Data & research · 5 MIN READ · AARON WALTON · JUL 24, 2024 · TAGS: Guidance
TL;DR
This is a summary of what you’ll find in each blog in this series:
- Volume I: Q2 by the numbers. We’ll look at an overview of incidents and which attack types are trending. This is a summary of all the volumes for this quarter.
- Volume II: Attackers advance with AI. In many cases, attackers use AI in place of the skills they don’t have or to augment their existing capabilities. We share examples and insights from attacks we’ve seen against our own customer base.
- ➡️ Volume III: Malware infection trends. We discuss what types of malware appear to be trending (spoiler alert: it’s Remote Access Trojans [RATs]) and long-time threats that don’t appear to be going away anytime soon.
- Volume IV: Phishing trends. Phishing-as-a-Service (PhaaS) platforms make phishing easy. These services really took off in the last year and a half and show no sign of stopping. We share what these are, how they work, and how they can be counteracted.
- Volume V: Latent-risk infostealing malware. Infostealers present a serious risk to businesses. We examine recent notable breaches involving infostealers, highlighting the importance of being able to detect, mitigate, and respond to this form of malware.
So far, we covered our top takeaways from Q2 of 2024 (volume I) and shared two cases where we saw cybercriminals leveraging AI (volume II). Now, our series continues with a look at malware infection trends.
Getting access to an environment
Not all malware is created equal.
Though “malware” is a pretty familiar term to most, we like to highlight that malware is just software. In gardening, if a plant is in an undesired location, that plant is considered a weed, even if that plant may not be bad in and of itself. Similarly, some malware may be legitimate software, but when it’s deployed with ill intent and used for malicious things, it’s considered malware.
