Current events · 8 MIN READ · BRITTON MANAHAN, SIMON WONG AND HIRANYA MIR · MAR 17, 2022 · TAGS: Guidance / tech stack / threat landscape
We’re often asked about the biggest threats we see across the incidents we investigate for our customers. Where should security teams focus their efforts and budgets?
To answer these questions, we’re sharing monthly reports on the top attack vectors, trends, and resilience recommendations identified by our security operations center (SOC). Our goal is to translate the security events we’re detecting into a security strategy for your org.
For this report, our SOC analyzed the incidents we investigated in February 2022 to determine the top attack vectors used by threat actors. Here’s what stood out this month:
- Attackers using tried and true tactics – including Log4j – to infiltrate systems and deploy coin miners
- Threat actors deploying the “AsyncRAT” remote administration tool through an ISO file
- Phishing tactics targeting credentials through Adobe and cryptocurrency
Keep reading for details and our tips on what to do about all the above.
The usual suspects
TL;DR: It’s important to keep an eye on known threats even as new ones emerge. We observed attackers using multiple threat vectors and tactics this month that we’ve highlighted in previous reports.
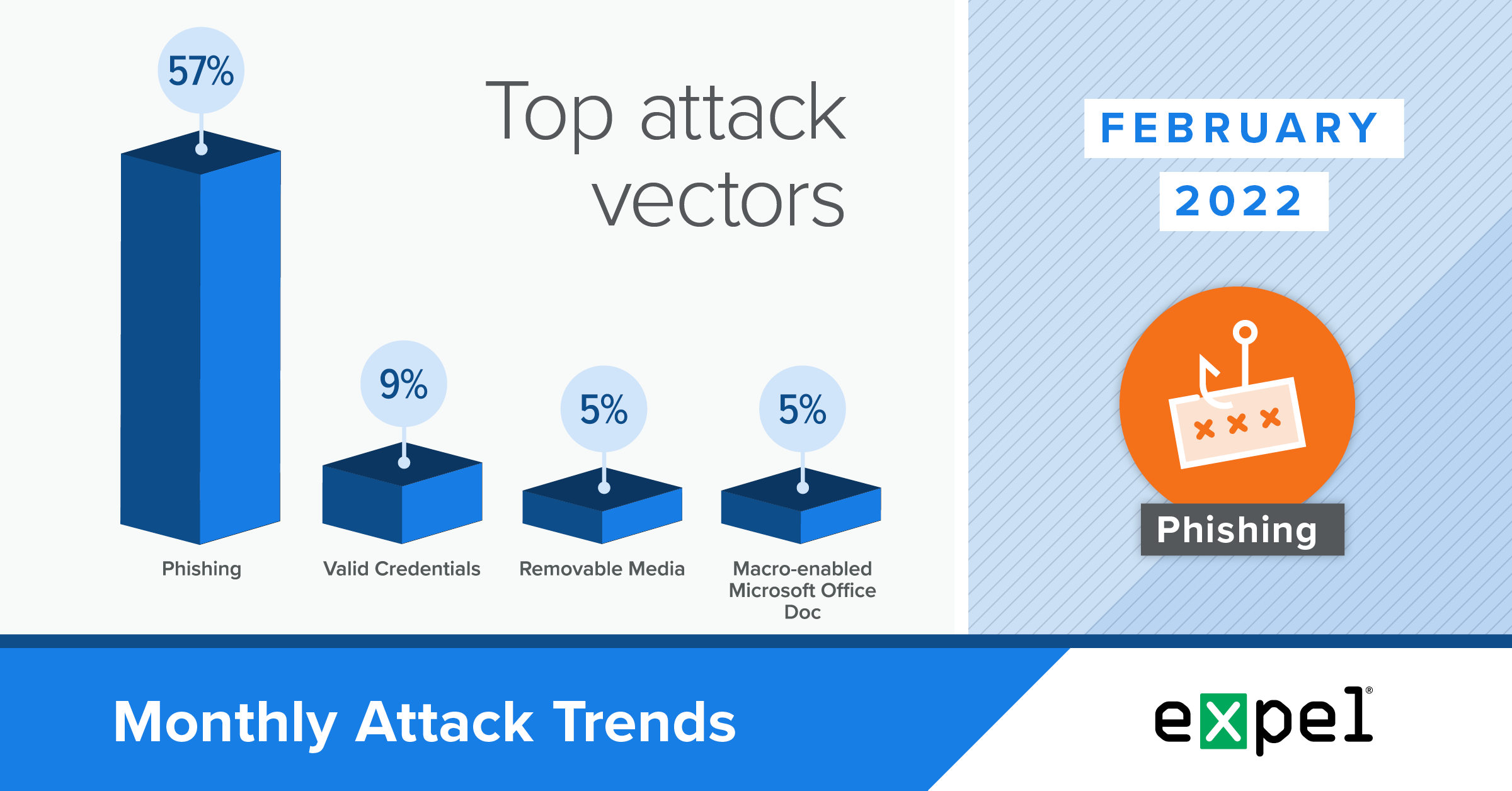
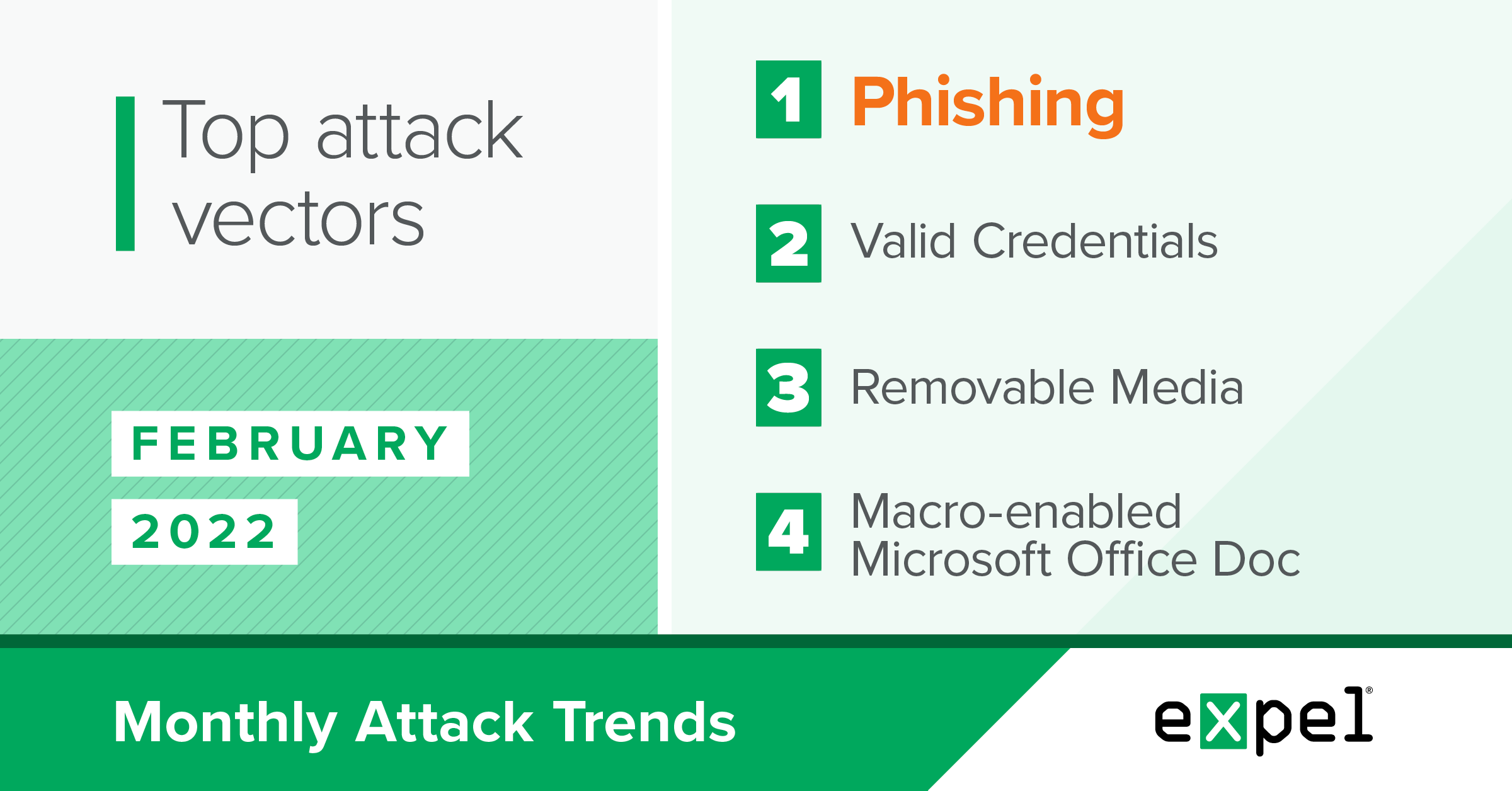
In February 2022, we observed a more even distribution of non-phishing threat vectors, with the usual suspects from previous reports making a reappearance. This includes removable media ranking as the initial vector for five percent of February’s incidents, indicating it remains a relevant threat after our discussion in last month’s report.
