Current events · 3 MIN READ · BRUCE POTTER · APR 7, 2020 · TAGS: Guidance
If someone asked you to think about elections, what’s the first thing that comes to mind?
For most people, it’s that moment when you show up at your polling place and cast your ballot.
But the reality is that the system is so much larger than that — elections are about far more than the voting machine and election security is about more than securing a single piece of equipment.
Consider voter registration efforts and election rolls, all of the information voters have digested leading up to voting day that have influenced their decisions … And don’t forget what happens after you cast your vote and how the results are tallied.
Now combine all those moments in the election security supply chain with a global health crisis — think sending absentee ballots to everyone in a given state so they can vote in the primary — and you’ve got even more potential election-related vulnerabilities on your hands.
To understand and mitigate election security, it’s essential to consider the entire supply chain.
The parts of our election security “supply chain”
There are six distinct parts of the election supply chain (see below) and they all have the potential to be compromised at different times (and in different ways) during the election cycle.
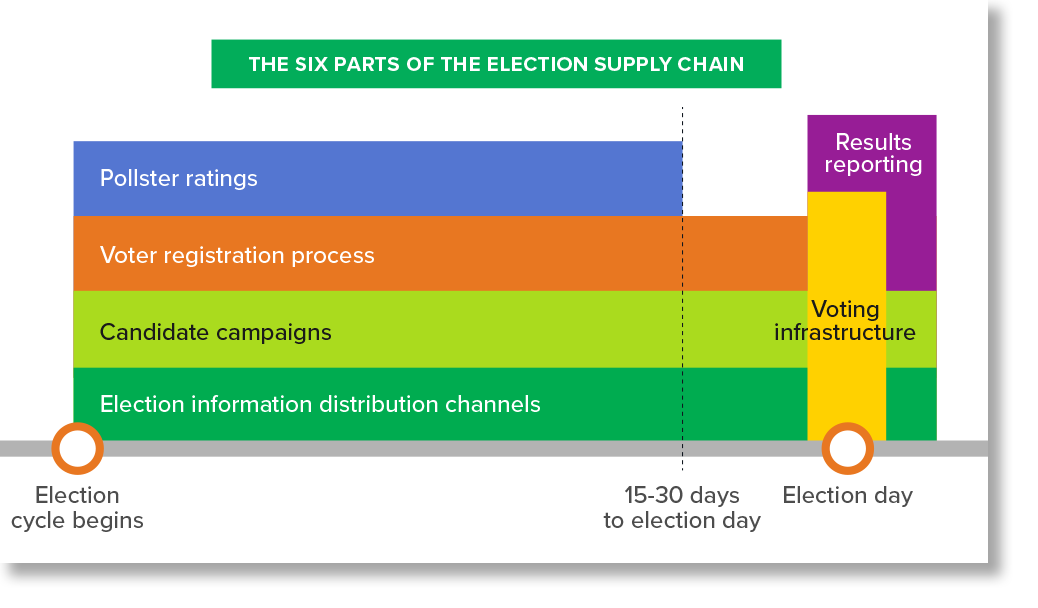
The TL;DR? The potential for election compromise starts long before Election Day.
Which is exactly why we created a handbook about the election security supply chain.
We know there are other election security guides out there — but most of them focus only on a single part of the election process, like voting infrastructure.
In our latest guide, we zoom in on each step along the election supply chain and look at potential points of compromise including how a crafty attacker could “hack” each piece along the chain.
For each part of the election supply chain we also offer up ideas about how public and private sector organizations—even individual, well-informed citizens who are planning to vote—can better protect our elections from attacks.
Why it matters
Whether you work in security, are an election official or just happened to be, well, an informed voter, there are plenty of ways we can all band together to collectively improve the security posture of our elections systems.
And no matter your role in the process, maintaining or improving the integrity of our democracy is in everybody’s best interest.
What we (yes, you) can do about it
By focusing on even a few key proactive security measures, our election security supply chain would be far better protected than it is today.
Here are just a few ideas on how we can work together to improve election security:
- Educate yourself (and others). Whether you’re making sure your election officials know how to transfer election results to a website (ahem, Iowa) or sending your security analysts to relevant training sessions or conferences, educating the people who impact each part of the election supply chain is paramount. And if you’re a regular ol’ voter? Fact check what you read about candidates and issues, and get your information from multiple, varied sources.
- Learn about (and implement) security best practices and frameworks. If you’ve worked in security for any length of time, chances are good that you’ve heard of the NIST Cyber Security Framework (CSF). The NIST CSF is one of the many frameworks out there that can help you gauge your effectiveness when it comes to security and think about how you want your efforts to change or grow. So whether it’s NIST or something else, pick a framework and use it to understand where and how you can get better.
- Pressure test your systems. You know what helps when bad things start happening? Having a plan and knowing who needs to do what when something goes sideways. Create an incident response plan—better yet, create a plan, emulate an incident and practice what you might do if that bad thing happened in real life.
Grab your copy of our election security handbook
Want to read more?
Click the button below to download your copy of our election security handbook right now.






