Security operations · 4 MIN READ · PETER SILBERMAN · FEB 8, 2024 · TAGS: MDR
Auto remediation represents substantial benefits, including cost savings and faster response times, but one size doesn’t fit all. Your solution should be customizable for your specific environment.
[This post originally published in 2022. We’ve updated it with current information. Special thanks to Kim Mahoney and Matt Dubie for their work in helping to update the post.]
Here’s a basic truth for any managed detection and response (MDR) provider: effective remediation of cybersecurity incidents is critical for our customers’ business. Getting to the fix quickly is obviously job one, but when done properly, the organization realizes a host of additional benefits centered on increased security and cost savings.
What is automated remediation?
Automated remediation is the process of analyzing and resolving cybersecurity issues without manual intervention via automatic application of customized scripts, algorithms, or machine learning.
By automating the troubleshooting and resolution of common issues, organizations can significantly reduce response times, minimize downtime, and enhance overall system reliability.
Automated remediation and cybersecurity benefits
Auto remediation represents tremendous value for organizations.
Faster response to critical issues
Perhaps most importantly, auto remediation excels in rapid response. Every second matters in an investigation, and whether it’s a system failure, network outage, or security breach, automated solutions drastically reduce response times, minimizing the impact on business operations. (It’s also important that customers have complete transparency into the investigation.)
Cyberattacks often exploit vulnerabilities swiftly, and a delayed response can result in substantial financial losses and damage to an organization’s reputation. Automated remediation helps organizations safeguard their assets by preventing the escalation of threats.
Quick response times also contribute to regulatory compliance adherence. Many data protection regulations require organizations to promptly detect and address security incidents. Automated remediation ensures a consistent and timely approach to compliance, reducing the risk of regulatory penalties and legal repercussions.
Reduced downtime and increased reliability
One of the primary benefits rests with its ability to minimize downtime. It’s hard (read, impossible) for human analysts to pore over billions of log entries, but it’s a snap for automated systems, which can identify and address issues in real-time, often before users even notice a problem. This means dramatically improved system reliability, increased availability, and faster response times.
Cost savings
Manual troubleshooting and issue resolution can be time-consuming and thus costly. These processes generates significant cost savings by automating alert analysis, which significantly frees up resources, allowing security and IT teams to focus on more strategic tasks that contribute directly to business objectives.
A deeper look at the numbers illustrates the cost-savings benefits of automated remediation for the customer. In Q2 2022:
- We had 3,378 remediation actions (RA) that were manual.
- ~30% of incidents had more than one remediation action.
In our Quarterly Threat Report for Q2, we noted that the median time to complete a non-automated remediation action was two hours. When automated, the median time drops to 15 minutes—an 87.5% reduction.
If you have a napkin handy, you can flip it over and ballpark the benefit to your organization.
Enhanced scalability
As businesses grow, so does the complexity of their IT infrastructures. Since automated solutions can adapt to changing environments and handle a growing number of devices and systems, auto remediation lets organizations scale efficiently without an increase in the need for manual intervention. The business can grow in capability without having to add headcount, or deal with a drop in service levels that typically come with a growing team.
Improved compliance and security
Automated remediation processes help organizations maintain compliance with industry regulations and security standards. By promptly addressing vulnerabilities and security incidents, businesses can strengthen their overall cybersecurity posture and protect sensitive data.
Beware the one-size-fits-all approach: customer control is essential
Perhaps the most important benefit of automated remediation, though, lies in its powerful flexibility.
During an active incident, remediation reduces an organization’s risk, but customer control of that process is absolutely essential. Many providers sell a one-size-fits-all, full-remediation model, but organizations should have the option to tailor the function to their specific business context, technology, risk tolerance, policies, and general comfort level, allowing them to dictate when to remediate and when not to.
Any number of factors can influence that comfort zone, including internal policies, familiarity with the vendor, lingering aches and pains from bad past experiences—we get it. For example, if you don’t want a third party to isolate hosts during an incident, that should be your decision. A good solution can disable compromised user accounts without isolating hosts.
Remediation isn’t (or shouldn’t be) all-or-nothing.
The platform itself should know the rules and preferences of the customer; this ensures consistency and scale, and also makes sure security operation center (SOC) analysts don’t have to pass around sticky-notes reminding them to remediate a certain way for customer A, but not customer B.
A security operations platform that’s context-aware and customizable allows the client organization to:
- Reduce risk by allowing automated remediation steps the moment an issue is detected.
- Reduce fatigue and burnout (why wake a customer analyst at 2 am to disable an account when the system can do it for you?).
- Keep customer analysts focused on more important work—what does the business deem important?
MDR/automated remediation at Expel
Regardless of whether they opt for auto remediation, organizations should insist on comprehensive reporting that includes remediation steps as part of the investigative process. Vendors can (and should) always recommend remediation actions, even if that vendor isn’t going to take the steps themselves.
