Product · 3 MIN READ · CHANDLER MATTHEWS · OCT 31, 2023 · TAGS: Announcement
Cybercriminals recently deployed novel methods of persistence and privilege escalation in Okta. Expel analyzed the information and has developed two new detections.
On August 31, Okta published an article describing a recent novel attack they’d observed in their customer’s organization. This strategy gained global attention when used to deploy ransomware against MGM. The attack created an additional identity provider that allowed access to apps in the victim organization. New techniques are notoriously difficult to build detections for due to limited information. Luckily, Okta was proactive in their article, detailing what events to track to detect cross-tenant impersonation attempts.
The initial access and privilege escalation involved were not new, though. The attack started with social engineering targeting an IT service desk, requesting a reset of MFA credentials for admin accounts. The compromised admin account was then used to reset MFA factors in other admin accounts or grant admin rights to additional compromised users. Okta included details in their article on how to detect these techniques, as well.
With all these detections outlined for us, it seems like a pretty straightforward solution—alert on each of the events described in the article. The problem is that on their own these individual signals are noisy and false-positive prone.
For example:
- We could alert every time a user’s MFA factors are reset, but how often does a user get a new phone and need those factors reset?
- Or we could alert every time a user is granted admin rights, but how frequently are new admins created?
- Maybe instead we can alert every time an identity provider is created in an organization, but again, how often does this happen?
We’ll save you the research: these events happen all the time for completely legitimate reasons. So our next step is determining how we can pair and enrich these events to detect the true evil.
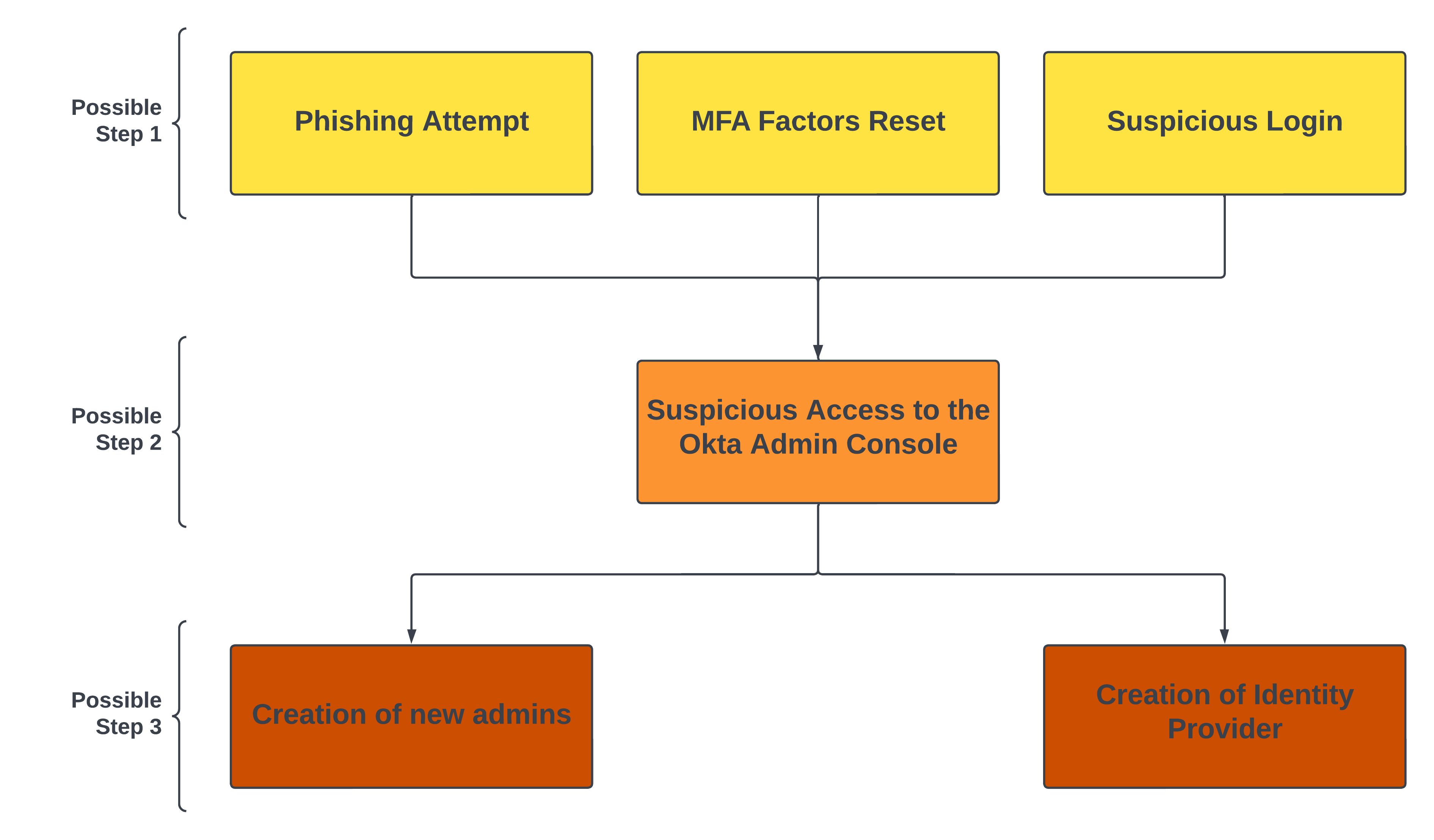
The techniques from this attack follow an obvious order that we can leverage to build our detections.
