Data & research · 4 MIN READ · AARON WALTON · OCT 21, 2024 · TAGS: Get technical / Guidance
TL;DR
This is a summary of what you’ll find in each blog in this series:
- Volume I: Q3 by the numbers
- Volume II: CAPTCHA trick or treat. We look at the rising fad of using CAPTCHAs and fake error messages to trick users into executing malicious code on their own devices.
- Volume III: Malware trends. Infostealer malware—specifically Lumma—is trending, so we discuss recommendations.
- Volume IV: Identity trends. Phishing-as-a-service (PhaaS) continues to rise in popularity; we offer recommendations to detect their use.
- Volume V: Spotlight—preparing for software supply chain risks. We look at risks that exist now (and into the future) that need addressed to ensure a secure software supply chain.
So far, we covered our top takeaways from Q3 of 2024 (volume I) and shared cases where we saw cybercriminals leveraging fake popup messages (volume II). Now, our series continues with a look at malware infection trends.
Trends in types
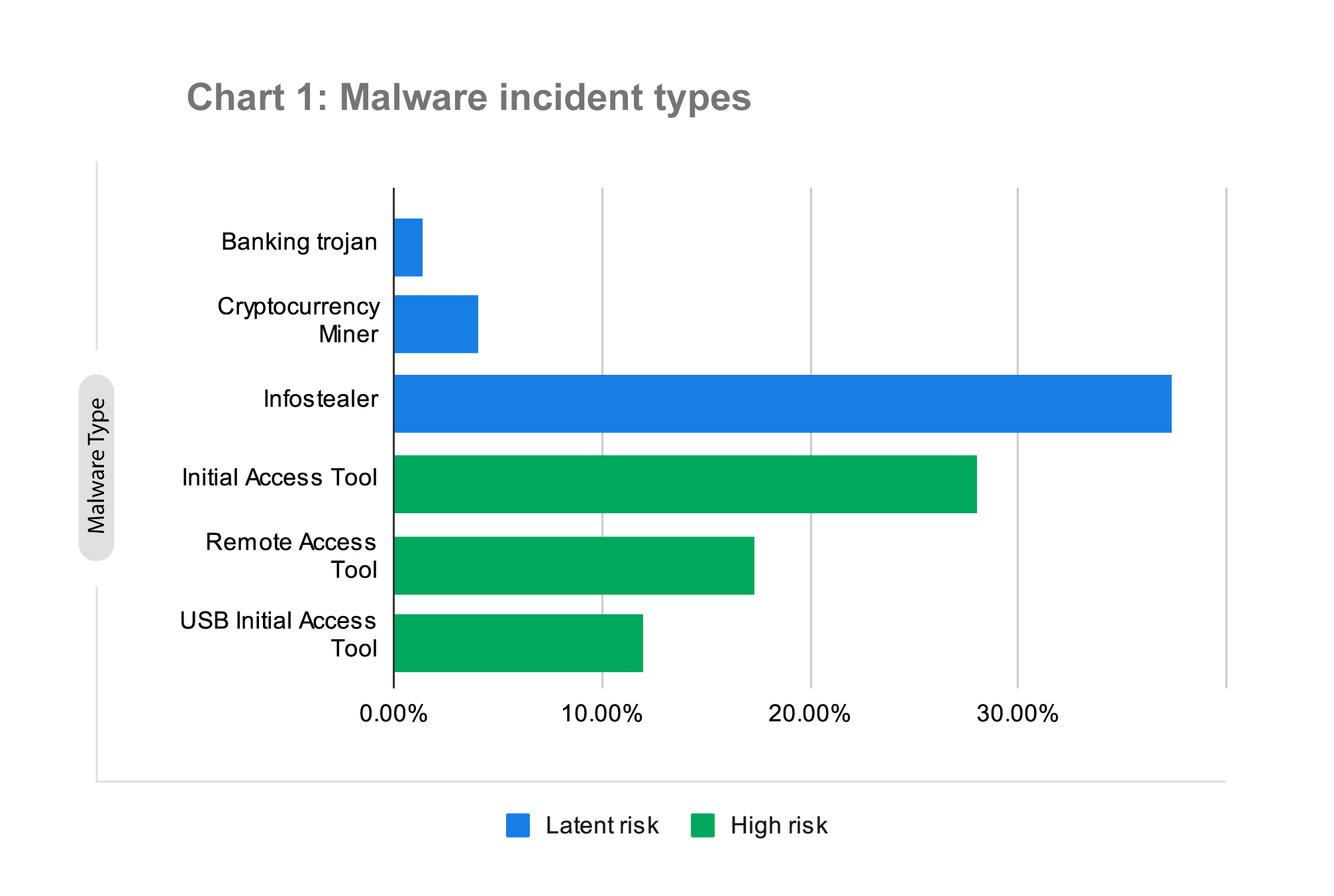
At Expel, we categorize malware into a few basic types. The two major types we discuss are high-risk and latent-risk malware. We consider malware high-risk when we know it’s leveraged by ransomware actors, or the malware provides a high degree of access to a victim’s computer or network. In the chart below, the USB initial access tools (USB IATs), remote access tools (RATs), and other IATs are considered high-risk. The remaining types are considered latent risk—that is, while they introduce risk, the threat isn’t immediate.
This quarter, the latent risk threat of infostealer malware was trending as the most common malware type we observed. The following chart breaks down the different types of malware that we saw across our customer base in Q3, and identifies whether the malware is high- or latent-risk.
A fraction of the total infostealer malware count was the result of a social engineering tactic discussed in volume II of this report.
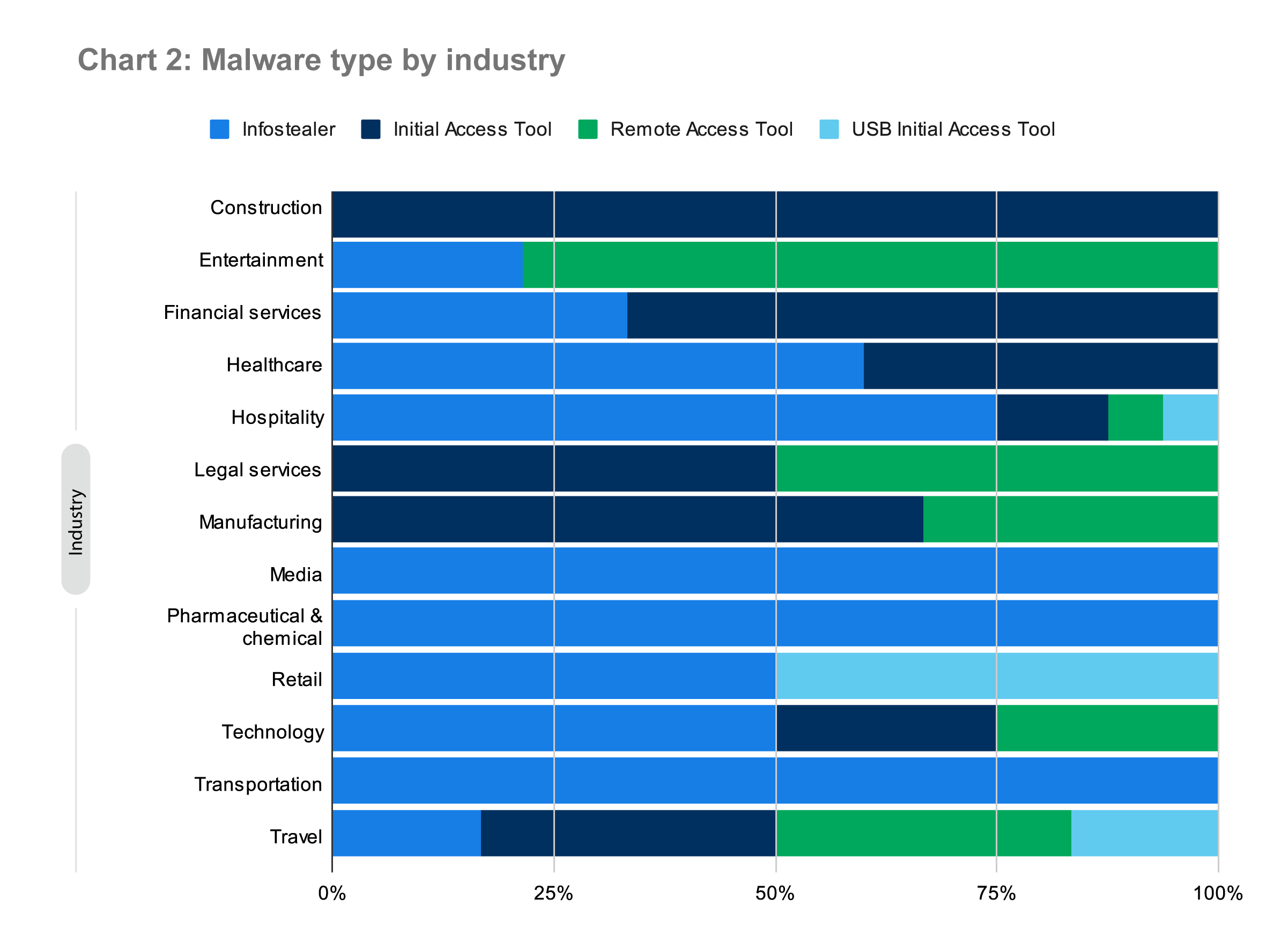
The chart below depicts the malware types we observed in Q3 across industries within our customer base. In comparison to last quarter, we saw infostealers across a broader range of industries and customers than before. This is likely because of a newer tactic—leveraging fake captchas—that tricks the user into executing malicious code. We’ll talk more about this tactic in volume III.
