Table of Contents
In simple terms, a SOC is a centralized team where security professionals monitor, detect, analyze, and respond to cybersecurity threats around the clock. Think of a SOC like a 24×7 emergency response center for your digital infrastructure—it’s where your security team keeps constant watch over your organization’s technology environment, ready to jump into action the moment something suspicious appears. Whether the SOC exists as a physical space, a virtual team, or a combination of both, its mission remains constant: protecting your organization’s assets, data, and systems from cyber threats that never sleep.
Modern organizations face an increasingly complex threat landscape. Cyberattacks can happen at any moment, targeting everything from intellectual property and customer data to business-critical systems and brand reputation. A SOC combines skilled security personnel with advanced technology tools to provide continuous monitoring, rapid threat detection, and coordinated incident response—eliminating security silos and creating a unified defense strategy.
What does a SOC team actually do?
A security operations center functions as your organization’s central hub for all cybersecurity activities. The team’s responsibilities extend far beyond simply watching monitors and waiting for alerts to appear.
Continuous monitoring and threat detection
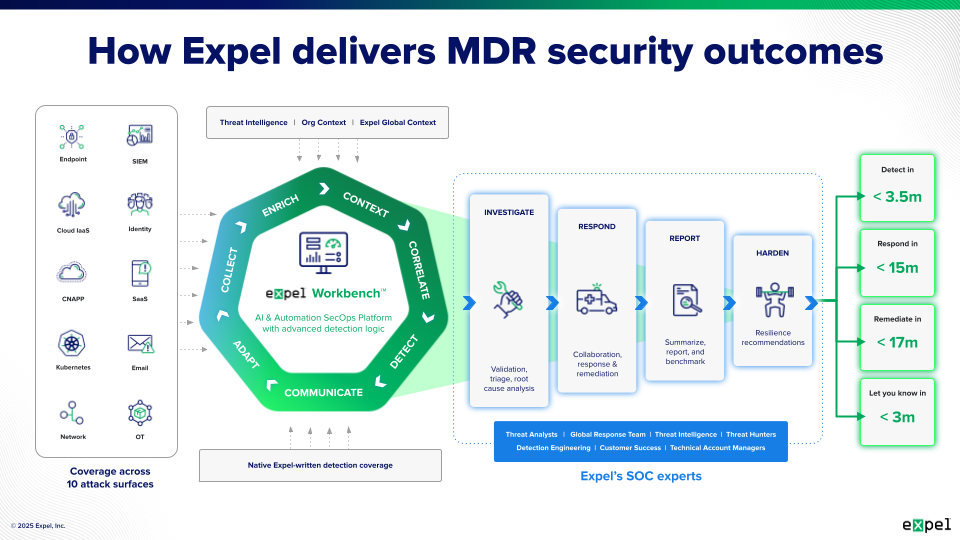
At the heart of every SOC operation is continuous monitoring across your entire technology environment. Security analysts track activity from endpoints, networks, cloud platforms, applications, and user accounts—gathering massive amounts of data every second. According to Expel, a typical SOC processes millions of events daily, filtering them down to hundreds of alerts that require human judgment, with about 33 requiring deeper investigation and resulting in 2-3 actual security incidents.
The monitoring function relies on various security technologies including endpoint detection and response (EDR), security information and event management (SIEM) platforms, extended detection and response (XDR) systems, and cloud security tools. These systems generate visibility data from every corner of your infrastructure—because attack vectors can form anywhere.
