TL;DR
- This is part three of four of our Quarterly Threat Report blog series for Q1 2025
- You can find parts one, two, and four here post-publication
- Part three covers trends and insights for endpoint threats
Thus far in our Quarterly Threat Report (QTR) blog series, we covered our top takeaways from the first quarter (Q1) of 2025 in volume I: Q1 by the numbers. In volume II, we dug deeper into cloud-based service incident trends.
Our series continues with a look at general trends on endpoint activity and the continued threat of infostealing malware.
Initial access vectors
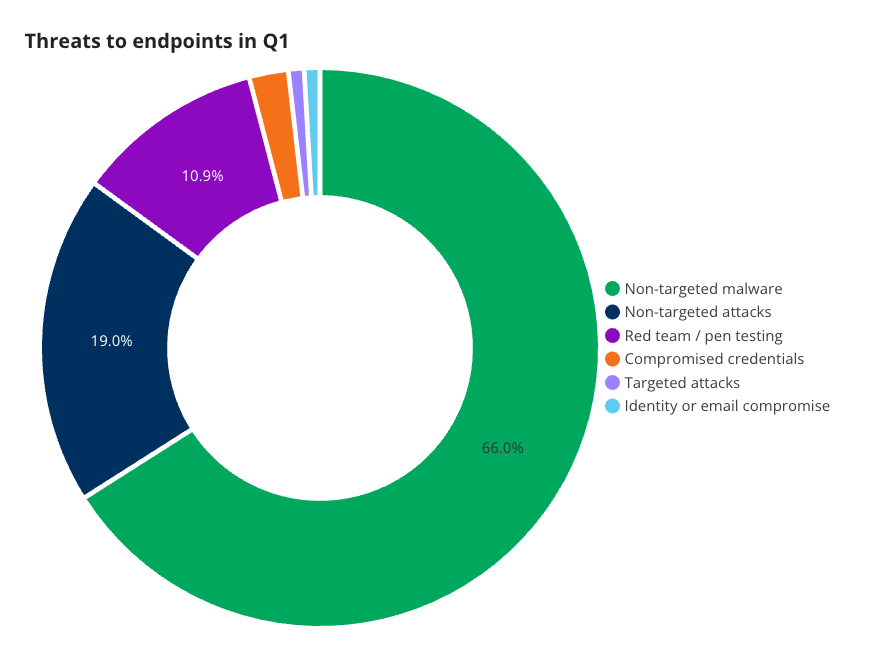
In the graph below, we break down the incidents impacting endpoints into the same categories from the first blog.
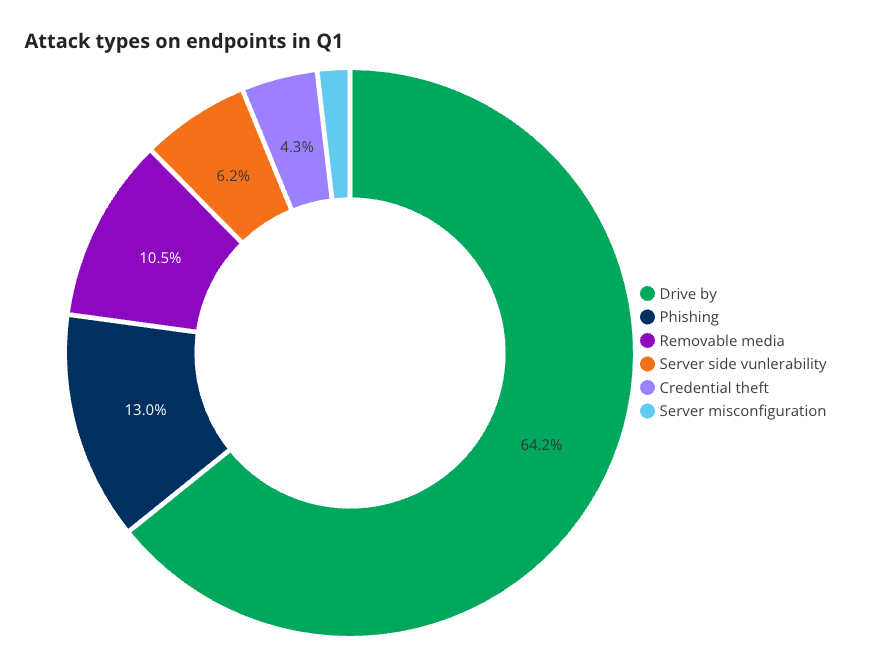
Based on the analysis of incidents our SOC saw this quarter, we’re able to break down the attacks further into specific attack types.
The attack vectors are defined as:
- Drive-by download: An attack leveraging infected or attacker-controlled websites to trick a user into downloading and executing a malicious file.
- Phishing: An attack was part of a broader attempt to trick a user, such as a call-back phishing scam or a file download.
- Removable media: An incident which was the result of an infected USB device.
- Server misconfiguration: An incident which was the result of a server or cloud resource being configured incorrectly or with easily guessable credentials.