Cybercriminals choose their malware based on their needs, and in responding to incidents, we try to understand the threat actor’s intentions and goals. In some cases, the actor is attempting to acquire information, such as credentials, from a device, and in other situations, the actor is attempting to attain remote access to the device. We’ve found that understanding the attacker’s goals, and knowing if and how legitimate software is being deployed for illicit purposes, helps us know how to mitigate incidents and prevent them from happening again in the future.
At Expel, we categorize malware into a few basic types. Two major types we discuss are high-risk and latent-risk malware. We consider malware high-risk when we know it’s leveraged by ransomware actors or the malware provides a high degree of access to a victim’s computer or network. In the following breakdown, the USB initial access tools (USB IATs), remote access tools (RATs), and other IATs are considered high-risk. The remaining types are considered latent-risk: that is, while they introduce risk, the threat is not immediate. (In a later volume in this series, we’ll talk about the latent-risk of information stealing malware in more depth.)
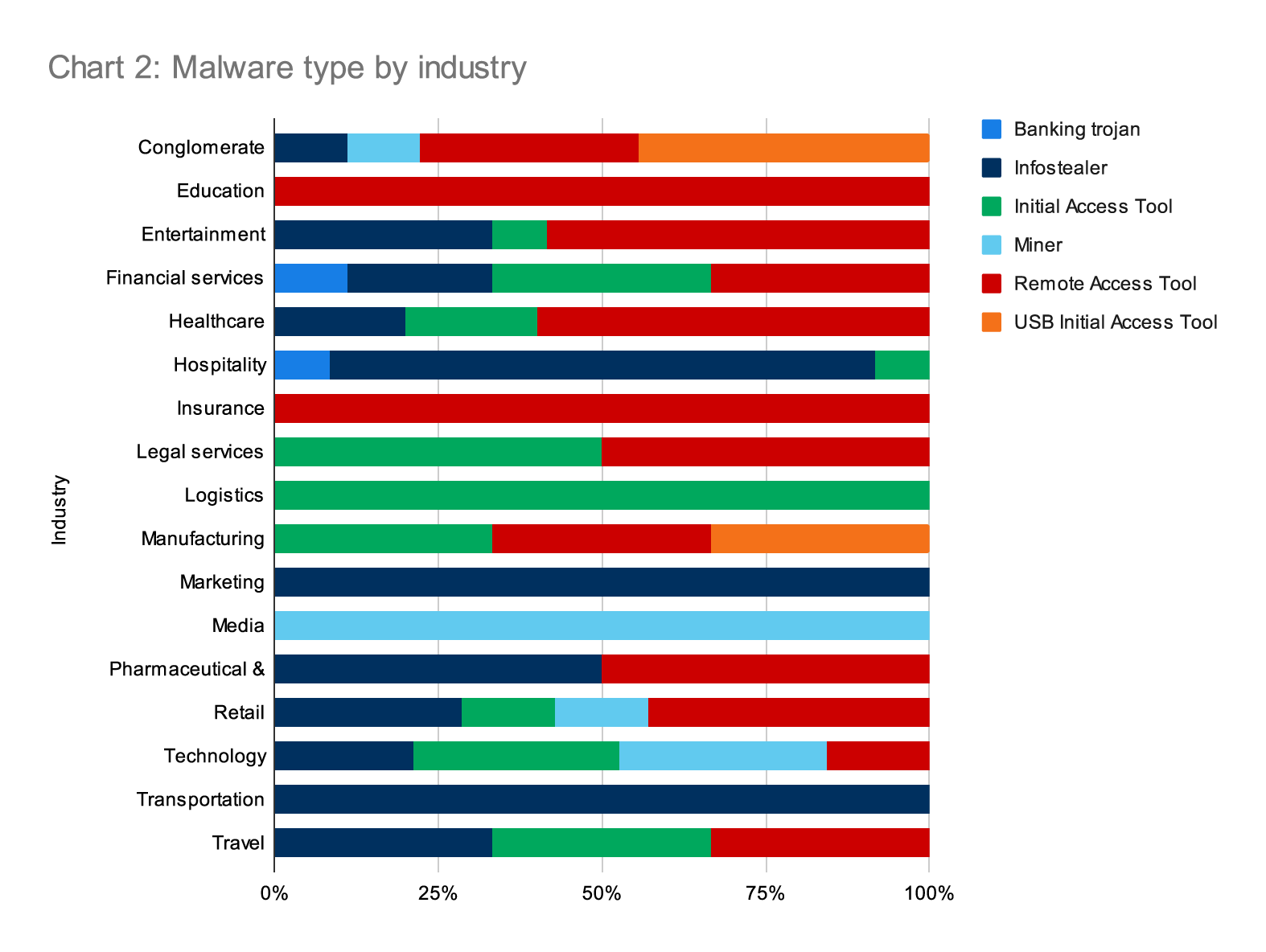
The following chart breaks down the different types of malware that we saw across our customer base in Q2. The highest rate of malware we observed were RATs, including both commercially available tools (like AnyDesk, NetSupport, LogMeIn) and attacker-designed tools (such as AsyncRAT).
Note: The astute reader may notice that the percentage of infostealers is less than what we talk about in Volume V: Latent-risk infostealing malware. That’s because Chart 1 is weighted due to a targeted campaign.
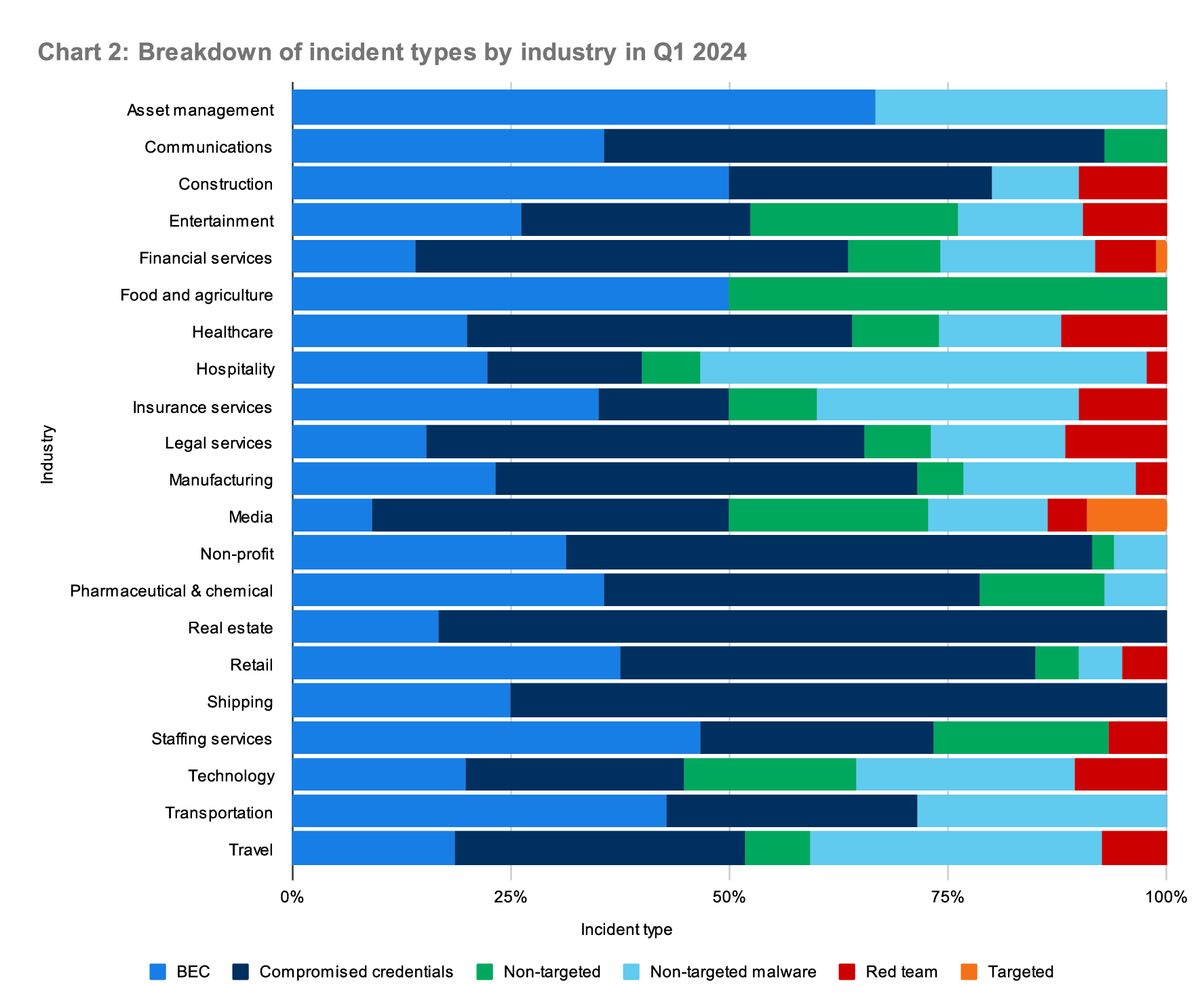
The malware discussed here is primarily deployed opportunistically.
Many of the incidents we’ve seen for the last year (and consistently over this quarter), were the result of an end user downloading a file or software they believed to be legitimate from a malicious advertisement or an infected website. Since these malware are often deployed opportunistically, they can affect a large range of industries. The chart below depicts the distribution of malware types we observed in Q2 across industries within our customer base. We haven’t observed any industry specifically targeted.
