Data & research · 3 MIN READ · AARON WALTON · OCT 23, 2024 · TAGS: Get technical / Guidance / Phishing
TL;DR
This is a summary of what you’ll find in each blog in this series:
- Volume I: Q3 by the numbers
- Volume II: CAPTCHA trick or treat. We look at the rising fad of using CAPTCHAs and fake error messages to trick users into executing malicious code on their own devices.
- Volume III: Malware trends. Infostealer malware—specifically Lumma—is trending, so we discuss recommendations.
- Volume IV: Identity trends. Phishing-as-a-service (PhaaS) continues to rise in popularity; we offer recommendations to detect their use.
- Volume V: Spotlight—preparing for software supply chain risks. We look at risks that exist now (and into the future) that need addressed to ensure a secure software supply chain.
In volume I of our threat report series, we highlighted that identity-based incidents are the top incident type we observe, quarter-over-quarter—largely the result of the increasing accessibility of phishing-as-a-service (PhaaS) platforms. In this volume, we take a closer look at PhaaS platforms and discuss what we’ve seen, and what actions we recommend.
Phishing facilitation
Last quarter, we discussed phishing-as-a-service (PhaaS) platforms. If you aren’t familiar with these platforms, you may want to read the post from last quarter. While it isn’t necessary, it does provide additional context.
We continue to observe a steady increase in the use of these services. PhaaS platforms provide easy configuration for bad actors interested in conducting business email compromise (BEC). These services provide automation that can access accounts using stolen credentials, templates for phishing campaigns, and manage sending out the phishing emails. Since the platform provides these services, defenders can key off common indicators—like hosting providers used—across campaigns from each platform.
