Auto remediation
Reduce time to resolution but still control who, when, and why
What is auto remediation anyway?
In broad terms, it entails using tools capable of identifying and resolving cybersecurity concerns such as misconfigurations, threats, vulnerabilities, and the like, all without requiring human intervention.
Woah. Give up (some) control to automated remediation?
We get it. It’s smart to be cautious of a new approach. A lot of security practitioners who’ve purchased MDR services still want to maintain internal control of remediation steps. Why use Expel to auto remediate?
- Personalized to your org. You decide what resources we’ll remediate on your behalf.
- Stay protected. Coverage across all attack surfaces 24×7.
- Save time. Creates space and time to breathe during an incident.
- Focus on other initiatives. Creates space by automating repetitive tasks so your team can focus on other initiatives.
Why did we do it?
It all comes down to speed and latency. The faster you remediate, the better the outcome.
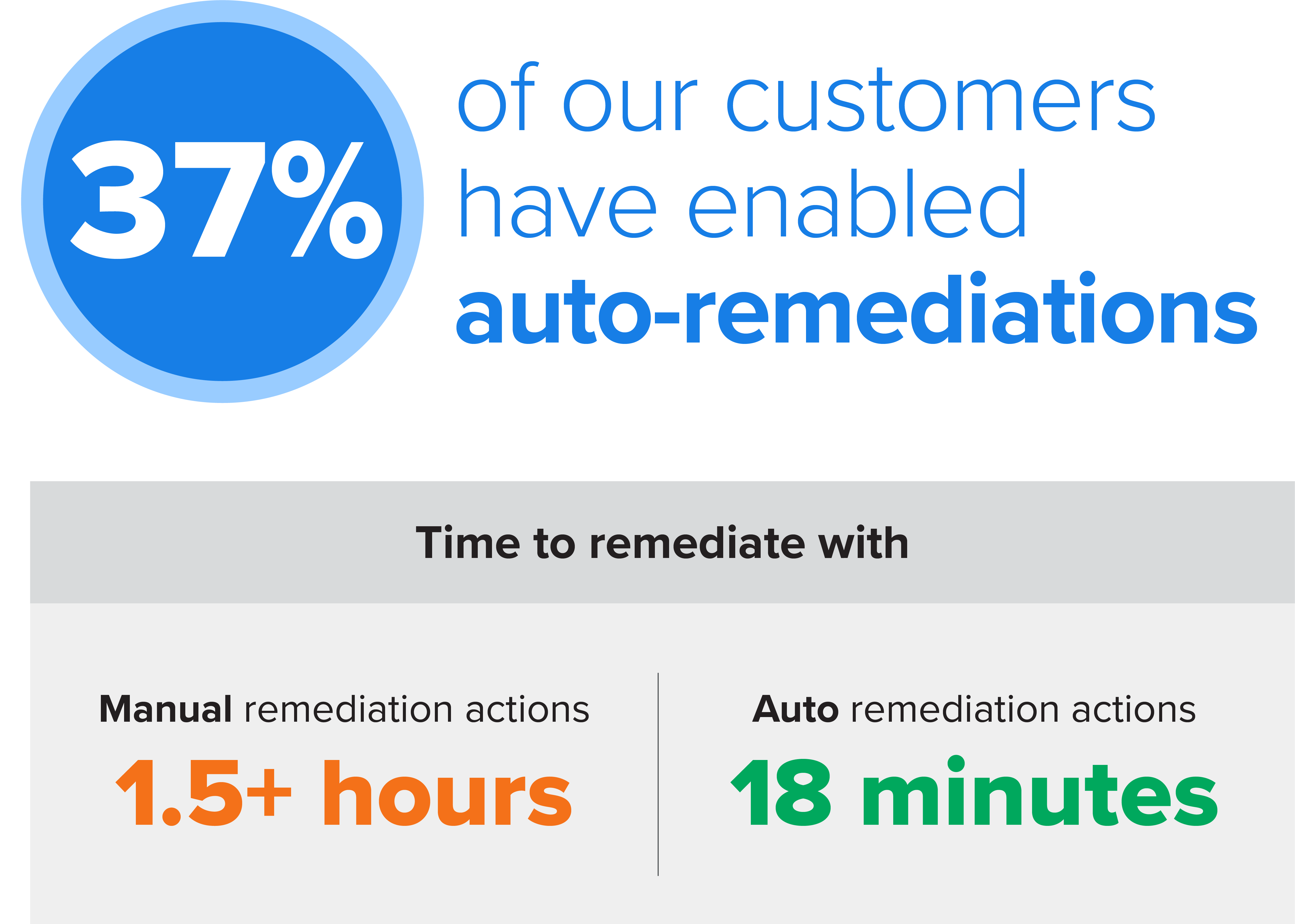
Peace of mind is nice. We tell you what to fix or fix it for you.
What can we auto remediate?
From business email compromise, to malicious files, to ransomware, we’ve got you covered. You tell us what you’d like us to remediate and which ones you’d prefer to handle.
With 24×7 coverage, you have the time to plan your next steps…even if that means waiting until Monday morning.
Our approach to automated remediation is personal to your organization and based on the frequency of threats seen in your environment. You’re in control of which users and endpoints you’d like us to immediately take offline after a compromise is confirmed. So you’re involved when you want to be. This means your team can focus on other security initiatives—without spending a ton of time on remediation