Threat actors and file types
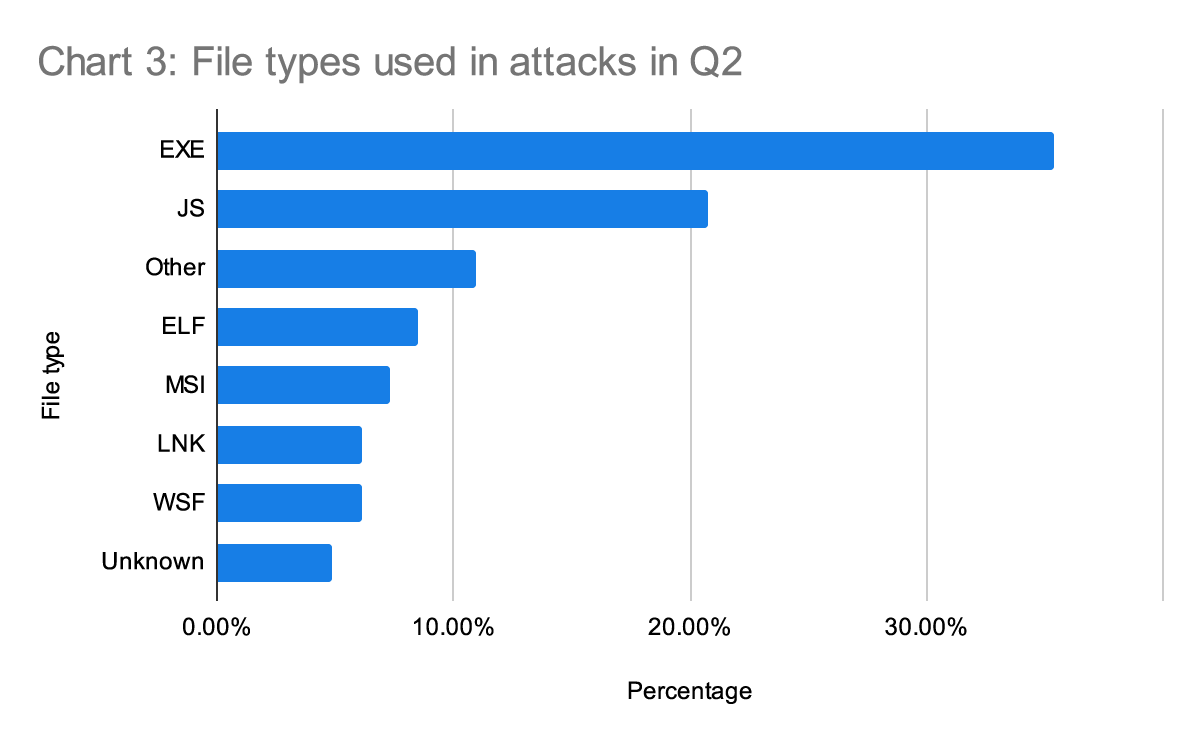
In addition to the actor’s goals for the malware, we consistently track file types to help us identify what mitigation techniques are possible. Detection and prevention techniques differ based on file types and available security technologies.
This quarter, the increased frequency of commercial RAT abuse caused a shift from JavaScript to EXE files as the most common high-risk malware files—the first shift we’ve seen in a while.
How to protect your organization:
Be sure that security teams are aware of which RATs are authorized in an environment. Some tools, like Microsoft’s Defender for Endpoint, can block files if they aren’t common, don’t meet age requirements, or aren’t on a trusted list.
Same old threats
One of our 2024 predictions was that even with the rise of new criminals enabled by AI, some of the old threats that have been around for a decade would still be some of the major threats to businesses this year. That appears to be true. Three actors that are consistently at the top of our list are: SocGholish, GootLoader, and ZPHP. Each of these actors use JavaScript to gain an initial foothold in the environment before they attempt to download additional payloads—they’re also known to sell access to infected endpoints to ransomware actors.
SocGholish and ZPHP use infected websites to deliver their malware. These infected websites are managed by a traffic delivery system (TDS) that determines which users are expected targets. TDS systems can also be leveraged to prevent analysis of an infected website. The TDS may determine whether or not to display malicious content if there was a recent visit from the same user or same IP address. However, if the user meets the target criteria, they will be presented with a message telling them that they need to update their browser (or perform some other action). If the user does as they are instructed, the malware downloads a RAT to the host.
