Guidance
SOC | 7 min read
Why building a 24×7 SOC is getting harder (and what actually works instead)The math on building an in-house SOC has changed, including the real costs, why retention is brutal, and what actually works.
MDR | 3 min read
DORA and NIS2: what you need to know about today’s cybersecurity regulationsTwo new EU regulations—the Digital Operational Resilience Act (DORA) and Network and Information Security Directive 2 (NIS2)—are in effect.
MDR | 5 min read
Network and Information Security Directive (NIS2) compliance for businessesHere's what to know about the Network and Information Security Directive (NIS2), a new cybersecurity standard for EU essential services.
MDR | 6 min read
How the Digital Operations Resilience Act (DORA) will affect your businessHere's what you should know about The Digital Operations Resilience Act (DORA), a new cybersecurity standard for financial orgs in the EU.
Threat intel | 3 min read
Expel Quarterly Threat Report, Q3 2025: Threat intel recapHere's a refresher on the threat intel we shared throughout the third quarter of 2025. Catch up on what you missed.
Threat intel | 4 min read
Expel Quarterly Threat Report, Q3 2025: Q3 by the numbersPart I of our Quarterly Threat Report summarizes key findings and stats from Q3 of 2025. Learn what to focus on right now.
Current events | 2 min read
Cybersecurity Awareness Month: Good reminders for the entire yearOctober is Cybersecurity Awareness Month. Here are four tips for staying secure this month (and the rest) at work and at home.
MDR | 5 min read
Cybersecurity myths from the depths of Reddit (that security pros want you to know about)Cybersecurity professionals often take to Reddit to share thoughts with their community. You can learn more secure practices from it, too.
Cloud security | 2 min read
Cloud Decoded (part 3): Hey CISOs, stop guessing when it comes to cloud securityPart three of our Cloud Decoded blog series focuses on what you need to know about cloud detection and response (CDR).
MDR | 7 min read
How to sell Expel MDR to your CFO: the complete guideSelling MDR to a CFO is challenging. Use numbers that matter, and be prepared for questions. This guide can help you prepare your proposal.
MDR | 4 min read
The hidden costs of ‘cheaper’ securityBeware of the hidden costs of "cheaper" security, and know what you should ask and pay attention to before switching MDR providers.
Threat intel | 5 min read
Expel Quarterly Threat Report, Q2 2025: Q2 by the numbersPart I of our Quarterly Threat Report summarizes key findings and stats from Q2 of 2025. Learn what to focus on right now.
Cloud security | 3 min read
Cloud Decoded (part 2): What attackers don’t want you to knowThis is part two of Expel's blog series on decoding the cloud. It dives in to what attackers don't want you to know.
Current events | 3 min read
What we’re seeing from Iran (and what it means for you)Here's Expel's take on what the geopolitical issues between the US, Israel, and Iran look like for the cybersecurity community to date.
MDR | 5 min read
Insights on the MDR market from the Gartner® Security & Risk SummitExpel attending the Gartner Security & Risk Summit. Here are the insights we gathered on the MDR market post-conference.
Rapid response | 2 min read
Scattered Spider’s heightened activity—here’s the 411Threat group Scattered Spider is making headlines again as they increase targeting for financial services and insurance orgs.
Current events | 4 min read
5 questions to ask when your security vendor gets acquiredWhether your MDR provider is going through a merger or acquisition, here are five questions you'll want to ask your new point of contact.
Product | 3 min read
How to onboard with Expel in 7 minutes (No, really. We’ll show you.)See with your own eyes how Expel MDR is up and running in less than seven minutes, from API connection to immediate protection.
MDR | 6 min read
Scaling detection: When 1 + 1 = 3 (grouping IPs to find bad actors across orgs)Here's an overview of how at Expel, we group large data sets via IP information to identify bad actors working across multiple customers.
Cloud security | 4 min read
Cloud Decoded (part 1): The cloud security mythbuster—what MDR really means for cloudThis is part one of Expel's blog series on decoding the cloud. The first one covers what MDR really means for cloud.
MDR | 4 min read
MDR pricing decoded: what CISOs and security directors need to knowDiscover the hidden costs behind MDR pricing models. Learn what CISOs need to know about managed detection and response pricing, per-endpoint costs, and avoiding 'free' feature traps to make informed MDR cost decisions.
