Current events · 7 MIN READ · KYLE PELLETT · DEC 14, 2021 · TAGS: Guidance / tech stack / threat landscape
We’re often asked about the biggest threats we see across the incidents we investigate for our customers. Where should security teams focus their efforts and budgets?
To answer these questions, we’re sharing monthly reports on the top attack vectors, trends, and resilience recommendations identified by our Security Operations Center (SOC). Our goal is to translate the security events we’re detecting into a security strategy for your org.
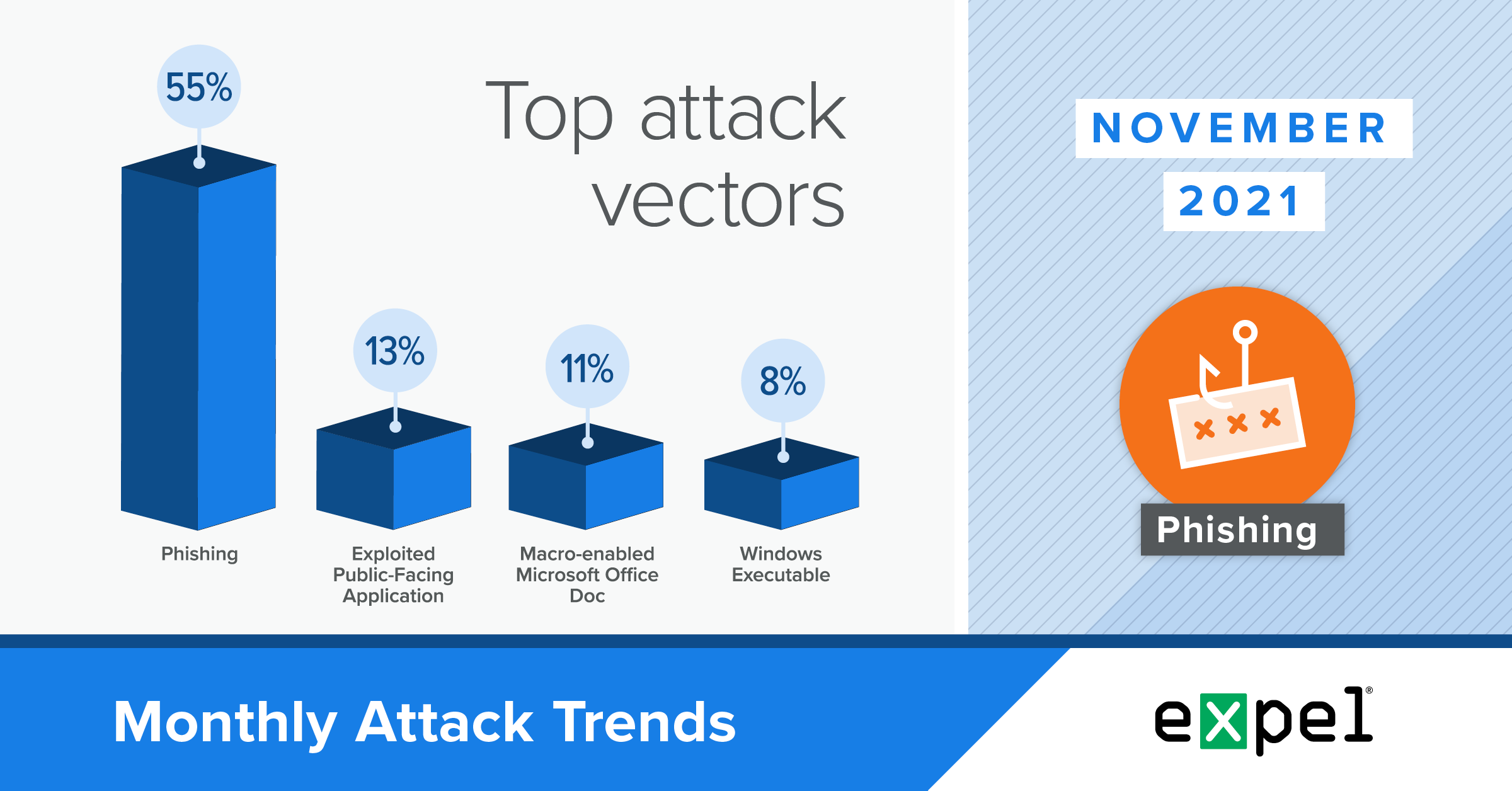
