Data & research · 3 MIN READ · AARON WALTON · OCT 17, 2023 · TAGS: Phishing / Threat hunting
Identity attacks, malware, AiTM, and DarkGate: cyberattackers are relentless, but so are the defenders…
Our Quarterly Threat Report (QTR) for Q3 2023 is live, and as always, it provides a helpful look at what attackers are up to and how their tactics are evolving.
The trends described in the report are based on incidents our security operations center (SOC) identified through investigations into alerts, email submissions, and threat hunting leads in the third quarter this year. Our customer base includes organizations of all sizes, in many industries, and with differing security maturity levels, affording your organization a broad context for evaluating your own footprint.
Here are a few of our top findings.
1. Identity-based attacks accounted for a significant majority of the incidents identified by our SOC.
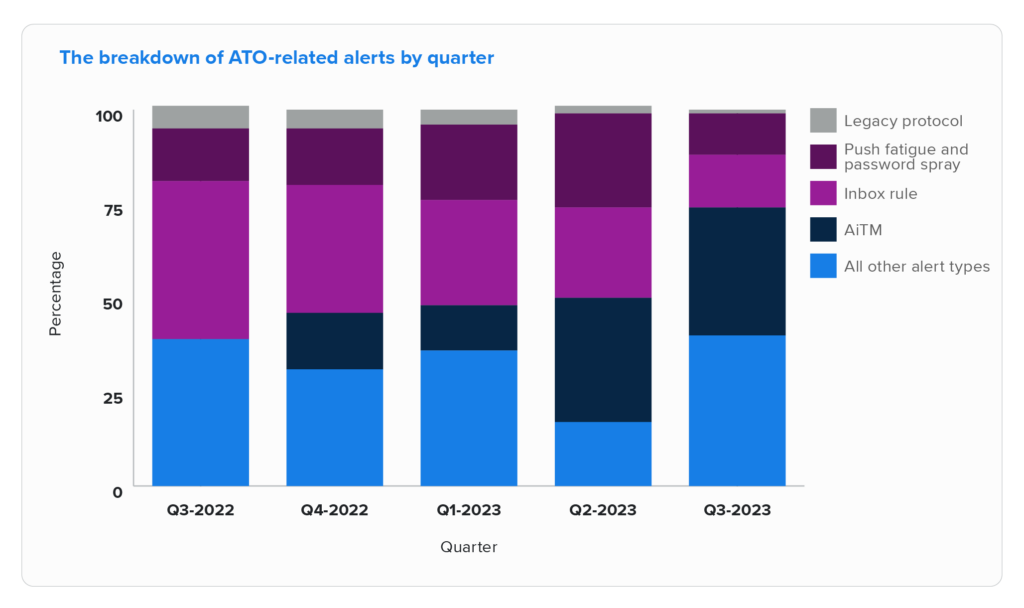
Identity threats are consistently the biggest threat we see, and Q3 was no different: account compromise, account takeover (ATO), and long-lived access key theft comprised 71% of all incidents during Q3. This number represents a seven percentage point increase for the second consecutive quarter.
2. Half of all malware incidents presented immediate significant risk.
In half of the malware incidents we saw in Q3, the malicious files deployed posed a pressing risk to customer operations, including pre-ransomware and exfiltration. This number is consistent with previous quarters, but we’ve updated our methodology to better articulate the specific risk represented by the malware.
The current numbers are calculated from initial access malware (which attempts to circumvent defenses and download/load other tools or malware) and remote access tools (RATs, which enable remote access). Both provide an attacker access to an endpoint in the environment, introducing significant risk as the attacker is now loose in the network. We attribute many of these attacks to initial access brokers (IABs), who sell access to ransomware gangs or to other enterprising threat actors.
3. AiTM: from nowhere to everywhere.
A year ago, adversary-in-the-middle (AiTM) attacks weren’t even on the radar for phishing attackers. Literally—there were zero AiTM session cookie theft attacks among our customer base in Q3 2022.
But Microsoft disabled legacy authentication protocols in Q4 2022, and more organizations enabled MFA, so attackers have been forced to cultivate new tactics (or abandon phishing, and that was a hard no). Enter AiTM techniques, which are now the single most common type of alert associated with successful account takeover attacks.
Worse, the most entrepreneurial attackers even took the opportunity to help other bad actors with software-as-a-service offerings, making it easy for anyone to execute these attacks—for a fee, of course.
4: Phishing with QR codes.
Our SOC saw a significant increase in QR code abuse in Q3. Phishing scams traditionally relied on emails, bad grammar, foreign princes, and/or malicious attachments and links. Managing those is fairly straightforward. When the attack is embedded in a QR code, though, things are trickier.
Essentially, a QR code is a link hidden within a picture. You’re probably familiar with them: you scan them like a barcode using your mobile phone’s camera and it takes you to a website (since Covid, they’ve gotten especially popular with restaurants and bars, where you can scan to pull up a menu on your phone). In this new generation of phishing emails, attackers mention something along the lines of a security or benefits update, and then direct the user to a QR code link for more detail.
But how do security and IT teams know if users scanned the QR code, thus successfully granting attackers access to their account? With a URL, they can look for workstations that connected to the malicious domain, but a QR code moves the activity to the user’s mobile device. This complicates the task for security teams and subjects users and the organization to increased risk.
5. DarkGate: initial access malware for the masses.
This quarter, the popularity of a malware known as DarkGate exploded. DarkGate is commodity malware: it’s sold to attackers to use when and where they see an opportunity.
We saw attackers distribute DarkGate in a few different ways, including through online ads that lead to fake websites (where users are unwittingly tricked into downloading malicious files); files downloaded through links in emails; and even through files shared through Microsoft Teams.
The bad guys continue to innovate and iterate so that when we shut down one mode of attack they’re ready to move to another. They’re clever, resourceful, and dedicated, but so are those of us in the security industry.
Download the Q3 QTR today and spend a few minutes reviewing its findings and the advice we provide on how to protect your organization. Then, if you do have questions or comments, drop us a line.