Product · 6 MIN READ · ETHAN CHEN, LIZ MCLAUGHLIN, IAN COOPER, BRIAN BADORREK AND TYLER BEAUREGARD · JUL 16, 2025 · TAGS: AI & automation
TL;DR
- Expel’s AI-powered classification engine categorizes identity alerts and provides transparent decision-making
- Our system uses classifiers for intelligent triage and highlights key evidence-driving classifications to support human decision-making
- Smart auto-closure is implemented with safety nets, including quality control and guardrails, to minimize risk
The 2am identity crisis: Why your SOC is drowning and how to throw it a lifeline
2am. A weary analyst, fueled by lukewarm coffee, stares at an alert. User_Jane_Doe, who never logs in after 6pm, has just accessed a sensitive database from an IP address in a country she’s never visited. Is it a critical breach in progress, or did Jane forget to tell IT about her last-minute vacation and is just catching up on work? The ensuing investigation is a frantic scramble through logs, historical data, and cross-system checks, burning precious minutes—or even hours—while other critical alerts pile up.
This isn’t a rare nightmare; it’s a daily reality for security operations centers (SOCs) grappling with identity-based alerts. And these alerts make up a significant portion of work time for the SOC, sucking up disproportionate time and resources. Analysts battle noisy, voluminous evidence, struggling to distinguish genuine threats from the static of legitimate, albeit unusual, behavior. They also present a significant challenge for newer analysts who may lack the time needed for the thorough investigations they demand.
The fallout? These alerts consistently demand considerably more time to resolve, taking on average 73% longer to identify malicious activity. They’re a major factor dragging out key operational timelines, such as how long it takes to understand an alert and how long it takes for an analyst to even begin working on it. The cost isn’t just in time; it’s in analyst burnout and the risk of real threats slipping through the cracks. Imagine reclaiming nearly thousands of analyst hours a year by taming this beast.
Enough is enough. We’re here to talk about a smarter path forward. This post dives into how we’re leveraging advanced analytics and machine learning to fundamentally change the game for identity alerts. Our mission: to build a more efficient SOC by injecting powerful automation into our response framework. We’re talking automated triage assistance that provides clear answers, intelligent alert disposition, and smarter routing to get genuinely malicious activity in front of human eyes faster than ever before. It’s time to turn identity alert headaches into high-efficiency wins.
At Expel, we run millions of microservices, databases, and workflows per day to support millions of people worldwide through our service. This includes over 135+ third-party vendor integrations among large, distributed ecosystems with multiple stakeholders and a 24×7 SOC at the front lines of some of the largest and most critical organizations in the world (like Visa).
From alert chaos to crystal clarity: Our blueprint for conquering identity threats
Remember that 2am identity crisis? The endless sifting through data, the gnawing uncertainty? We knew there had to be a better way than just throwing more hours or more analysts at the problem. Our strategy isn’t about working harder; it’s about working smarter, by building intelligence directly into our defense systems. We’re essentially giving our SOC a powerful new toolkit, supercharged with advanced analytics and machine learning, to transform how we handle identity alerts from the ground up.