The second-most frequent attack vector in February was the use of valid credentials. In two of the incidents involving valid credentials, we saw attackers authenticate into cloud-based single sign-on (SSO) identity providers. We detected and stopped this activity before attackers could progress based on logins from abnormal countries and the identity provider reporting suspicious activity for the account.
We previously covered the opportunities available to threat actors who gain access to SSO accounts in our September 2021 report. Phishing emails containing links to credential harvesters and other types of credential exposure or reuse increase the risk of threat actors gaining access to any business apps provisioned by the SSO provider. It’s not uncommon for credential harvester pages to mimic popular SSO cloud identity providers like Okta.
While down significantly from previous months, we also observed one public-facing exploit used to deploy a crypto miner in February. In this incident, the attacker took advantage of the Log4j vulnerability, which we detected based on indicators of compromise (IOCs) matching a current threat actor campaign. In our December 2021 report, we spoke about how the downstream nature and prevalence of this Java logging library will keep this vulnerability relevant for some time.
Another trend called out in our October 2021 report was cybercriminals targeting cryptocurrency by highjacking computing resources to mine for rewards — also known as cryptojacking. In the previously mentioned Log4j incident, we saw the threat actor use their unauthorized access to deploy the XMrig crypto mining software. Despite the current dip in the cryptocurrency market, threat actors are clearly still interested in acquiring cryptocurrency as 15 percent of payloads deployed in critical incidents we investigated in February were crypto mining software.
Resilience recommendations:
- Make sure your security awareness training includes sections on the dangers of external USB storage devices.
- Implement phish-resistant MFA everywhere (FIDO/WebAuthn).
- Enforce MFA prompts when users connect to sensitive apps through app-level MFA.
- Conduct a vulnerability scan to understand your attack surface and detect any vulnerabilities present on public-facing systems.
- If you’re using Log4j, you should update to version 2.17.1 ASAP if you haven’t already. The latest version is on the Log4j download page. The patched version of Log4j 2.17.1 requires a minimum of Java 8. If you’re on Java 7, you’ll need to upgrade to Java 8.
- If updating to the latest version isn’t possible, you can also mitigate exploit attempts by removing the JndiLookup class from the classpath.
AsyncRAT
TL;DR: We observed AsyncRAT malware used as a payload in several incidents this month.
The AsyncRAT malware variant made up 15 percent of all identified malware payloads for incidents we responded to in February 2022.
AsyncRAT is an open-source remote administration tool (RAT) written in C# and available on GitHub. Its functionality includes all the standard RAT abilities, including file uploading, downloading, and command execution.
The incidents we encountered deployed AsyncRAT using an initial ISO file, which was mounted on the local computer system as a drive containing a VBScript file. When executed, this initial VBScript file launches a PowerShell script that’s responsible for decompressing two DotNet modules. One of these DotNet modules is loaded into memory by the PowerShell script while the raw bytes for the second module are passed as a parameter to the initial module. The initial DotNet module loaded into memory by the PowerShell script then injects the second DotNet module (the AsyncRAT payload) into a process supplied as a parameter. In both incidents, aspnet_compiler.exe, the compilation tool for ASP.NET website projects, was the target process for this final AsyncRAT payload.
The deobfuscated command from the PowerShell script used to achieve this AsyncRAT injection was:
[Reflection.Assembly]::Load($InjectionModule).GetType(‘NV.b’).$get1(‘Execute”).Invoke($null,(‘C:WindowsMicrosoft.NEtFrameworkv4.0.30319aspnet_compiler.exe’,$ASyncRAT))
$InjectionModule is the DotNet Module that performs the process injection based on the target program (aspnet_compiler.exe in this example) and $AsyncRAT holds the raw bytes for the AsyncRAT remote access payload that will be injected into the remote process.
