Data & research · 3 MIN READ · AARON WALTON · JUL 22, 2024 · TAGS: Guidance
Welcome to the Expel Quarterly Threat Report (QTR) for Q2 2024. If you’re new here, our QTRs provide data and insights on the attacks we’re seeing, how to spot them, and ways you can protect your organization. By sharing how attackers got in, and how we stopped them, we’ll translate the security events we detect and remediate into strategy for your organization.
About these reports
The trends described in our QTRs are based on incidents our security operations center (SOC) identified through investigations into alerts, email submissions, or threat hunting leads in the second quarter (Q2) of 2024. We analyzed incidents across our customer base, which includes organizations of all sizes, in many industries, and with differing security maturity levels. In the process, we sought patterns and attacker tendencies to help guide strategic decision-making and operational processes for your team.
TL;DR
This is a summary of what you’ll find in each blog in this series:
- ➡️ Volume I: Q2 by the numbers. We’ll look at an overview of incidents and which attack types are trending. This is a summary of all the volumes for this quarter.
- Volume II: Attackers advance with AI. In many cases, attackers use AI in place of the skills they don’t have or to augment their existing capabilities. We share examples and insights from attacks we’ve seen against our own customer base.
- Volume III: Malware infection trends. We discuss what types of malware appear to be trending (spoiler alert: it’s Remote Access Trojans [RATs]) and long-time threats that don’t appear to be going away anytime soon.
- Volume IV: Phishing trends. Phishing-as-a-Service (PhaaS) platforms make phishing easy. These services really took off in the last year and a half and show no sign of stopping. We share what these are, how they work, and how they can be counteracted.
- Volume V: Spotlight: Latent-risk infostealing malware. Infostealers present a serious risk to businesses. We examine recent notable breaches involving infostealers, highlighting the importance of being able to detect, mitigate, and respond to this form of malware.
To kick things off, let’s talk about Q2 by condensing it down to some numbers.
Q2 by the numbers
- Identity-based attacks (account compromise and account takeover [ATO]) accounted for 65.4% of all incidents our SOC identified.
- In the context of this report, we define identity threats as attackers attempting to gain access to a user’s identity to perpetuate fraud. This includes failed attempts to abuse compromised credentials, as well as attackers who successfully gain access to a target account (also known as business email compromise [BEC]). Identity-based attacks are consistently the predominant threat our SOC sees.
- Malware-based incidents made up 18% of incidents in Q2 and unauthorized RATs accounted for 37% of those malware incidents. RATs introduce serious risk to an environment as they’re often leveraged by ransomware actors.
- 65% of malware incidents were considered high-risk and the remainder were what we consider latent risks.
- Incidents in cloud infrastructures (AWS, GCP, Azure, and Kubernetes) made up only 2% of the total incident volume. The most common cause of incidents were misconfigurations and vulnerabilities allowing malware deployment.
- In general, other incident types appear to pale in comparison to identity-based attacks (compromised credentials and BEC on Chart 1). This increase is largely a result of the accessibility of PhaaS, which we explore in Volume IV: Phishing trends.
- BEC incidents are those in which an attacker is able to log into an account.
- Compromised credential incidents occur when an attacker compromises credentials, but fails to be able to login.
- Non-targeted attacks include vulnerability exploitation, hands-on attacker activity, and more.
- Non-targeted malware consists of broad malware campaigns and commercially available malware.
- Red team activity refers to internal and authorized security testing.
- Targeted attacks are defined as incidents driven by attackers with a specific target in mind.