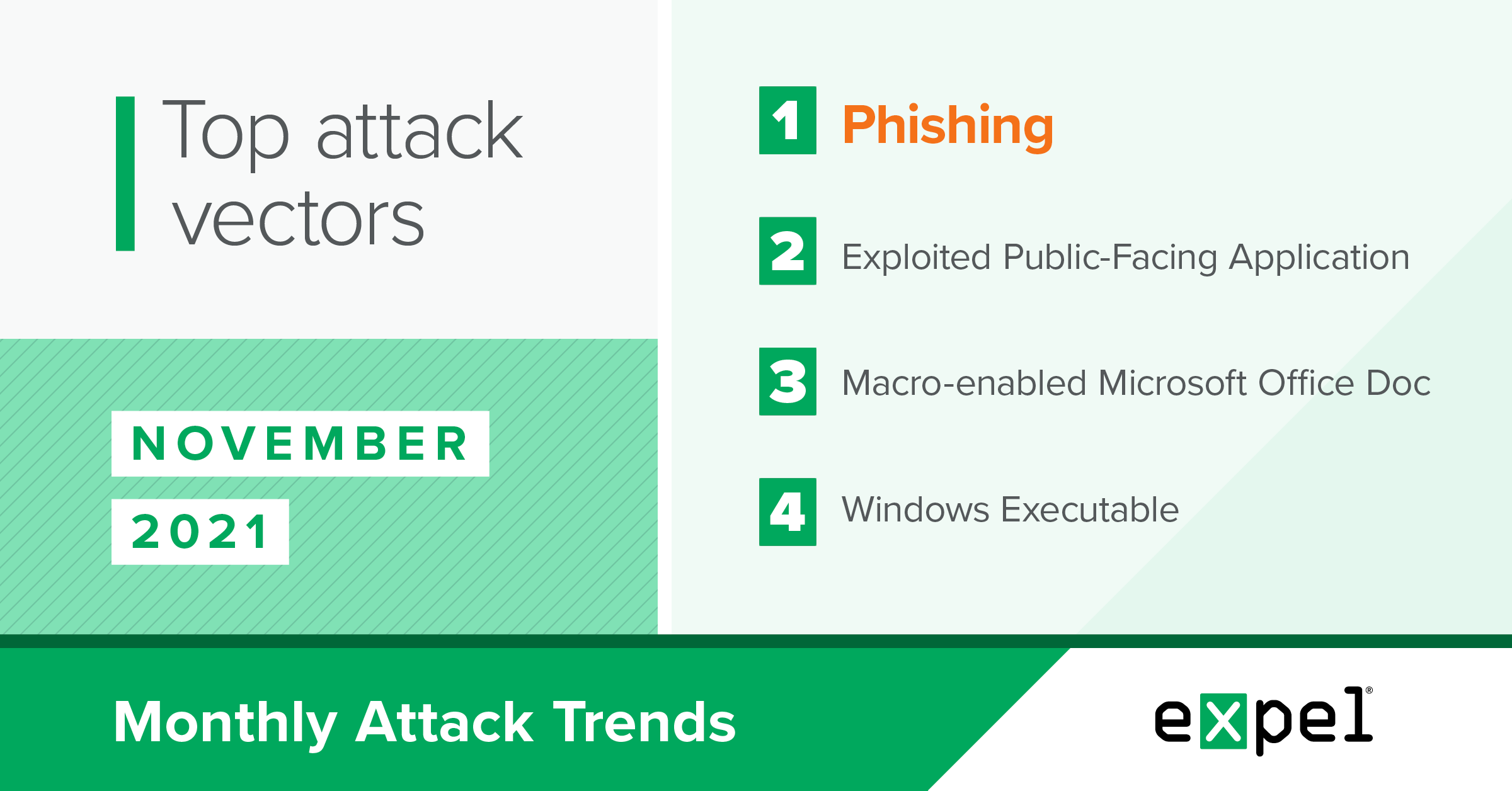
For this report, our SOC analyzed the incidents we investigated in November 2021 to determine the top attack vectors used by bad actors. Here’s what’s ahead:
- A rise in phishing emails linking to malicious macro-enabled Microsoft Office docs, ultimately targeting financial accounts
- A breakdown of cryptojacking and the latest tactics we’re seeing
- What to do about all the above
Evil macros used to deploy SquirrelWaffle
TL;DR: 25 percent of the commodity malware incidents we investigated in November were attempts to deploy SquirrelWaffle.
