Current events · 7 MIN READ · BRITTON MANAHAN · JAN 13, 2022 · TAGS: Guidance / tech stack / threat landscape
We’re often asked about the biggest threats we see across the incidents we investigate for our customers. Where should security teams focus their efforts and budgets?
To answer these questions, we’re sharing monthly reports on the top attack vectors, trends, and resilience recommendations identified by our security operations center (SOC). Our goal is to translate the security events we’re detecting into a security strategy for your org.
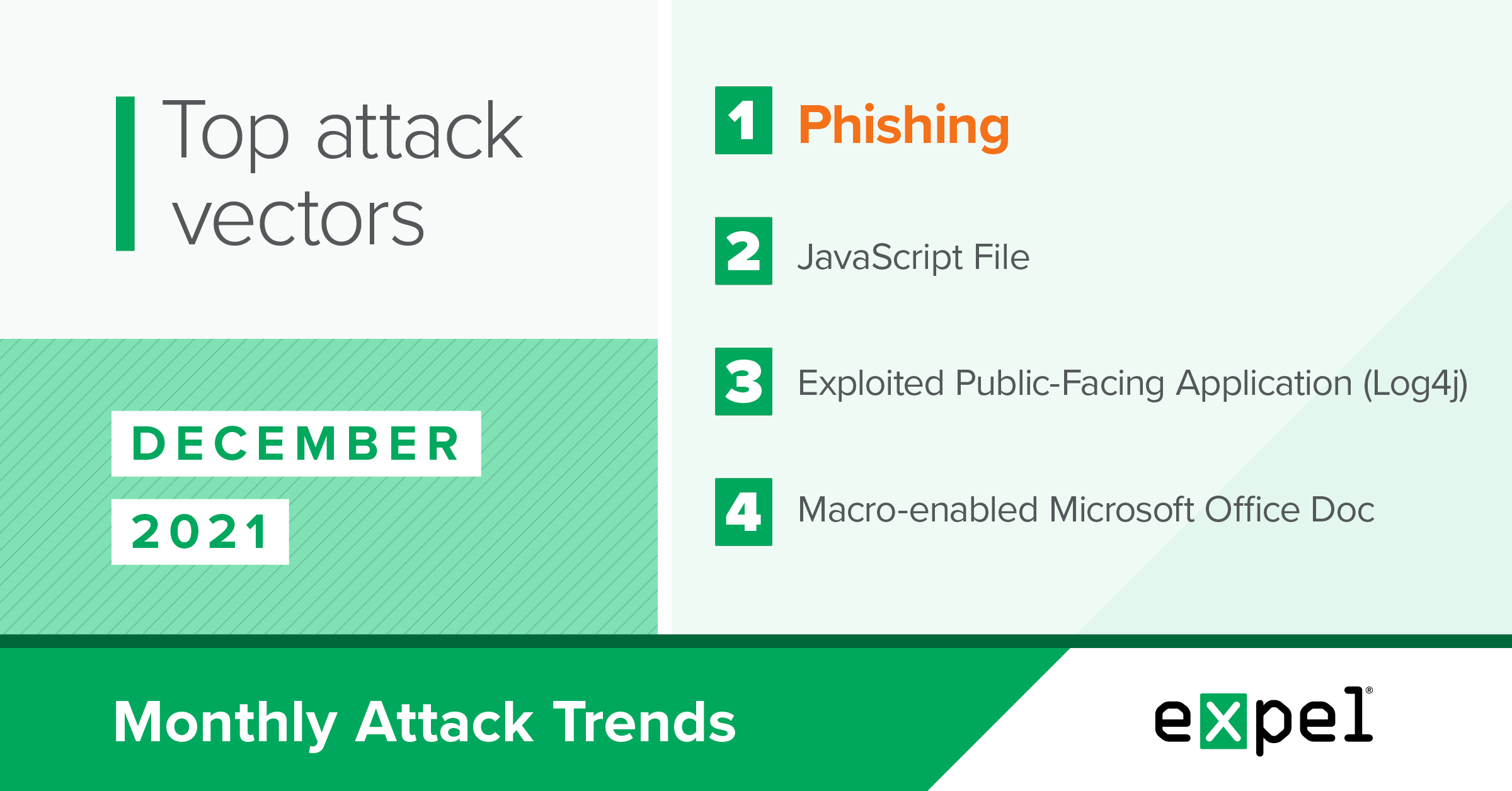
For this report, our SOC analyzed the incidents we investigated in December 2021 to determine the top attack vectors used by threat actors. In a month with cybersecurity news about the Log4j vulnerability making top headlines, here’s what stood out:
- Threat actors performing large-scale scans to exploit systems using the Log4j zero-day vulnerability
- Attackers continuing to use the Cobalt Strike command and control toolkit as malware
- Threat actors using a new attack pattern to deploy ransomware
- Attackers authenticating into an isolated Citrix remote access session, then breaking out of it
Read on to learn more and see our tips for what to do about all of the above.
