Table of Contents
Cloud security is a comprehensive set of policies, technologies, controls, and services designed to protect cloud-based systems, data, and infrastructure from cyber threats. As organizations increasingly migrate their operations to cloud environments, understanding and implementing robust cloud security measures has become essential for protecting sensitive data, maintaining compliance, and ensuring business continuity.
According to the National Institute of Standards and Technology (NIST), organizations must adapt their security frameworks to address the unique challenges of cloud computing environments.
With over 80% of businesses expected to adopt a cloud-first strategy by 2025, the need for comprehensive cloud security has never been more critical. Unlike traditional on-premises security, cloud security addresses unique challenges such as shared responsibility models, multi-tenancy, and the dynamic nature of cloud environments.
What is meant by cloud security?
Cloud security encompasses all the security measures, processes, and technologies used to protect data, applications, and services that operate in cloud computing environments. This includes protection for Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) deployments across public, private, and hybrid cloud configurations.
At its core, cloud security addresses both the protection of data stored in the cloud and the security of the connections and access points to that data. Cloud computing involves the delivery of numerous computing services, including storage, databases, servers, networking software, and analytics over the Internet. Each of these services requires specific security considerations and protections.
The concept operates on a shared responsibility model where cloud service providers (CSPs) are responsible for securing the underlying infrastructure, while customers are responsible for securing their data, applications, and user access within the cloud environment.
Core concepts of cloud security
Understanding cloud security requires grasping several fundamental concepts that differentiate it from traditional cybersecurity approaches:
| Core concept | Description | Example |
|---|---|---|
| Shared responsibility model | Division of security responsibilities between CSP and customer | AWS secures infrastructure; customer secures data and applications |
| Identity and access management (IAM) | Controls who can access cloud resources and what they can do | Multi-factor authentication, role-based access controls |
| Data encryption | Protection of data both at rest and in transit | AES-256 encryption for stored files, TLS for data transmission |
| Configuration management | Ensuring cloud resources are properly configured for security | Security groups, network access control lists, firewall rules |
| Continuous monitoring | Real-time detection of threats and anomalous behavior | CloudTrail logging, security information and event management |
| Compliance management | Meeting regulatory and industry security standards | SOC 2, HIPAA, PCI DSS, GDPR compliance requirements |
These concepts work together to create a comprehensive security framework that adapts to the dynamic nature of cloud environments while maintaining strong protection against evolving cyber threats.
Ready to enhance your cloud security posture? Explore Expel’s cloud security services for comprehensive protection across AWS, GCP, Azure, and more with 24×7 expert monitoring and AI-driven threat detection.
What are the 4 types of cloud security?
Cloud security can be categorized into four main types, each addressing different aspects of cloud protection:
1. Infrastructure security
Infrastructure security focuses on protecting the underlying cloud infrastructure, including servers, networks, and data centers. This involves securing the physical and virtual components that make up the cloud environment.
Key elements include:
- Virtual machine security and hardening
- Network segmentation and firewall management
- Hypervisor security
- Physical data center security (typically managed by CSP)
- Infrastructure as Code (IaC) security scanning
2. Application security
Application security addresses the protection of cloud-hosted applications throughout their development and runtime lifecycle. This type of security ensures that applications running in the cloud are protected from vulnerabilities and attacks.
Components include:
- Secure coding practices and code reviews
- Application vulnerability assessments
- Web application firewalls (WAF)
- API security and management
- Container and microservices security
3. Data security
Data security focuses on protecting information stored, processed, and transmitted in cloud environments. This is often considered the most critical aspect of cloud security since data is typically the primary target of cyber attacks.
Key measures include:
- Data encryption at rest and in transit
- Data loss prevention (DLP) solutions
- Data classification and labeling
- Database security and access controls
- Backup and disaster recovery planning
4. Identity and access security
Identity and access security manages who can access cloud resources and what actions they can perform. This type of security is fundamental to maintaining control over cloud environments.