Threat intel | 5 min read
Expel Quarterly Threat Report, Q1 2025: Cloud infrastructure trendsVolume IV of our Q1 2025 Quarterly Threat Report summarizes key findings for cloud infrastructure. Learn what to focus on right now.
Threat intel | 3 min read
Expel Quarterly Threat Report, Q1 2025: Endpoint threatsVolume III of our Q1 2025 Quarterly Threat Report summarizes key findings for endpoint threats. Learn what to focus on right now.
Cloud security | 3 min read
Comparison of cloud resources (part IV): Making a roadmap for cloud securityThis is part four of our four-part blog series on comparing cloud resources. Part four covers the roadmap for cloud security.
Threat intel | 5 min read
MDR insights: Tracking lateral movement in a Windows environment (part 2)This is part two of a pocket guide created by Expel's SOC analysts to track and identify lateral movement within your Windows environments.
SOC | 7 min read
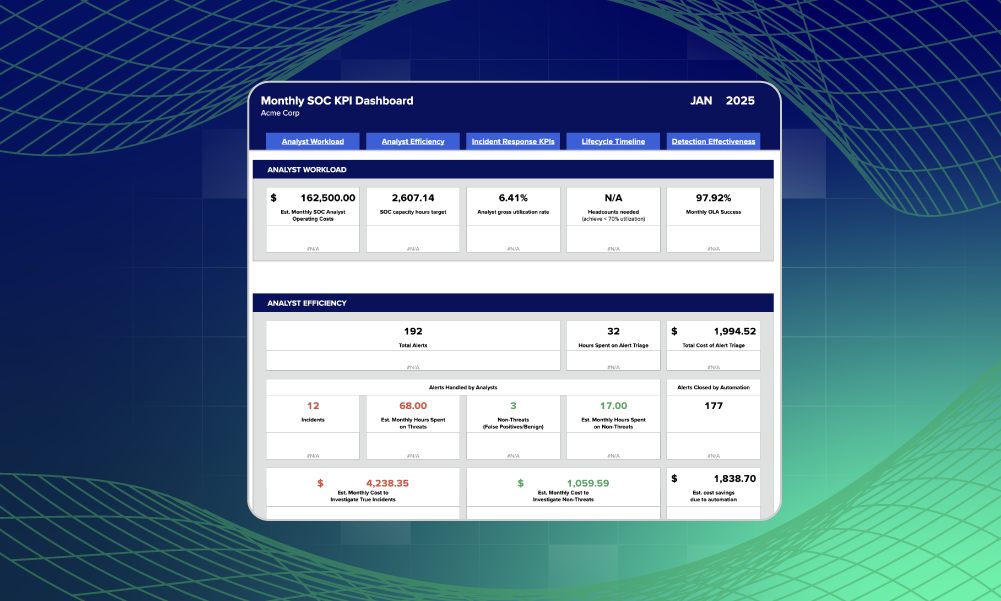
Stressed SOC? Data’s your best ally to justify more resourcesUse analyst workload metrics and efficiency KPIs data to build a business case for more SOC resources and increased budget.
Threat intel | 12 min read
Code-signing certificate abuse in the Black Basta chat leaks (and how to fight back)Ransomware gang Black Basta's chats were recently leaked, proving how they abuse code-signing certificates. Here's how to defend against it.
Cloud security | 9 min read
Vulnerability management for cloud environmentsVulnerability management in the cloud has its own unique challenges and strategies. Dive into the nuances and how Expel can help.
Current events | 2 min read
A Valentine’s Day guide to protecting your digital heartHappy Valentine's Day! Love is in the air, and unfortunately, so is cyber crime. Stay safe with these cybersecurity tips from Expel.
Threat intel | 7 min read
MDR insights: Tracking lateral movement in a Windows environment (part I)This is a pocket guide created by Expel's SOC analysts to track and identify anomalous lateral movement within your Windows environments.
MDR | 9 min read
MDR mythbusters: ten common myths, debunkedWe debunk ten MDR myths to help you make sense of the increasingly complex security landscape and understand cybersecurity alphabet soup.
MDR | 4 min read
Part I: How MDR can transform your SIEM investmentThis is part one of a three-part blog series on how MDR can transform your SIEM investment by augmenting and optimizing its capabilities.
Data & research | 5 min read
Expel Quarterly Threat Report Q3 2024, volume V: Preparing for software supply chain riskVolume V of our Q3 2024 Quarterly Threat Report focuses on preparing for software supply chain risk. Learn what to focus on right now.