Here’s how we’re turning the tables:
1. Your new first responder: The AI-powered classification engine
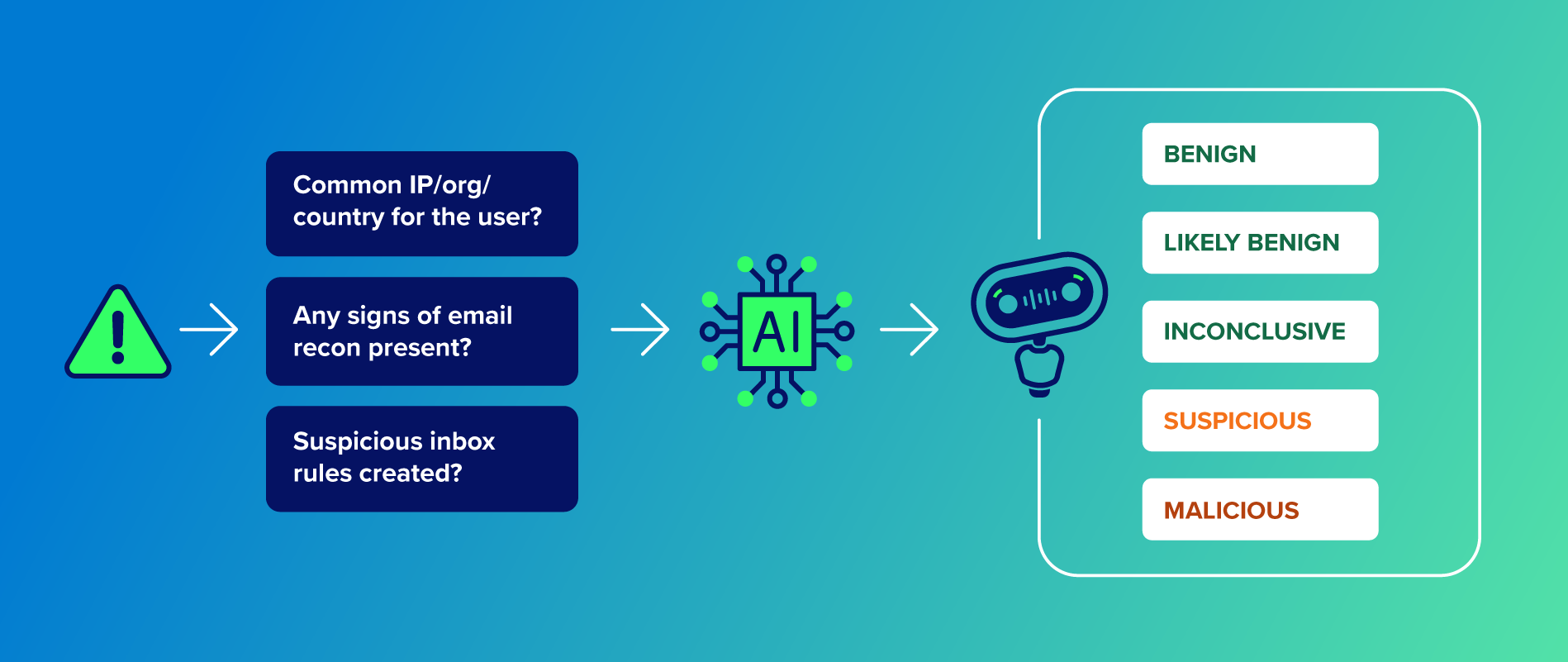
Our machine learning (ML) model analyzes multiple pieces of information to provide an additional layer of initial triage. Think of it as having a seasoned investigator offer immediate guidance. This information is normalized and enriched by our automations from Ruxie tackling highly repetitive tasks, including the root of user role chaining.
The system provides an initial judgment, the information it used to develop that judgment, and drops it into the appropriate queue:
- Malicious: Red alert! Strong indicators of a genuine threat have been detected.
- Suspicious: The model is raising an eyebrow, sensing behavior that leans towards malicious but isn’t a smoking gun yet. This alert is sent to the queue for triage.
- Likely benign: The model leans towards safe, but flags a tiny whisper of potential risk for a quick look.
- Benign: Clear signals of safe, everyday behavior. The alert is auto-closed with a comment, or sent for review if necessary for QA.
- Inconclusive: The digital tea leaves are murky; the model doesn’t have enough to make a strong call either way, signaling a need for human expertise.