A detection that correlates these exact events will be very high fidelity but also too specific. It wouldn’t leave room for fluctuations in the attacker’s process where they might do things differently. The attacker could switch accounts at any time making it very difficult to correlate. Or they could skip creating additional admins and go straight to creating the Identity Provider. This logic is too rigid and will only be useful if the attacker follows a very specific pattern.
We need something more dynamic that is still high fidelity.
Instead of using the rigid logic mentioned above we broke it down further. The various techniques used in this attack can be categorized by the order they may occur in.
Now we can build detections that alert on Step 1, followed by Step 2, followed by Step 3. The events in each category can be sorted into detectable patterns that are more dynamic and allow for variation in the attack. However, after extensive testing three detections were determined to be the highest fidelity.
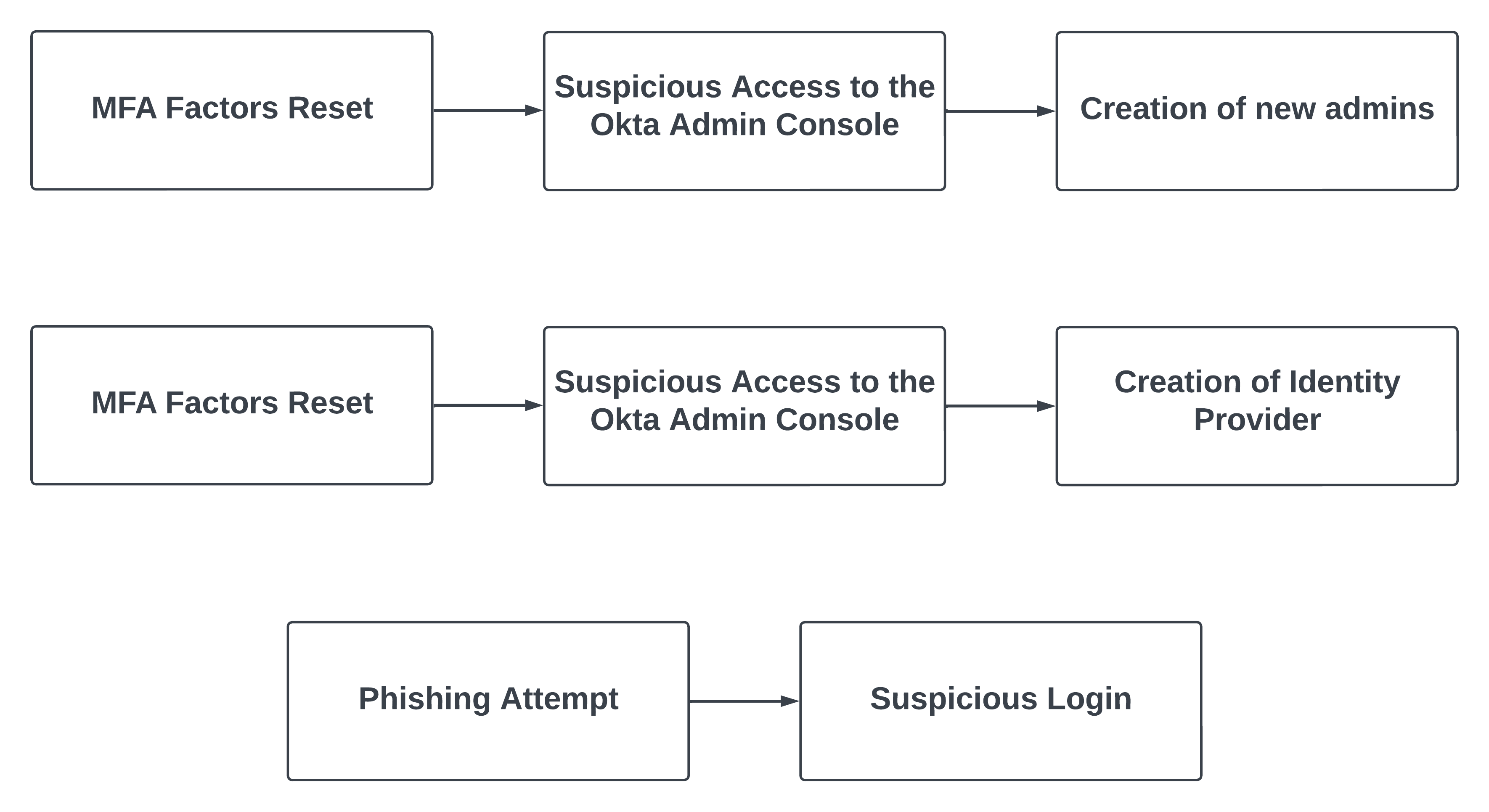