Log4j vulnerability was a top target
TL;DR: The recently-discovered Log4j vulnerability was a major target in December as attackers tried to outrun remediation by scanning the web for unpatched instances to exploit.
This probably isn’t your first time hearing about the Apache Log4j zero-day vulnerability discovered in early December 2021. It’s now considered one of the most impactful vulnerabilities uncovered in recent years. In a nutshell, this vulnerability allows for arbitrary remote code execution by exploiting a flaw in JNDI lookups performed by the Log4j Java logging library.
This vulnerability is so devastating because of the number of software applications and libraries that rely on Log4j, putting hundreds of millions of devices at risk.
We’ve received a steady stream of alerts related to the widespread scanning activity threat actors are conducting to locate vulnerable systems. And since this commonly-used logging library provides such a large attack surface, it’s no surprise that attackers are finding success.
In fact, 100 percent of incidents involving public-facing exploits that we investigated in December were a result of the Log4j zero-day vulnerability.
Out of the successful Log4j exploits we observed, 50 percent established a remote shell on the exploited system while the other half deployed malware like Cobalt Strike. The incidents involving remote shells may have been first steps towards deploying malware, but were detected and the systems contained before attackers had the chance.
When we have evidence that malware’s running on a system, our priorities are to stop it, then figure out how it got there. In December, many of our initial leads were broad internet scanning activity that we then had to investigate further to determine whether any successful Log4j exploitation actually occurred. And proving something malicious didn’t happen is definitely the more time-consuming task. So we spent a lot of time examining network activity on the targeted hosts for potential successful callbacks to attacker-controlled endpoints.
Due to the up-stream nature of the Log4j library (meaning its use by third-party apps and libraries), it can be difficult for orgs to know which of their systems may be running Log4j and are vulnerable to an exploit. As a result, this vulnerability will likely remain relevant for some time, even though patches have been released.
Resilience recommendations:
- Determine if you’re logging applications to other managed logging platforms (local or cloud-hosted).
- Validate whether these apps are vulnerable and/or impacted by this zero-day vulnerability.
- Use a vulnerability scan to confirm your findings and attack surface for this vulnerability.
- Anyone using Log4j should update to version 2.17.1 ASAP. The latest version is already on the Log4j download page. The patched version of Log4j 2.17.1 requires a minimum of Java 8. If you’re on Java 7, you’ll need to upgrade to Java 8.
- If updating to the latest version isn’t possible, you can also mitigate exploit attempts by removing the JndiLookup class from the classpath.
Cobalt Strike
TL;DR: Cobalt Strike was the most common malware family we observed in December and continues to be a favorite of threat actors.
In December 2021, 20 percent of the incident payloads we identified were variants of the Cobalt Strike penetration testing command and control (C2) framework. While originally designed as a paid tool for legitimate engagements, Cobalt Strike’s module nature and capabilities have made it a favorite tool of threat actors. It’s also motivated them to crack versions and release them on the secret web.
The Cobalt Strike Beacon payload can be generated in many forms, including a stand-alone exe, but it’s most often reflectively loaded into memory by an initial stage payload as a file-less loaded DLL. The functionality provided by this framework includes (but isn’t limited to) command and script execution, covert encryption communication over different network protocols, file uploads and downloads, reconnaissance, privilege escalation, and lateral movement.
Threat actors used several delivery methods and first stage payloads in December to ultimately try to establish a C2 connection through a Cobalt Strike Beacon. The initial infection vectors for these incidents included:
- Phishing
- Public-facing exploitation of Log4j
- Drive-by download
Using those infection vectors, attackers delivered these first stage payloads to then try to load different variants of a Cobalt Strike Beacon:
- BazarLoader
- Gootkit
- Generic Obfuscated PowerShell
Clearly, threat actors are using a variety of infection vectors to deploy an initial malware stage embedded with or configured to download a Cobalt Strike Beacon payload. Attackers have a wide range of choices for this initial stage, using Windows executables or scripting languages across different malware variants. But they typically avoid having the Beacon payload touch persistent storage when loading it into memory (file-less malware).