And for analysts who love to know the “why,” they can easily dive into the Enhanced Response Indicators. This offers a look under the hood at the factors that drove the model’s decision, providing transparency and building trust. Here’s what that looks like:
This model provides:
- Auto-closures: Reduced queue volume for those alerts the model is confident are benign
- Decision support: Details for analysts on why the model made its call, including the clear contributing factors
2. Intelligent triage with radical transparency
True to Expel’s identity of transparency—we arm our analysts with powerful, transparent, actionable intelligence. Our system uses a sophisticated ensemble of XGBoost classifiers—a proven and powerful machine learning model—to analyze dozens of data points and deliver its expert assessment. We specifically chose XGBoost for its industry-leading accuracy and speed; it excels at finding subtle, complex patterns in security data that simpler models often miss, ensuring a higher degree of fidelity in its classifications.
But we don’t only give our analysts an answer; we show them the evidence. For every single classification our model makes, we immediately provide feature importance, highlighting the top two pieces of evidence that were most influential in driving that decision. For example, an analyst might see an alert classified as “Suspicious” and instantly know it was due to a combination of an “Anomalous ISP” and “First-time Geo-location for User.” This extra layer of decision support is a game-changer. It allows our analysts to instantly grasp the “why” behind the AI’s conclusion, dramatically speeding up their own validation process and building deeper trust in the technology. We’re replacing automatic actions with high-fidelity, actionable intelligence.
3. Smart auto-closure with built-in safety nets
While the goal is to automate as much as possible, we’ve built in crucial safeguards, especially when it comes to closing alerts. While many alerts classified as “Benign” can automatically be resolved (freeing up immense analyst capacity!), we don’t do it blindly. Here’s why some benign alerts will still get a human touch:
- Continuous quality control: A random subset of these benign alerts is still routed to analysts for quality assurance. This helps us continuously monitor and refine the Enhanced Response model’s accuracy.
- The unshakable safety net: We’ve implemented powerful protective guardrails for certain alerts to always be reviewed. If an alert—even if classified as benign by the model—meets certain predefined critical conditions, these rules override the auto-close. This ensures that an analyst always reviews alerts where the potential impact is too high to leave to automation alone, effectively minimizing risk.
By embedding this intelligent classification and automated response directly into our workflow, we’re not just filtering alerts; we’re fundamentally changing our operational rhythm. We’re empowering our analysts to focus their expertise where it’s most impactful, move faster on real threats, and bring a new level of clarity and efficiency to the once-murky waters of identity security.
The benefit of Expel: Years of insight & continuous refinement
The AI-driven approach to handling identity alerts is one of the battle-tested cornerstones of our SOC that’s been delivering value and continues to evolve. Having integrated this intelligent system into our daily workflows, we’ve moved beyond initial implementation into a phase of persistent, data-driven enhancement. This isn’t just about having a smart tool; it’s about embedding a culture of continuous improvement at the heart of our identity threat detection and response.
This system isn’t just running; it’s learning. Years of operational insight now power its precision, turning raw data into sharper algorithms. The result? Less analyst fatigue, faster triage, and amplified efficiency—a standard we continually push higher.
“Measure, monitor, improve” isn’t just a motto; it’s our SOC’s heartbeat. We obsessively track performance, dissect alert trends, and pit our model against the newest threats. This vigilance keeps us adaptive, ensuring our defenses don’t just react, but anticipate.
A vital component of this long-term refinement strategy is the deep, ongoing collaboration between our AI and our SOC analysts. The process of comparing the model’s classifications with our analysts’ expert findings has been active from the outset and continues to be a rich source of learning. Every piece of feedback, every reclassification, every nuanced judgment from our team is fed back into the system. This iterative loop—active since the system’s inception—has been instrumental in honing the AI’s accuracy and its alignment with the complex realities our analysts face daily. It ensures our automated capabilities grow more sophisticated and reliable with each alert.
Our commitment is unwavering. The successes and efficiencies we’ve achieved with our AI-enhanced identity alert processing are a foundation upon which we continue to build. We’re dedicated to this path of relentless improvement, ensuring our defenses remain formidable and our analysts are empowered with the most intelligent tools available, now and into the future.
Interested in learning more about how our SOC functions? Here’s more info.