Tips · 10 MIN READ · YANEK KORFF · OCT 22, 2019 · TAGS: CISO / Managed security / Management / MDR
Back in 1972, in an effort to help its people deal with rising food prices and promote healthy choices, the National Board of Health and Welfare (Socialstyrelsen) in Sweden came up with a model of “basic” and “supplementary” foods. This model was refined into a triangle shape to help people visualize proportions a little better by Anna Britt Agnsäter, whose goal was to improve people’s dietary habits. This design spread gradually across the world hitting Australia in the 1980s and finally, the United States adopted a version of the pyramid in 1992.
We know now that the design was pretty terrible, and there have been several revisions since. Nevertheless, it was widely understood and widely adopted. As with most things, the primary driver for this adoption was that it was a simple message, frequently repeated. And while the model has (ahem) shortcomings, it did have some positive impacts including raising awareness about dietary health and getting people to think about portion sizes.
You may be wondering how food and cybersecurity are related. (It’s not just because I haven’t yet eaten breakfast.)
We’re facing the same sort of challenge in cybersecurity today as they were in Sweden back in the 1970s. Whether you’re a business or an individual, cybersecurity is some combination of complicated and expensive — both of which will demotivate you to do anything about it. Meanwhile, we’ve got massive FUD-based marketing campaigns that say little more than, “The bad guys are out to get you so you’d better spend lots of money!”
The cybersecurity patchwork we live under
Why are we in this state? Because there’s widespread disagreement around the cybersecurity fundamentals that help keep us safe.
This inconsistent application of basic cybersecurity practices creates a wonderful environment for organized adversaries to accomplish their missions — whether that’s stealing financial info or mucking with critical infrastructure.
I was on Capitol Hill a few months ago and lost track of the number of times I heard the phrase “rising tide” in relation to cybersecurity. We don’t yet have it. But we need it. Security one percenters (those with proportionally unlimited budgets) can find and retain talent and implement just about anything. Large enterprises can often afford a solid combination of security products and services to build a relatively effective security response strategy.
Everyone else? They struggle to build an effective security posture … whether it’s because of technology, hiring the right people or building the right bridge between the two.
The consequences of being in the “everyone else” boat are clear. Just look at the litany of breach reports hit the headlines only to be swallowed by bigger ones a few months or weeks later. And those are only the ones that get reported. Once in a while you’ll see a big company name … but more often the problem strikes further down in the mid-market. In fact, as most attackers have discovered at this point that it’s easier to get to large companies by attacking their less prepared suppliers. Larger enterprises push on their supply chains these days with long lists of high-level security questions as if their compliance will increase the chances of their security. (Spoiler alert: It doesn’t.)
There’s no shortage of recommendations. CIS security controls? Check. CISA guidance? Sure. Best practices for cloud security? You bet. The NIST CSF will help you work through decisions to improve your security posture. Yet the challenge most organizations face isn’t with knowing what to do, it’s the challenge of getting all those to-dos done.
The biggest challenge with cybersecurity? It’s not a lack of tech. Or a lack of “best practices.” It’s the business.
We’re approaching this wrong
It’s because the business can’t handle the disruption of turning off macros in excel documents that are downloaded from the Internet. The business isn’t willing to deal with the hassle that two-factor authentication introduces into people’s daily lives. A password manager? No way — the business is perfectly happy with sticky notes. Besides, after years of unreasonable password requirements, the business isn’t interested in jumping over your newest hurdles.
I’ve got a secret to share about the business. Like Soylent Green, the business is people! Some faceless business didn’t decide it needed to gradually increase its use of Apple mobile devices and laptops in the traditionally Wintel office environment. People did. You and I started using these devices at home and brought them into the workplace, gradually (but significantly) bolstering Apple’s success in the enterprise space.
Cybersecurity needs to vector into the enterprise in the same way. This is where the food pyramid comes in … or something like it. When you’re trying to drive a change like this — getting the business to care about security — success demands two things: people need to understand how making a change will help them and those changes need to be easy to remember.
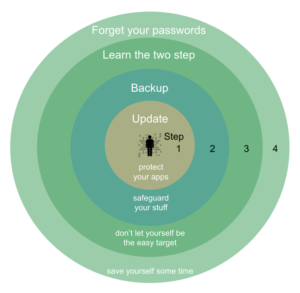
We need to encourage (just) four things
I’m asking people to do four things, in order.
The set of recommendations below come in two parts: one way to effectively communicate the recommendation to a broad audience, and the justification for why each is a recommendation in the first place.
Remember that the more recommendations we add, the less likely they’ll be remembered — and one “must do” of any cybersecurity framework is to make sure that the guardrails you’re coming up with are things that the business will actually do.
#1: Update
If you’re not up to date, you’re out of date — or so the saying goes. Or if it’s not a saying, it should be. Did you know that you can keep your data safe by doing nothing more than keeping your stuff up to date? Turns out that large companies in the headlines can often point to not-updating as the reason why they were breached. Save a lot of heartache and stay up to date.
Why update?
When I say “update,” you might think, “He surely means ‘patch.’”
But I’m not calling it patching. Patching has an innately negative connotation. It’s not a “fix,” it’s just a temporary “patch.” While that may be true since we’re talking about software, if the objective is to motivate action, “update” encourages the same behavior without the associated baggage.
Long-time information security practitioners will be unsurprised to hear that from 2016 to 2017, 60 percent of orgs that suffered a data breach can point to a known vulnerability as the reason for the breach. These vulnerabilities may allow direct access into an enterprise system to an external attacker, or could be paired with a phishing scheme that uses a malicious attachment to exploit a vulnerability local to the user’s machine. Adobe has the privilege of holding the top four slots (as I write this) on the Top 50 Products By Total Number Of “Distinct” Vulnerabilities in 2019. Several Microsoft ones shortly after that. You running any Adobe or Microsoft software in your enterprise? Yeah, I thought so.
Over the past several years, there have been arguments crop up from time to time advocating caution against patching … or at least automatic patching. Remember, we’re not talking about defining the best enterprise patching strategy here. We’re trying to build a culture amongst non-security people that they err on the side of turning on automatic updates wherever they go. As computer users, we should want software to be automatically updated. Because once in a blue moon, if something goes wrong, the user pushback becomes overwhelming to deal with. What if we were all on the same side? Let’s all be irate if patches break and demand better from vendors.
#2: Backup
It’s heartbreaking to lose precious data. Pictures you’ve taken over the past several years, old emails you’ve been keeping around for nostalgia’s sake, those few letters you’ve written … these are just as important to you as your yearbooks, old postcards, and other keepsakes in your home. Safeguard your data by using a backup service for your computer. Should your computer go up in smoke, you’ll always be able to get your files back.
Why backups?
Ransomware’s run rampant through businesses in the past several years, particularly because it’s been so successful and it’s substantially cheaper to pay the ransom than it is to hire consultants to fix the problem afterward. This then funds both a higher volume of adversaries and more sophisticated attack methods. It’s the gift that keeps on giving … to the bad guys. Turns out one of the simple and effective ways to protect against it is to have a backup of your data.
Should you test your backups? Of course. But the first step is actually backing up the data. Some argue that an untested backup is no backup — but it misses a crucial point. It’s entirely possible that an untested backup is just fine. You just don’t know. Introducing another hurdle before getting people to buy into doing a backup in the first place isn’t a good idea.
#3: Learn the two step
There’s a 1-in-170 chance that one of your social media accounts will be taken over by someone else today if you’re using only a password. The odds aren’t in your favor. Most people spend days apologizing to friends for things they didn’t even do (including tricking them into transferring money). Skip the hassle and turn on two-factor or two-step authentication.
Why not multi-factor authentication?
No, two-factor authentication and two-step authentication are not the same thing. Yes, I’m equally aware that SMS-based methods are substantially less secure than their app-centric counterparts.
The point is to start small. Let them discover the flaws after accepting the notion of “two things” and go from there. But even adopting two-step authentication over SMS is a stronger stance than using only a password.
