report, Q2 2025: Q2 by the numbersPart I of our Quarterly Threat Report summarizes key findings and stats from Q2 of 2025. Learn what to focus on right now.
Threat intel | 6 min read
Following the spiders: Investigating Latrodectus malwareLatrodectus malware is the latest infostealing malware on the market utilizing the ClickFix technique. Here's what you need to know.
MDR | 6 min read
Scaling detection: When 1 + 1 = 3 (grouping IPs to find bad actors across orgs)Here's an overview of how at Expel, we group large data sets via IP information to identify bad actors working across multiple customers.
Threat intel | 4 min read
MDR insights: Malware trends from the Q1 QTRDive into the malware data our SOC collected via incidents from Q1 2025. Here's what you should know, and how to defend against it.
Threat intel | 5 min read
Expel Quarterly Threat Report, Q1 2025: Cloud infrastructure trendsVolume IV of our Q1 2025 Quarterly Threat Report summarizes key findings for cloud infrastructure. Learn what to focus on right now.
Threat intel | 3 min read
Expel Quarterly Threat Report, Q1 2025: Endpoint threatsVolume III of our Q1 2025 Quarterly Threat Report summarizes key findings for endpoint threats. Learn what to focus on right now.
Threat intel | 5 min read
Expel Quarterly Threat Report, Q1 2025: Cloud-based service trendsVolume II of our Q1 2025 Quarterly Threat Report summarizes key findings for cloud-based services. Learn what to focus on right now.
Cloud security | 3 min read
Comparison of cloud resources (part IV): Making a roadmap for cloud securityThis is part four of our four-part blog series on comparing cloud resources. Part four covers the roadmap for cloud security.
Cloud security | 14 min read
Comparison of cloud resources (part III): Demystifying cloud security tools in the platform and application layerThis is part three of our four-part blog series on comparing cloud resources. Part three defines tools used in the platform and app layers.
Data & research | 8 min read
Key findings generation with GenAIAt Expel, we AI Responsibly. Our latest project focused on generating key findings (KF) to detail incident investigations.
Cloud security | 8 min read
Comparison of cloud resources (part II): Demystifying cloud security toolsThis is part two of our four-part blog series on comparing cloud resources. Part two defines the types of tools used for cloud security.
Threat intel | 5 min read
MDR insights: Tracking lateral movement in a Windows environment (part 2)This is part two of a pocket guide created by Expel's SOC analysts to track and identify lateral movement within your Windows environments.
Cloud security | 5 min read
Comparison of cloud resources (part I): Securing every layer of your cloud—from the control plane to appsThis is part one of our four-part blog series on comparing cloud resources. Part one covers the layers of the cloud infrastructure.
Data & research | 2 min read
It’s here: Expel’s 2025 Annual Threat ReportThis year’s Annual Threat Report describes the major attack trends we saw last year, advice to safeguard your org, and predictions for 2025.
Cloud security | 8 min read
Cloud security: alert best practices (part II)This is part two of a two-part blog on cloud security alerts, including what makes them unique and best practices for management.
Cloud security | 8 min read
Cloud security: alerts vs. on-prem alerts (part I)This is part one of a two-part blog on cloud security alerts, including what makes them unique and best practices for management.
Threat intel | 7 min read
MDR insights: Tracking lateral movement in a Windows environment (part I)This is a pocket guide created by Expel's SOC analysts to track and identify anomalous lateral movement within your Windows environments.
Cloud security | 6 min read
Part II: Fundamentals of Kubernetes securityLearn about the fundamentals of Kubernetes, including the four Cs of Kubernetes security and how Expel can help protect it.
Cloud security | 8 min read
Part I: Fundamentals of Kubernetes securityLearn about the fundamentals of Kubernetes, including its architecture, challenges, and false positives in part one of this two-part blog series.
Data & research | 8 min read
MDR insights: defense against persistent threats and Oracle WebLogic CVE-2020-14882Initial access broker (IAB) Magnet Goblin is currently targeting CVE-2020-14882 in Oracle WebLogic. Here's how to identify and stop them.
Data & research | 5 min read
Expel Quarterly Threat Report Q3 2024, volume V: Preparing for software supply chain riskVolume V of our Q3 2024 Quarterly Threat Report focuses on preparing for software supply chain risk. Learn what to focus on right now.
Data & research | 3 min read
Expel Quarterly Threat Report Q3 2024, volume IV: Suspicious infrastructure from phishing-as-a-service (PhaaS) platformsVolume IV of our Q3 2024 Quarterly Threat Report focuses on phishing-as-a-service (PaaS). Learn what to focus on right now.
Data & research | 4 min read
Expel Quarterly Threat Report Q3 2024, volume III: Malware trendsVolume III of our Q3 2024 Quarterly Threat Report focuses on malware trends. Learn what to focus on right now.