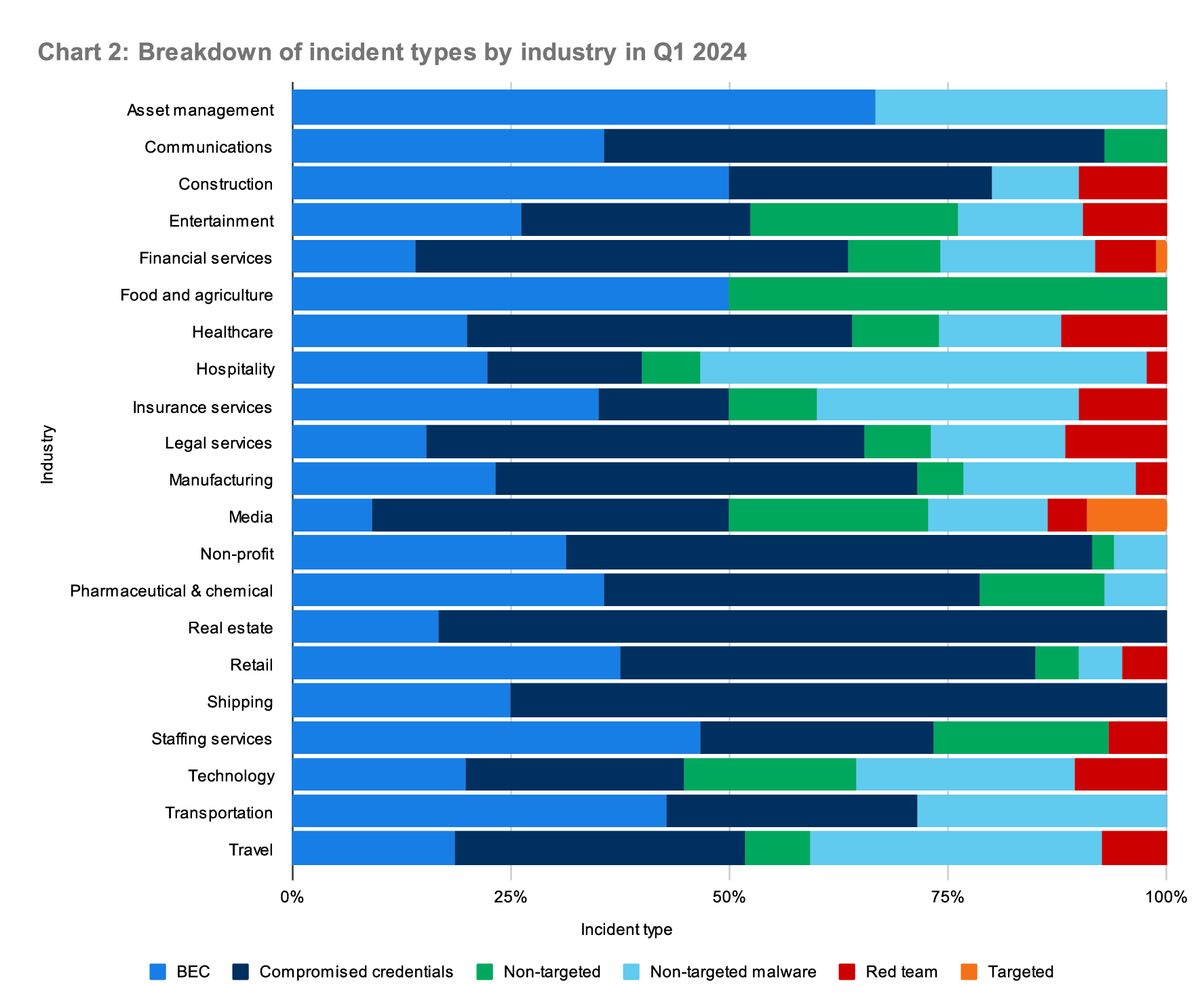
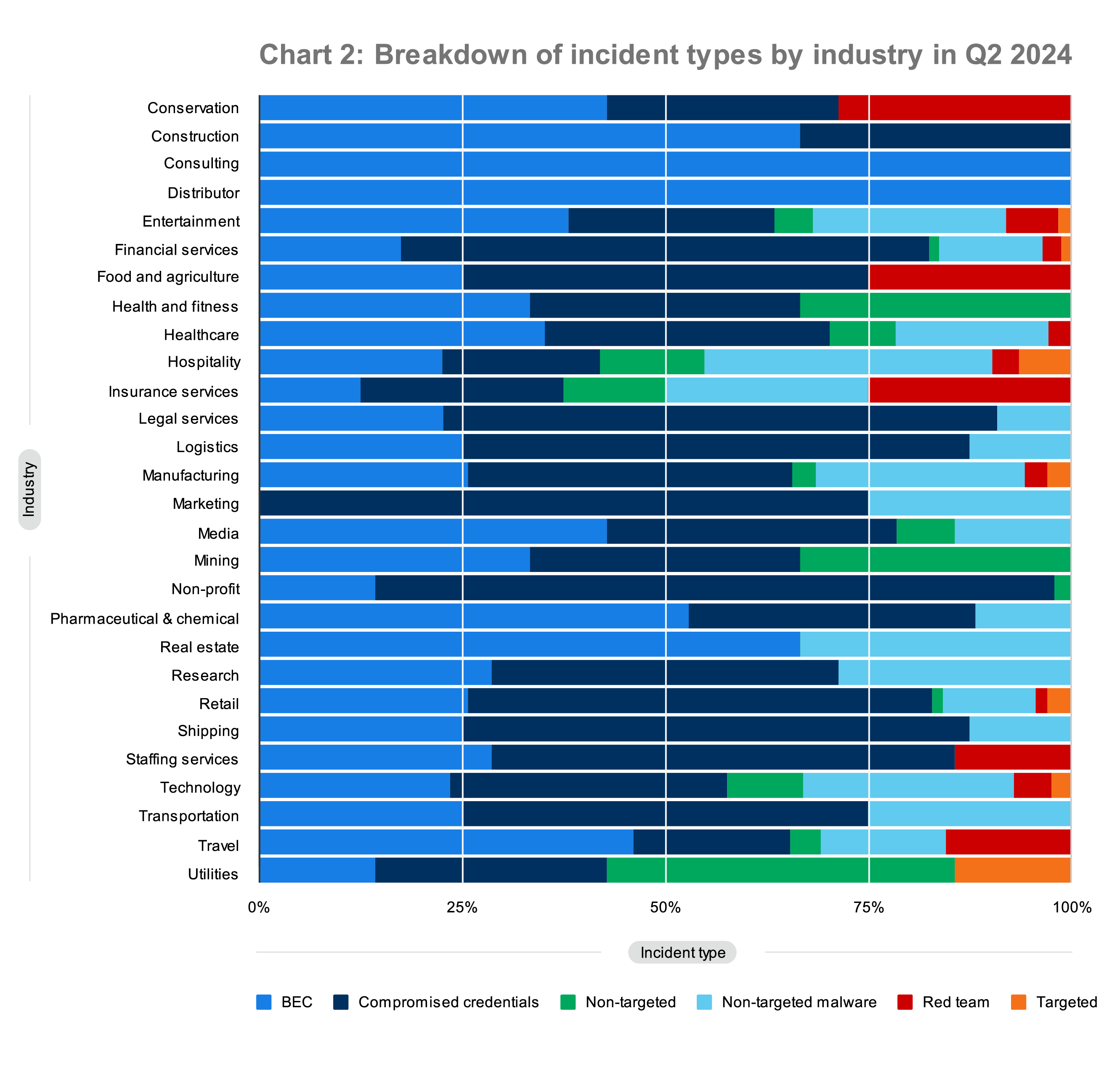
This quarter also continues to show us that identity-based threats (and threat actors) don’t favor any particular industry. Chart 2 looks at the incident types across the industries comprising our customer base, illustrating that attackers opportunistically target the vulnerable, no matter the industry.
And if you have any questions or just want to chat, don’t hesitate to drop us a line.






