TL;DR
- This is part two of four of our Quarterly Threat Report blog series for Q1 2025
- You can find parts one, three, and four here post-publication
- Part two covers trends and insights against cloud-based services
As discussed in our first post, we’ve broken the attack surfaces we monitor into three distinct defensive fronts: cloud-based services, endpoint, and cloud infrastructure.
In this blog, we’ll take a closer look at cloud-based services. These apps and services are operated and maintained by third parties and hosted on their infrastructure. Think of everyday business tools such as communication apps, office suites, design tools, and so on.
These services are often the targets of bad actors because they offer a way into a corporate environment. For instance, attackers often target cloud email services in the first stage of an attack, compromising user accounts and attempting to further their attacks with this foothold.
Naturally, since many cloud-based services are run and maintained by third parties, in these scenarios, attackers see little need to attack these services head on. (Supply chain attacks notwithstanding.) And why should they concern themselves with more advanced attack techniques when they can simply log in? As a result, there are little to no signs of malware or exploitation of vulnerabilities on this front, as this space is dominated by the use of compromised credentials.
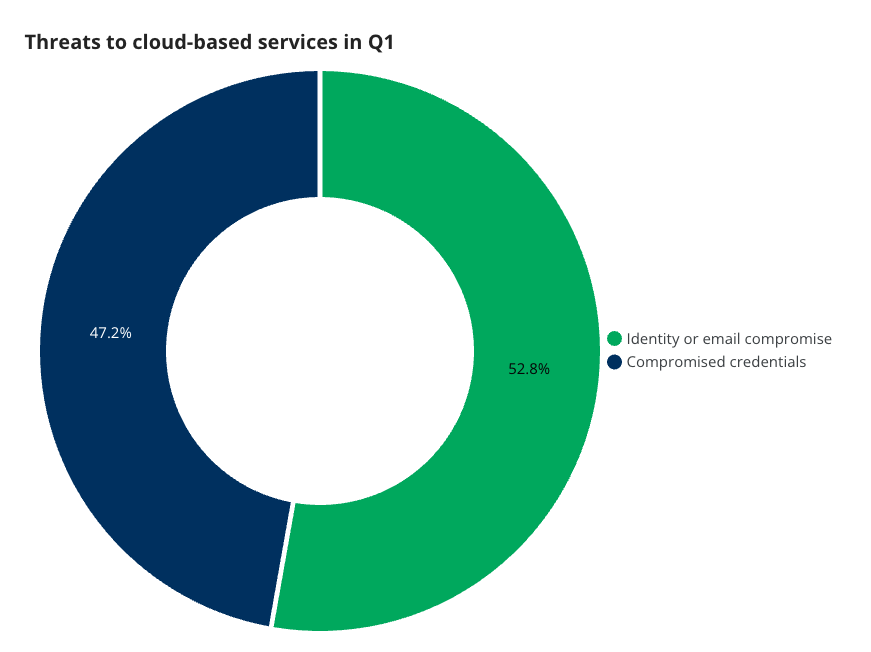
We covered this in some detail in part one, but in summary, the cloud service incidents we saw were cases where users’ identities or email accounts were either compromised directly by the attacker during the attack, or the adversary managed to obtain stolen credentials through other means. When an attacker uses those credentials, we investigate to identify for certain if they were able to gain access to the account. The following graph breaks down that success rate. More than half of the time, attackers were able to bypass security controls once they had valid credentials.
No matter how attackers acquire credentials, it’s evident they see user credentials as their keys towards eventually gaining access to the corporate kingdom.
Identity as the elephant in the room
Before going too much further, it’s worth calling out that identity based incidents have always dominated the total number of incidents we see. The scale of these attacks and their potential impact is massive, so it’s important to regularly talk about them.
Incidents classified as identity or email compromise are instances where an attacker is able to gain access to a user’s login credentials for their email or for the user’s identity provider. As organizations have adopted identity providers to manage single sign-on (SSO) and similar technologies, these incidents have become even riskier as an attacker can access arbitrary applications if they aren’t stopped.
In our experience, the most effective means of blocking these incidents are policies requiring logins to come from managed devices or using FIDO2 compliant MFA, such as passkeys. These options are essential for organizations with no tolerance for the risk of account compromise.
Incidents classified as compromised credentials are instances where a credential has been compromised, but an attacker has been blocked from accessing the account due to conditional access (or another control). Expel considers these high-risk due to the likelihood of attackers trying again—often by using a VPN or residential proxy—and levering a stolen session token. These are also risky due to credential re-use. As in, if the user has used the same password elsewhere, those accounts are also at risk.
Using the keys to access the kingdom
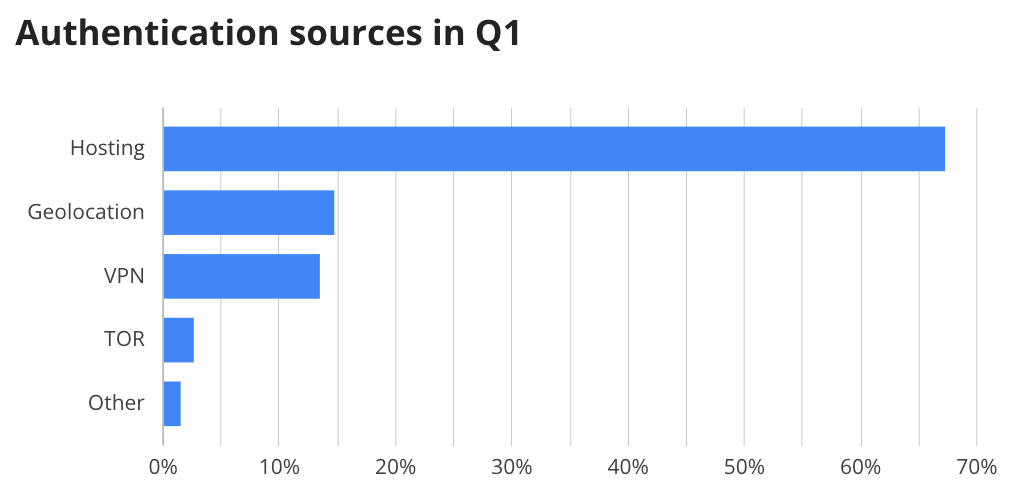
When using these credentials, bad actors often log in from a variety of sources. More often than not, the adversaries’ logins will originate from hosting providers, as opposed to internet service providers or VPNs—which is what we’d expect for most legitimate users.
