MDR · 3 MIN READ · GRANT OVIATT · FEB 8, 2018 · TAGS: tech stack
by Grant Oviatt, Ben Brigida, Jon Hencinski
We think it’s important for your managed security service provider’s (MSSP) interests to align with yours.
Unfortunately, that’s not always the case. It’s easy to fall into the trap (that many MSSPs do) of measuring their value by just pointing to the number of alerts they review and incident reports they produce.
But what if threats don’t show up on any given Tuesday? Well, among other things, it can shine a spotlight on how misaligned your interests can become… and it can lead to a discussion that goes something like this:
Customer: I’m not getting (m)any alerts. What am I paying you for?
MSSP: Hold on a sec. [turns knob to send more low-priority alerts to customer]. Are you getting more alerts now?
Customer: Ummm… yeah.
Do you really want to get more alerts and more incidents if you aren’t more compromised (if that sounds familiar check out our post on 5 warning signs your MSSP isn’t the right fit)?
We don’t think a managed security provider should be off the hook for delivering value just because things are quiet. Finding bad things is critical. But in our view, detection is only half of the equation. We think a managed security service should make your security better, not busier.
And getting better means preventing bad things from happening again (and again) or impacting you in the first place. To do that, you need two things:
- First, you need a way to identify the root causes of incidents and assess risk (beyond the occasional red team exercise)
- Second, you need the data to make the case for change (even to people who don’t speak security)
That’s why we created resilience.
What is resilience?
Resilience is our way of making you better even when there aren’t any security incidents.
At its core, resilience is comprised of recommendations that describe:
- A specific security risk
- The potential impact, and
- The steps to mitigate it
Resilience recommendations do one of two things – disrupt attackers or enable defenders. Recommendations that disrupt attackers prevent threats from successfully performing their intended goal, while recommendations that enable defenders allow your team (including us) to respond more effectively when they do. Resilience recommendations cover a broad spectrum of security content from Windows settings that reduce the exposure of plain text credentials in-memory to specific configurations for getting the most out of your firewall or endpoint detection and response (EDR) solution.
Resilience in action
So now you’ve heard a little bit about what resilience is… let’s talk about how it works.
Step 1. Find the root cause and identify how to improve
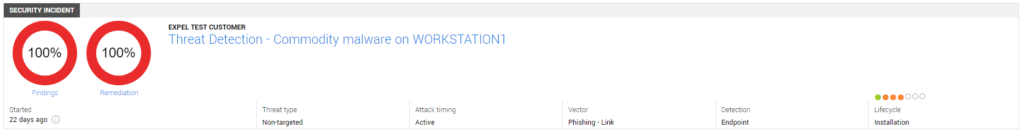
Let’s say Expel detects commodity malware on a host in your environment. We’d validate the event, and notify you.
That’s where most MSSPs would stop.
But we’ll investigate that activity using your technology to understand how the host was infected and provide remediation steps to remove the problem at hand. In the example above, it turns out the host was compromised when a user downloaded and opened an MS Word document with an embedded macro from a phishing email link.
This is where most managed detection and response (MDR) providers would stop.
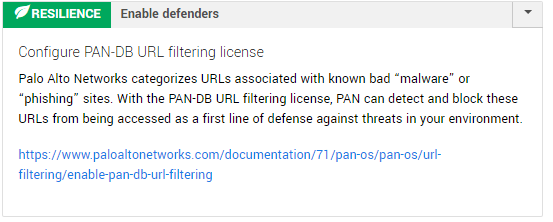
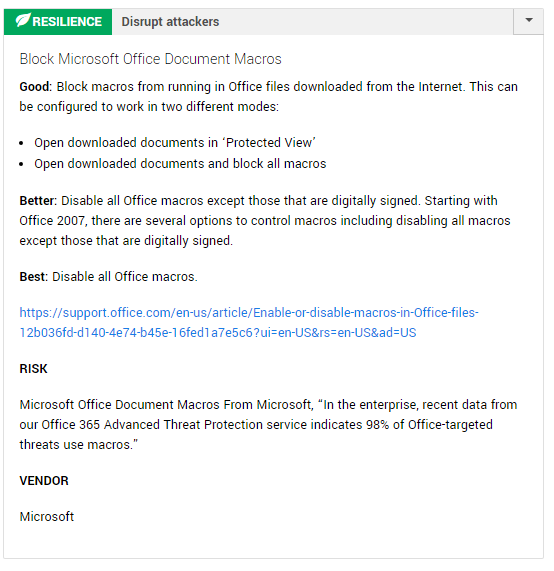
It’s also where resilience kicks in to tell you how this incident could have been prevented altogether. In this case, we found the attack would’ve been disrupted if macros were blocked in MS Office files downloaded from the Internet. We also noticed that your defenders could have responded faster if the Palo Alto Networks firewalls had a URL filtering license. The additional license would have allowed us to detect or block maliciously categorized URLs like the phishing link (who says that identifying risk has to be just a pentesting thing?).