It’s important to drive home the message of safety here. Unintended accidents happen. Send a “herd immunity” message. Despite evidence to the contrary, it works.
#4: Forget your passwords
Save time logging in anywhere by skipping the username and password prompt. Install a password manager. It’ll generate passwords for you, log you in with one click, and keep your account much safer. When your favorite website tells you they lost your password to hackers, you can change just one password instead of a dozen because password managers help you use a unique password on every website (that you don’t even have to memorize).
Why password managers?
I won’t list all the problems with passwords, but there are many. Multi-factor authentication goes a long way to improving the situation here, as do alternative methods for authentication like biometrics. Recovering from a compromised account is bad enough, but dealing with constantly changing passwords for sites whose accounts have been compromised en masse is a pain. Considering that most people reuse passwords, this threat surface is huge.
Beyond the security reasons for using a password manager, though, is the fact that it actually makes it easier to deal with all your accounts. Most password managers act like bookmarks and will log you into sites automatically with one click.
That said, it can be a huge mental shift for people. So what will it take to be convincing? Keep reading.
Stick to some messaging themes
Maybe you buy the arguments above, maybe you don’t. Regardless, I’d like to offer some thinking around why these recommendations are expressed in this way.
The TL;DR: It’s all about making your employees feel that these (few) recommendations are easy for them to remember and follow. Because then they’ll be more likely to put them into practice.
Make it personal
When you’re selling these ideas, it’s critical to make it clear that we’re talking about your apps (software), your stuff (data) and yourself (your identity, time, and money). Making this personal creates a stronger connection with the recommendations. You know how Apple creates a connection when you walk into a store? They intentionally angle the screens of their laptops so the first thing you do is adjust it — you touch the machine. When it’s about you, you’re more likely to take action.
Safety over security
The pedantic will argue that “security” is the right word to use here. But I’ve had enough conversations with people who say, “that would never happen to me,” that tells me safety is the better word. In case you’re not caught up on the difference, general consensus appears to be that “safety” is about protecting against unintended threats, while “security” is about protecting against intentional ones. While most people don’t believe in intentional threats, they’re willing to make accommodations for unintentional ones to avoid becoming collateral damage.
No buzzwords
Instead of telling people to “use multi-factor authentication” or “install a password manager,” introduce a catchy phrase that says what to do and how you’ll benefit — in everyday language.
Some symmetry
Notice the two recommendations pair. The first two, updates and backups, speak to keeping your data safe. In the former case, you’re protecting your data by making it hard for people to break into your apps. In the latter case you’re protecting your data by making a copy of it. The second two recommendations are about keeping people away from your stuff with effective (and in the latter case, time-saving) authentication.
No red
I’ll grant you that working at Expel gives me a particular predisposition to green. Still, we have enough red, grey and black in the security space and what people need is a path towards a safer tomorrow versus campaigns full of FUD with photos of attackers wearing hoodies. This reminds me of parenting toddlers: don’t tell them what not to do, tell them what to do instead.
What’s next?
Remember our premise: the business is people and you need to drive change in people’s behavior.
Frankly, most people don’t care much about the overall security of the company in which they work. You might — if you’re on the security team.
Everyone else, though, has a job to do and they care much more about that than the security implications of sending an email or hosting a Zoom meeting. Or worse: They think security might get in the way of getting their stuff done.
If you really want to drive better security awareness, forget the business. Promote individual security. Promote basic behaviors that people can start doing at home and then they can bring those same practices into the office. Convince people to care about their own email and social media accounts. Help people understand the costs and hassles associated with identity theft or simple loss of data, and provide the tools for them to secure their personal lives. At scale, they’ll bring this mindset back into the office and together will drive a rising tide.
Having a message is the first step, and we’ve talked a lot about what that might look like. Simplifying it is step two — and I’m not convinced we’re there yet — but perhaps you can take the messages above and move in that direction. Once you’re there, the third step is repeating it frequently enough and in sufficiently unique ways that the message resonates. The marketing rule of 7, if you will.
It’s cybersecurity awareness month this month and it’s a great time to roll out this sort of campaign in your org.
Will you join us and help drive a rising tide?