Elements include:
- Multi-factor authentication (MFA)
- Single sign-on (SSO) solutions
- Privileged access management (PAM)
- Zero-trust network access
- Identity governance and compliance
Looking to secure your AWS environment? Check out Expel’s AWS cloud security solutions with tailored detections, cross-environment correlation, and dedicated cloud expertise.
Which tool is commonly used in cloud security?
Cloud security relies on various specialized tools, but some categories are more commonly deployed than others. Based on current industry trends and adoption rates, here are the most prevalent types of cloud security tools:
| Tool category | Purpose | Common examples |
|---|---|---|
| Cloud Security Posture Management (CSPM) | Automate discovery and remediation of misconfigurations | AWS Security Hub, Azure Security Center, Prisma Cloud |
| Cloud Access Security Broker (CASB) | Control access between users and cloud services | Microsoft Cloud App Security, Netskope, Zscaler |
| Identity and Access Management (IAM) | Manage user identities and access permissions | AWS IAM, Azure Active Directory, Okta |
| Cloud Workload Protection Platform (CWPP) | Protect cloud workloads including VMs and containers | Trend Micro Cloud One, Aqua Security, Sysdig |
| Security Information and Event Management (SIEM) | Collect and analyze security events from cloud environments | Splunk, IBM QRadar, Azure Sentinel |
CSPM tools automate the identification and remediation of risks across cloud infrastructures. They provide continuous monitoring and compliance checks, helping organizations to maintain a secure cloud posture. These tools are particularly valuable because about 15% of cybersecurity breaches have been caused by cloud misconfigurations.
The most effective cloud security strategies typically combine multiple tool categories to provide comprehensive coverage across all aspects of cloud protection.
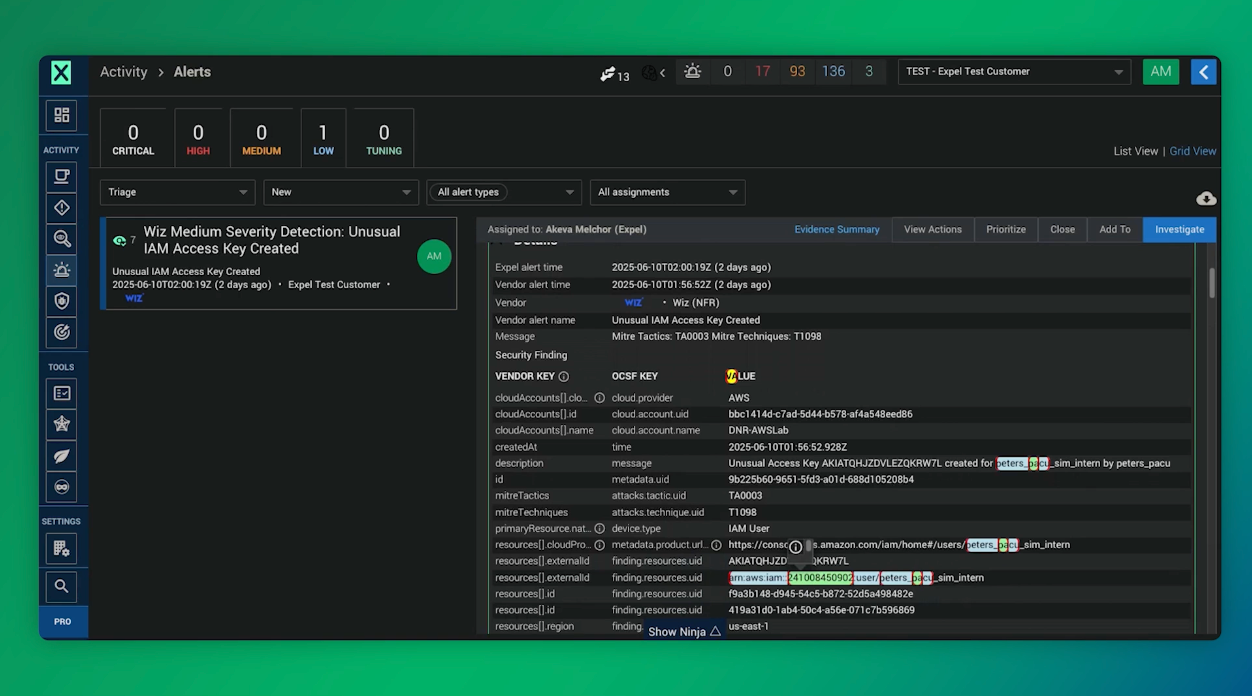
What are the main categories of cloud security?