Additionally, our analysis found that the DotNet modules from one of these incidents added a level of obfuscation by using the ConfuserEx DotNet module obfuscator to avoid detection of the fileless DotNet module components. These components are considered fileless because their unobfuscated and decompressed versions are never written to persistent storage, but are loaded into the live run-time memory of the local computer system.
Resilience recommendations:
- Confirm your endpoint detection and response (EDR) coverage across all of your endpoints.
- Configure Windows Script Host (WSH) files to open in Notepad. By associating these file extensions with Notepad, you mitigate a primary entry point.
- Implement layered security controls across your environment to detect and prevent evolving threats.
- Perform a penetration test against your environment to evaluate any gaps in your security.
- Subscribe to open source intelligence (OSINT) feeds to stay up-to-date on malware trends and use this intelligence in your deployed security tech.
Phishing
TL;DR: We saw an increase in credential harvesters using Adobe services and cryptocurrency scam emails in February 2022.
As usual, phishing was the biggest attack vector used by threat actors in February, involved in 57 percent of the incidents we investigated. We reviewed over 5,000 potentially malicious email submissions and identified two key phishing trends using the following techniques:
Credential harvesters using Adobe services
We noticed an increase in the number of emails using legitimate Adobe domains. Attackers are taking advantage of the ability to register an adobe.com subdomain through Adobe Campaign to give their emails a sense of legitimacy. Emails from this trend typically contain requests to collaborate on new projects, aiming to deceive recipients into believing the emails are legitimately work-related.
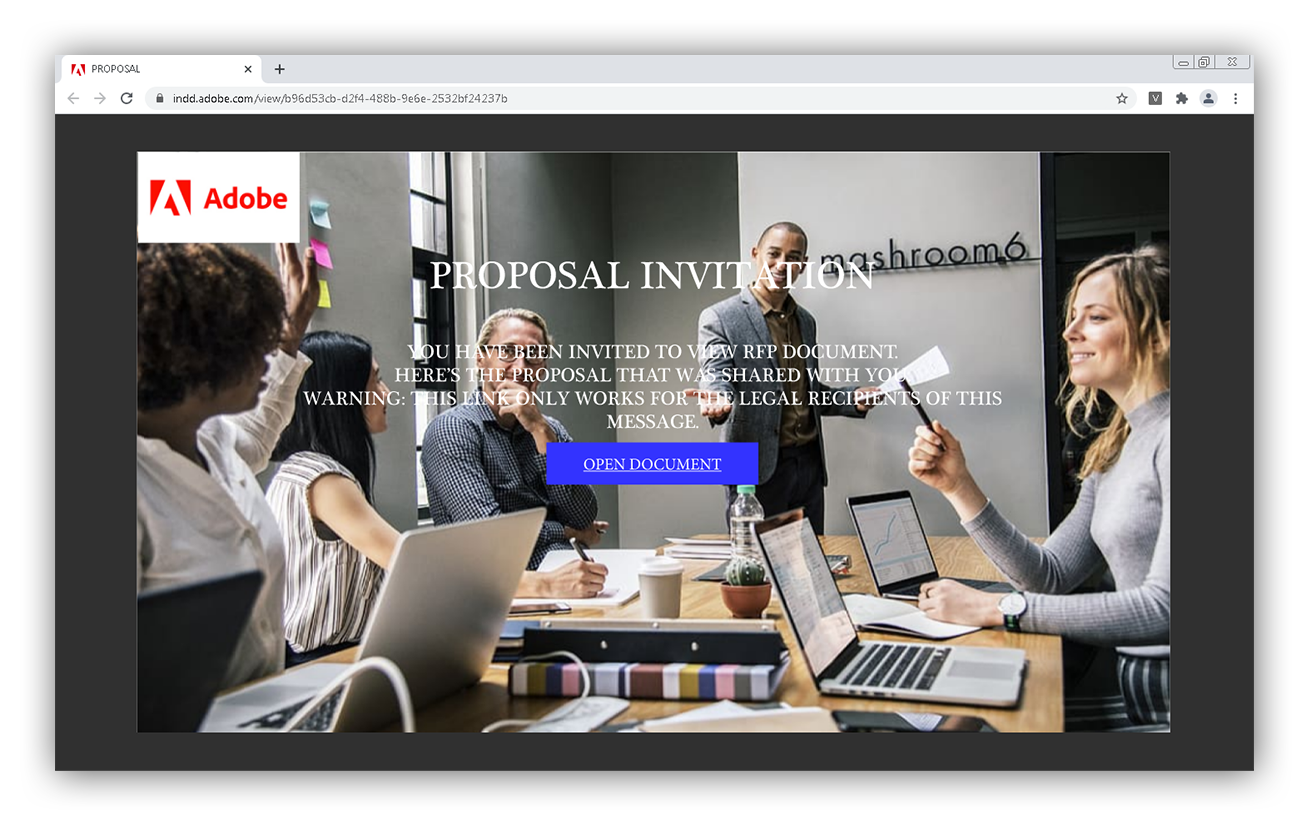
Recipients are instructed to follow links that redirect them to what seems to be an Adobe webpage, but actually prompts them to download a file containing malicious code or click another link to navigate to a fake sign-in page. If the victim then enters their credentials, threat actors capture them and can begin a business email compromise attempt.
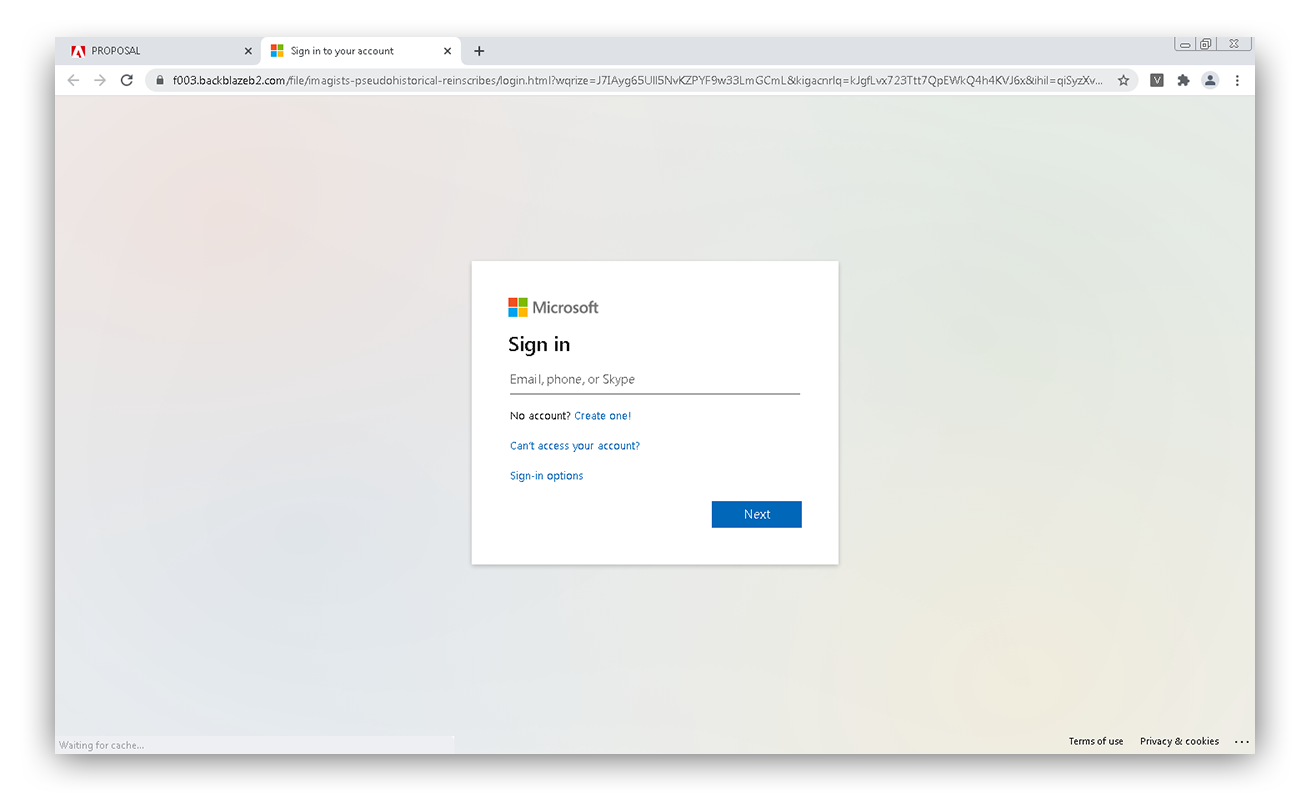
Cryptocurrency scams
Since the surge in popularity of cryptocurrency, we’ve observed an influx of new phishing tactics as threat actors try to take advantage of the anonymity of cryptocurrency transactions to keep themselves from being traced.
