Security operations · 2 MIN READ · AARON WALTON · APR 17, 2024 · TAGS: MDR
Thus far in our Quarterly Threat Report (QTR) blog series, we covered our top takeaways from the first quarter (Q1) of 2024 in volume I: Q1 by the numbers. In volume II, we dug deeper into attackers using AI for social engineering attacks, including the growing threat of Deepfake technology.
Our series continues with a look at high-risk malware incidents—from what our security operations center (SOC) team saw, to attack trends and recommendations you can take to protect your org.
Increased prevalence of high-risk malware
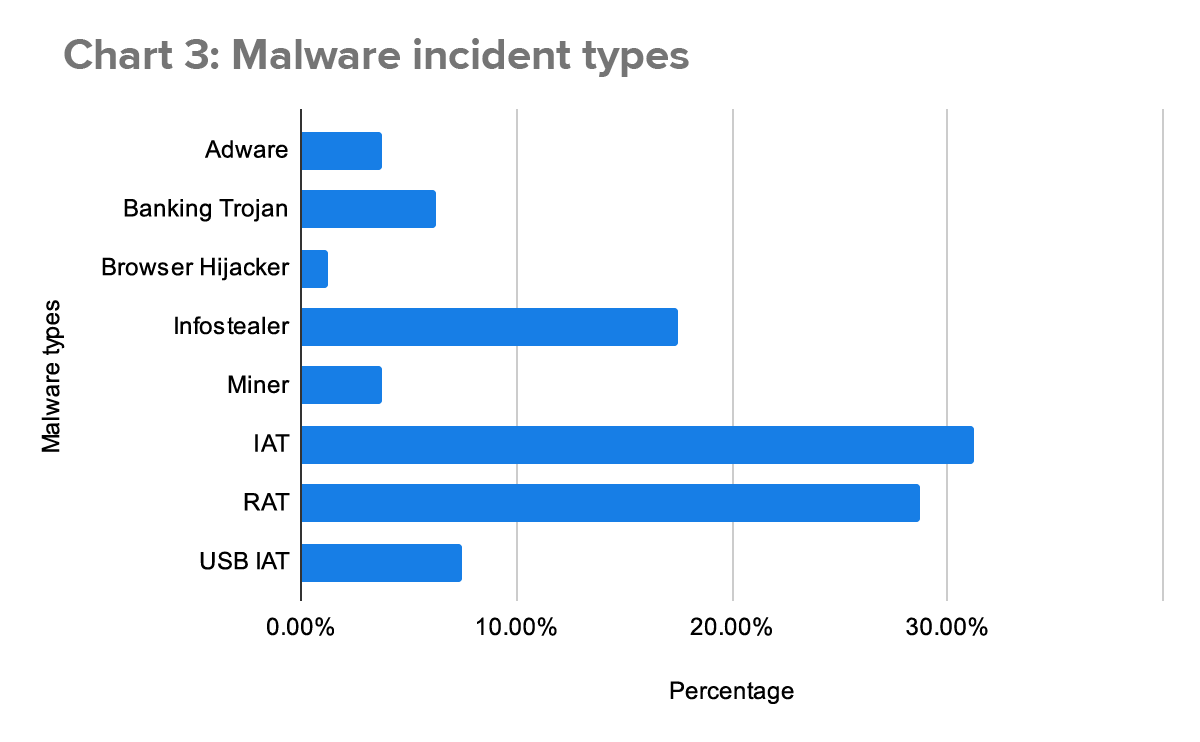
This quarter, high-risk malware made up 67% of malware incidents. This is up from about 50% in Q4 of 2023.
We consider malware high-risk when we know it’s leveraged by ransomware actors, or the malware provides a high degree of access to a victim’s computer or network. In the following breakdown, the USB Initial Access Tools (USB IATs), Remote Access Tools (RATs), and other IATs are the malware we consider high-risk. The remaining categories are considered latent risk: that is, while they introduce risk, the threat is not immediate. (Read a more in-depth discussion of these categories in our 2023 Q3 report and most recent annual threat report.)
