Data & research · 2 MIN READ · LIZ MCLAUGHLIN · MAY 7, 2025 · TAGS: AI & automation
TL;DR
- Expel’s machine learning is transparent, and designed with (and for) humans
- We use machine learning to lighten the tedious workload of analysts, doing things like classifying automated marketing emails
- By teaching our tech with our people, we’re watching performance increase rapidly
In an era where cyber threats are evolving at lightning speed, machine learning (ML) stands as a critical technological ally, offering adaptive, intelligent protection. It’s currently supporting the fight across our industry in various ways. It can help identify security breaches, detect phishing attempts, analyze user behavior to establish baselines, and even forecast potential future attack trends.
It’s important to recognize that even while ML offers powerful solutions, humans bring something fundamental—contextual understanding, nuanced judgment, and deep cybersecurity expertise. Many security companies rely on opaque ML models making decisions in a black box. Expel’s ML is transparent, methodical, and deliberately designed with human expertise at its core.
Behind the scenes: How Expel brings humans back into the loop
Meet our phishing automated marketing email (AME) classification model
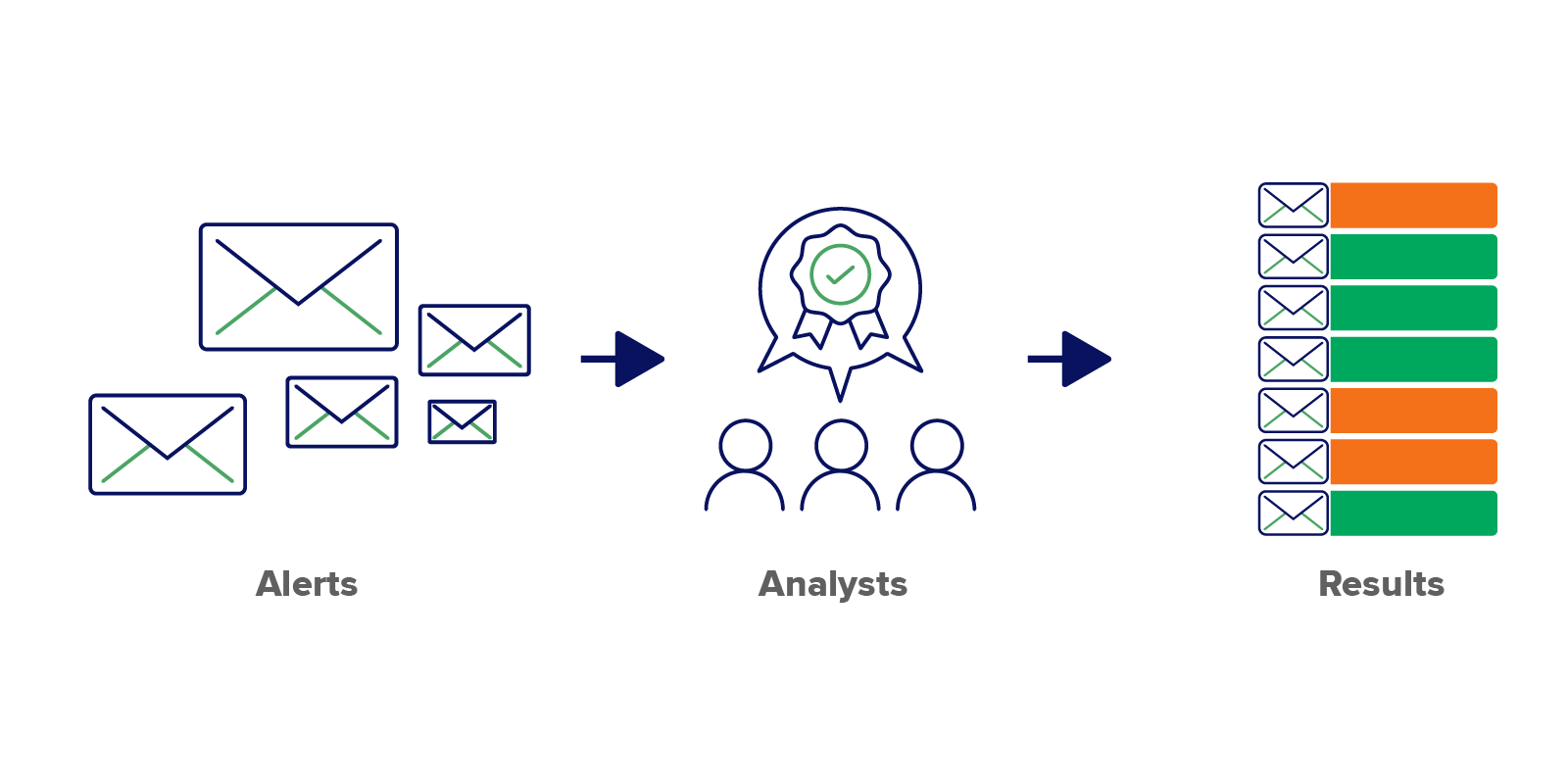
Our specialized machine learning model does something deceptively simple, yet incredibly powerful. When a phishing alert comes in, it quickly assesses whether it’s a benign marketing email, or a potential threat. It cuts through the noise so our analysts can focus on what really matters, and quickly separates dangerous phishing attempts from the mountains of routine marketing emails flooding inboxes.