Since the start of the invasion of Ukraine, threat actors have specifically begun to impersonate legitimate aid organizations to exploit people’s desire to support refugees and victims with donations.
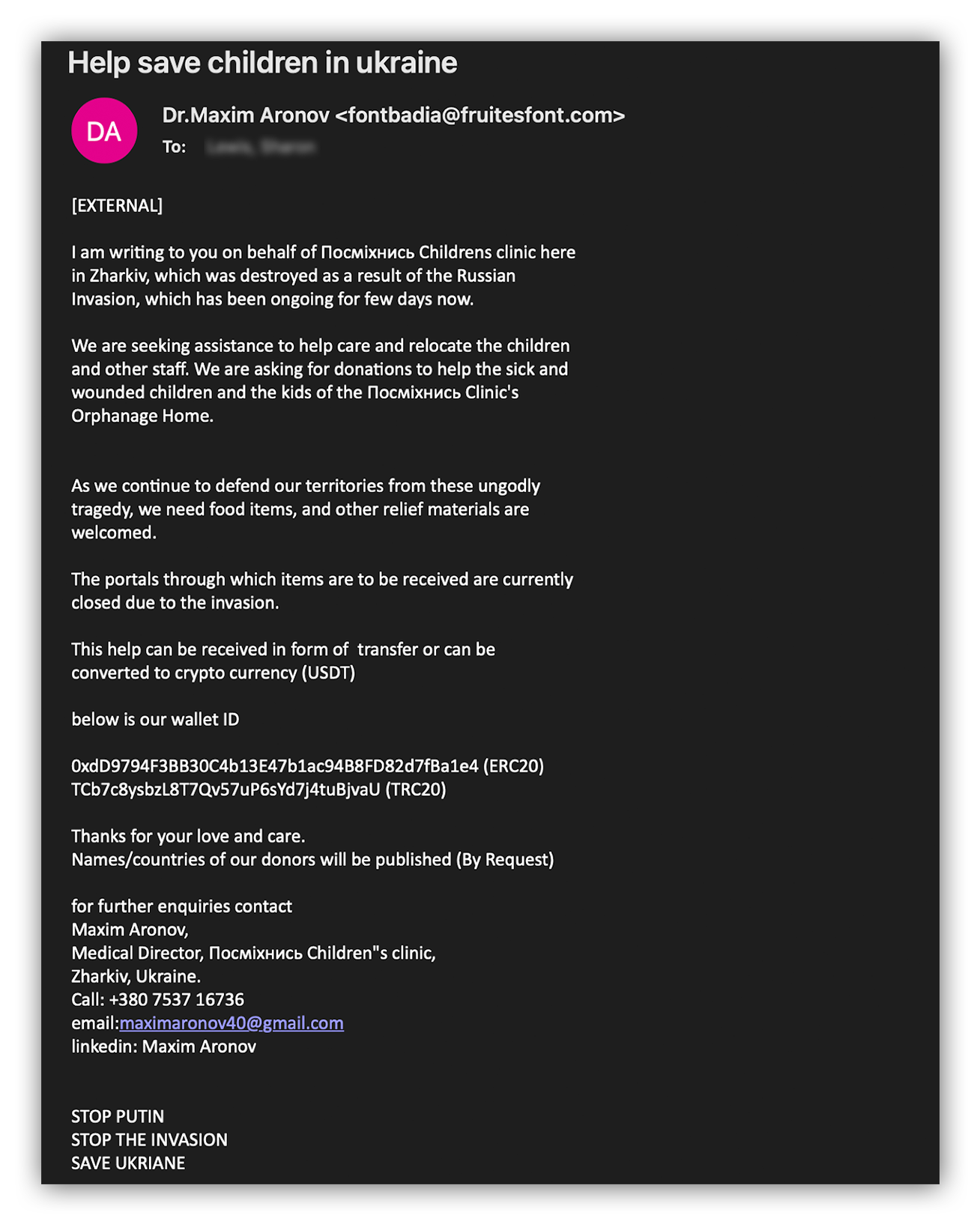
Here are a few phrases we’ve seen in phishing emails referencing Ukraine to target cryptocurrency:
Email subject:
- “Help – Bitcoin”
- “Payment from your account”
- “Help save children in ukraine”
- “Crypto – Account”
- “Ukraine Donations”
Email body:
- “Here is my BTC wallet”
- “transfer bitcoins”
- “This is my bitcoin id”
- “Now accepting cryptocurrency donation”
- “below is our wallet ID”
Given threat actors’ horrible appropriation of this conflict for malicious means and personal gain, those looking to provide financial support to victims of the invasion of Ukraine should confirm the legitimacy of any donation-related communications before providing financial information. For example, recipients should inspect the sender’s email address, search the organization online to confirm key contact details, and hover over any buttons/URLs in the email to inspect the redirect path without clicking it.
