Security operations · 3 MIN READ · AARON WALTON · APR 18, 2024 · TAGS: MDR
Our new Quarterly Threat Report (QTR) blog series for Q1 covers a lot of ground. So far, we gave you our top takeaways up front with Q1 by the numbers (volume 1), dug into how we see attackers using AI (volume II), and left off with our take on the rise of high-risk malware (volume III).
But our Q1 QTR wouldn’t be complete without an analysis of identity-related incidents. In the context of this series, identity-related incidents refer to attackers attempting to gain access to a user’s identity to perpetuate fraud. Take a look at some of the attacks our security operations center (SOC) team saw this quarter, emerging trends, and steps you can take to protect your org.
Identity-based threats and suspicious authentication sources
It isn’t a surprise to us–and probably not a surprise to you if you follow our publications–but identity-related incidents continue to be the top threat facing our customers. The IC3 reported business email compromise (BEC) as causing $2.9 billion USD of damages in reported crimes in 2023. (I.e., these threats can cause real financial damage.)
To better mitigate these threats, we monitor the trends associated with malicious logins. Over the course of 2023, actors attempting credential theft started to heavily use adversary-in-the-middle (AiTM) techniques. These techniques enable the threat actor to leverage a credential harvester to capture login credentials and bypass multi-factor authentication (MFA). Many of these credential harvesters are dynamic and well designed: they’re able to load the branding associated with the targeted victim, and also present the expected MFA method—such as a push verification or an authentication code. These features help set the trap, making it appear authentic.
How to protect your org:
MFA prevents attackers from gaining access to your environment with a password alone, but threat actors are adapting. Include additional restrictions to increase security, such as requiring authentication from managed devices (limiting logins from unknown devices).
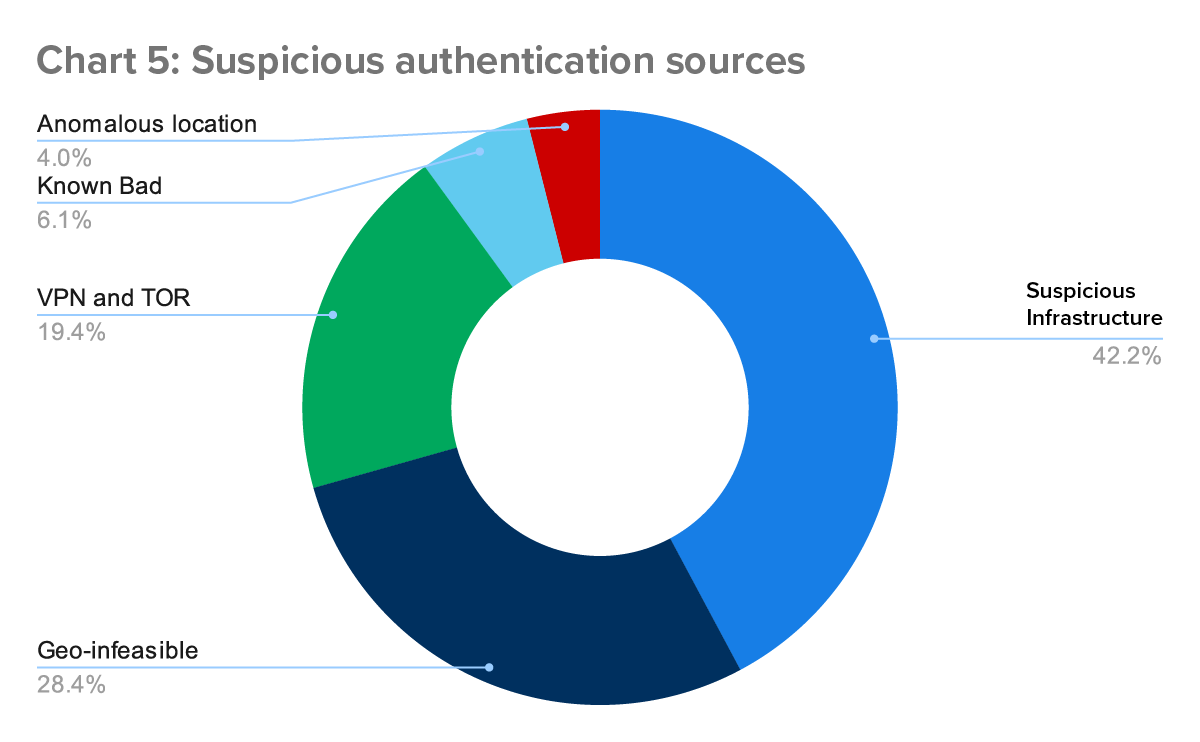
After successfully stealing a user’s credential, actors attempt to login to the account and begin whatever malicious activity they have in store. In the last quarter, actors logged in from the following sources: Suspicious Infrastructure (such as hosting providers); geo-infeasible locations, using VPNs or TOR, from known bad IP addresses and from anomalous locations, such as locations eerily close to the victim. We break down the numbers below (Chart 5).
Most frequently (42%), attackers leveraged hosting providers when accessing victim accounts. These hosting providers offer Virtual Private Servers (VPS), and attackers use these to proxy their traffic. The ease and relative anonymity virtual servers provide makes this a common tactic.
The providers range from lesser-known entities (such as Clouvider and GhostVPS) to the well-known (such as Azure and Amazon). The use of a VPS allows an attacker to distance themselves from the IP address associated with the login, helping them stay anonymous. The server locations can also help the attacker make their login appear to be from a closer and less suspicious location, making geolocation and regional based detections less effective. Some business partners and SaaS solutions may use these same providers, making activity from those providers even less anomalous.
But attackers hide their location in other ways, too. In 19% of incidents, threat actors leveraged VPNs and TOR routing to disguise their location. With VPNs and TOR, attackers can set their location to a country or region more consistent with the victim they are targeting. In another 4% of incidents, attackers used residential proxies—infected devices, such as home computers or phones, that an attacker can use like a VPN to hide their traffic.
Even though threat actors have the means to disguise themselves, suspicious locations are still an important indicator of malicious activity. In fact, we identified 28% of incidents because the attacker’s geolocation differed substantially from the victim’s expected location.
Stay tuned as we wrap up this series with our Quarterly Spotlight, exploring the danger of authentication bypass vulnerabilities. If you have questions or want to keep the conversation going, feel free to drop us a line, any time.
Q1 QTR series quick links
Check out the other blogs in the series for more of our Q1 findings: