Data & research · 2 MIN READ · AARON WALTON · OCT 17, 2024 · TAGS: Guidance / Phishing
Welcome to the Expel Quarterly Threat Report (QTR) for Q3 2024. If you’re new here, our QTRs provide data and insights on the attacks we’re seeing, how to spot them, and ways you can protect your organization. By sharing how attackers got in, and how we stopped them, we’ll translate the security events we detect and remediate into tips and strategies for your organization.
About these reports
The trends described in our QTRs are based on incidents our security operations center (SOC) identified through investigations into alerts, email submissions, or threat hunting leads in the Q3 of 2024 (July–September). While securing orgs across our customer base—of varying sizes, industries, and security maturity levels—we analyzed incidents and sought out patterns and attacker tendencies to help guide strategic decision-making and operational processes for your team.
TL;DR
This is a summary of what you’ll find in each blog in this series:
- Volume I: Q3 by the numbers.
- Volume II: CAPTCHA trick or treat. We look at the rising fad of using CAPTCHAs and fake error messages to trick users into executing malicious code on their own devices.
- Volume III: Malware trends. Infostealer malware—specifically Lumma—is trending, so we discuss recommendations.
- Volume IV: Identity trends. Phishing-as-a-service (PhaaS) continues to rise in popularity; we offer recommendations to detect their use.
- Volume V: Spotlight—preparing for software supply chain risks. We look at risks that exist now (and into the future) that need addressed to ensure a secure software supply chain.
To kick things off, let’s talk about Q3 by condensing it down to some numbers.
Q3 by the numbers
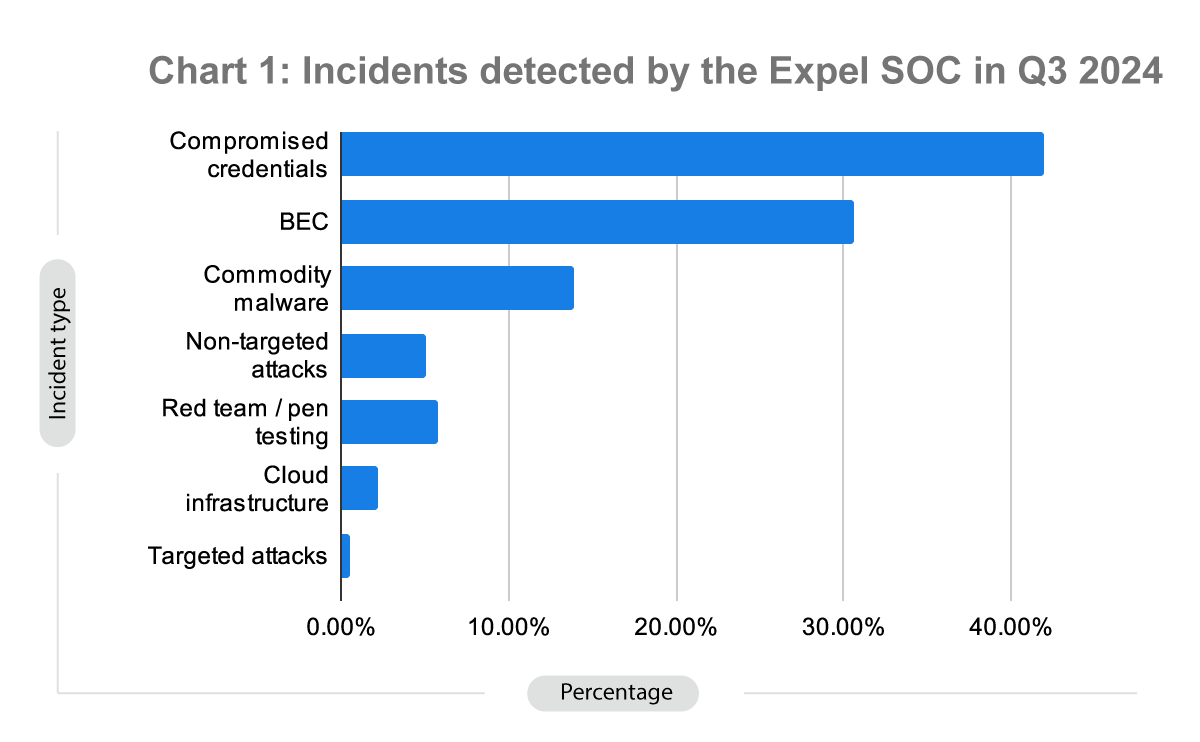
Incident types
- Identity-based attacks (account compromise and account takeover) accounted for 72% of all incidents our SOC identified.
- In the context of this report, we define identity threats as attackers attempting to gain access to a user’s identity to perpetuate fraud.
- This includes failed attempts to abuse compromised credentials, as well as attackers who successfully gain access to a target account (also known as business email compromise, or BEC).
- Identity-based attacks are consistently the predominant threat our SOC sees.
- We continue to see a preference among attackers to use virtual private server hosting providers when accessing a compromised account.
- Malware-based incidents made up 14% of all incidents in Q3. These are incidents where the malware wasn’t blocked by other security controls.