Because of Expel’s service offerings, we have a unique vantage point: we can see a wide berth of the attack cycle, and have broad visibility into phishing campaigns that are being conducted. We can see user-submitted phishing emails—which are triaged by our phishing service—and see any suspicious cloud identity activity with our SOC. With this vantage point, we can alert on authentications consistent with known phishing infrastructure and dig deeper into phishing campaigns.
What we saw
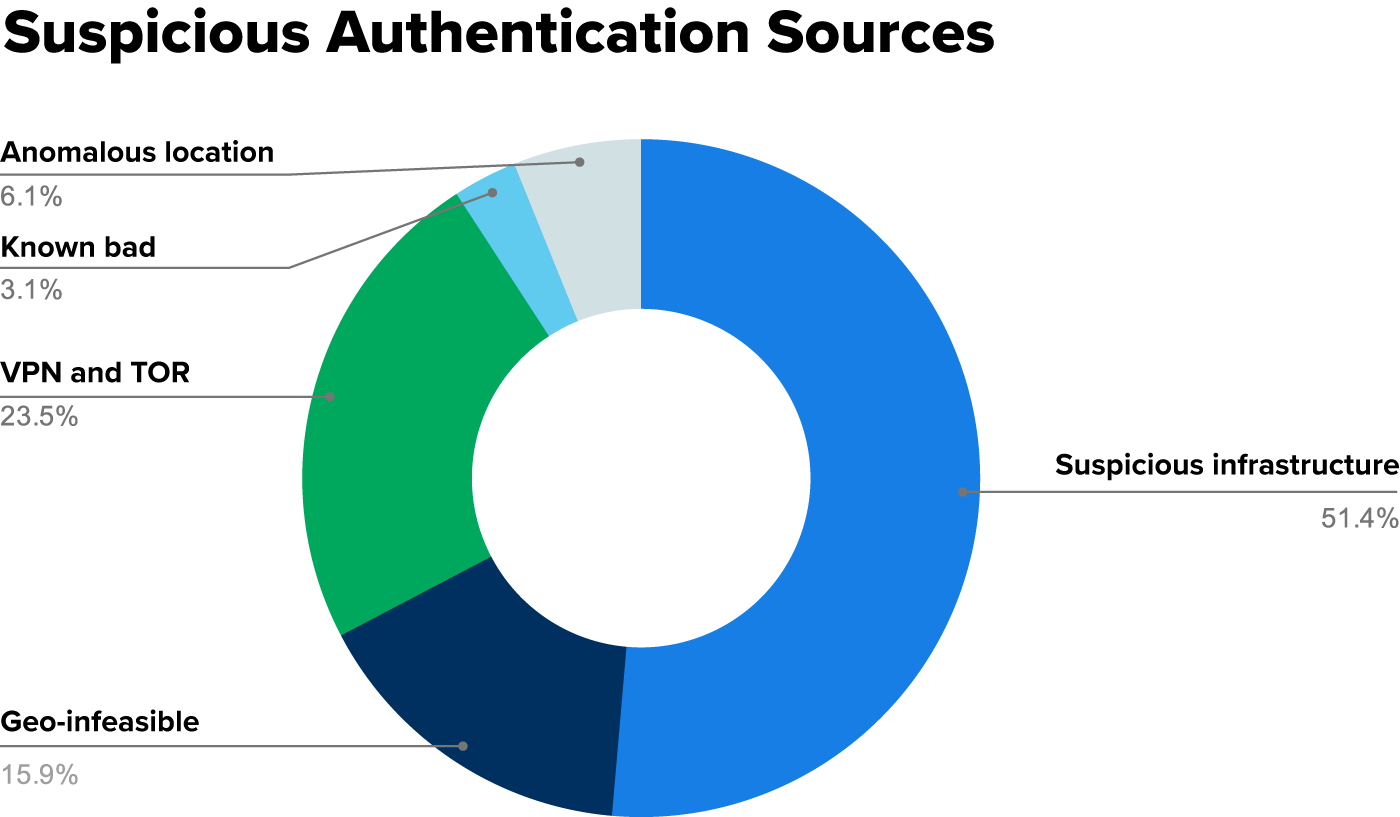
In Q2, we observed that malicious account authentications were increasingly using what we classify as suspicious infrastructure. This trend is continuing upward, increasing from 46% in Q2 of all identity incidents to 51% of all identity incidents in Q3. We define suspicious infrastructure as hosting providers and virtual private server (VPS) providers. The IP addresses associated with these hosting providers are generally categorized as having a hosting provider affiliation, rather than affiliation with an internet service provider, a virtual private network (VPN), or Tor network. Compared to normal user behavior, logins from hosting providers are considered extremely suspicious—both to our automations and to our human analysts.
The chart below looks at the source of authentication across all of the incidents in Q3.
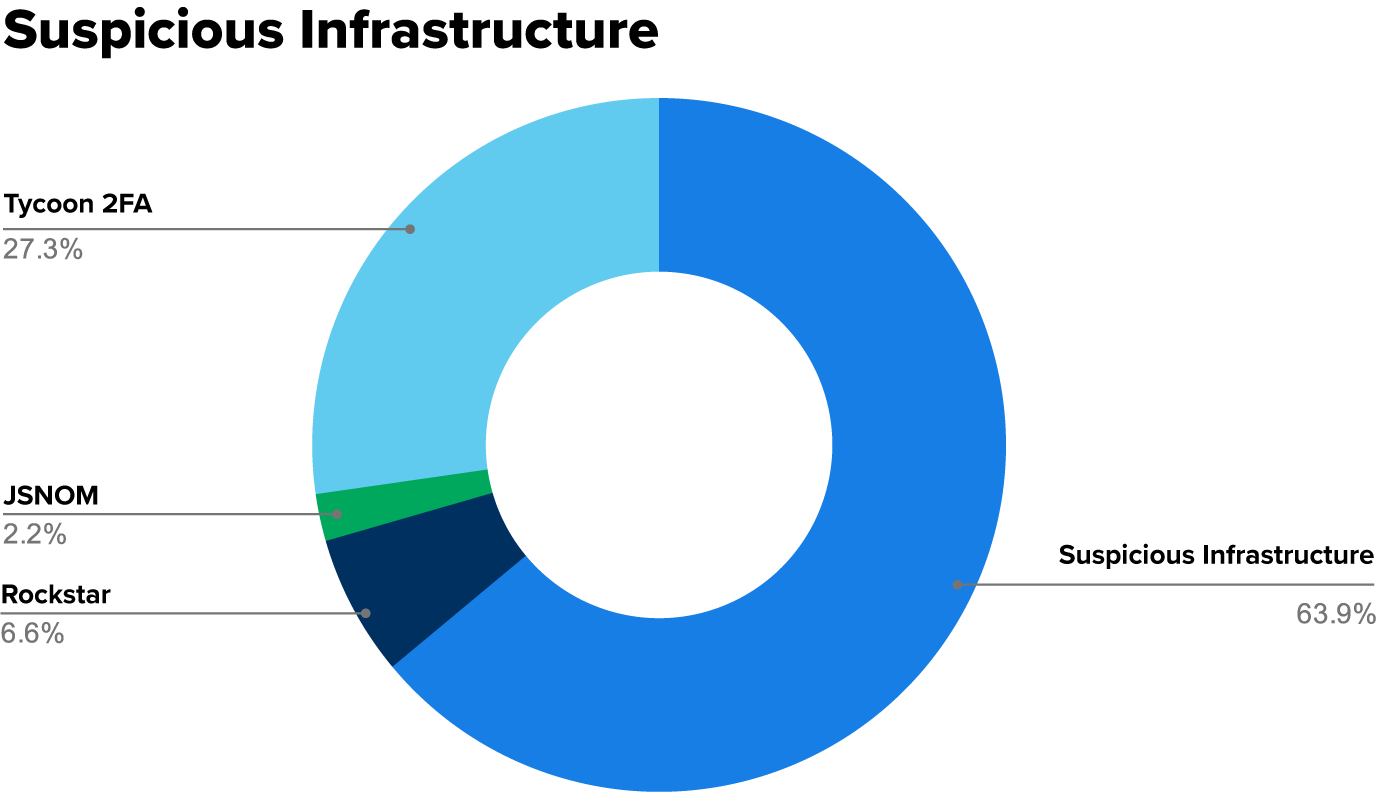
The suspicious infrastructure category can be further divided based on PhaaS providers that we’ve confidently identified.
At this time, we have consistently identified three main platforms that we observe consistently across our customer base: Tycoon 2FA, Rockstar (formerly known as Dadsec), and one we refer to—internally—as JSNOM, based on the web resources used by the credential harvester. These platforms are identified based on the body of the phishing email, the style of the credential harvesters, and hosting providers used for authenticating into compromised accounts.
When any of these identifying indicators are observed, we flag these for the SOC as known phishing infrastructure to help communicate what intelligence we have regarding these common tactics. The following chart breaks down the suspicious infrastructure category by its identified PhaaS provider.