In November, we observed a 10 percent increase in commodity malware incidents resulting from phishing emails containing links to download malicious macro-enabled Microsoft Office or Excel documents. We attributed most of this activity to SquirrelWaffle, a malware loader. One in four commodity malware incidents were attempts to deploy this family of malware. This is a substantial increase from previous months and we expect this trend to continue.
A typical attack chain to deploy SquirrelWaffle looks like the following:
- An employee receives a phishing email containing a seemingly innocuous link and an urgent call to action
- If the employee clicks the link, they receive a ZIP file with an embedded macro-enabled Office or Excel document
- The document instructs the employee to enable macros (red flag!)
- If the employee enables macros, this initiates the SquirrelWaffle infection process
- SquirrelWaffle is then typically used to deploy additional malware to an infected host
To date, we’ve seen that SquirrelWaffle often downloads a variant of the Qakbot banking trojan to scrape the victim’s machine for sensitive financial data and send it back to the attackers.
SquirrelWaffle can also load more insidious malware like CobaltStrike’s Beacon agent, a post-exploitation attack emulation tool that’s popular among cybercrime and ransomware groups.
Notable: We integrate with many Endpoint Detection and Response (EDR) technologies and have identified a trend where SquirrelWaffle executes at least partially, regardless of the EDR in use. Here’s an example.
In a recent investigation involving a Windows 10 host with an EDR agent, an employee downloaded a malicious ZIP file with an embedded Office document and then enabled macros.
This kicked off the SquirrelWaffle infection process. The evil macro was configured to download and execute evil Windows DLL files on the infected host. Shortly after, we detected process activity on the infected host consistent with reconnaissance. At this point in the attack, the EDR agent terminated the evil process.
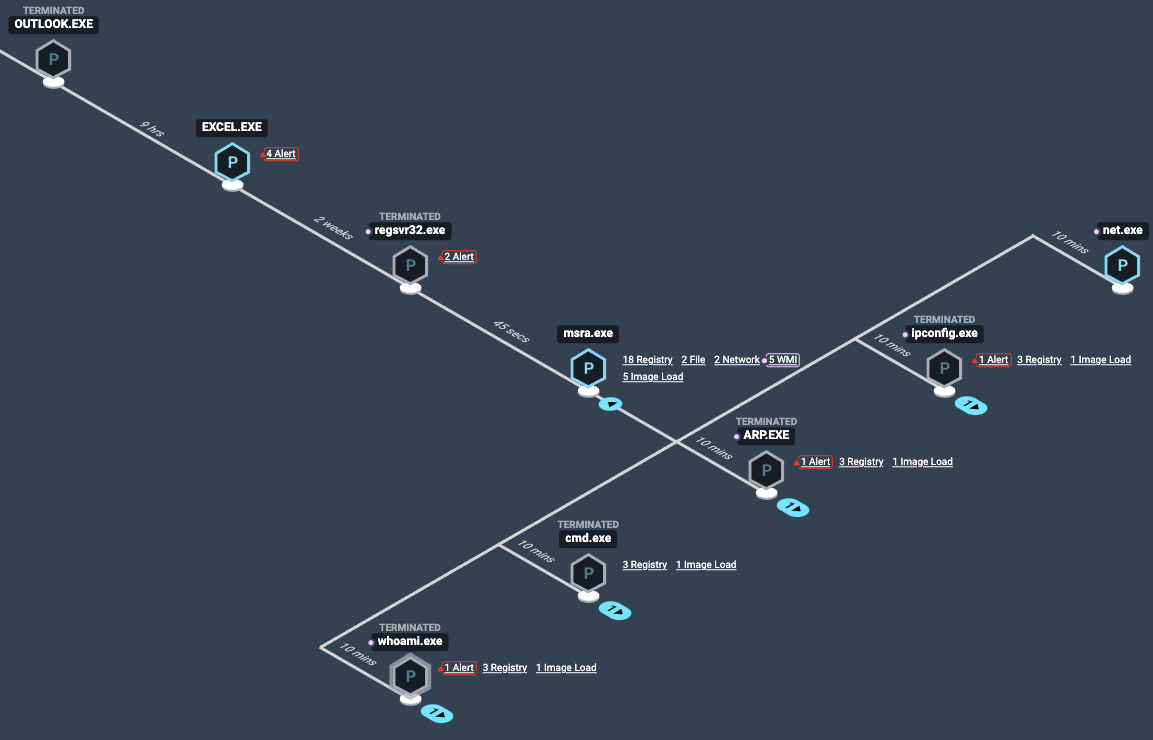
Here’s what that looks like from a defender’s perspective:
Endgame process tree view of SquirrelWaffle resulting in second stage payload execution.
What’s the goal here?
In most cases, the goal is to scrape the infected host for credentials, including financial account information. When a host is infected, attackers gain access to that victim’s contact list and can use their compromised accounts to play on trust between the account owner and their contacts to enable further infections.
How to detect SquirrelWaffle:
- Alert when you see an Excel process spawn Regsvr32.exe to load DLL files in C:Datop
- For a broader approach, alert when you see an Excel process spawn Regsvr32.exe
- Alert when you see Regsvr32.exe execute with references to .good or .text files within the process arguments
- Alert when you see Microsoft Remote Assistance (msra.exe) spawn process typically associated with recon (whoami.exe, arp.exe) and its parent process is Regsvr32.exe
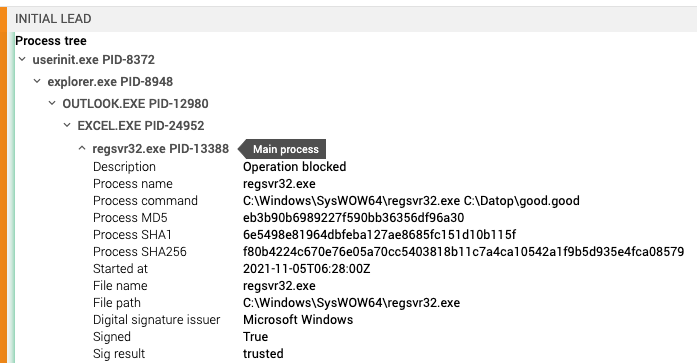
Here’s an example of a SquirrelWaffle alert in the Expel Workbench™:
Expel Workbench™ process tree lineage of SquirrelWaffle: Outlook -> Excel -> Regsvr32
Resilience recommendations:
- Block Microsoft Office macros and Excel 4.0 macros as they’re a popular target to exploit with malware. While macros may offer some productivity improvements, if you can live without them, it’s best to disable them entirely.
- We know it’s a tall order, but spend time educating your users on how to spot phishing emails and suspicious links or attachments.
Various exploits used to deploy coin miners
TL;DR: Routes of infection vary, but attackers’ end goal remains the same: deploying crypto mining software.
We’ve now brought up cryptojacking in a few of these reports. So you may be asking yourself, “what is cryptojacking and why should I care?” That’s a totally fair question. The quick answer is that attackers want to use other people’s computing resources to do computational work to earn cryptocurrency and profit.
Crypto mining generally isn’t profitable when you factor in operational costs – it requires tons of energy and resources to earn cryptocurrency this way. But if attackers can cut costs by using other people’s resources (electricity, internet and primarily processing power), it can become profitable.
Consider this metaphor – you’re a hard working gold panner in your local creek. You’ve been panning for gold for a year now and some days you’re able to find a nugget and pay your bills for the month, but on average, you don’t break even. In fact, you’re losing money gambling on your luck, which is also dependent on how many hours you put into the actual work of wading into the water and sifting through rocks and sand.
But what if you could convince your neighbors to also spend their days panning for gold in their creeks and send you the nuggets? Your problem would be solved! Except that no one would actually do that since there’s nothing in it for them. Which is what cryptojacking boils down to – taking advantage of other people’s resources without their permission so you profit.
So how does this happen in a digital world? Primarily by taking advantage of vulnerable servers on cloud infrastructure. We’re typically alerted to a cryptojacking operation by an alert for network traffic patterns that we know resemble crypto mining. We’ll see lots of outbound traffic to a miner pool, which is essentially the digital river from our metaphor where people send their cryptographic hashes and try to get a reward. Our investigations typically lead us back to an exploited vulnerability on a public-facing web server. Here are some of the specific tactics we’ve seen recently:
Public Amazon S3 buckets are a necessary storage option used regularly by AWS cloud customers. This also makes them a popular target for attackers. Bad actors scan the contents of these buckets for valuable access keys and other identifiable information that shouldn’t be public. These data leaks can occur if proper S3 bucket access controls aren’t implemented.
In one instance, attackers gained access to AWS through credentials that were mistakenly made publicly available. The first thing the attackers did was run new EC2 instances (virtual servers hosted on AWS) in our customer’s AWS environment and begin crypto mining. Notably, they didn’t attempt any other exploitation – we suspect they didn’t want to set off alarms, so took the shortest path to begin crypto mining as quietly as possible. Going unnoticed while their operations run is the ideal scenario for cryptojacking attackers.
So what coin miners do we typically see? A lot of XMRig to mine Monero. But on rare occasions, we see a coin miner deployed alongside advanced malware that not only mines coins but also steals access keys and spreads within an organization’s cloud environment. In November, we observed the crypto mining TNT Worm (which is also able to steal AWS access keys) on a customer’s demo EC2 instance within minutes of being turned on. We suspect this EC2 instance was compromised because it hadn’t been regularly updated since it was for demo purposes and wasn’t frequently active.
This worm has remained prevalent, consistently taking advantage of misconfigured systems. The worm also has an interesting greedy characteristic – it attempts to identify if there are any other miners running on the infected hosts and disables any that are to ensure processing power and mining capabilities are dedicated to its mining operation.
The TNT Worm is configured to spread itself by scanning for additional misconfigured Docker platforms and Kubernetes systems. In this incident, we identified the worm and provided remediation steps to our customer in seven minutes after evidence of crypto mining was identified. Our investigation didn’t find evidence of AWS access key exposure. We suspect the TNT Worm prioritizes getting mining operations up and running before downloading additional scripts that attempt to propagate in the environment through AWS access keys.
With regard to another crypto jacking infection pathway, this month also showed us that poisoning npm packages wasn’t a one hit wonder. Last month, we discussed hijacked ua-parser and rc packages used to deploy crypto mining software. This month, we saw the popular coa package causing trouble for a few of our customers.
Resilience recommendations:
- Regularly check and update outdated software on public-facing servers and maintain a consistent update regimen to keep up with newly discovered vulnerabilities.
- Follow security news and subscribe to threat intelligence feeds about current and past exploits to stay up-to-date on the latest targets.
- Implement network layer controls to detect and block network communications to cryptocurrency mining pools.
- Have computing resource alarms forwarded to your SIEM to alert your team of overtaxed resources deployed for cryptojacking.
- Implement access controls for Amazon S3 buckets.
- Scan and identify public-facing assets using Shodan.
- Confirm your endpoint detection and response (EDR) coverage across all of your endpoints.
Takeaways
One of the most notable trends our team detected this month was a 10 percent increase in commodity malware incidents resulting from phishing emails containing links to download malicious macro-enabled Microsoft Office and Excel documents – in most cases, SquirrelWaffle. If not detected and stopped, SquirrelWaffle typically downloads a banking trojan onto victims’ machines to compromise their financial accounts.
Our top tip to combat this trend: disable Microsoft Office macros and Excel 4.0 macros since they’re such a popular target to exploit with malware. Then, spend time educating your users on how to spot and report phishing emails and suspicious links or attachments so they’re less inclined to click when that malicious scam comes through. And in case a user does fall for the phishing campaign, deploying SquirrelWaffle into your environment, consider the detection opportunities discussed above to catch it in its tracks.
Another key trend we’ve mentioned before is that malicious cryptocurrency activity is on the rise this year. Attackers are using different methods of infection, but share the same end goal – cryptojacking, or using their victims’ computing resources to run crypto mining software.
To keep miners out of your environment, make sure to keep your software up-to-date on public-facing servers and keep an eye out for newly discovered vulnerabilities. Also make sure to follow proper endpoint guidance, including EDR and patching. Additionally, tools that alert your operations team of overtaxed resources can also help your security team by indicating resources deployed for cryptojacking.
We’ll be back with insights on December’s top attack vectors. In the meantime, have questions about this month’s data or what it means for your org? Drop us a note.