Injecting our SOC’s expertise into the process
Continuous learning: Our process begins with curating a comprehensive dataset of recent phishing alerts. Our analysts work collaboratively in structured labeling sessions for every model retrain, leveraging their collective expertise to:
- Individually review and hand-label each alert
- Discuss edge cases and trends
- Reach consensus on challenging classifications
The result is a rigorously vetted dataset, where our analysts inject their wisdom into every training cycle. Every time our analysts manually review and label an alert, they’re not just checking a box. They’re teaching our ML the nuanced art of distinguishing between a harmless marketing email and a potentially devastating phishing attempt.
Quarterly deep dives: Our comprehensive model assessments go beyond simple metrics. Our Data Science and SecOps teams collaborate to:
- Conduct comprehensive performance reviews
- Analyze edge cases and potential improvement areas
- Develop targeted enhancements, ensuring our classification remains razor-sharp and adaptive
The numbers don’t lie
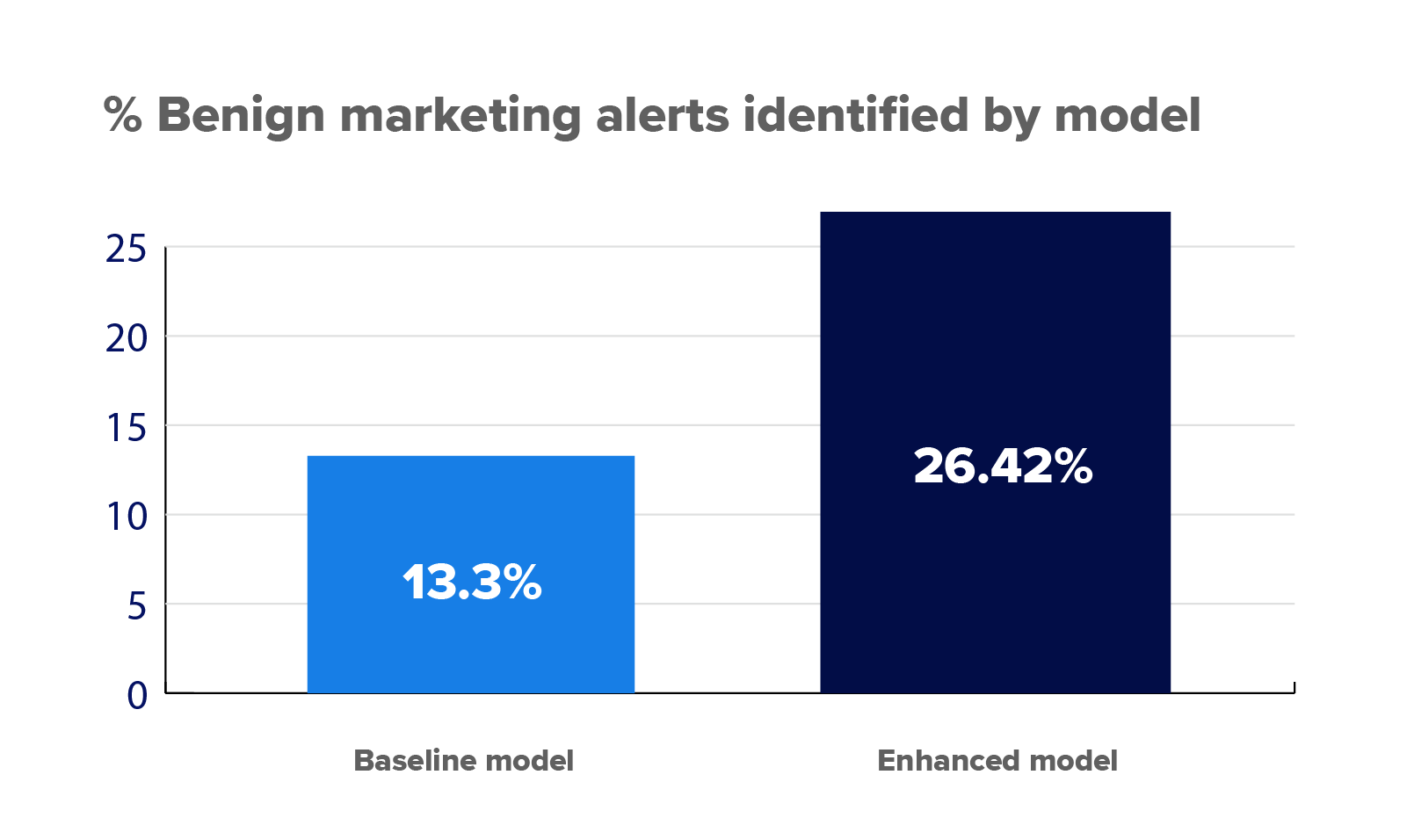
By incorporating human-in-the-loop learning, we’ve nearly doubled our system’s ability to recognize harmless marketing emails. After implementing this process in September 2024, our recognition rate went from 13.3% to 26.4% to date.
ML in cybersecurity shouldn’t be about replacing human judgment, but instead about amplifying it. Our hands-on approach ensures that our threat detection isn’t just fast, but able to capture the subtle contextual insights that only human expertise can provide.