Data & research | 4 min read
Expel Quarterly Threat Report Q3 2024, volume II: CAPTCHA trick or treatVolume II of our Q3 2024 Quarterly Threat Report focuses on malicious CAPTCHAs. Learn what to focus on right now.
Data & research | 5 min read
MDR insights: using vulnerability data to inform remediation strategiesMDR vulnerabilities data can be used with EPSS scoring and the CISA catalog to glean insights, reduce alert noise, and guide remediation.
Data & research | 3 min read
Expel Quarterly Threat Report volume V (Q1 2024): authentication bypass vulnerabilitiesIn volume V of our Q1 2024 QTR, we cover authentication bypass vulnerabilities. Here's what our SOC found and what you should know.
Data & research | 3 min read
Expel Quarterly Threat Report volume IV (Q1 2024): suspicious authentication sourcesIn volume IV of our Q1 2024 QTR, we're covering suspicious authentication sources. Take a look at what our SOC saw to learn from it.
Data & research | 2 min read
Expel Quarterly Threat Report volume III (Q1 2024): high-risk malwareNext up in our Q1 2024 QTR series, we examine high-risk malware incidents. Here's what our SOC learned, and how you can remediate.
Data & research | 2 min read
Expel Quarterly Threat Report volume II (Q1 2024): attackers and AINext up in our Q1 2024 QTR: check out these examples of attackers using AI to advance their goals. Learn what to focus on right now.
Data & research | 3 min read
Expel Quarterly Threat Report volume I (Q1 2024): Q1 by the numbersVolume I of our Quarterly Threat Report summarizes key findings and stats from Q1 of 2024. Learn what to focus on right now.
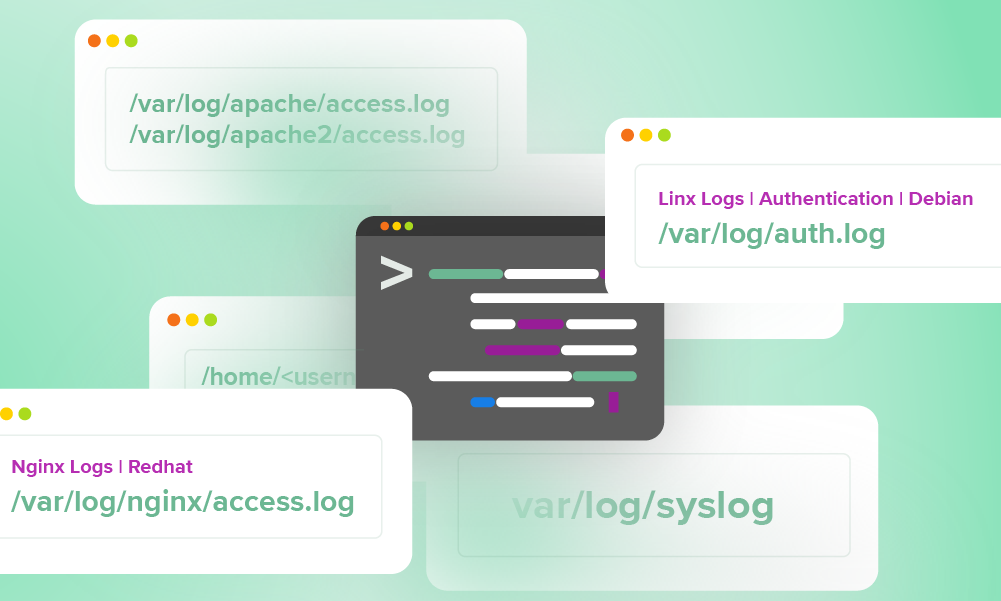
SOC | 7 min read
Logs your SOC can use every day: a quick reference guideWe pulled the logs our SOC team use daily into a handy quick reference guide for our analysts—and now, you.
Data & research | 3 min read
2024 Annual Threat Report: findings and predictionsThis year’s Annual Threat Report shares the major attack trends from last year, advice to secure your org, and predictions for 2024.
Company news | 2 min read
Oh Noes! Our IR tabletop game is new and improved!Oh Noes! is our incident response game (like D&D). You’ll create characters and role-play cybersecurity incidents specific to your org.
Data & research | 2 min read
Cyberattackers evolve: the Quarterly Threat Report for Q2 2023Our Q2 2023 Quarterly Threat Report examines the rise of commodity malware, AiTM phishing techniques, and the impact of software vulnerabilities.
Data & research | 2 min read
Top three findings from Q1 2023 Quarterly Threat ReportHackers use the same methods because they’re still effective. Expel’s Q1 Threat Report reveals gaps in your security and how to close them.
Data & research | 2 min read
2023 Great eXpeltations report: top six findingsThe Great eXpeltations Report is here. Learn about the biggest threats our SOC team saw in customer environments last year, and get expert insights to stay safe.
Cloud security | 5 min read
Understanding role-based access control in KubernetesUnderstanding authorization is critical to securing Kubernetes. Learn how RBAC works and the rules that govern your access control.