A login from a hosting provider is often an indication of a phishing-as-a-service (PhaaS) platform. We’ve talked a bit about these before, but these platforms facilitate phishing campaigns and will authenticate using successfully stolen credentials and user sessions, causing the abnormal login. We’ve seen steady growth in the use of these services over the last year, as reported in our 2025 Annual Threat Report, and this trend has continued to climb this quarter, now reaching 67.3% of the total malicious logins we tracked in Q1. The other 33% of malicious logins are broken down in the table below.
Instances classified as geolocation were cases where the login attempt came from an unlikely location for the user. These came in second at 15%, and were closely followed by VPN (13.6%), where the login attempt occurred using some type of virtual private network deemed abnormal for the user.
A fine kettle of phish
When it comes to identity-related attacks bad actors leverage to access cloud-based services, phishing has long been one of the primary methods used to capture the necessary credentials. Let’s take a closer look at an analysis of end-user-identified phishing we’ve seen to learn how attackers are leveraging phishing in their most recent attacks.
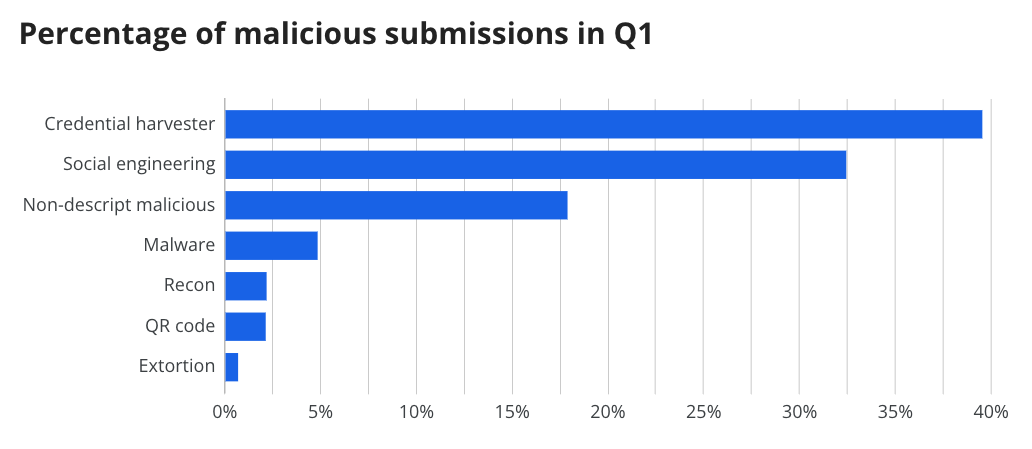
Credential harvesters remain on top, accounting for 39.7% of malicious submissions. These are emails mimicking corporate login pages and popular cloud-based services, such as online office applications or booking sites, aiming to trick users into entering their credentials.
Social engineering was the second-most common submission we saw in Q1. These emails involve the user being coerced into carrying out certain instructions for the attack to succeed. 32.3% of submissions fell into the social engineering category.
One notable submission category we saw in Q1 is what we call “recon.” These are emails designed to gather information about available users. They’re often blank, which may not arouse suspicions, as their sole purpose is to check the validity of the email addresses they are sent to. Generally speaking, these emails can be seen as a precursor to a larger attack—the adversary is finding out which emails to utilize in the next stage of their attack.
Getting the clicks
For phishing to be successful, the subjects of the emails need to entice the curiosity of the end user. Looking at the types of emails we saw in phishing attempts during Q1, the most common email subjects included password resets, financial topics, and the names of prominent business people. The most popular subject line was actually no subject line at all—it was left blank. These emails with blank subjects most commonly fell into the recon submission category. The table below highlights the top ten most common phishing email subject lines.
| Email subject line | |
|---|---|
| 1 | [blank] |
| 2 | Password Reset Request |
| 3 | Teacher Gifts: Your Top Qs Answered |
| 4 | Thai Lee |
| 5 | SharePointOnline |
| 6 | Status and Invoice-Due |
| 7 | Thank you for connecting with The Join Commission! |
| 8 | Shankh Mitra |
| 9 | Help Recovering Money and Damages From Electrical Utility Company |
| 10 | Returned mail: see transcript for details |
| Sender domain | Percent | |
|---|---|---|
| 1 | gmail.com | 13.3% |
| 2 | dropbox.com | 1.6% |
| 3 | hotmail.com | 1% |
| 4 | docusign.net | 1.2% |
| 5 | paypal.com | 1.6% |
| 6 | outlook.com | 0.6% |
| 7 | icloud.com | 0.6% |
| 8 | aol.com | 0.4% |
| 9 | salesforce.com | 0.5% |
| 10 | yahoo.com | 0.3% |
Up next, we’ll take a deep dive into incidents involving endpoints and trends we’ve observed on this attack surface. If you have questions about what you’ve seen here, drop us a line.