- Server side vulnerability: An incident which was the result of a vulnerability in a service or application on a server.
The source of most endpoint incidents are drive-by downloads—situations where a user downloads a file they weren’t intending to download, or were tricked into downloading it. The high rate of malware incidents from this method highlights the need to further monitor and defend this endpoint.
In 51% of all malware incidents, a user was tricked into executing malicious code. This represents a new attack surface defenders need to think about, and we suggest using group policy to restrict use of PowerShell and the Windows Run program for users who don’t need it to defend against this tactic.
Phishing only made up 13% of sources this quarter, and infected USB devices (“removable media”) continue to account for 10.5% of incidents. These are important threat vectors to be defended against, but, due to changes in the threat landscape, aren’t as big of a threat as they used to be.
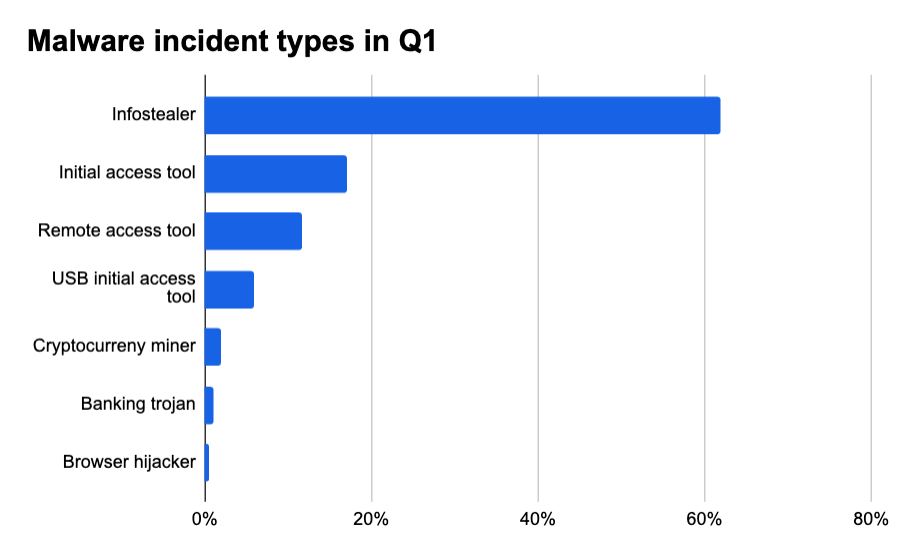
Trending malware types
The most popular malware type we saw is still infostealing malware. Infostealers are cybercriminal-created malware that attempts to steal credentials from a victim’s browser and computer. In this report, we primarily emphasize their ability to steal credentials from browsers; but it’s important to understand they target other kinds of data as well, such as cryptowallets and passwords stored by the operating system.
In Q3 of 2024, we saw the prevalence of infostealing malware trending upward. At the time, infostealing malware made up 37% of all malware incidents. Then in Q4, it accounted for 61.9% of all malware-based incidents. Infostealers still account for 61.9% of all malware based incidents in Q1 of 2025.
In our 2025 Annual Threat Report, we compared all incidents from 2023 to 2024 and discussed the events and trends driving this change. Namely, we pointed to the disruption of some of the major initial access brokers and the rise of the click-fix tactic. As a refresher, the major initial access brokers have historically maintained robust infrastructure, allowing them to distribute malware very broadly and run massive email campaigns sending malware that can install initial access tools, and then selling the access to ransomware actors. Those initial access brokers have had to change tactics, and so have the ransomware actors.
Ransomware actors, like other financial crime actors, have shifted more to stealing credentials and leveraging access gained through credentials to ransom an environment. Multiple gangs have made a long career prioritizing this attack vector. Akira ransomware has been known to buy or brute-force corporate VPN credentials, Black Basta—according to their leaked chat logs—also shifted from using initial access malware to using valid credentials and even building unique tools to brute-force corporate VPN credentials, and Hellcat was recently observed using stolen Jira credentials to steal data and demand a ransom. The theft of stolen credentials empower ransomware and other crimes. Being able to prepare for, detect, and respond to stolen credentials is important to protect an organization.
Defense against infostealing malware should be built into security controls and policies. For defending against infostealers, we recommend the following controls:
- Enforce the use of password managers for all users, including contractors. Keeping these credentials stored in encrypted applications keeps infostealers from being able to access them.
- Disable the Run program in Windows via the Group Policy Editor for users who don’t need it. The click-fix tactic relies on the run program. By disabling it, the risk of infostealers, ransomware gangs, and nation-state actors using this tactic is reduced.
- Restrict Windows PowerShell usage through the Group Policy Editor as well. Many common malware, including infostealers, rely on PowerShell to pull down and execute commands. This restriction ensures only users who need PowerShell have it available.
In our fourth and final blog this quarter, we’ll be looking at cloud infrastructure trends—what we consider this front covers, trends we’ve seen, and approaches you can take to defend it.