Cloud security · 2 MIN READ · DAVID BLANTON · NOV 17, 2020 · TAGS: AWS / Resource
Our SOC team remediates quite a few incidents in Amazon Web Services (AWS). Some of these were surprise attacks from red teams, while others were live attackers in our customers’ cloud environments. When running these incidents down, some common themes emerged about when and why attackers use different AWS APIs – and they mapped nicely to the MITRE ATT&CK tactics.
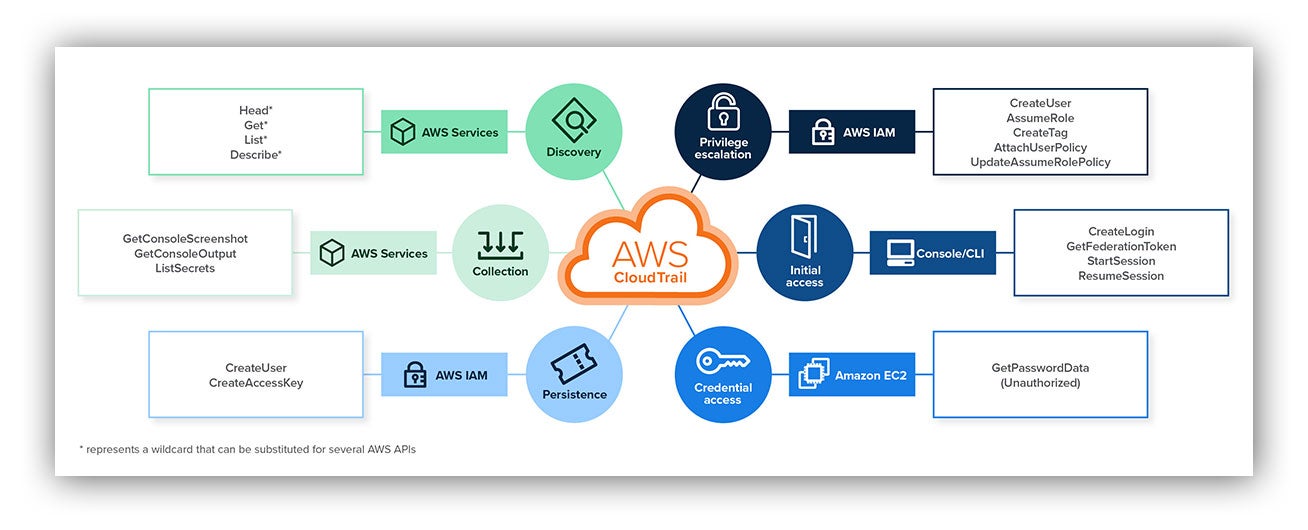
We noticed that these notes were really helpful when our analysts were investigating CloudTrail logs. So we captured these AWS APIs in a mind map and loaded it into our Expel Workbench.
This mind map is a TL;DR of the attack paths an attacker may take once they gain access to an AWS environment.
Why do we think you’ll find it useful?
First, it can help analysts see the bigger picture during investigations, so they can quickly identify risk and possible compromise. Full disclosure, the AWS mind map doesn’t cover every API call and the associated ATT&CK tactic. But it can be a resource during incident response and, after remediation, can help you tell the story of what happened to the rest of your team or your customer.
For example, let’s say you find yourself responding to a GuardDuty alert for compromised EC2 credentials. While reviewing successful AWS API calls from the external source IP address and Amazon Resource Name (ARN), you spot API calls for CreateUser followed by PutUserPolicy and AttachUserPolicy after a series of Get*, Describe* and List* calls. If this were unauthorized activity, the mind map can help piece together that this may indicate automated reconnaissance in which an attacker created a privileged user to establish persistence in your environment.
We’ve also used the mind map to summarize red team engagements after we’ve chased them in a customer’s environment. We told the story of the engagement by filling in a blank mind map with what APIs the red team used during their engagement.
And these are just some examples of how the Expel AWS mind map has already been incredibly useful to us.
We hope this resource will be helpful to you if you ever find yourself chasing a bad guy through the cloud.
In addition to the mind map, we’ve created a cheat sheet for how to use and get the most out of the mind map, along with a blank mind map that you can use during your investigations.
Click here to get our AWS mind map kit sent directly to your email inbox!