Security operations · 5 MIN READ · BRUCE POTTER · AUG 25, 2020 · TAGS: CISO / Managed security / Management / MDR / SIEM
Updated on July 3, 2023
Maybe you’ve already got a SIEM and you’re looking for help managing it. Maybe you’re thinking of buying a SIEM and concerned it might be too much to handle on your own. Or maybe you’re using an MSSP and thinking of gaining more control of your data by working collaboratively in your SIEM rather than letting them do all the work.
However you’ve arrived at the concept of “co-managed SIEM,” there are a number of potential pros and cons to consider when making your decision. It’s important to really understand what you’re going to get out of a co-managed SIEM—it’s a big resource and dollar commitment, and mistakes made early on can take a long time to correct.
Our team encounters a lot of co-managed SIEM myths, and in this post I’ll share the most common ones, along with our perspective on the actual realities.
First, here’s a general idea of how we might assign roles at Expel:
| Roles and responsibilities with third-party security partner |
|---|
| Responsibility | Co-Managed SIEM | Expel |
|---|---|---|
| System Upgrades | Provider | You |
| Log Source Onboarding | Both | You |
| Health Monitoring | Both | Expel |
| Rule Management | Both | Expel |
| Alert Triage & Investigation | Both | Expel |
| Reporting | Both | Expel |
| Remediation | You | You |
5 perceived benefits of co-managed SIEM
Myth: It’s the only way to get transparency.
One of the biggest benefits people want from co-managed SIEM is visibility into their security operations. By working with a partner in your SIEM, you maintain some control over the detection rules that are in place, the sources of data and what your analysts are doing (regardless of whether they’re YOUR analysts or your partner’s analysts).
Reality: There are other (better) ways to get transparency.
We strongly believe that you can’t build trust without transparency. It’s key to being a good partner to our customers. It’s also vital for efficiency and accuracy. So we’ve put a lot of thought into what transparency should look like in practice.
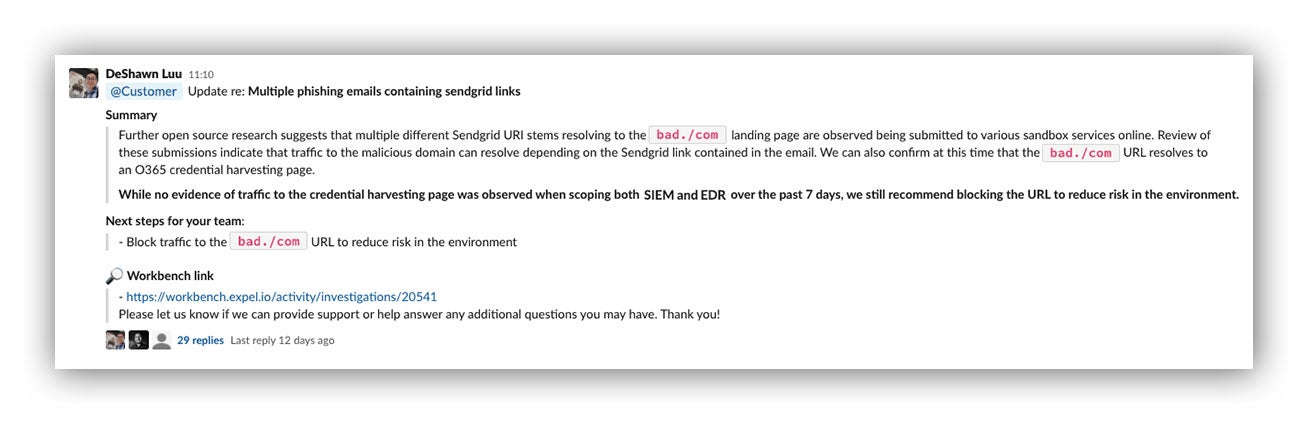
At Expel, we provide our customers with complete visibility into our analysis and investigations—in fact, we invite all our customers to watch what we’re doing in Expel Workbench or talk with us in a dedicated Slack channel as an incident unfolds. We literally work alongside your analysts to prosecute events and respond to incidents.
Example conversation in Expel’s customer Slack channel
Further, you can review all activity to check our work … make sure you agree with what we’ve done and help improve detection and response capability.
We want all third-party security providers to be held to the same account, since this is what we’d expect from any MSSP we deal with (we’re a customer of ourselves, so it works out great for us).
Myth: Greater control over business logic produces more detection value.
