Threat intel · 4 MIN READ · AARON WALTON AND SCOUT SCHOLES · MAY 5, 2025 · TAGS: Get technical
TL;DR
- While malware isn’t always the threat with the largest volume of incidents, it’s still critical to protect against, regardless of your industry
- Infostealer malware remains a top threat for every industry, and is on trend to remain as the most common malware we’re seeing right now
- This data covers trends and insights on malware incidents from Q1 2025, along with other historically relevant malware incident data
In previous Quarterly Threat Reports (QTRs), we’ve had entire sections dedicated to trends in malware and what we’re seeing the most of within our SOC. For our latest QTR, we switched our narrative and focused on attack surface types to create a more tactical approach. However, we still have great data on malware trends we want to share for awareness. So here’s the 411 on the latest malware trends we saw in Q1 2025.
Before we dive into the data, here’s a quick reminder of how each malware type works:
- Infostealer: Infostealers malware accesses sensitive data on a device and then sends it to an attacker. They most frequently target passwords stored in the browser, cryptocurrency wallets, or files stored in common places.
- Initial access tools (IATs): Also called loaders or droppers, IATs attempt to circumvent defenses to get onto a system, so they can download or load additional malware.
- Remote access tools (RATs): Aptly named, RATs enable remote access to computers. RATs can include abuse of legitimate commercial tools like remote management and monitoring (RMM) tools or custom attacker-built tools.
- USB initial access tools (IATs): This malware runs from infected USB drives. When the infected drive is plugged into a computer, the malware attempts to connect to pull down additional tools to give bad actors access to the device.
- Cryptocurrency miner: This malware uses the resources of a computer or server to generate cryptocurrency on behalf of the attacker.
- Banking trojan: This type of malware steals or intercepts financial information as the victim is using this information.
- Browser hijacker: This malware changes browser settings without a user’s permission, and can then do things like redirect victims to unwanted or malicious websites.
What we saw in Q1 2025
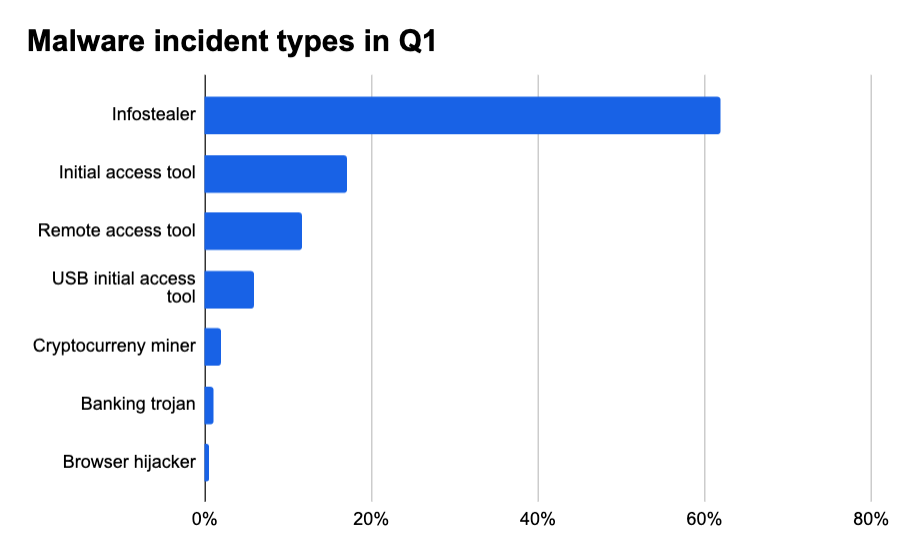
It was no surprise to us that infostealer malware was the most commonly encountered, with 61.9% of all malware incidents being attributed to infostealer. Nothing else came close. Initial access tool (IAT) and remote access tool (RAT) malware were the next most common, at 17% and 11.7%, respectively. We also saw USB IAT (5.8%), cryptocurrency miner (1.9%), banking trojan (0.9%), and browser hijacker (0.4%) malware. But, infostealer malware was almost four times as common as the next highest malware type (IAT), and over 100 times more likely to encounter than the least common malware (browser hijacker). So it’s safe to say infostealer was (and spoiler alert: will likely continue to be) the star of the malware show.