Discerning the bad
Microsoft (and other security services) often identify authentications from hosting providers as anomalous. However, being identified as anomalous isn’t very descriptive. We recommend further enriching this alert by determining when the authentication source is a hosting provider, and treating it as extra suspicious. We do this with automation in our Expel Workbench™ platform, but you can do this too with APIs from providers such as ipinfo.io, iphub.info, AbuseIPdb, Spur, or many others.
In reviewing the activity, we compare the authentication against the user’s baseline, and also compare it against behavior from other users in the organization. When we observe the same infrastructure being used consistently across customers or industries, we often have a good indication that the infrastructure is being used maliciously.
If we then move our investigation further upstream, we can take note of patterns associated with the phishing attacks. Emails associated with the same PhaaS platform will have identical features. The phishing emails may consistently use the same obfuscation tactics.. Reviewing these allows us to implement detections on these emails to identify the emails at an earlier stage, and ensure that similar phishing emails associated with the same campaign are removed from the email inboxes of the targeted organization.
In the final post in this series, we’ll talk about risks on the horizon to the supply chain.
About these reports
The trends described in our QTRs are based on incidents our security operations center (SOC) identified through investigations, alerts, email submissions, or threat hunting leads in the third quarter (Q3) of 2024. We analyzed incidents across our customer base, which includes organizations of all sizes, in many industries, and with differing security maturity levels. In the process, we sought patterns and attacker tendencies to help guide strategic decision-making and operational processes for your team.