Current events · 3 MIN READ · PAUL LAWRENCE AND ROGER STUDNER · MAY 16, 2023 · TAGS: AI & automation / Phishing
This type of phishing attack can be ridiculously sneaky
We love when our customers run red team engagements. Aside from testing and validating current security controls, detections, and response capabilities, we see it as a great opportunity to partner with our customers on areas of improvement. Here’s the story of how a red team helped Expel improve our phishing service and how we used our platform capabilities to detect some sneaky activity.
So, what happened? (Spoiler alert: it’s a homoglyph attack)
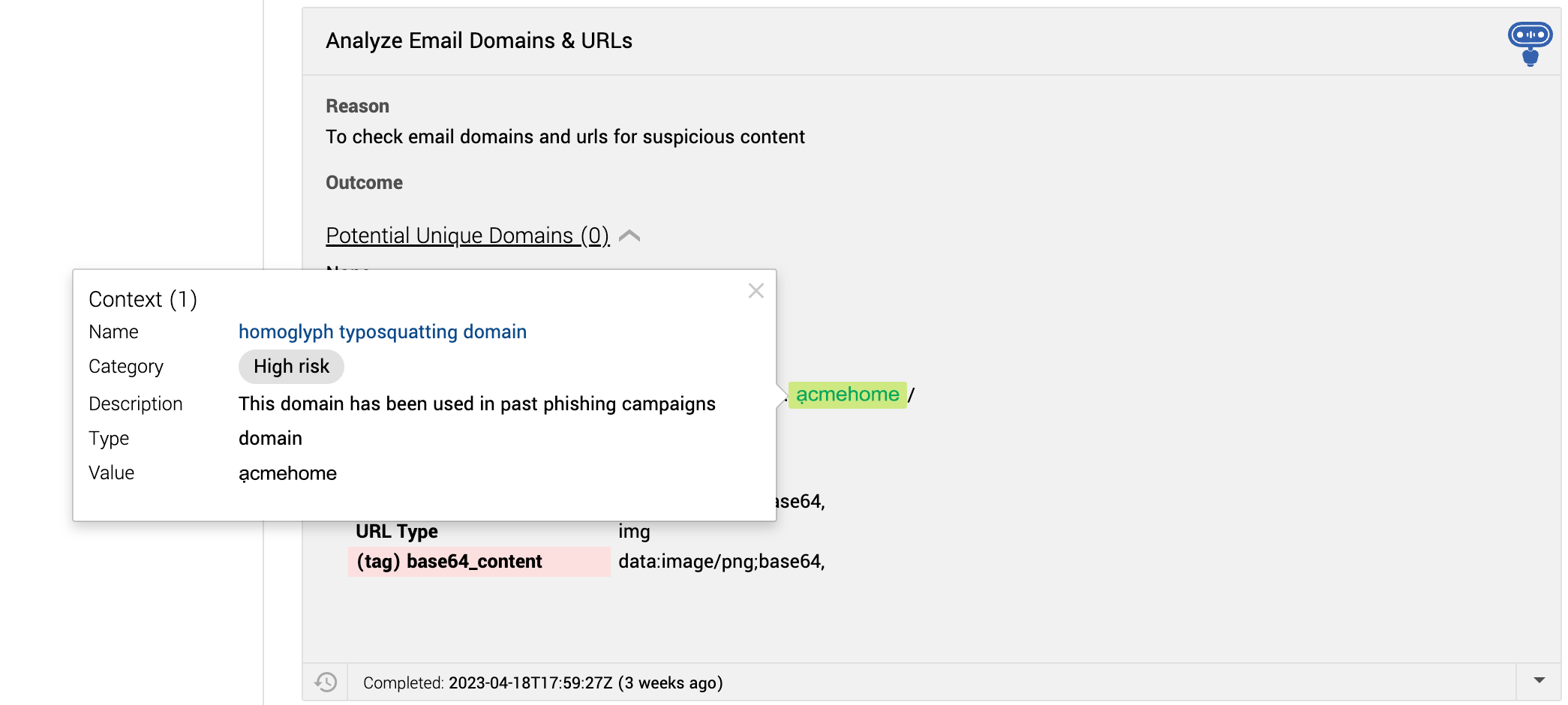
Our client—let’s call them Acme Corp—had an enterprising red teamer with a clever idea. For one of their exercises, the red team purchased a domain: ạcmehome[.]com. Notice anything odd? Let’s look closer:
ạcmehome[.]com vs acmehome[.]com
If you missed it, don’t feel bad. That’s the point.
A bit of background
The problem is that the “a” isn’t an “a” at all, but an “ạ.” It’s a homoglyph—”one of two or more graphemes, characters, or glyphs with shapes that appear identical or very similar but may have differing meaning.” This one specifically is a Vietnamese particle used “at the end of the sentence to express respect.”
Fast Company called homoglyph attacks (aka homography or Punycode attacks) one of the four most intriguing cyberattacks of 2022.
[They’re] a type of phishing scam where adversaries create fake domain names that look like legitimate names by abusing International Domain Names that contain one or more non-ASCII characters. In other words, hackers discovered at some point that a lot of alphabets, like the Cyrillic and Russian alphabets, have characters that look like English or what we call Latin English. So, a Cyrillic “a” will be different from a Latin English “a,” but when these characters are used in domain names, they are indistinguishable to the naked eye. This allows phishers to spoof brand names and create look-alike domains which can be displayed in browser address bars if IDN display is enabled.
There are lots of homoglyphs and the potential for mischief is off the hook (which is why top-level domain registries and browser designers are exploring ways to minimize the risks of hõmògIÿphìč chäôs).
There’s even a homoglyph “attack geñerator.”
This app is meant to make it easier to generate homographs based on homoglyphs than having to search for a look-a-like character in Unicode, then copying and pasting. Please use only for legitimate pen-test purposes and user awareness training. [emphasis added]
Back to Acme. The red team’s fake domain used the Vietnamese homoglyph to trick users into thinking it’s the actual domain—in this case, acmehome[.]com—when that itty-bitty dot under the “a” makes a huge difference. The tactic also relies on a security operations center (SOC) analyst who’s been staring at mind-numbing alerts slipping up and not noticing the difference in domain names. In truth, for most SOCs and attackers, this isn’t a bad strategy.
What we did
After meeting with the red teamers, we uncovered a need to better scrutinize unique domains within emails that could intentionally trick the naked eye. Technology to the rescue. Since we have a content-driven platform capability—customer context (CCTX)—Expel was easily able to change the platform behavior to recognize the attack for that homoglyph site in Acme’s Workbench™. Having a platform that’s content-driven means Expel users can change how the platform operates without having to engage with engineering teams to release new features.
NOTE: When you have a platform that allows users to drive content and configuration, it means that once you understand how a feature works, you can bring your own creativity to solving problems. It’s really fun when you’re able to adapt a feature (especially if it allows for rapid response to new or emerging techniques) to accomplish something unanticipated during the design of the feature—which is what happened in this case.
The result?
Acme Corp’s red team conducted a similar attack again, and this time the SOC caught it with CCTX.
What does it all mean?
Multiple things, possibly.
First, homoglyphs represent a technique that SOCs need to account for.
Second, there are branding reasons (as well as security ones) to sort homoglyph usage. While most businesses with accents and other homoglyphs in their names (Société Générale, A.P. Møller-Mærsk, and Nestlé come to mind), they typically use unaccented letters in their URLs. Would an analyst notice if a phishing attack used the homoglyph? Or, if the accented URL works (for example, loréal.com), what if hackers put a different accent into play (è vs é)?
Third, this potentially matters even more for companies in nations whose languages employ extended iconography (this includes most non-English-speaking countries). Which means it matters more for cybersecurity firms serving them. Like us.
Short version: homoglyph attacks are prevalent and sneaky. They pose particular challenges for human analysts, but as our Acme Corp case demonstrates, the combination of well-placed automation and humans leads to great results.
If you have questions, or think your organization might be at risk, drop us a line.