GootLoader uses search engine optimization (SEO) poisoning to deliver malware. In this attack, the user often searches for a legal document, and one of the top results may be an infected website that uses GootLoader’s SEO poisoning. GootLoader also uses a system to prevent analysis–any other users connecting to the infected website from the same IP won’t see the malicious content. If the user meets the target criteria, they’ll find a fake forum offering them a download of their desired file.
Recently, we’ve also observed that the GootLoader threat actor is expanding into malicious advertisements. We identified some instances where the intended target attempted to download an installer for Microsoft Teams, but downloaded the GootLoader malware instead.
How to protect your organization:
Attackers often look for ways to abuse abnormal file types. Use Group Policy to set uncommon script formats like JavaScript (JS), Windows Script Host (WSH), and Windows Script File (WSF) to open in Notepad when double-clicked. This prevents users from executing any accidentally downloaded files. These downloads are designed to be deceptive, so technical solutions to prevent these malware are the most effective.
Next up in this series: we dig into Phishing-as-a-Service (PhaaS) and authentication sources for attackers in Volume IV: Phishing trends.
Do you have questions about how Expel can help protect your organization from malware infections? Drop us a line.
About these reports
The trends described in our QTRs are based on incidents our security operations center (SOC) identified through investigations into alerts, email submissions, or threat hunting leads in the second quarter (Q2) of 2024. We analyzed incidents across our customer base, which includes organizations of all sizes, in many industries, and with differing security maturity levels. In the process, we sought patterns and attacker tendencies to help guide strategic decision-making and operational processes for your team.