Current events · 5 MIN READ · TYLER FORNES AND BRITTON MANAHAN · SEP 16, 2021 · TAGS: Guidance / tech stack / threat landscape
We’re often asked about the biggest threats we see across the incidents we investigate for our customers. Where should security teams focus their efforts and budgets? To answer these questions, we’re sharing monthly reports on the top attack vectors, trends, and resilience recommendations identified by our Security Operations Center (SOC). Our goal is to translate the security events we’re detecting into security strategy for your org.
For this report, our SOC analyzed the incidents we investigated in August 2021 to determine the top attack vectors used by bad actors. A sneak peek at what’s ahead:
- What to do about business email compromise (BEC)
- The rise in exploited public-facing vulnerabilities and our #1 resilience recommendation
- How credential-stealing malware is targeting crypto wallets
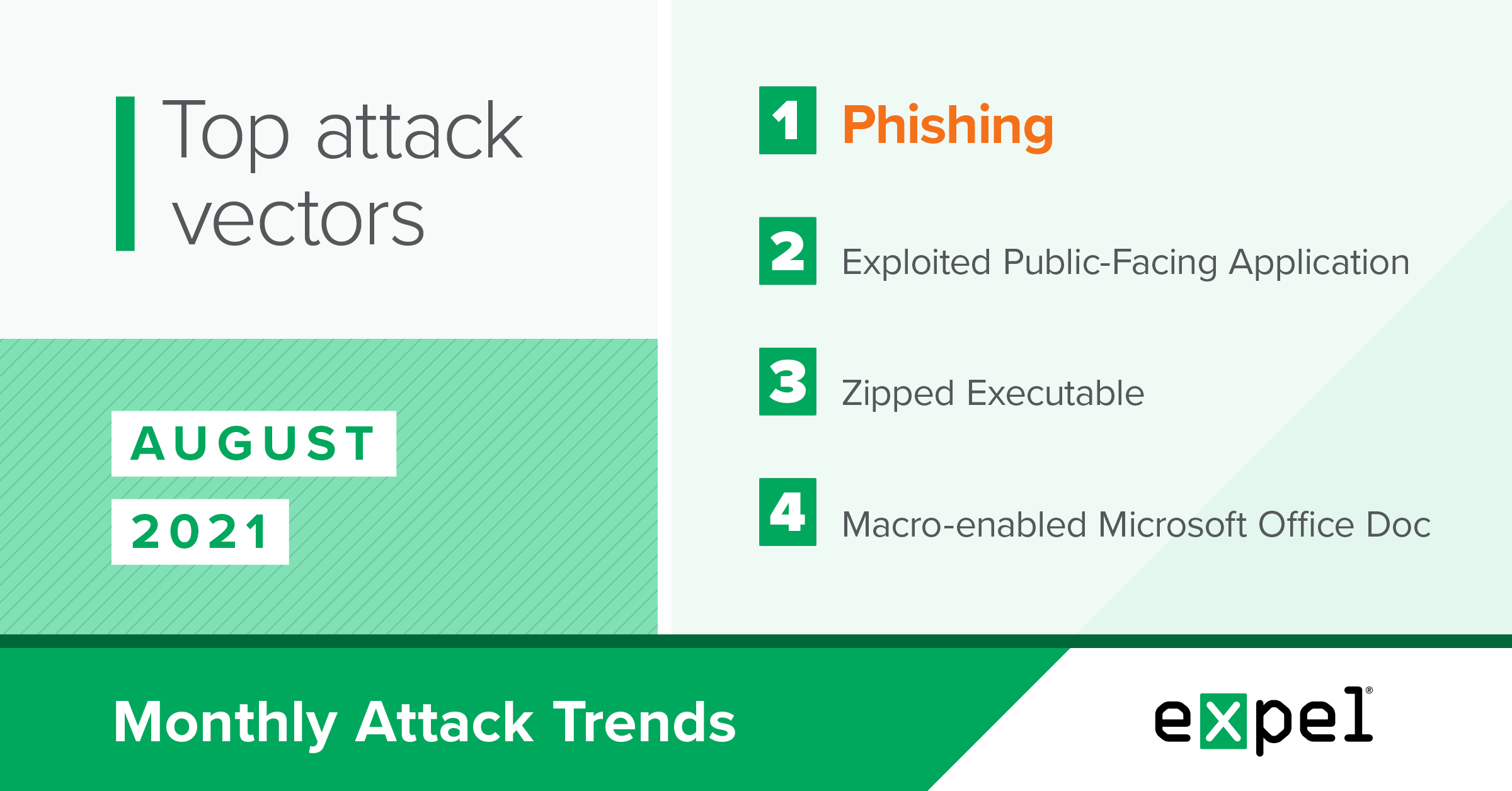
Business email compromise (BEC)
TL;DR: BEC continues to top the charts. Azure AD Identity Protection helps.
It’s no surprise to us that in August 2021, 63 percent of incidents our SOC handled were the result of a business email compromise. BEC continues to be the number one attack vector across our customers.
However, BEC is different from a standard phishing attack. What we’re looking for in these cases is an attacker abusing a stolen credential (previously phished from a user) and using it to access that user’s inbox – giving them access to sensitive information. Chaos ensues, and we’ve witnessed everything from mass mail spam to fraudulent wire transfers happen next.
Wondering how to get better at identifying BEC?
In August, 61 percent of all BEC we responded to was identified by Azure AD Identity Protection. This is no surprise – last month, we noted that 53 percent of BEC incidents we identified were targeted against Microsoft O365. We can safely assume that Microsoft accounts will remain a prime target for attackers heading into the later months of 2021.
But if you’re an org struggling with BEC and looking for a solution, Azure AD Identity Protection can provide help.
What do we like about it? Its ability to identify anomalous logins based on tracking a user’s login behavior.
Azure AD Identity Protection generates profiles based on this information, then provides dynamic alerting that can be adjusted based on a user’s travel and location history. When a user logs in from two improbable places at once (i.e. the U.S and West Africa), you get an alert. We refer to this as Geo infeasibility at Expel, and it’s the number one way we catch bad actors in inboxes.
That being said, a single product won’t solve all your woes here. But the stats speak for themselves. Azure AD Identity Protection is a powerful tool for catching BEC.
We’d bet our paychecks that BEC will continue to top the charts of attack vectors for the rest of 2021 and into 2022. If you haven’t reviewed your defenses recently, here’s your monthly reminder to enable multi-factor authentication (MFA) and disable IMAP and POP3.
Resilience recommendations:
- You know we’re going to say it, but MFA everything and everywhere.
- Conditional access policies are a great way to help mitigate Geo infeasibility.
- Disable legacy protocols like IMAP and POP3 (these don’t enforce MFA).
- Consider Azure AD Identity Protection to help identify suspicious mailbox logins.
Public-Facing Vulnerabilities
TL;DR: Opportunistic attackers are taking advantage of vulnerable web applications more than ever.
Incidents involving the exploitation of public-facing web applications rose 400 percent from July 2021. Overall, 55 percent of our critical incidents in August 2021 were found to be the result of an exploited application running on a public-facing web server.
Why?
We’re finding that most of these attacks are opportunistic, looking to deploy ransomware, coin miners and webshells. In most cases, the scripted delivery of these exploits is the result of internet-wide scanning and allows an opportunistic attacker to broaden their attack surface and proliferate their payload of choice in as many orgs as possible.
Once exploited, we notice the early signs of these attacks through detections that monitor a web-working process (such as IIS or Apache) spawning a command shell (cmd/bash/PowerShell). In these relationships, we‘re looking for a command shell that’s downloading a second stage payload or performing unusual reconnaissance actions that may indicate the presence of a webshell.
Below is a summary of the top web application vulnerabilities we’ve seen exploited across our customer base. One key takeaway: more than half of the vulnerabilities we’ve seen exploited are over two years old.
| CVE-2019-2725 | Oracle WebLogic Server |
| CVE-2019-18935 | Telerik UI for ASP.NET AJAX |
| CVE-2018-7669 | Sitecore CMS |
| CVE-2017-10271 | Oracle WebLogic Server |
| CVE-2021-26084 | Confluence Server |
From our security team to yours –— identifying and patching border-facing assets should be number one on your to-do list. If you aren’t sure where to start, a few quick queries on Shodan can save you a lot of heartbreak by helping to understand what applications are exposed (and potentially vulnerable) at the border of your network. Here’s a simple one to get you started:
net:1.2.3.4/24 (where 1.2.3.4 is your network range in CIDR notation)
Resilience recommendations:
- Deploy an Endpoint Defense and Response (EDR) tool on web servers.
- Scan and identify public-facing assets using Shodan.
- Ensure public web applications are patched to their latest version.
- Deploy a Web Application Firewall (WAF).
Credential Stealers
TL;DR: Attackers are hungrier than ever for crypto. Keep your wallets safe!
Commodity malware is riddled with credential stealers, and we see a lot of them. In fact, we noticed that 15 percent of incidents we identified in August included the deployment of credential stealing malware by an attacker — a 114 percent increase from July 2021.
We noticed several samples of the REDLINE malware being deployed throughout our customer base. In all cases, REDLINE was delivered through a zipped executable to the user, likely through a phishing email. These campaigns rely on the “double click and let it rip” principle, where user interaction is required to kick off the infection. We talked at length about this in July’s report, and firmly expect the trend of threat actors favoring user execution to continue.
We dug through several samples of REDLINE during August 2021 and had a few surprising findings.
First, what’s old is new again — all samples of REDLINE that we analyzed used the Nullsoft Scriptable Install System to kick off the malware installation. A blast from the past, but a solid way of presenting a familiar and user-friendly interface for installing “software.”
Second, as August progressed and we observed additional REDLINE samples, we noticed that the malware started to heavily target cryptocurrency wallets resident on the infected machines. It became obvious that as trends in cryptocurrency favored certain coins, REDLINE developers were quick to add wallets of high value.
This is a good reminder that credential stealers are highly configurable and also often target stored credentials in browsers, financial services and other legitimate software. As 2021 beats on, it’s more important than ever to talk to your users about trusted software and identifying suspicious applications.
Nine times out of ten, if someone emails you a zip file and asks you to install a piece of software, it’s likely bad.
Resilience recommendations:
- We know it’s a tall order, but spend some time educating your users about trusted software and identifying suspicious applications.
- Consider implementing an application safelisting tool (like Windows Defender Application Control) to help defend against malicious software installation.
- Consider implementing/tuning your email gateway to inspect zipped attachments that include executables, or encrypted zip files.
Takeaways
August continued to prove that BEC isn’t going away anytime soon. You know our top recommendation — MFA, MFA, MFA. But also take a look at how Azure AD Identity Protection may be able to help your org clamp down on BEC attempts through Geo infeasibility notifications.
Also check out our phishing recommendations in last month’s report to keep bad actors from accessing credentials in the first place.
Next: exploitation of vulnerabilities in public-facing web apps is on the rise.
Number one on the to-do list is to identify and patch border-facing assets — Shodan is a great tool to help identify exposure. Then consider taking some of the additional resilience actions we’ve discussed, like deploying an EDR tool and a Web Application Firewall (WAF).
Lastly, user execution will remain bad actors’ preferred method of infection. So ramp up user education on trusted software and identifying suspicious applications to keep malicious zipped attachments from impacting your org. Also watch out for users’ crypto wallets as malware adapts to target new trends in cryptocurrency.
We’ll be back with insights on September’s top attack vectors. Have questions about this month’s data or what it means for your org? Drop us a note.