Malware for Macs, too
For the last three quarters, infostealer malware for Mac has averaged 9% of the total number of infostealer malware that we see. This is important because just a few years ago, malware targeting Macs was very uncommon. Now, there are several well-known Mac infostealer families and it’s fairly common.
Part of the reason Mac malware is becoming more common is because it’s often delivered by the same systems delivering Windows malware. Malware delivery often happens as part of a Traffic Distribution System (TDS). When a user visits an infected website connected to the TDS, the TDS assesses whether to deliver malware, and what malware to deliver. This system can determine not to deliver its malware to avoid discovery by analysts, but it can also determine whether the visitor is using a Windows system or a Mac, and deliver malware accordingly. This allows the operators of the TDS to capitalize on the traffic to the infected website, regardless of machine type.
This time around, the recommendations we make at the end of this blog are important for Mac users as well.
Lumma prominence
In previous quarters, we observed a wide range of infostealer malware making it past security tools. However, this quarter, we observed one infostealer occurring more often on Windows systems than other varieties: Lumma infostealer. Lumma infostealer is a commodity malware. Commodity malware is sold to and used by cybercriminals, and Lumma is sold on a subscription basis. It is up to the buyer to identify ways that they want to deliver the malware. As a result, Lumma is distributed in a wide variety of ways, including those mentioned in volume II.
Lumma became publicly available in 2022, and has changed its behavior over the years. In 2023, it disguised network traffic as API traffic using domains like gstatic-node[.]io and gapi-node[.]io After these were reported for abuse by the cybersecurity community, they instead began using a series of rotating domains on a regular basis. Due to the constant rotation of domains, they generally leverage top-level domains (TLD) that are less expensive, such as .xyz, .site, or .shop.
These less expensive domains may allow some mitigation strategies by your security team. For example, we recommend restricting network traffic with tools such as firewalls and secure web gateways. These tools, if configured appropriately, can block first-seen websites or newly created websites. This can help mitigate the initial download of these malwares, or block attempted command-and-control communication.
General recommendations
We recommend the following to protect against the rising popularity of Lumma infostealer (and other malware):
- Prepare a playbook for credentials that need to be reset if infostealer malware is executed in your network.
- Most infostealers prioritize stealing credentials from the victim’s browser. These credentials should be changed to prevent their abuse.
- Implement a password manager within your organization.
- Password managers store passwords in an encrypted format until they’re needed. If an infostealer malware is deployed on a system, they’ll be unable to access passwords from the password manager.
- Ensure that contractors are also able to store passwords in a safe manner. Contractors are at risk of downloading infostealers too! A compromise of their systems may easily lead to an impact on your own organization. (Check out this previous post for more discussion around this latent risk.)
- Be aware that some infostealer malware intentionally targets AWS, Azure, and GCP credentials that are saved on a host. Build it into your playbook to rotate these credentials, too—if they’re on the host.
In the next volume, we’ll talk about trends we’ve seen associated with identity threats. Though we talk primarily about phishing, infostealer malware plays a role there, too, because Expel monitors for suspicious activity no matter how the victim’s credentials were stolen.
About these reports
The trends described in our QTRs are based on incidents our security operations center (SOC) identified through investigations, alerts, email submissions, or threat hunting leads in the third quarter (Q3) of 2024. We analyzed incidents across our customer base, which includes organizations of all sizes, in many industries, and with differing security maturity levels. In the process, we sought patterns and attacker tendencies to help guide strategic decision-making and operational processes for your team.