We chose to include the MFA Factors Reset event in two patterns because Okta called it out specifically as a strategy used against multiple organizations in recent weeks. Both of these are included in our new detection Okta Suspicious Admin Activity Correlation.
Based on the details provided we also created a detection for an Okta Fastpass Phishing Alert followed by Suspicious Login Activity. As a bonus, this alert provides coverage beyond this attack. This is included in our new detection Okta Fastpass Phishing Attempt and Geo-infeasible Login Correlation.
We got to work as soon as Okta released information on this attack. After planning out how we can build high fidelity detections we put them into testing, tuned them for accuracy, re-tested them, and then had two solid detections ready for production.
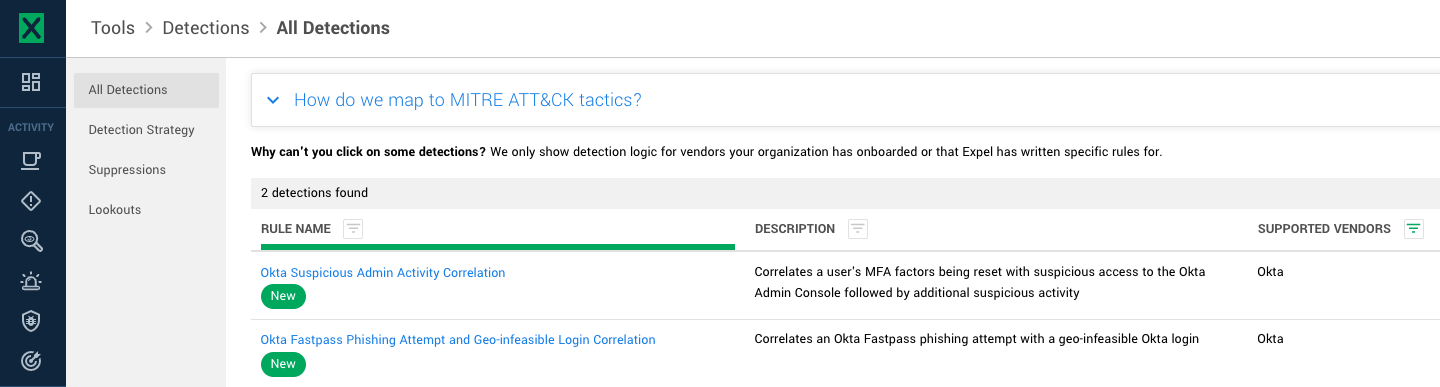
These events are being correlated and surfaced by two Expel detections today:
- Okta Suspicious Admin Activity Correlation
- Okta Fastpass Phishing Attempt and Geo-infeasible Login Correlation
As seen in Workbench:
Attacker’s strategies never stop evolving, but Expel is creating new detections to match them every step of the way. We provide coverage for our customers, but we recommend using Okta’s best practices to prevent an incident from ever starting.