- The top three types of malware we observed were: information stealing (or infostealer) malware (37%), remote access tools (17%), and initial access tools (28%).
- This quarter, it’s notable that Lumma stealer accounted for 56% of all infostealer malware infections we observed. For reference, last quarter Lumma stealer only accounted for 7% of these infections.
- Many of these infections were the result of social engineering a user to execute PowerShell (We’ll dive into this in detail in volume II).
- Ten percent of infostealer malware incidents targeted MacOS systems.
- Incidents in cloud infrastructures (AWS, GCP, Azure, and Kubernetes) made up only 2% of the total incident volume. This has stayed consistent over the last few quarters. There are a few threat actors specifically targeting cloud infrastructure, but not many. Most compromises still take advantage of misconfigurations. However, there are plenty of risks on the horizon, and we’ll talk about these in our Volume V spotlight.
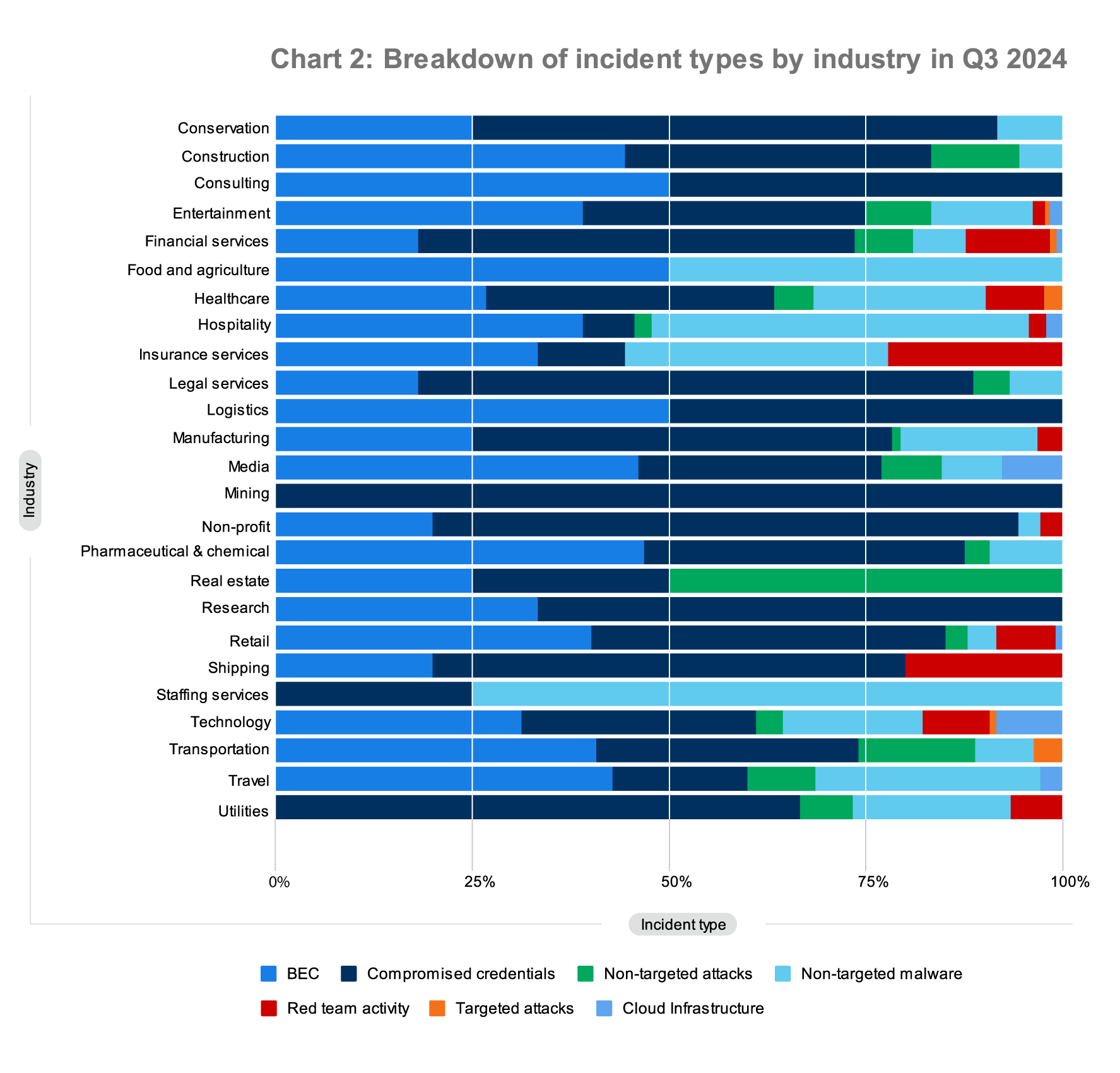
The chart below looks at incident types across the industries comprising our customer base. The gist of it? Attackers opportunistically target the vulnerable, regardless of their industry.
A lot happened this quarter, so stay tuned for the continuation of this series with Volume II: CAPTCHA trick or treat.
And if you have any questions or just want to chat, don’t hesitate to drop us a line.
If you don’t have time to read the full report, you can watch an overview of it in this webinar recording in under 15 minutes.