Cloud security tools and solutions fall into several main categories, each addressing specific security needs and challenges:
Detection and response tools
These tools focus on identifying and responding to security threats in real-time:
- Cloud Detection and Response (CDR): By continuously analyzing cloud activities, CDR tools also play a vital role in the incident response process, ensuring that security teams can quickly address vulnerabilities and attacks.
- Extended Detection and Response (XDR): Provides unified threat detection across multiple security layers
- Security Orchestration, Automation and Response (SOAR): Automates incident response processes
Configuration and compliance management
Tools that ensure cloud environments are properly configured and compliant:
- Cloud Security Posture Management (CSPM): Continuous monitoring for misconfigurations
- Infrastructure as Code (IaC) scanning: Security assessment of cloud infrastructure templates
- Compliance monitoring: Automated checks against regulatory frameworks
Identity and access control
Solutions that manage who can access cloud resources:
- Cloud Infrastructure Entitlement Management (CIEM): CIEM solutions manage access entitlements and permissions in cloud environments, preventing excessive privileges and access rights.
- Privileged Access Management (PAM): Controls administrative access to critical systems
- Zero Trust Network Access (ZTNA): Verifies every access request regardless of location
Data protection and privacy
Tools focused on protecting sensitive information:
- Data Security Posture Management (DSPM): DSPM tools are used for monitoring and securing data across cloud environments. They focus on identifying and mitigating risks related to data storage, access, and transfer in cloud platforms.
- Cloud Access Security Broker (CASB): Enforces security policies for cloud applications
- Data Loss Prevention (DLP): Prevents unauthorized data exfiltration
Application and workload protection
Security solutions for cloud-hosted applications:
- Cloud Workload Protection Platform (CWPP): Protects VMs, containers, and serverless functions
- Container security: Specialized protection for containerized applications
- API security: Protects application programming interfaces from attacks
Need comprehensive cloud detection and response? Learn about Expel’s cloud security services that provide continuous expert monitoring, broad cloud coverage, and AI-driven insights across AWS, GCP, Azure, and more.
Do I need cloud security?
The short answer is yes—if your organization uses any cloud services, you need cloud security. The question isn’t whether you need it, but rather how comprehensive your cloud security strategy should be based on your specific risk profile and cloud usage.
Why cloud security is essential
Several factors make cloud security a necessity rather than an option:
Rising threat landscape: About 45% of security incidents are reported to have originated from cloud environments, which calls for enhanced security measures. This statistic alone demonstrates the critical importance of dedicated cloud security measures.
Financial impact: The average cost of a data breach has increased to $4.88 million in 2024, making prevention significantly more cost-effective than dealing with the aftermath of a breach.
Compliance requirements: Most industries have regulatory requirements that extend to cloud environments. The Cloud Security Alliance (CSA) provides comprehensive guidance on cloud security best practices and compliance frameworks that organizations must consider.
Shared responsibility confusion: Many organizations mistakenly believe their cloud service provider handles all security aspects, but CSPs only secure the infrastructure—not your data, applications, or user access.
Assessing your cloud security needs
Consider these factors when determining your cloud security requirements:
| Factor | Low risk | High risk |
|---|---|---|
| Data sensitivity | Non-sensitive business data | PII, financial records, healthcare data |
| Cloud usage | Single SaaS application | Multi-cloud, complex infrastructure |
| Regulatory requirements | Minimal compliance needs | HIPAA, PCI DSS, SOX compliance |
| Business impact | Low impact if compromised | Mission-critical systems |
| User access | Few internal users | Many users, external partners |
Even organizations with relatively simple cloud usage should implement basic security measures such as multi-factor authentication, encryption, and access controls.
