Solutions
Protect my SaaS apps
24x7 monitoring and response for Microsoft 365, G Suite and more
Overview
Protecting your SaaS apps is overwhelming
“Last year, the average number of SaaS apps used per organization stood at 80.” – Exploding Topics, August 2022
These applications house a ton of important data. And as your cloud environment grows and gets more complex, risk increases. Understanding your users’ behavior is critical in securing your SaaS apps. And you can’t assume what’s normal for one role is the same for another—it can change from app to app.
With an increasing number of SaaS apps, users, and access patterns, how can you keep up? How do you know who, what, where and how? We can help.
What are your organization’s SaaS protection challenges?
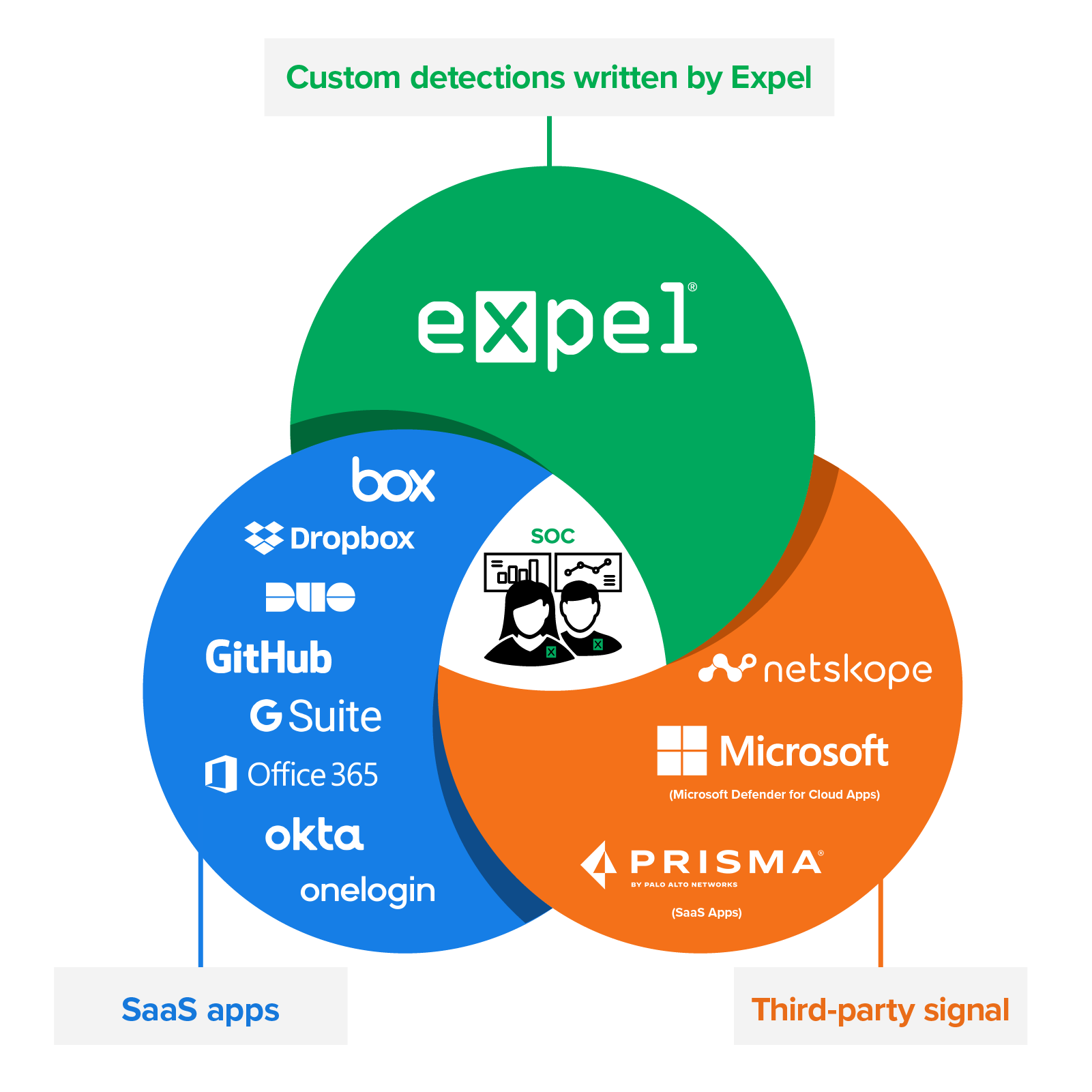
Expel customized detection and response for SaaS apps
We’ve got you covered when it comes to protecting SaaS apps. And we’ve done it a lot, with Google Workspace, Microsoft 365, Duo, Okta, Dropbox, OneLogin, Github, and Box, to name a few (and with more to come).
We alert on things unique to your business so that you know the first signs of abnormal user activity. Our detection and response strategy is built specifically for each app. Our analysts are trained on how to investigate incidents that originated from there—we look for suspicious user activity, network activity, authentications, file events, and process events. We’ll tell you when we spot risky behavior, investigate and provide you with next steps or we can auto-remediate for you (just say the word).
Alert-to-remediation in 21 minutes. You read that right.
Results. Not more alerts to handle.
See Expel SaaS protection in action
Our detection strategies are tailored for each SaaS app. For example, for Microsoft 365 we can apply our detection strategy to detect things like authentication from a suspicious country, authentication via Tor node, MFA bypass, Azure AD conditional access policy update, global admin access to Powershell, and many more. Need to map detections to MITRE ATT&CK tactics? We do that too! This custom strategy means you only get prioritized Expel-treated alerts for the critical SaaS apps in your environment. This way, you, or we, can remediate quickly. Here’s some things you can expect when working with Expel:

Reduce response times
Use automation for initial triage so our analyst can focus on spotting suspicious behavior.

Boost visibility
Detections unique to each of your apps like Microsoft 365, Okta and Dropbox.

Stop threats from spreading
When we identify a compromised user, we’ll automatically disable the account.

Keep your people secure
Prioritize alerts based on key assets and users.