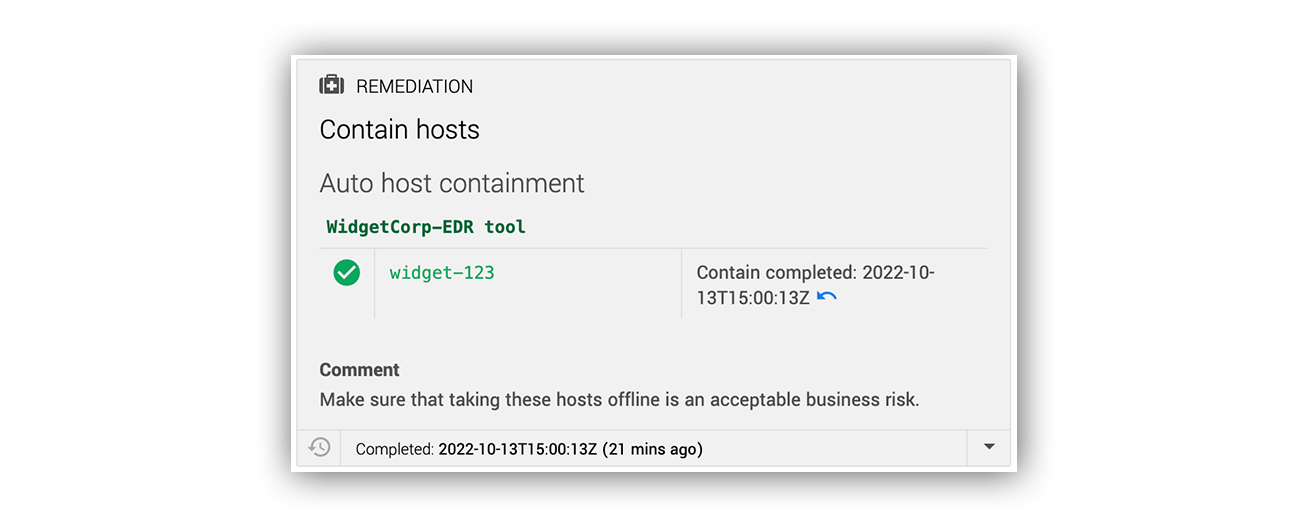
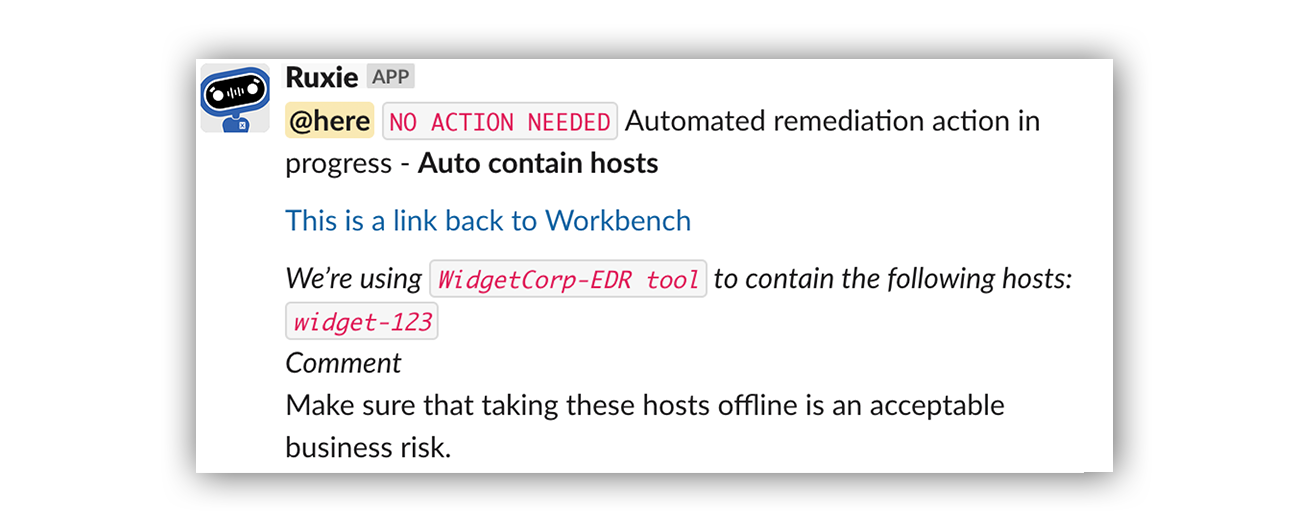
Here’s what it looks like in Slack:
Many actions can be automated, including (but not limited to) host containment, disabling a user account, removing suspicious emails, or blocking a known bad hash. Customers can also decide what resources Expel can remediate on their behalf. As mentioned above, this is far from a cookie-cutter approach.
Raspberry Robin/Evil Corp incident: huge time savings
Raspberry Robin, a widespread USB-based worm that acts as a loader for other malware, has significant similarities to the Dridex malware loader, meaning that it can be traced back to the sanctioned Russian ransomware group Evil Corp. (Source: DarkReading)
This past June a CrowdStrike alert hit our queue that related to msiexec launching with unusual arguments on a customer host. Our team identified this as activity consistent with the installation of a variant of the Raspberry Robin Worm malware family attributed to Evil Corp.
Using CrowdStrike’s APIs, it took our analysts 5.5 minutes to progress from the alert hitting the queue to containing the host and stopping the ransomware. When the stakes are high, there’s no time to waste in remediating.
Auto remediation: it’s your call
Automated remediation should be tailored to your organization and based on the frequency of threats seen in your environment. The customer decides which users and endpoints should be immediately taken offline after a compromise is confirmed. This allows the security team to focus on other initiatives instead of spending a ton of time on remediation.
As you consider MDR and reducing risk, we hope offloading some of this costly work to a trusted provider is front-of-mind. It’s also useful to understand the unique context of your org, which includes business goals, existing technology, even corporate culture, and to talk with your provider about it.
Want to learn more about Expel’s approach to automated remediation?