Security operations · 2 MIN READ · KIM MAHONEY · JUN 22, 2023 · TAGS: MDR
Risk-based prioritization—aka vulnerability prioritization—boosts security and maximizes scarce resources by focusing SecOps on the most critical threats facing an organization.
According to a 2021 Joint Cybersecurity Advisory cosponsored by (among others) the Federal Bureau of Investigation (FBI), the National Security Agency (NSA), and the Cybersecurity Infrastructure and Security Agency (CISA), unpatched software is one of the top three access routes for hackers.
For example, and hot off the presses:
Several US federal government agencies have been hit in a global cyberattack by Russian cybercriminals that exploits a vulnerability in widely used software, according to a top US cybersecurity agency.
…
Aside from US government agencies, “several hundred” companies and organizations in the US could be affected by the hacking spree, a senior CISA official told reporters later Thursday, citing estimates from private experts.
Some numbers illustrate the ongoing magnitude of what security operations centers (SOCs) are up against.
- According to a recent Forrester report, software vulnerabilities are the second-most reported attack vector.
- Over 26,000 software security flaws were reported in 2022.
- 11+% of vulnerabilities have a critical score.
- Critical vulnerabilities were up 59% in 2022 compared with 2021.
- 66% of security leaders report a backlog of more than 100,000 vulnerabilities.
- 77% of organizations say it takes 21 minutes to detect, prioritize, and remediate each vulnerability.
- 74% of SOCs say they can’t take critical applications and systems offline to patch them quickly.
- 72% reported difficulty in prioritizing what needs patching.
Most security groups could use a little help. But if it’s to provide lasting value, that help must be strategic, systematic, and scalable. Remediation efforts should be proactive and built on a clearly defined and continuously iterated ruleset that articulates risk thresholds within the organization’s specific business and technical context.
Enter risk-based prioritization
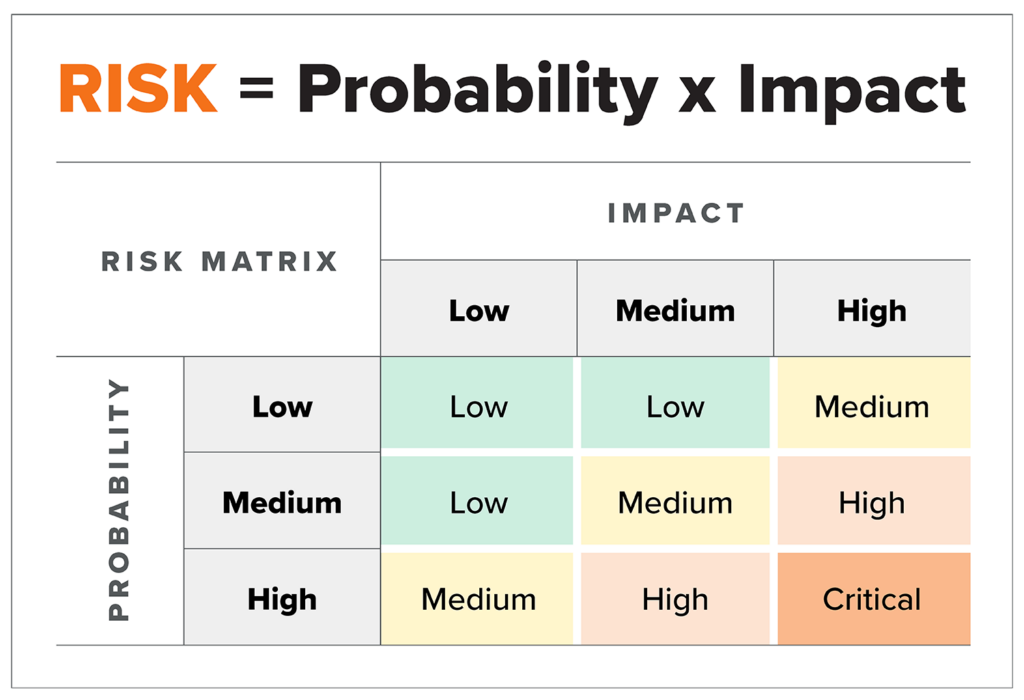
Instead of wasting resources on unimportant or low-risk vulnerabilities, vulnerability prioritization focuses on the most critical ones: identifying, prioritizing, and remediating based on the relative risk they pose. It accounts for the likelihood and impact of exploitation, as well as the business criticality and exposure of the affected systems.
Benefits of risk-based prioritization
- Efficient resource allocation: by focusing on vulnerabilities that pose the highest risk, companies can direct their efforts where they’ll have the greatest impact, ensuring a better return on investment.This is especially important given that the cybersecurity industry is currently dealing with a 3.4 million-person talent shortage. Qualified analysts are scarce and expensive to hire/retain even if you can find them, so every scrap of operational efficiency is critical to organizations looking maximize security while minimizing burnout, turnover, and costs. (This is especially true if vulnerability prioritization is executed within the context of managed detection and response, which directly addresses the talent shortage problem not only for the vulnerability management process, but for all areas of cybersecurity.)
- Decreased time-to-remediation: the sheer volume of vulnerabilities demands a keenly optimized remediation process. Risk-based prioritization drives faster response times by making sure vulnerabilities with the greatest potential risk are addressed promptly, minimizing your organization’s overall risk exposure.
- Enhanced risk mitigation: by aligning remediation efforts with the potential impact and likelihood of exploitation, organizations can more effectively lessen risks. Swiftly addressing high-risk vulnerabilities reduces the probability of successful attacks and minimizes the potential damage they can cause.
- Improved compliance and reporting: risk-based prioritization allows companies to demonstrate due diligence in addressing vulnerabilities that pose the greatest risk to sensitive data or critical systems, enhancing compliance efforts and facilitating comprehensive reporting on vulnerability management practices.
The cyber-threat growth curve isn’t really vertical, but it probably feels that way to a lot of frazzled SecOps pros. There’s not a magic bullet, but risk-based prioritization in the vulnerability management lifecycle can certainly lighten the load while improving security.
If any of this sounds familiar, we’d love to talk. Drop us a line.