Alert triage and investigation
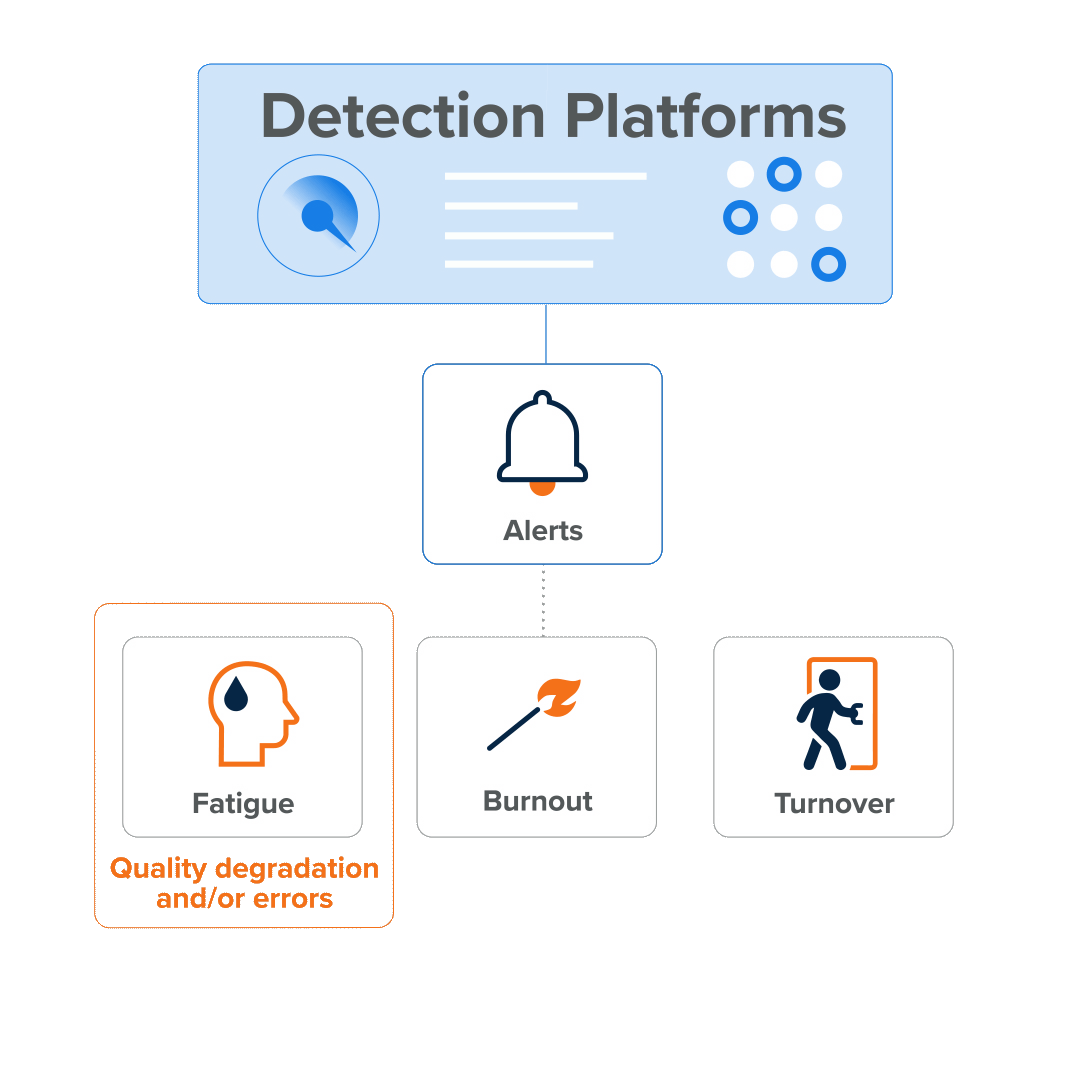
Not every alert represents a genuine threat. In fact, one of the biggest challenges SOCs face is alert fatigue—being overwhelmed by false positives and low-priority notifications. The SOC team’s job is to determine which alerts actually matter by correlating data from multiple sources and applying their security expertise.
Most security products aren’t good storytellers—they generate alerts but don’t explain what’s really happening. A correctly staffed SOC has the right people to investigate critical alerts and construct a complete narrative about what occurred, why it happened, and what it means for your organization.
Incident response and threat mitigation
When the SOC identifies a genuine security threat, rapid response becomes critical. Seconds count when preventing a threat from escalating into a full-blown attack. The SOC team follows established incident response procedures to contain threats, eliminate malicious activity, and minimize damage to your organization.
This includes actions like isolating compromised systems, blocking malicious network traffic, disabling compromised user accounts, removing malware, and patching vulnerabilities. The team documents everything they do, creating detailed records of the incident timeline, response actions taken, and lessons learned for future prevention.
Threat hunting and proactive defense
Beyond responding to alerts, advanced SOC teams engage in proactive threat hunting—actively searching for hidden threats that may have evaded automated detection. This involves analyzing patterns in your environment, investigating suspicious but not obviously malicious activity, and staying ahead of emerging attack techniques.
Strategic security guidance
The best SOCs don’t just react to threats—they help strengthen your overall security posture. SOC teams should continually offer strategic guidance and support, helping organizations understand how to fix the root causes of recurring incidents and implement security improvements that reduce future risk.
What are the core functions of a SOC?
While specific responsibilities may vary by organization, every effective security operations center performs several essential functions:
Detection: Turning data into insights
Detection is the process of converting massive volumes of raw visibility data into usable security insights. Automated analysis helps generate initial findings, but skilled security analysts must apply their knowledge and experience to distinguish genuine threats from false alarms and understand the full context of suspicious activity.