Phishing resilience recommendations:
- Conduct regular security awareness training for employees, including phishing simulations.
- Don’t click any links in a suspicious email.
- Double check the sender’s address and return path in suspicious emails.
- Use open source tools to verify details for external senders and organizations.
- Use a verified internal channel (for example, an email to a verified third-party vendor or a message on your company’s internal messaging platform) to confirm if the communication/request in a suspicious email is legitimate and expected.
- Block access to malicious websites.
- Remove the email from a user’s inbox if it’s determined to be a phishing attempt.
Takeaways
In February 2022, we observed several threat vectors and tactics discussed in our previous reports making a strong reappearance, including:
- Removable media
- Use of valid credentials for cloud identity providers
- Public-facing exploitation of Log4j
- Cryptojacking
- Phishing with credential harvesters
An important step to protect against many of the above: deploy phish-resistant MFA (FIDO security keys) everywhere you can. This is particularly important to make sure threat actors don’t gain access to your SSO tools and all of the sensitive apps and data they provide access to.
While only involved in one incident we investigated in February, it was telling to see the Log4j vulnerability continuing to be exploited against public-facing systems. This vulnerability will remain relevant and should be examined during any vulnerability scans conducted in and against your digital environment.
In terms of malware, AsyncRAT made up 15 percent of identified malware payloads from incidents we detected and responded to in February 2022. This open source remote administration tool was initially deployed using an ISO file and used a number of stages to eventually inject its final payload into the memory of a legitimate process.
And let’s not forget: removable media remained an important attack vector in February and threat actors continued to use unauthorized system access to deploy crypto mining software. The takeaway: attackers will return to the vectors and tactics they know work, even as new ones emerge.
Phishing remained in the top spot for infection vectors in February. Two key trends stood out: first, threat actors using the ability to register an adobe.com subdomain through Adobe Campaign to give their emails a sense of legitimacy. Attackers hope the association with adobe.com will make their victims more likely to click links in the email and follow through on downloading malicious files or entering credentials. Users should check sender addresses and URL pathways (without clicking) and check with colleagues through verified channels if they’re expecting to collaborate on Adobe-based projects. When in doubt, it’s always better to forward potential phishing emails to your security team for investigation.
The other phishing trend we observed involved cryptocurrency — specifically, threat actors requesting crypto transfers by pretending to solicit donations related to the war in Ukraine. While Ukraine has legitimately raised $35 million in cryptocurrency donations, threat actors are trying to take advantage of the crisis for personal financial gain. The verified crypto wallet addresses for donations to Ukraine can be found on the country’s official Twitter account. Details for other organizations should be confirmed through verified external sources before any financial information is provided.
We’ll be back with more attack vectors insights and threat data — but we’re changing things up! Our threat reports are going quarterly so we can provide more data on what we’re seeing, highlight detection opportunities, and dive further into resilience recommendations that can protect your org. Expect to see our first quarterly threat report in May. If you read our Great eXpeltations annual report, that’s a hint of what’s coming your way!
In the meantime, have questions about this month’s data or what it means for your org? Drop us a note, we’re happy to chat.