Cloud security | 3 min read
Three Kubernetes events worth investigatingMonitoring your Kubernetes environment? Learn what to look for and how to use audit logs to secure your production workloads.
Product | 2 min read
Cutting Through the Noise: RIOT Enrichment Drives SOC ClarityCut through the noise in your SOC with RIOT enrichment. Also known as the rule-it-out enrichment, see how it works.
Product | 5 min read
Detecting Coin Miners with Palo Alto Networks NGFWWorried about cryptojacking? Learn how we use a Palo Alto Networks firewall to detect it and how our bot automates a response to help.
Data & research | 2 min read
Great eXpeltations 2022: Cybersecurity trends and predictionsWhat are the biggest threats of 2022? Our Great eXpeltations report shares cybersecurity trends and SOC predictions, with actionable advice.
MDR | 9 min read
Well that escalated quickly: How a red team went from domain user to kernel memoryA red team deployed a custom rootkit via PowerShell. Find out how we spotted the crafty tactics and successfully defended the network.
Cloud security | 11 min read
Migrating to GKE: Preemptible nodes and making space for the Chaos MonkeysSee how Expel's internal teams migrated our core infrastructure to GCP with zero downtime. Learn the strategy behind the successful move.
Data & research | 8 min read
Containerizing key pipeline with zero downtimeMigrating to Kubernetes with zero downtime is a tall order. See how Expel’s engineers pulled it off without interrupting analyst workflow.
Data & research | 7 min read
Plotting booby traps like in Home Alone: Our approach to detection writingHow do D&R engineers think about detection writing? Learn their process for creating alerts that help SOC analysts make smarter decisions.
Data & research | 6 min read
Prioritizing suspicious PowerShell activity with machine learningAttackers use PowerShell for malicious plans. See how our senior data scientist used machine learning to quickly spot the activity.
Product | 6 min read
How to create and maintain Jupyter threat hunting notebooksAfter Infosec Jupyterthon 2020, we answer your top questions about configuring Jupyter notebooks. Get tips for infosec processes.
MDR | 9 min read
Obfuscation, reflective injection and domain fronting; oh my!A CrowdStrike EDR alert flagged a suspicious VBScript file during a red team engagement. See what our SOC learned from the malware code.
Product | 3 min read
Where does Amazon Detective fit in your AWS security landscape?Running workloads on AWS? Get up to speed on the latest and greatest AWS-native security tools in our newest post.
Product | 8 min read
Using JupyterHub for threat hunting? Then you should know these 8 tricks.Jupyter Notebook gave us the freedom to rethink the way we analyzed hunting data. Here are some tips and tricks you can use in your own analysis.
Cloud security | 5 min read
Making sense of Amazon GuardDuty alertsRunning AWS workloads? You need GuardDuty. Get our pro tips on what it is and how to make sense of all its security signals.
Product | 5 min read
Better web shell detections with Signal Sciences WAFIs Signal Sciences WAF part of your tech stack? Then you’ve got an amazing webshell detection method right at your fingertips.
MDR | 4 min read
Does your MSSP or MDR provider know how to manage your signals?How well is your MSSP or MDR going to manage your fleet of security signals over time? Here’s how to figure out whether they’re up for the challenge.
Cloud security | 7 min read
How to build a useful (and entertaining) threat emulation exercise for AWSWant to test your analysts’ detection skills in the cloud? Here are our tips and tricks for building your own threat emulation exercise in AWS.
Data & research | 6 min read
Five tips for improving your data ingestion and auditing processYou’re processing loads of data every day...but are you catching it all? Here are tips from our pros for rocking your data auditing.
Cloud security | 8 min read
How to find Amazon S3 bucket misconfigurations and fix them ASAPWhy do Amazon S3 bucket breaches happen? Get the AWS pro tips you need to protect your org from making this costly mistake.
Product | 6 min read
Evaluating GreyNoise: what you need to know and how it can help youBoost analyst efficiency! Learn why GreyNoise is a key technology used behind the scenes to enhance Expel Workbench and our analysts' work.
MDR | 10 min read
Seven ways to spot a business email compromise in Office 365Protect your Office 365 from BEC scams. Learn what Business Email Compromise is and get examples of mailbox rules for prevention.
MDR | 8 min read
Why we love threat emulation exercises (and how to get started with one of your own)If your team doesn’t have lots of incident response practice under their belt (yet!), a threat emulation exercise is the perfect way to help them flex.
MDR | 4 min read
Five quick checks to prevent attackers from weaponizing your websiteHere are some of the most frequent ways attackers can use your website and your web presence to harm your company, your users and the public at large.
SOC | 8 min read
What “I Love Lucy” teaches us about SOC performanceA little nerdy (and a lot math-y) post to help you better understand your SOC's systems, so you know how changes will impact its operation.
MDR | 7 min read
From webshell weak signals to meaningful alert in four stepsStop wasting time on weak security signals. Learn how to combine endpoint and network events for a single, actionable alert.