Modern SOCs leverage advanced detection capabilities including:
- Behavioral analytics that identify anomalous user and system activity
- Threat intelligence integration that recognizes known malicious indicators
- Machine learning models that detect unusual patterns
- Correlation engines that connect related events across different systems
Analysis: Understanding the full picture
Once potential threats are detected, SOC analysts dig deeper to understand exactly what’s happening. This investigative work requires combining technical skills, security knowledge, and critical thinking. Analysts examine log data, review system activity, research threat actor techniques, and piece together the complete story of an incident.
Response: Taking swift action
Effective response separates capable SOCs from overwhelmed security teams. Response functions include immediate threat containment, malware removal, system remediation, evidence preservation for forensic analysis, and communication with stakeholders about security incidents.
Research shows that industry-leading SOCs can achieve mean time to respond (MTTR) of under 20 minutes—dramatically faster than the industry average. This speed prevents attackers from accomplishing their objectives and minimizes the potential impact of security breaches.
Orchestration: Streamlining workflows
Orchestration involves automating and streamlining investigation and remediation workflows. If your security practitioners are doing real security work rather than just pushing buttons and keeping technology running, they’re likely using orchestration capabilities. Expel’s approach includes an orchestration bot called Ruxie that runs thousands of investigative actions on behalf of analysts, makes triage decisions, and handles about a third of all daily investigations.
Continuous improvement: Learning and adapting
Security threats constantly evolve, so SOC operations must continuously improve. This means tracking key metrics like mean time to detect (MTTD) and mean time to respond (MTTR), analyzing incident patterns to identify systemic vulnerabilities, staying current on emerging threats and attack techniques, and refining detection rules and response playbooks based on lessons learned.
Who works in a security operations center?
A fully-staffed security operations center includes multiple specialized roles, each bringing unique skills and expertise to the team.
SOC analysts form the operational core of the security team. Organizations typically structure analyst roles in tiers:
Tier 1 analysts handle initial alert triage, monitor security dashboards, perform basic investigation tasks, and escalate suspicious activity to more senior analysts. They’re often the first line of defense and need strong attention to detail.
Tier 2 analysts conduct deeper investigations, perform advanced threat analysis, respond to confirmed security incidents, and develop detection rules. They have more experience and can handle complex security scenarios independently.
Tier 3 analysts serve as expert-level incident responders, lead major incident investigations, conduct advanced threat hunting, and mentor junior analysts. They’re seasoned security professionals with deep technical expertise.
SOC manager: The SOC manager oversees daily operations, manages team schedules and workload distribution, tracks performance metrics, coordinates with other IT and security teams, and ensures the SOC meets its service level objectives. They balance operational efficiency with team wellbeing.
Security engineers: Security engineers focus on the technology infrastructure that enables SOC operations. They implement and configure security tools, integrate new data sources, develop automation scripts, optimize detection rules, and maintain the technical platform that analysts depend on.
Threat intelligence analysts: These specialists track emerging threats and attacker tactics, analyze threat actor behavior and campaigns, provide context about new vulnerabilities and exploits, and help the SOC prioritize threats based on relevance to your organization.
Incident response specialists: When major security incidents occur, specialized incident responders lead the response effort—coordinating containment and recovery actions, conducting forensic analysis, communicating with executive leadership and affected parties, and developing remediation plans.
The talent challenge
As Expel highlights, SOC teams struggle with significant challenges including alert fatigue from overwhelming numbers of false positives, talent shortages in the cybersecurity industry, constant pressure from the 24×7 nature of security operations, and lack of time for more impactful strategic work. Meanwhile, security leaders wrestle with hiring, training, and retaining qualified talent—creating resource constraints that many organizations struggle to overcome.
What problems does a SOC solve?
Organizations invest in security operations centers to address critical business and security challenges:
Round-the-clock threat protection: Cyber attackers don’t work 9-to-5 schedules, and neither can your security defenses. Maintaining security against attacks isn’t a 9-to-5 gig—it’s a complex task that demands round-the-clock attention. A SOC provides 24x7x365 monitoring and response capability, ensuring someone is always watching for threats regardless of when attacks occur.
Reducing dwell time: Dwell time—the period between when attackers first compromise your environment and when you detect them—represents pure opportunity for adversaries. The longer threats go undetected, the more damage they can cause. A well-functioning SOC dramatically reduces dwell time by detecting threats quickly and responding immediately.
Managing security tool complexity: Modern organizations deploy multiple security technologies—firewalls, endpoint protection, email security, cloud security tools, network monitoring systems, and more. Without a SOC to centralize management and correlation, these tools operate in silos, generating disconnected alerts that overwhelm security teams. A SOC combines the right security personnel with the right security tools, eliminating security silos and increasing operational efficiency.
Addressing the cybersecurity skills gap: The cybersecurity industry faces a severe talent shortage—there simply aren’t enough qualified security professionals to meet demand. Building and maintaining an effective in-house SOC requires hiring multiple specialized roles, which can cost organizations well over a million dollars annually. Many organizations facing these challenges see value in managed SOC services that provide the required levels of expertise, readiness, and service.
Providing actionable intelligence: Security tools generate massive amounts of data, but data alone doesn’t protect organizations—you need intelligence. Most security products aren’t good storytellers. A SOC transforms raw data into actionable intelligence, providing clear answers about what happened, why it matters, and what to do about it.
Supporting compliance requirements: Many regulatory frameworks and industry standards mandate specific security monitoring and incident response capabilities. A documented SOC operation helps organizations demonstrate compliance with requirements like PCI DSS, HIPAA, SOC 2, and others by providing evidence of continuous monitoring, incident handling procedures, and security controls.
Is a SOC the same as a NOC?
No—while the acronyms sound similar, a security operations center (SOC) and a network operations center (NOC) serve fundamentally different purposes, though they may work closely together.
A NOC monitors IT infrastructure to ensure systems remain available and perform optimally. NOC teams track network uptime, bandwidth utilization, server performance, application availability, and hardware health. When systems go down or performance degrades, the NOC works to restore normal operations. Their primary concern is keeping technology running smoothly for users.
In contrast, a SOC focuses specifically on identifying and responding to security threats. SOC teams monitor for signs of malicious activity, investigate suspicious behavior, contain security incidents, and work to prevent breaches. Their primary concern is protecting the organization from cyber threats.
So where do they overlap?
In some organizations, SOC and NOC functions complement each other closely. A NOC might detect unusual network traffic patterns and alert the SOC to investigate whether it’s malicious. Similarly, when the SOC responds to a security incident that requires taking systems offline, they coordinate with the NOC to minimize operational disruption.
Some organizations operate integrated SOC/NOC environments where teams share physical space and communication channels, though their responsibilities remain distinct. Smaller organizations might have a single team handling both functions, though this approach can dilute focus and expertise.
Choosing the right SOC approach for your organization
Organizations have several options for establishing SOC capabilities.
In-house SOC: Building an internal SOC gives you complete control and customization but requires significant investment in personnel, technology, and facilities. This approach works best for large enterprises with substantial security budgets and the ability to attract and retain top security talent.
Managed SOC services (SOCaaS): For organizations that lack the time, staff, or budget to operate an in-house SOC, managed SOC services provide cybersecurity protection without the overhead. Managed SOC providers deliver the capabilities of a modern security operations center without the cost and complexity of building one yourself.
Hybrid models: Many organizations adopt hybrid approaches, maintaining some internal security capabilities while outsourcing specific functions to managed service providers. This allows organizations to leverage external expertise while building internal security knowledge.
The ideal SOC maintains a deep collaborative relationship with the organization’s internal security team, functioning as a true partner rather than just a vendor providing services.
The bottom line
A security operations center represents your organization’s dedicated defense against cyber threats. By combining skilled security professionals, advanced technology tools, and well-defined processes, a SOC provides the continuous 24×7 monitoring, rapid detection, and coordinated response capabilities that modern organizations need to protect their digital assets.
Whether you build an in-house SOC, partner with a managed security service provider, or adopt a hybrid approach, the goal remains the same: detecting and stopping threats before they can cause significant damage to your organization. In today’s threat landscape, having a well-functioning SOC isn’t just a technical consideration—it’s a business imperative.
FAQs
- How much does it cost to build a security operations center? Building an in-house SOC typically costs over $1 million annually when factoring in analyst salaries, security tools, 24×7 shift coverage, training, and facility costs. Managed SOC services offer more predictable costs through subscription pricing.
- What’s the difference between a SOC and cybersecurity? Cybersecurity is the broad practice of protecting systems and data from threats, while a SOC is the specific team, facility, and operational framework that implements cybersecurity monitoring, detection, and response on a continuous basis.
- How many people work in a typical SOC? SOC team sizes vary widely based on organization needs. Small SOCs may have 5-10 analysts, while enterprise SOCs can employ 50+ security professionals across multiple tiers and specialized roles to provide 24×7 coverage.
- What tools does a SOC use? Common SOC tools include SIEM platforms, endpoint detection and response (EDR), extended detection and response (XDR), security orchestration and automated response (SOAR), threat intelligence platforms, and network monitoring systems.
- Can small businesses afford a SOC? While building an in-house SOC is often cost-prohibitive for small businesses, managed SOC services (SOCaaS) provide affordable access to enterprise-grade security operations through flexible subscription models scaled to smaller organizations.