Changes from last year
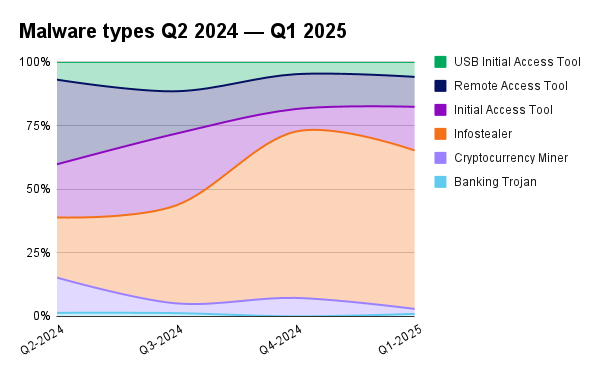
Based on reporting from our 2025 Annual Threat Report, the popularity of infostealer malware is carrying over from the overall trend we saw take over in 2024. Popularity of IATs and RATs seem to shift back and forth between the second and third most common malware types we see, and that’s consistent with data we’ve seen since 2023. USB IAT is continuing to drop in popularity. We touched on this in our Q1 2025 Quarterly Threat Report: Endpoint threats blog—essentially, direct access to a computer through this type of malware is declining, and so is the frequency of this threat.
Examples of common malware in the wild
Lumma infostealer (42.1% of malware incidents)
Lumma is currently the most popular infostealer. It’s become popular because of its ease of use and functionality. Purchase of Lumma includes the command and control panel that the malware relies on for stealing data and making it available to the user. Deploying the malware itself is up to the buyer. As a result, it’s conveniently delivered through whatever means the buyer chooses. We commonly see it deployed through the Click-Fix technique or masquerading as popular software downloads.
SocGholish (4.6% of malware incidents)
SocGholish is the most common IAT malware we see. Instead of selling the malware, the actors behind SocGholish sell access to infected computers. Most commonly, this access is sold to ransomware gangs.
The malware is delivered through infected websites. Another cybercriminal infects the websites and connects them to a traffic delivery system (TDS). The TDS allows criminals to determine which visitors get what malware.
Breakdown by industry
In the top 15 industries with the most malware incidents in Q1 2025, there was only one industry where infostealer malware wasn’t the top threat, and it’s possible it’s simply because the malware remained unidentified. So it’s safe to say infostealer malware is an industry-agnostic threat, and being able to defend against it is critical in today’s threat landscape.
| Industry | Percentage of total malware incidents | Most common malware type |
|---|---|---|
|
Healthcare |
18.3% | Infostealer |
|
Manufacturing |
10.6% | Infostealer |
|
Technology |
10.2% | Infostealer |
|
Financial services |
9.3% | Infostealer |
|
Entertainment |
8.5% | Infostealer |
|
Education |
8.1% | Infostealer |
|
Hospitality |
8.1% | Infostealer |
|
Utilities |
6.8% | Infostealer |
|
Insurance |
5.5% | Infostealer |
|
Retail |
2.9% | Infostealer |
|
Non-profit |
2.9% | Infostealer |
|
Legal services |
2.5% | Infostealer |
|
Pharmaceutical & chemical |
2.5% | Infostealer |
|
Media |
1.2% | Infostealer |
|
Travel |
0.8% | Infostealer |
Additionally, it’s worth noting the industries with the most incidents in the quarter were not necessarily the most affected by malware. Financial services saw the most incidents overall, but healthcare saw the most malware incidents in Q1. The table below compares the top ten industries with the most incidents, to the top ten industries who saw the most malware incidents:
| Most incidents in Q1 by industry | Most malware incidents in Q1 by industry | |
|---|---|---|
|
1 |
Financial services | Healthcare |
|
2 |
Healthcare | Manufacturing |
|
3 |
Manufacturing | Technology |
|
4 |
Entertainment | Financial services |
|
5 |
Technology | Entertainment |
|
6 |
Retail | Education |
|
7 |
Education | Hospitality |
|
8 |
Pharmaceutical & chemical | Utilities |
|
9 |
Hospitality | Insurance |
|
10 |
Legal services | Retail |
How to protect against malware threats
As we shared in our latest QTR, here’s how we recommend defending against infostealers:
- Enforce the use of password managers for all users, including contractors. Keeping these credentials stored in encrypted applications keeps infostealers from being able to access them.
- Disable the Run program in Windows via the Group Policy Editor for users who don’t need it. The click-fix tactic relies on the run program. By disabling it, the risk of infostealers, ransomware gangs, and nation-state actors using this tactic is reduced.
- Restrict Windows PowerShell usage through the Group Policy Editor as well. Many common malware, including infostealers, rely on PowerShell to pull down and execute commands. This restriction ensures only users who need PowerShell have it available.
Additionally, when it comes to malware in general, be sure to educate your employees on what a valid site, download, or attachment looks like. While they aren’t as common as infostealers lately, JavaScript file downloads are a still a classic way to launch malware, and as we’ve seen in the past, attack tactics don’t die just because they’re old.
Stay safe out there!