Resilience recommendations:
- Confirm your endpoint detection and response (EDR) coverage across all of your endpoints.
- Perform a vulnerability scan against your externally facing systems.
- Consideration conducting internal or external penetration testing using a legitimate version of the Cobalt Strike framework.
- Implement network layer controls capable of detecting or blocking traffic to low reputation destinations.
- Conduct regular security awareness training for your employees with a focus on phishing.
Other incidents of note
TL;DR: Two particularly interesting incidents stood out in December – one where threat actors were likely preparing to deploy ransomware and another where they broke out of a remote access Citrix session.
One incident of note that we observed in December highlights a recent pattern across attack lifecycle stages used to ultimately deploy ransomware across an environment.
The incident began with a phishing email used to deploy the initial BazarLoader malware payload, which communicated out over a URL that tried to appear related to Zoom – our first indicator of malicious activity. The indicators of compromise (IOCs) from this incident directly correlated to an ongoing campaign where attackers use BazarLoader to download and load a Cobalt Strike Beacon into memory to start internal reconnaissance on the network and establish a valid method of lateral movement. Threat actors then typically begin widespread deployment of the Diavol family of ransomware. However, we detected this activity early in its lifecycle and contained the system that the attackers were using as an entry point before they could deploy ransomware.
A second notable incident we detected and responded to in December involved a server running the Citrix remote access application. After obtaining credentials provided to a third-party vendor, the threat actors were able to authenticate into a Citrix remote access session running on the server.
The most interesting part of this incident happened next – the attackers were able to break out of this isolated session with a method using Internet Explorer. We determined this through the process tree, which showed Internet Explorer as the parent process for several command prompt, PowerShell, and system reconnaissance-related processes.
After breaking out of the isolated Citrix session, the attacker acquired credentials and used Remote Desktop Protocol (RDP) to move laterally in the environment and access several additional systems. However, they were detected and expelled from the environment before they had time to exfiltrate any sensitive data or perform any other harmful activities.
Resilience recommendations
- Regularly perform an external penetration test to make sure your environment is prepared to detect advanced tactics and techniques.
- Review your company’s incident response process and procedures to make sure you can confirm true positives and respond promptly to incidents in progress to minimize the impact a threat actor can have.
- Confirm your endpoint detection and response (EDR) coverage to maximize your visibility and ability to respond in your environment.
Takeaways
Phishing remained the most common attack vector in December (check out our top resilience recs!), but we also observed a bunch of novel trends and incidents.
The recently-discovered Log4j zero-day vulnerability is historic because of its frequent use as an error logging library in a variety of Java-based apps. Threat actors wasted no time starting to mass scan the Internet for vulnerable systems and try exploits to establish remote shells or deploy malware. While activity related to this vulnerability has come down from its peak in December, Log4j will stay relevant for some time because of its widespread (and sometimes difficult to identify) impact. If you haven’t already, it’s critical to understand which of your systems are running Log4j and make sure they’re updated to version 2.17.1.
The most common malware payload we observed in December was the Cobalt Strike Beacon. Attackers are more and more drawn to cracked versions of this penetration testing software released on the secret web because of the number of built-in features it provides and its high level of stability. To avoid detection, this command and control framework is most commonly reflectively loaded into memory by the initial payload delivered to the host, without touching persistent storage. To help defend against malicious Cobalt Strike, focus on initial infection vectors by conducting regular security training for your employees and performing vulnerability scans of your externally-facing systems.
We also highlighted two interesting incidents that we responded to in December. One of these involved a recent threat actor campaign following an established formula for typical network intrusion. This flow uses a phishing email as the initial entry point to deliver a first stage payload. The first stage malware then brings down additional functionality to perform internal reconnaissance, privilege escalation, and lateral movement. Once the attacker is satisfied with the level of access they’ve gained in the environment, they’ll deploy a ransomware variant. But in this particular incident, the threat actor was detected and stopped before they could release ransomware into the environment.
Another notable incident in December involved a Citrix remote session authenticated through compromised third-party credentials. The attacker was able to break out of this isolated Citrix session with one of several methods that use Internet Explorer. Once the threat actor broke out and had access to the underlying server, they were able to gather credentials to start moving laterally before they were expelled from the environment. Consider having an external third party perform a penetration test in your environment to evaluate your security controls against sophisticated attacker techniques.
We’ll be back with insights on January’s top attack vectors. In the meantime, have questions about this month’s data or what it means for your org? Drop us a note.