SOC · 4 MIN READ · BEN NAHORNEY, ISA JUDD AND HAFSAH MIJINYAWA · OCT 29, 2025 · TAGS: Phishing
TL;DR
- Our new Stories from the SOC series shares real-world attacks that our SOC analysts see and stop on a regular basis.
- We recently encountered a phishing attack at a prominent university that first appeared to target a faculty member.
- As our analysts investigated, we discovered the attack went much deeper, targeting more than 4,800 users across the campus.
Working in a SOC, we see some wild stuff. A SOC sits on the front lines of the threat landscape after all, and the folks filling those chairs are the first to see and respond to attacks. We often see new and novel techniques before anyone else, and are well positioned to identify attack technique trends. We know the difference between what happens in principle and practice better than anyone.
This is where Stories from the SOC comes in. This series showcases the types of attacks we see bad actors attempt, how we identify the attacks, and what we do to stop them.
Sometimes, these stories cover new and novel attack techniques not seen before on the threat landscape. Other times it’s about sharing something that we are seeing regularly, so you’re prepared to deal with it. Either way, our goal with these stories is to raise awareness around what’s currently happening in real-world attacks.
We recently saw an attack where a few account compromises lead to thousands of internal phishing emails. The interesting aspect of this attack is that the deeper we dug, the bigger it got. Let’s take a look at how this attack unfolded as the SOC was alerted to it.
From the SOC’s POV
We became aware of the attack when the vice president of a prestigious university clicked on a link in a phishing email. It claimed his Office 365 account was about to be terminated, and not wanting to interrupt business, you could forgive him for falling for it.