Rapid response | 1 min read
Security alert: Fortinet zero-day vulnerabilityFortinet has disclosed a zero-day vulnerability that needs to be patched immediately, or the protocol connection to the internet should be disabled.
Data & research | 3 min read
Expel Quarterly Threat Report Q3 2024, volume IV: Suspicious infrastructure from phishing-as-a-service (PhaaS) platformsVolume IV of our Q3 2024 Quarterly Threat Report focuses on phishing-as-a-service (PaaS). Learn what to focus on right now.
Data & research | 4 min read
Expel Quarterly Threat Report Q3 2024, volume III: Malware trendsVolume III of our Q3 2024 Quarterly Threat Report focuses on malware trends. Learn what to focus on right now.
Data & research | 4 min read
Expel Quarterly Threat Report Q3 2024, volume II: CAPTCHA trick or treatVolume II of our Q3 2024 Quarterly Threat Report focuses on malicious CAPTCHAs. Learn what to focus on right now.
Data & research | 2 min read
Expel Quarterly Threat Report, volume I: Q3 2024 by the numbersVolume I of our Quarterly Threat Report summarizes key findings and stats from Q3 of 2024. Learn what to focus on right now.
Data & research | 5 min read
Expel Quarterly Threat Report Q2 2024 volume V: Latent-risk infostealing malwareLast up in our Q2 QTR series: we dig into infostealers and the importance of detecting, mitigating, and responding to this form of malware.
Data & research | 3 min read
Expel Quarterly Threat Report Q2 2024 volume IV: Phishing trendsPhaaS platforms make phishing easy. In this volume in our series, we share what these are, how they work, and how they can be counteracted.
Data & research | 5 min read
Expel Quarterly Threat Report Q2 2024 volume III: Malware infection trendsVolume III of our Quarterly Threat Report covers malware trends in Q2 of 2024. Learn what to focus on right now.
Data & research | 3 min read
Expel Quarterly Threat Report Q2 2024 volume II: Attackers advance with AIVolume II of our Quarterly Threat Report covers how attackers are advancing with AI in Q2 of 2024. Learn what to focus on right now.
Data & research | 3 min read
Expel Quarterly Threat Report Q2 2024 volume I: Q2 by the numbersVolume I of our Quarterly Threat Report summarizes key findings and stats from Q2 of 2024. Learn what to focus on right now.
SOC | 7 min read
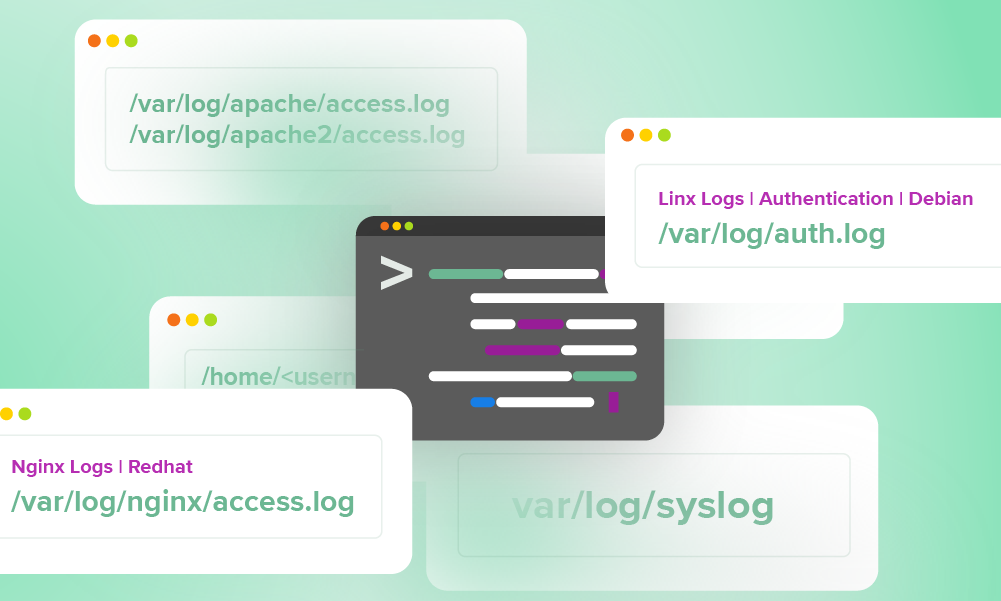
Logs your SOC can use every day: a quick reference guideWe pulled the logs our SOC team use daily into a handy quick reference guide for our analysts—and now, you.
MDR | 3 min read
No honor among ransomware criminalsTake steps to assess your org’s security now, so you can protect yourself from ransomware gangs like BlackCat.
Current events | 1 min read
GKE/Gmail vulnerability: notes and tipsSecurity researchers have discovered a new Google Kubernetes Engine misconfiguration. Here’s what you need to know.
MDR | 6 min read
Assessing suspicious Outlook rules: an exerciseOutlook Inbox rules are used for legitimate and malicious reasons. Use these case exercises, tips, and tricks on how to analyze them.
SOC | 5 min read
Work with your SOC/MDR in a cybersecurity risk assessmentThere are different kinds of security assessments, and what you perform should be aligned to your organization's goals.
MDR | 3 min read
When does an org need to up its cybersecurity game?Every company must have an acceptable level of security to earn customer and partner trust as it grows. How do you know when you're there?
Product | 3 min read
Following the lifecycle of a cloud alert in Expel WorkbenchOur tour shows you the journey a cloud alert takes in Expel MDR for cloud infrastructure, in a single or multi-cloud environment.
Rapid response | 1 min read
Security alert: privilege escalation vulnerability in Confluence Data Center and Server, CVE-2023-22515Here's how to mitigate a Confluence Data Center and Server vulnerability that lets attackers create admin accounts on external-facing servers.
Rapid response | 1 min read
Security alert: zero-day vulnerability CVE-2023-4863 in libwebp (WebP) libraryCVE-2023-4863 is a zero-day vulnerability in libwebp, which can result in arbitrary command execution when exploited. Here’s why it matters and what to do.
MDR | 6 min read
Wake me up, before you log-log (…or when September ends, whichever comes first)Logs are a necessary and useful component in any cybersecurity practice, but when and how you use them can significantly change your security outcomes.
MDR | 3 min read
Red team sneakiness: Splunking for AD certificate abuseRecently we saw a red team operation which included attacks against Active Directory. Here’s how we solved the mystery.
Current events | 4 min read
AiTM attacks and business email compromise attacks: what to watch forAttackers commonly defeat MFA by using credential harvesters for an AITM attack. Here's advice on how to short-circuit it.
Current events | 2 min read
Addressing the new SEC cyber incident disclosure rulesHere's what to know about new SEC rules requiring publicly traded companies to disclose material incidents from cyberattacks within 4 days.
MDR | 2 min read
Threat hunting basics: understanding key principlesThreat hunting basics—continuous monitoring, intel-driven, hypothesis testing, and collaboration—help you detect and smother threats faster.
MDR | 2 min read
Vulnerability management, prioritization, and assessment: what’s the difference?Prioritize vulnerabilities effectively. Learn how management covers the full lifecycle and why prioritization is key to reducing your risk.
SOC | 2 min read
How we built it: the Expel SOC-in-the-SkyCurious what it takes to turn a hotel ballroom into a 24/7 SOC? Learn how and why we created a "SOC-in-the-Sky" for our company kickoff.
Cloud security | 3 min read
Kubernetes security checklist: what to look forLearn what to look for and get key suggestions for your future security strategy and tools with this Kubernetes security checklist.
Cloud security | 7 min read
Five common multi-cloud security challengesSwitching to multi-cloud is hard. An Expel engineer shares what you need to think about and how to stay sane during the transition.
Current events | 2 min read
BEC and a “Visionary” scamThe skepticism you use in real life applies to cybersecurity. Learn how to take your healthy doubt with you online to avoid threats.
Expel culture | 5 min read
The Security ClauseLike Santa, a new cybersecurity pro has a lot to learn. See the surprising parallels between The Santa Clause and starting a new security role.
Data & research | 5 min read
45 minutes to one minute: how we shrunk image deployment timeWe recently figured out how to reduce Kubernetes image deployment time from 45 minutes (way too long) to one minute (really fast). Here’s how we did it.
SOC | 3 min read
Touring the modern SOC: where are the dials and blinking lights?An Expel SOC tour isn’t about blinking lights. It's a discussion about mission, mindset, and the operations that make security work.
Rapid response | 6 min read
Incident report: how a phishing campaign revealed BEC before exploitationAfter 89 phishing alerts, we knew a large-scale campaign was underway. This case study walks you through what happened and how we responded.
Current events | 8 min read
Top Attack Vectors: February 2022Stay ahead of the latest threats. Our report on February 2022 incidents reveals top attack vectors and recommendations to protect your org.
MDR | 5 min read
Evaluating MDR providers? Ask these questions about their onboarding processEvaluating MDR providers? Get the critical questions you should ask about their onboarding process. Plus, see how Expel does it.
Current events | 6 min read
Top Attack Vectors: January 2022Get the top attack vectors and trends from our SOC's January 2022 incident investigations. Learn our key recommendations to protect your org.
Cloud security | 3 min read
5 pro tips for detecting in AWSCloud security is complex, but start with the basics. Get pro tips to help focus your lens for detecting threats in AWS effectively.
Current events | 7 min read
Top attack vectors: December 2021Get the top attack vectors and trends from our SOC's December 2021 incident investigations. Learn our key recommendations to protect your org.
MDR | 5 min read
Threat hunting: Build or buy?Should you build your own threat hunting capability or get a partner? This post breaks down your options and the crucial cost considerations.
MDR | 4 min read
What’s threat hunting and is it worth it?Confused about threat hunting? You're not alone. Learn what it is, how it works, and the value it brings to your org's detection and response.
Current events | 7 min read
Top attack vectors: November 2021Stay ahead of the latest threats. Our report on November 2021 incidents reveals top attack vectors and recommendations to protect your org.
Current events | 6 min read
Top attack vectors: October 2021Get the top attack vectors and trends from our SOC's October 2021 incident investigations. Learn our key recommendations to protect your org.
Current events | 5 min read
Top attack vectors: September 2021Get the top attack vectors and trends from our SOC's September 2021 incident investigations. Learn our key recommendations to protect your org.
Current events | 5 min read
Top attack vectors: August 2021Get the top attack vectors and trends from our SOC's August 2021 incident investigations. Learn our key recommendations to protect your org.
Current events | 5 min read
Top Attack Vectors: July 2021Get the top attack vectors and trends from our SOC's July 2021 incident investigations. Learn our key recommendations to protect your org.
Cloud security | 6 min read
How Expel goes detection sprinting in Google CloudBuilding detections in GCP? Our engineers demystify the process for you. Learn how to get strategic with your cloud detection and response.
MDR | 4 min read
How should my MDR provider support my compliance goals?Find out what compliance means in practice and how your MDR provider can support your compliance program, not become a liability.
Current events | 3 min read
Kaseya supply chain attack: What you need to knowRansomware attack hits Fourth of July weekend. Learn what’s happening and the immediate steps to take to protect your org right now.
MDR | 4 min read
Someone in your industry got hit with ransomware. What now?How do targeted attacks differ from common opportunistic attacks? Here's tips on keeping your org safe from these types of ransomware attacks.
Cloud security | 7 min read
Cloud attack trends: What you need to know and how to stay resilientTop pandemic attack trends are here. Learn how to remediate and use our crew’s tips to build resilience against these attacks.
Cloud security | 6 min read
5 best practices to get to production readiness with Hashicorp Vault in KubernetesFlying blind running Hashicorp Vault in Kubernetes? Get the best practices and tips to accelerate production without compromising on security.
Data & research | 7 min read
Plotting booby traps like in Home Alone: Our approach to detection writingHow do D&R engineers think about detection writing? Learn their process for creating alerts that help SOC analysts make smarter decisions.
Cloud security | 6 min read
Supply chain attack prevention: Three things to do nowCan’t trust the internet? Supply chain attacks like SolarWinds are not new. Get actionable tips to prepare and guard against similar attacks.
Current events | 3 min read
The SolarWinds Orion breach: 6 ideas on what to do next and whyGet our early observations on the SolarWinds Orion breach. Learn what to do next to detect related activity and better protect your org.
MDR | 9 min read
3 steps to figuring out where a SIEM belongs in your security programHow can a SIEM help you address your business needs? Do you even need a SIEM? Here are some tips to help you make a decision that works best for you.
MDR | 5 min read
The myth of co-managed SIEMsThinking of a co-managed SIEM? Our CISO busts common myths and shares the realities you must consider before making a decision.
Cloud security | 8 min read
Behind the scenes in the Expel SOC: Alert-to-fix in AWSWonder what cloud investigation looks like? See how our team foiled a real-life coin-mining attack in AWS, from alert to fix.
Product | 6 min read
How to create and maintain Jupyter threat hunting notebooksAfter Infosec Jupyterthon 2020, we answer your top questions about configuring Jupyter notebooks. Get tips for infosec processes.
Current events | 7 min read
10 tips for protecting computer security and privacy at homeYou're a remote worker now. Learn 10 essential tips to keep your at-home network safe and stay secure while working remotely.
Current events | 3 min read
Election security: Why to care and what to do about itThe security of our election system is vital. Find out the key challenges it faces and what you can do to help protect our election ecosystem.
SOC | 5 min read
7 habits of highly effective (remote) SOCsSecurity ops is a team sport … but how do you “play” together when your company’s working 100% remotely? Jon’s got some advice.
Product | 5 min read
Creating data-driven detections with DataDog and JupyterHubStop alert fatigue! Learn the tips, tricks, and favorite tools we use to determine optimal alert thresholds for customer environments.
Product | 6 min read
Exabeam: an incident investigator’s cheat codeWe love EDR tools too, but here are our best tips and tricks for combining EDR data with other (equally) important security signals.
Cloud security | 8 min read
Why the cloud is probably more secure than your on-prem environmentIs on-prem safer? Probably not. Get 5 reasons why the cloud offers better security than your on-prem environment.
Product | 3 min read
Where does Amazon Detective fit in your AWS security landscape?Running workloads on AWS? Get up to speed on the latest and greatest AWS-native security tools in our newest post.
Product | 8 min read
Using JupyterHub for threat hunting? Then you should know these 8 tricks.Jupyter Notebook gave us the freedom to rethink the way we analyzed hunting data. Here are some tips and tricks you can use in your own analysis.
SOC | 6 min read
7 habits of highly effective SOCsWondering what it takes to build an effective SOC full of motivated, happy analysts? We’ve got some thoughts on that.
Expel culture | 4 min read
5 tips for writing a cybersecurity policy that doesn’t suckAll good cybersecurity policies share some similar traits. Here are our pro tips for creating a solid policy for your own org.
MDR | 6 min read
Five things law firms can do now to improve their security for tomorrowRelativity CSO Amanda Fennell shares the top five, easy-to-get-started things she sees forward-thinking law firms doing to improve their security.
Data & research | 8 min read
Our journey to JupyterHub and beyondUsing JupyterHub? Get our configuration tips, tricks, and learn how we use it to make technical research and security analysis easier.
MDR | 4 min read
3 must-dos when you’re starting a threat hunting programSo you decided you want to build a threat hunting program...but where do you start? Here are our three must-dos when you’re planning your hunt.
MDR | 6 min read
How to make your org more resilient to common Mac OS attacksGot Macs in your org? Here are a few recent Mac OS attack trends and how you can become more resilient to ‘em.
Cloud security | 5 min read
This is how you should be thinking about cloud security challengesModern IT isn't about servers—it's cloud. Get our pro tips for easily cracking the cloud security code and modernizing your defense.
MDR | 4 min read
Don’t blow it — 5 ways to make the most of the chance to revamp your security postureStarting a new security program from scratch? Get our guide on exactly how to get started and make the most of your blank canvas opportunity.
MDR | 4 min read
How to get your security tool chest in order when you’re growing like crazyNeed to expand your security tool chest? Our CISO’s got some tips to consider when thinking about what tech to keep or buy.
MDR | 7 min read
Warning signs that your MSSP isn’t the right fitLook out for these 5 indicators that it's probably time to start considering alternatives to your managed security services provider (MSSP).
MDR | 5 min read
How to avoid shelfwareSet yourself up for success by asking these four questions before you purchase new security products and software.
MDR | 7 min read
From webshell weak signals to meaningful alert in four stepsStop wasting time on weak security signals. Learn how to combine endpoint and network events for a single, actionable alert.
MDR | 3 min read
Get your security tools in order: seven tactics you should knowGet your work right. Learn seven things to consider to bring harmony to your security toolchain and get the equipment you need to succeed.
MDR | 7 min read
How to triage Windows endpoints by asking the right questionsThe three parts of the investigative mindset and how to apply them when you triage Windows endpoint alerts.
MDR | 5 min read
A cheat sheet for managing your next security incidentTactical advice on how to survive a security incident when you don’t have an incident response plan, including a cheat sheet.