What is the difference between cyber security and cloud security?
While cloud security is a subset of cybersecurity, there are important distinctions between the two disciplines:
Scope and focus
Cybersecurity is the comprehensive practice of protecting digital systems, networks, and data from cyber attacks, regardless of where they’re located. It encompasses protection for on-premises systems, mobile devices, networks, and cloud environments.
Cloud security specifically focuses on protecting data, applications, and services that operate in cloud computing environments. It addresses the unique challenges and opportunities that cloud computing presents.
Key differences
| Aspect | Traditional cybersecurity | Cloud security |
|---|---|---|
| Infrastructure control | Full control over physical and virtual infrastructure | Shared responsibility with cloud service provider |
| Perimeter definition | Clear network perimeter with defined boundaries | Fluid perimeter that changes with cloud resources |
| Scalability | Manual scaling with physical hardware limitations | Rapid, automatic scaling requires dynamic security |
| Visibility | Direct access to logs and system information | Relies on APIs and cloud provider logging services |
| Compliance | Direct control over compliance implementations | Must work within CSP compliance frameworks |
| Incident response | Full control over investigation and remediation | Collaboration with CSP may be required |
Complementary relationship
Rather than being separate disciplines, cloud security and traditional cybersecurity work together as part of a comprehensive security strategy. Organizations typically need both:
- Traditional cybersecurity for on-premises systems, endpoints, and network infrastructure
- Cloud security for cloud-hosted applications, data, and services
- Hybrid security approaches that bridge on-premises and cloud environments
Securing hybrid environments? Discover Expel’s managed detection and response services that protect organizations from cloud to ground with 130+ integrations and 24×7 expert monitoring.
Cloud security trends and challenges in 2025
The cloud security landscape continues to evolve rapidly, with several key trends shaping how organizations approach protection:
Emerging trends
AI-driven security: AI-driven threat detection and response are transforming cybersecurity and cloud security in 2025 by enabling real-time analysis of large amounts of data to identify abnormal behaviors and potential threats.
Zero trust architecture: The zero-trust model remains a linchpin of cloud security in 2025, reflecting a shift from trusting authenticated users to verifying identities continuously at every stage.
Unified security platforms: 97% of respondents prefer unified cloud security platforms with centralized dashboards to simplify policy configuration, ensure consistency, and enhance visibility across an organization’s cloud footprint.
Key challenges
Organizations face several significant challenges in implementing effective cloud security:
Skills shortage: 76% of organizations report a shortage of expertise in cloud security, highlighting the need for automation, targeted upskilling, and resource optimization.
Multi-cloud complexity: Over 78% of respondents utilize two or more cloud providers, underscoring the growing importance of multi-cloud approaches to enhance resilience and leverage specialized services.
Configuration errors: 81% of organizations have public-facing assets that are neglected. These are cloud systems running outdated software or left unpatched for 180 days or more, often with open ports that are easy targets for bad actors.
Real-time threat detection: 64% of respondents lack confidence in their organization’s ability to handle real-time threat detection.
The MITRE ATT&CK Framework provides valuable guidance for understanding cloud-specific attack techniques and developing appropriate defensive strategies for cloud environments.
Best practices for cloud security implementation
Implementing effective cloud security requires a systematic approach that addresses all aspects of cloud protection:
1. Establish a cloud security strategy
- Define clear security policies for cloud usage
- Implement a cloud governance framework
- Establish roles and responsibilities for cloud security
- Create incident response procedures for cloud environments
2. Implement strong identity and access management
- Deploy multi-factor authentication for all cloud access
- Use role-based access controls (RBAC) with least privilege principles
- Implement single sign-on (SSO) where appropriate
- Regularly review and audit user permissions
3. Secure cloud configurations
- Use Infrastructure as Code (IaC) for consistent, secure deployments
- Implement automated configuration scanning and remediation
- Follow cloud service provider security best practices and CIS Benchmarks for secure configuration
- Regularly audit cloud resource configurations
4. Protect data throughout its lifecycle
- Encrypt data at rest and in transit
- Implement data classification and handling procedures
- Use data loss prevention (DLP) solutions
- Maintain secure backup and recovery processes
5. Enable continuous monitoring and detection
- Deploy cloud-native security monitoring tools
- Implement security information and event management (SIEM)
- Use behavioral analytics to detect anomalous activities
- Establish automated alerting and response procedures
Need expert guidance for cloud security implementation? Contact Expel’s security specialists to discuss how our comprehensive cloud security services can protect your organization across all major cloud platforms.