Your SIEM is the codification of business logic you use to detect specific threats inside your organization. Custom rules and configurations allow you to look for attacks tailored to your systems and architectures. A co-managed SIEM allows you to continue to maintain this business logic.
Reality: The vast majority of what you detect is the same as your peers and many other companies.
Orgs think they want more control to write rules and generate alerts, but they don’t realize how much it costs to manage detection content. Unless you invest a lot in this area, you’ll end up with a pile of false positives.
In reality, your rules probably aren’t as unique as you think. Your provider has an advantage since it sees the big picture (aka lots of customers) and has the expertise to manage the detection content.
However …
You should expect your security provider to tailor their detection strategy for you to your business. This could mean fine-tuning rules that already exist, taking advantage of rules you’ve written in your SIEM or working together to build new rules in our platform.
Have a suggestion? No problem. Just let us know and we’ll work to understand the use case and ensure you’re covered. No matter what security provider you work with, once you share your suggestion they should do the rest.
Myth: You’ll get assistance from outside experts.
By going to a co-managed SIEM, you’re hoping to take advantage of the collective knowledge from your service providers. Presumably your provider has seen lots of good and bad and can advise you and your team on doing SIEM better. You’d also think that they will answer general security questions and concerns you may have.
Reality: You should expect this assistance from your third-party security partners.
Once again, your third-party security partner shouldn’t just process alerts. MSSPs have lots of institutional knowledge they can share to help improve your broader security program. We work to push as much information to our customers (and publicly) as we can to help everyone make their organizations more secure. Further, our engagement managers are a window into Expel that can get you answers to tough security questions.
Myth: My SIEM will have all of the data required for detection and response.
Many organizations envision their SIEM as the single place where all data exists for detection and investigation. Thinking about co-managed SIEM as a strategy doubles down on this assumption as you’re paying for a provider to help manage that signal and detection content. The hope is that your SIEM will provide visibility across the entire environment and enable your team to respond to all kinds of threats.
Reality: Storing data in a SIEM is a lot of work.
Getting all the data that you want into a SIEM can be an exhausting process. And making sure it continues to go into a SIEM isn’t much easier.
We’ve built API integrations with more than 100 different vendors. We learned pretty quickly that data sent to a SIEM isn’t nearly as rich as data that can be pulled from API—which can inhibit detection and response with a SIEM.
As organizations increasingly use cloud applications and infrastructure, the vision of the SIEM as a single source of truth starts to make less sense. So it’s important to evaluate why you need (or think you need) a SIEM. There will be instances when sending your data to a SIEM is a wise choice (we’ll explore this a bit more in a future blog post). But, for example, you don’t need to store those Office 365 or AWS logs in your SIEM when your cloud provider is already storing them for you and your MSSP can consume them directly.
That’s why we connect directly to cloud providers—meaning that regardless of the choice you make, you’ll always get the visibility you need.
And the reality that’s all too familiar …
This is a big one.
It’s “too many cooks in the kitchen.”
One of the problems with a co-managed SIEM is orchestrating who is doing what.
A SIEM is a big piece of technology and dividing up responsibilities can be confusing. Who handles upgrades? Who’s responsible for rule QA? Who handles device integration? How about analyst shifts?
If the answer is “it depends”—expect friction.
By having a third-party security partner rather than a co-managed SIEM, the roles are clearer for both your staff and the service provider. Avoiding confusion at this stage helps ensure you’re focused on the right issues (like generating good signal, minimizing noise and detecting bad actions) and not wasting time on RACI charts and scheduling.
The value in SIEMs
SIEMs can be a valuable part of an organization’s security architecture. When properly fed, they’re the source of truth for an investigation. The information and analytical capability in your SIEM can be invaluable for analysts and investigators when working through the trail of alerts and data involved with suspicious activity.
Further, SIEMs are great data normalizers. Taking in unstructured data, providing structure and storing it all in an orderly way can open up many more opportunities for signal generation in your company. Data that might otherwise go ignored can be put to great use in your SIEM.
Finally, they’re great tools for your analysts. From experimentation to ongoing operations, a good SIEM and staff that know how to use them can fulfill their promise … serving as a focal point for your security operations.
However, even the best SIEM needs people.
If you don’t have in-house expertise and are thinking about co-managed SIEM as an option, consider these common myths and what you could accomplish by asking more of your third-party security partner. A managed detection and response service that can transparently use your SIEM can be a real game changer in your security program. Let us know if you want to chat.