Where things become more interesting is when you start to tie a bunch of incidents to the same resilience recommendation. Now you can start building a fact-based case for doing something about it – as long as you’re armed with the right data.
Step 2: Arm yourself with data
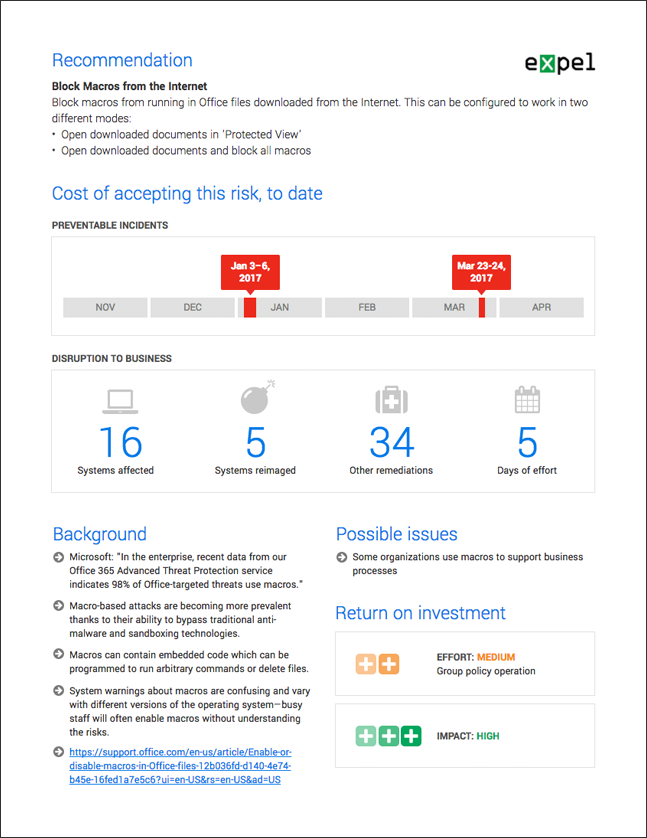
It probably isn’t news to you that blocking MS Office macros is a good idea. We know how hard it can be to implement changes like this in your environment – especially when there are other business units involved in the decision (talking about you IT). Making the case to get it done is half the battle. To help with that we give you a “tear sheet” for each resilience recommendation. It contains data from your environment and anonymized data from other customers that shows the cost (and risk) of doing nothing about a recommendation. How many of your systems have been impacted? How much time has been spent fixing problems that could have been prevented by addressing the root cause? How have others fared when implementing this recommendation?
Conclusion / Executables
So that’s a quick overview of how we approach resilience here at Expel. Call us crazy but we just don’t think that being compromised should be a prerequisite for getting value out of your MSSP.
That said, you don’t need Expel to put resilience into practice. Here are a couple resilience recommendations our customers have implemented recently to start you off on the path towards security improvement.
- Resilience example #1: Disrupt attackers
Mitigate Microsoft Group Policy Preferences (GPP) vulnerability
- Resilience example #2: Enable defenders
Configure Palo Alto Networks Firewalls to block or alert on C2 URL traffic