Cloud security FAQ
How much does cloud security cost?
Cloud security costs vary significantly based on the size of your environment, the complexity of your cloud architecture, and the level of protection required. Factors influencing cost include:
- Number of cloud accounts and resources
- Types of security tools and services needed
- Compliance requirements
- Internal staffing vs. managed services
Many organizations find that investing in cloud security is cost-effective compared to the potential impact of a data breach, which averages $4.35 million according to IBM’s Cost of a Data Breach Report.
Can I use the same security tools for cloud and on-premises?
While some traditional security tools can work in cloud environments, cloud-specific tools are often more effective because they’re designed to address the unique challenges of cloud computing, such as:
- API-based management and monitoring
- Dynamic scaling and ephemeral resources
- Shared responsibility model considerations
- Cloud-native threat vectors
How do I know if my cloud environment is secure?
Regular security assessments should include:
- Configuration reviews and compliance scans
- Vulnerability assessments and penetration testing
- Access reviews and permission audits
- Security monitoring and incident response testing
- Third-party security assessments
What happens if my cloud provider has a security breach?
Cloud providers typically have extensive security measures and incident response procedures. However, the impact depends on the shared responsibility model:
- CSP breaches affecting infrastructure are usually handled by the provider
- Data breaches may still be the customer’s responsibility depending on the cause
- Always have incident response plans that account for both scenarios
Is it safe to store sensitive data in the cloud?
Yes, when properly secured. Cloud environments can be as secure as, or more secure than, on-premises systems when appropriate security measures are implemented. Major cloud providers like Amazon Web Services, Microsoft Azure, and Google Cloud Platform invest billions in security infrastructure and maintain numerous compliance certifications. Key considerations include:
- Proper encryption and key management
- Strong access controls and authentication
- Compliance with relevant regulations
- Regular security monitoring and assessment
Getting started with cloud security
Implementing comprehensive cloud security doesn’t have to be overwhelming. Start with these foundational steps:
1. Assess your current cloud usage
- Inventory all cloud services and applications in use
- Identify where sensitive data is stored and processed
- Document current security measures and controls
- Evaluate compliance requirements and gaps
2. Prioritize your security investments
- Focus on high-risk areas first (sensitive data, critical applications)
- Implement basic security hygiene (MFA, encryption, access controls)
- Address compliance requirements
- Plan for advanced security capabilities as you mature
3. Consider managed security services
Given the complexity of cloud security and the shortage of skilled professionals, many organizations benefit from partnering with managed security service providers who specialize in cloud protection.
4. Develop ongoing security practices
- Establish regular security assessments and reviews
- Implement continuous monitoring and alerting
- Maintain incident response capabilities
- Provide security training for cloud users
How Expel enhances cloud security
At Expel, we provide comprehensive cloud security through our managed detection and response platform. Our approach combines AI-driven threat detection with expert analysis to protect organizations across AWS, Google Cloud Platform, Microsoft Azure, and other cloud environments.
Expert-written detections: Our platform ingests billions of events and continuously writes new detections based on threats we observe across our entire customer base, providing you with the most current protection against evolving cloud threats.
Rapid response: We achieve an industry-leading 14-minute mean time to remediate for high and critical incidents, with full transparency into our detection and response processes.
By combining world-class security practitioners with our AI-driven Expel Workbench platform, we help organizations achieve comprehensive cloud security without the complexity of building these capabilities in-house.
Ready to strengthen your cloud security posture? Explore Expel’s comprehensive managed detection and response services that provide 24×7 protection across cloud, Kubernetes, endpoints, and SaaS environments.