Threat actors and file types
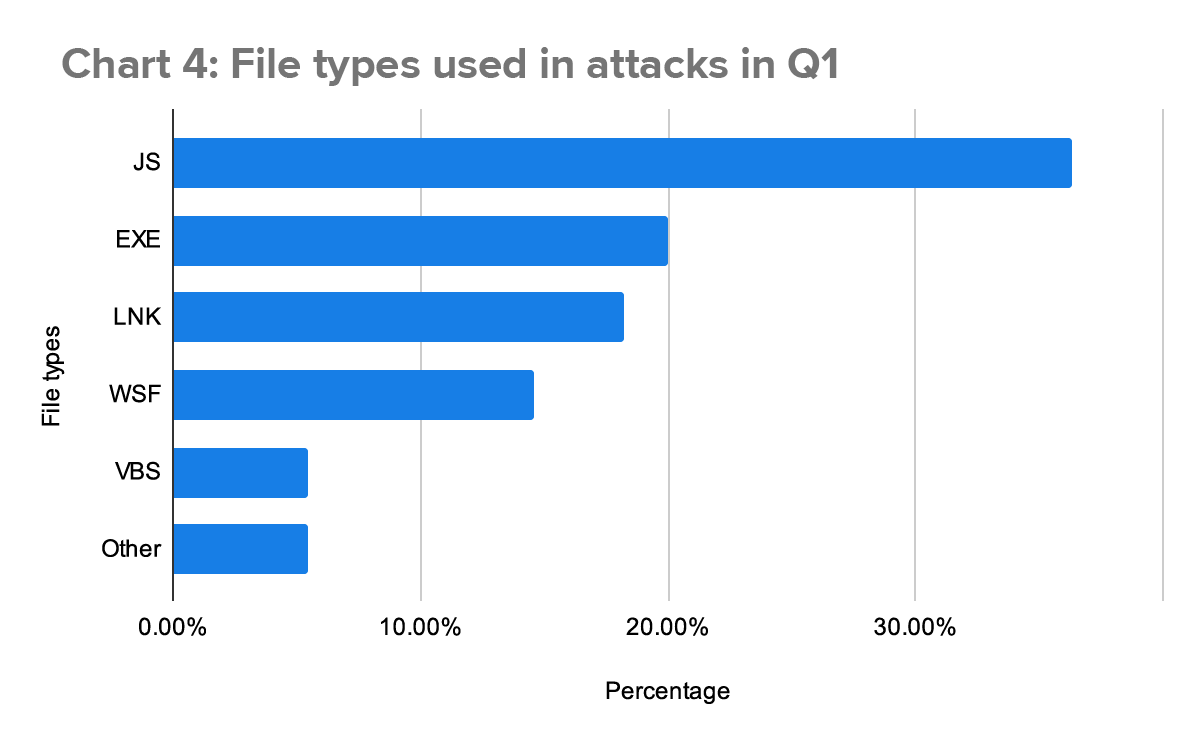
We track which threat actors target our customers’ environments to better enhance our detection strategy, as well as to make resilience recommendations to help our customers continuously improve. The majority of high-risk malware threats continue to use JavaScript to gain access to a device. These attackers often use infected websites to deliver downloads of the JavaScript files and when a the files are clicked, Windows executes them with the WScript application by default—making them dangerously easy to execute.
How to protect your org:
Use tools like Secure Web Gateways to block domains the first time they appear in your environment. Attackers using malware dropper sites often try to prevent investigators from visiting a website, so they block multiple visits. Blocking uncommon websites the first time they appear can stop the malware download in the first place.
The three primary threat actors leveraging JavaScript files this quarter were SocGholish, GootLoader, and ZPHP. Each of these actors use JavaScript to gain an initial foothold in the environment before they attempt to download additional payloads—they’re also known to sell access to infected hosts to ransomware actors.
Next up in this series: we dig into identity-based attacks and authentication sources. Questions about how Expel can help protect your organization from high-risk malware? Drop us a line.
Q1 QTR series quick links
Check out the other blogs in the series for more of our Q1 findings: