Security operations · 3 MIN READ · KYLE PELLETT AND LEAH BACHMANN · OCT 24, 2023 · TAGS: Cloud security / Expel Workbench / MDR
Do you know the journey a cloud alert takes before you get it?
If you’re working in a security operations center (SOC) or on a security team for an organization that’s utilizing a cloud environment, you’re probably familiar with your cloud’s native cybersecurity alerts. In fact, you may be too familiar. Clouds are well known (maybe even notorious…) for delivering a non-stop stream of alerts, which can quickly overwhelm you or your team if they aren’t managed correctly.
If you’re managing a multi-cloud environment (and research from the Cloud Security Alliance shows that many of you are), the problem is more complicated. Multi-cloud environments can deliver great benefits, like avoiding vendor lock-in, benefiting from the strengths of different cloud providers, and enjoying better performance and lower latency by spreading the load. But more clouds usually mean more alerts.
If you’re familiar with Expel, you know that we’re all about reducing the noise, whether it’s on-prem, in SaaS apps, or yes, in the cloud. With Expel Managed Detection and Response (MDR), we connect our security operations platform, Expel Workbench™, to our customers’ cloud infrastructures and apply our own detection rules to filter out unnecessary and false-positive alerts. And we do this across Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), and Kubernetes environments. This dramatically reduces the number of alerts that hit the SOC, and helps ensure that only the important ones actually get there.
You may be asking yourself, “That’s fine in theory, but how do alerts get there? How does Expel Workbench handle them?” We’ve just released a product tour that shows exactly that.
But let’s walk through it here too, using an AWS cloud alert as an example.
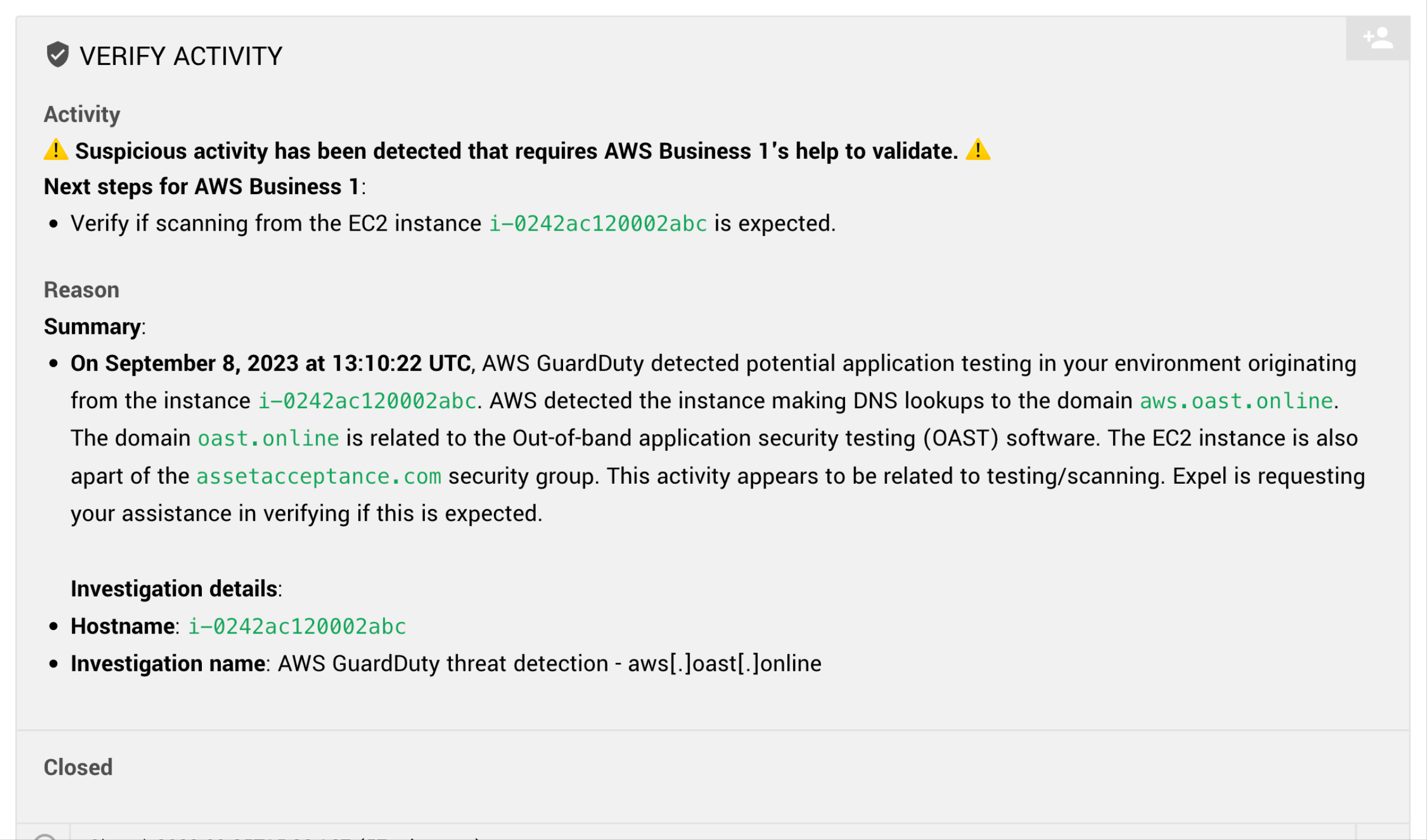
When AWS detects an issue, it triggers an alert that’s automatically logged in Workbench. Most of these alerts don’t represent an incident, and Workbench would quickly determine that they don’t need you to see or worry about them. But for the sake of this example, assume that the alert is real and for a compromised access key, meaning a bad actor may have accessed the AWS environment and is rooting around to see what he can access to plot his next steps. You can also see him twisting his comically long and thin mustache.
Workbench shows you all the alert details, including information about the access key, the user agent, and other information needed for further information.
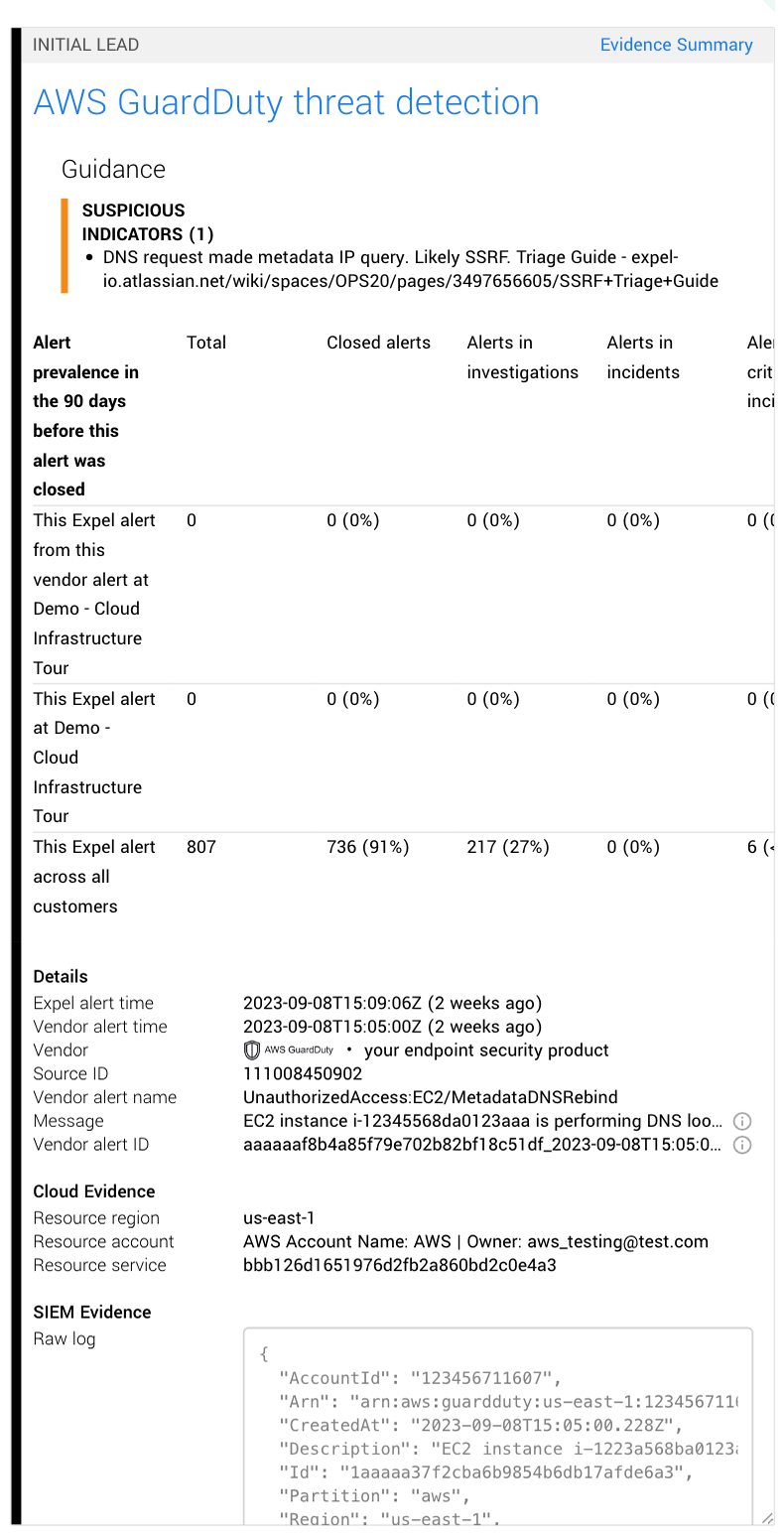
If you didn’t have Expel providing you with this context, AWS would just send the raw alert (in this case, “json blob”) with no additional information. You or your team would have to dig in and get that information manually, slowing down the decision-making process and delaying remediation steps. But with Workbench, you get Expel-specific detection logic, allowing the platform to prioritize the alert correctly.
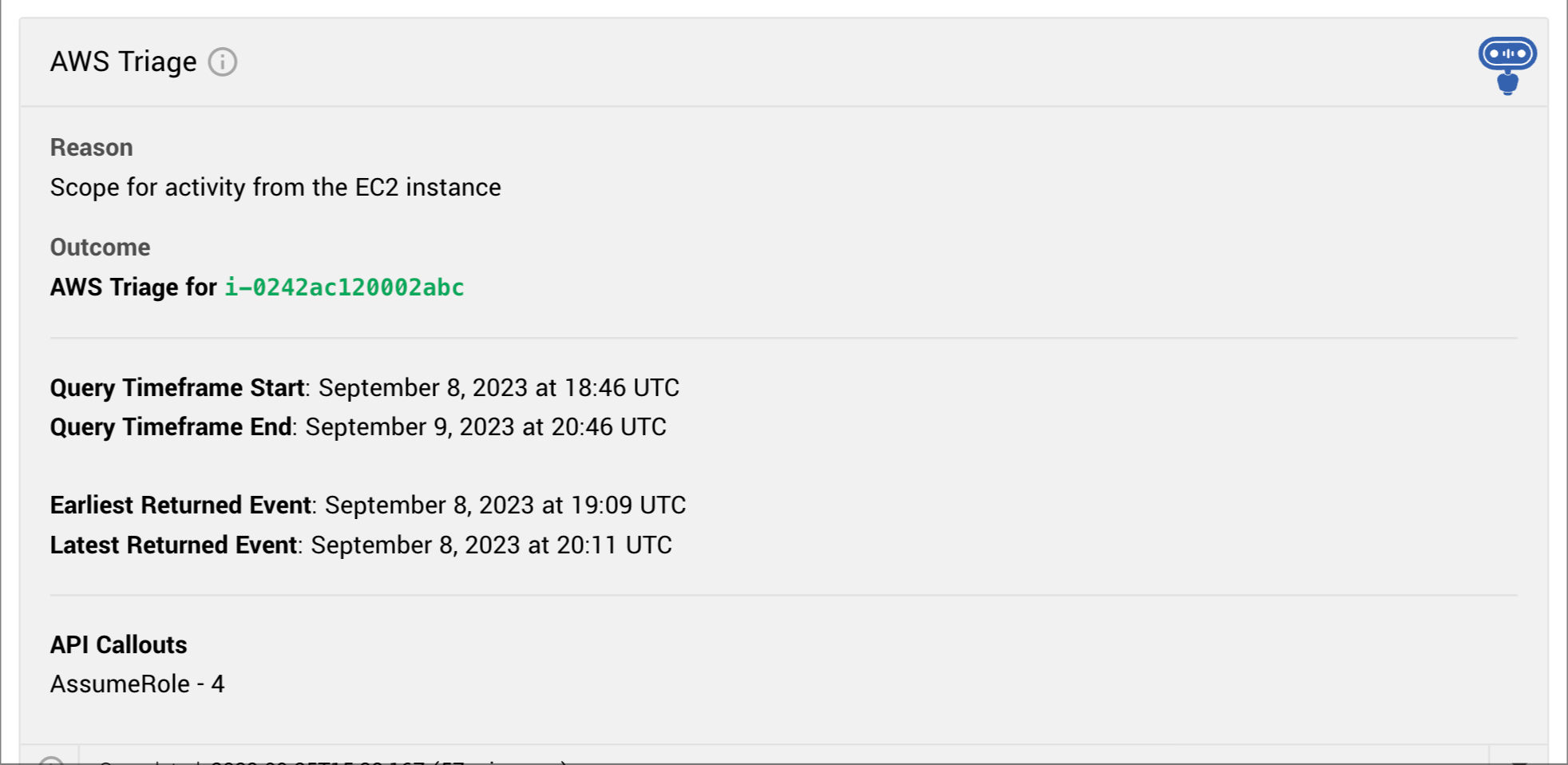
The next steps are automated too. Our bots look up the behavior around that access key in the previous 14 days and create a report that summarizes the activity. This is another way Workbench reduces manual fact-finding and saves precious time, and this report is just one example of the automated actions our bots can perform.
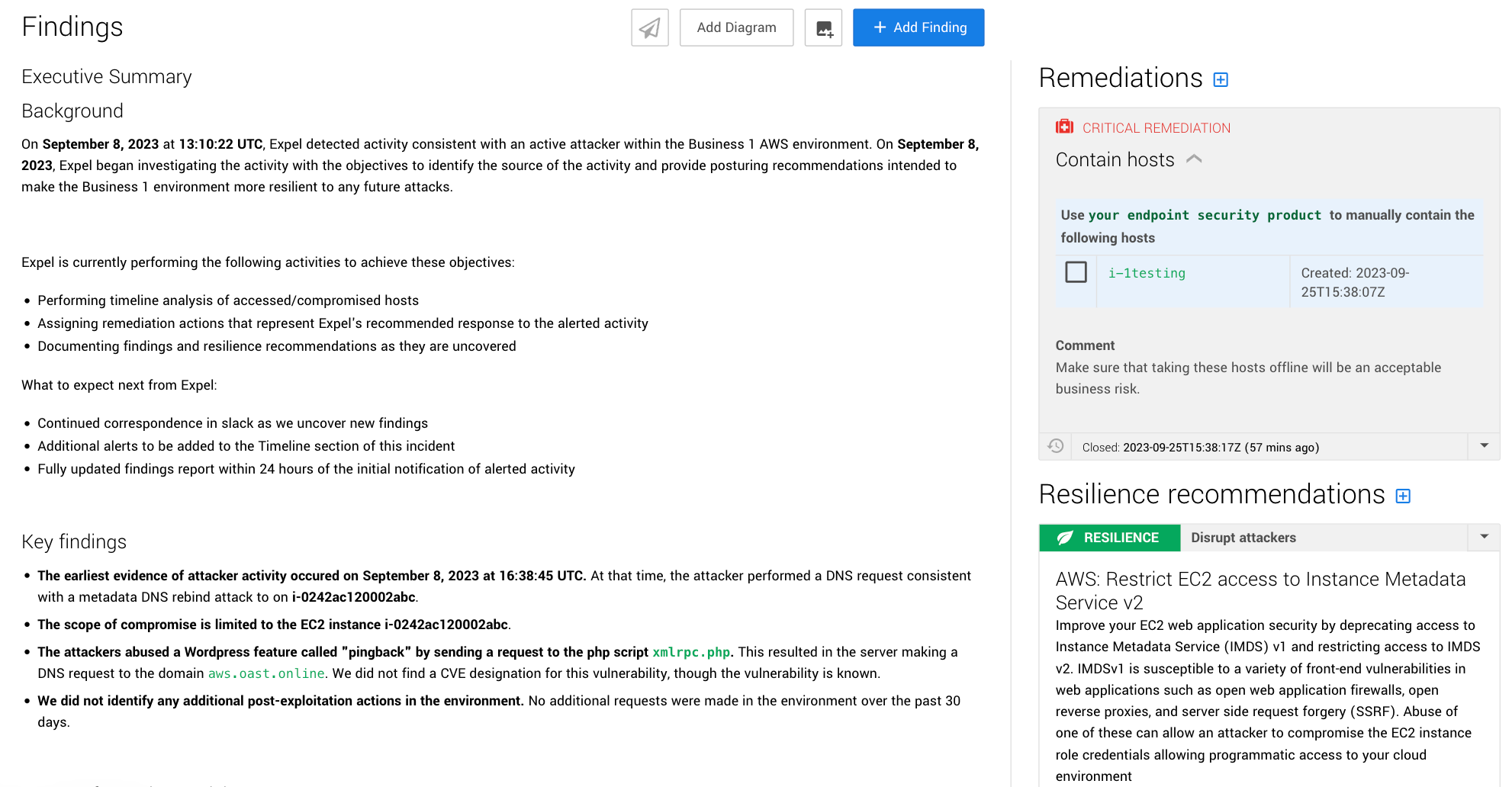
Workbench then puts all that info in front of an Expel SOC analyst who reviews it all and continues the investigation. For this sort of AWS alert, the Expel analyst would typically review the user’s activity before and after the alert to see if anything changed or if they engaged in any suspicious behavior. Once the analyst uncovers the threat and its root cause, the info goes into a findings report in Workbench.
Workbench then notifies you through Slack, Microsoft Teams, or via email of the investigation and presents you with the report that includes all the relevant info along with remediation recommendations on how to resolve the incident. And to help protect against similar attacks in the future, we also provide some resilience recommendations.
All said and done, we typically handle critical alerts in less than a half hour. Now picture this process if you’re in a multi-cloud environment. You’ve got Expel Workbench fielding all these native alerts from your different cloud providers, investigating, triaging, and only surfacing the most important ones to you, with the context and information described above. It can dramatically cut down on the time you spend on cloud security operations, freeing you up to focus on other important things.
Want a better look at how we handle a cloud alert? Head on over to our product tour. And if you want to get hands-on, sign up for a 14-day free trial of Expel MDR in your cloud.
If you’ve got other questions, drop us a line.