But that’s only the top layer of the attack. As we peeled back the layers, we uncovered a much larger attack was underway at the university.
The sender of the email was a student at the university. We discovered that earlier that day this student’s email account was compromised (we’ll call them Student 1).
The threat actor proceeded to send out a phishing email using Student 1’s account to 4,800 other users at the university with “TERMINATE OFFICE 365 ACCOUNT” as the email subject.
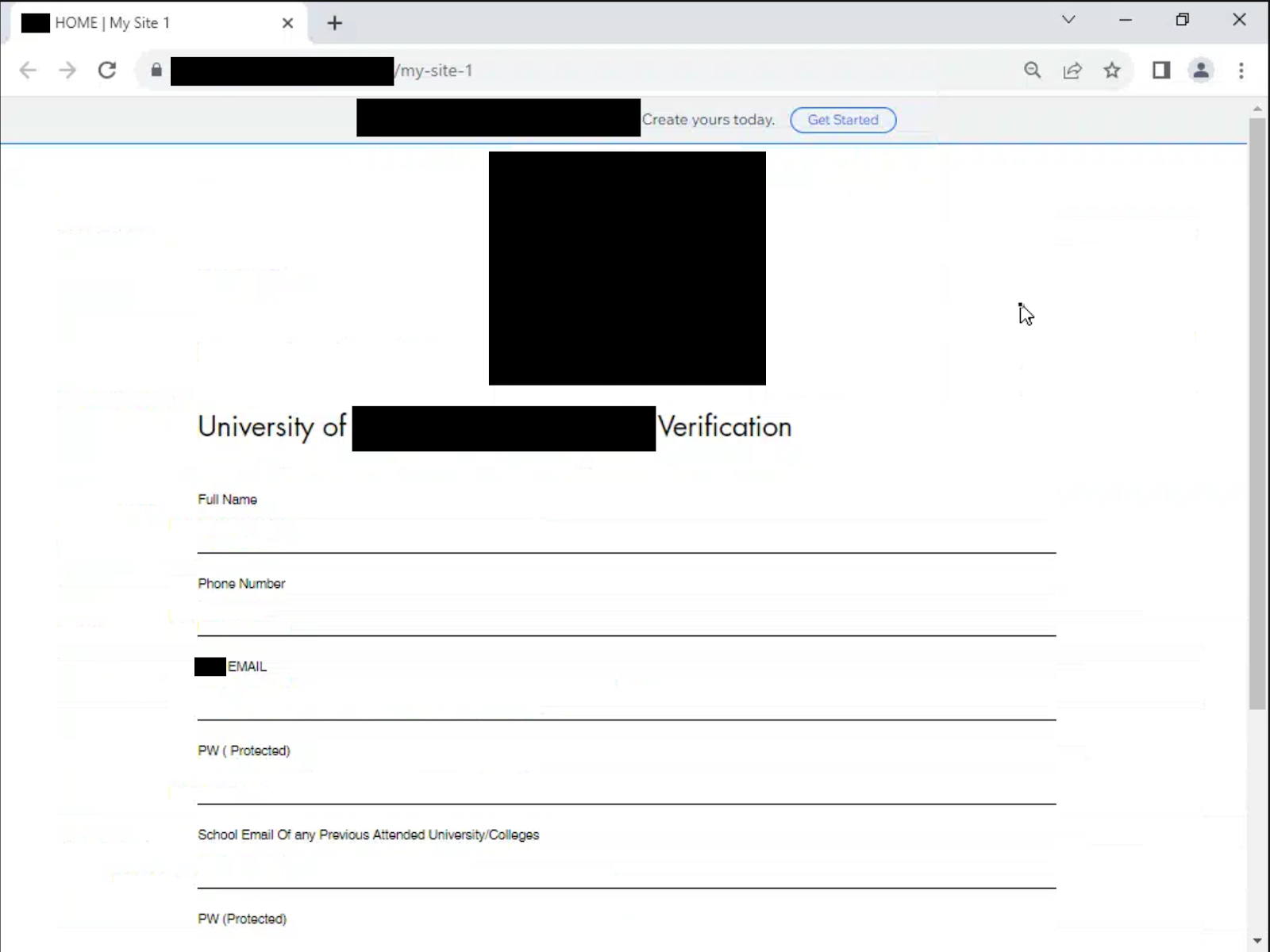
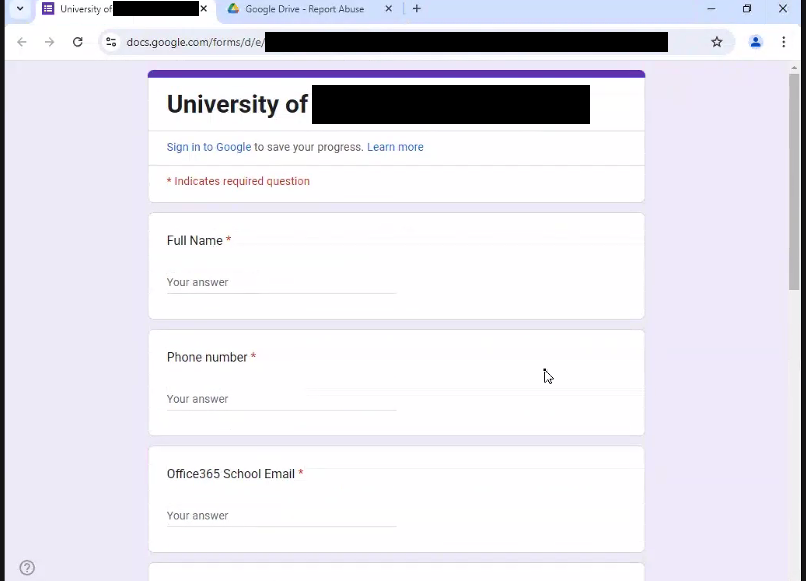
The phishing email urged users to fill out a form located at a link provided in the email. The lure claimed failure to do so would result in the termination of their university email accounts. The form requested personal information such as the target’s name, phone number, university email, passwords, and previous accounts.
All told, 40+ recipients of the email ended up clicking the phishing link.
But it turned out as we went further down the rabbit hole, we discovered that Student 1 wasn’t the beginning of this attack.
Following the breadcrumbs
We investigated logs for Student 1 to understand when and how they were compromised. We pinpointed the initial login by the threat actor, including a suspicious login from a specific IP address that occurred shortly before the phishing email was sent out.
This is where the detective work began. Our analysts took that IP address and pivoted their investigation across the entire university environment, expanding the IP address range to discover other logins to other university email accounts from this IP range.
One login stood out—that of another student email account that contained a suspicious inbox rule. It was configured to delete incoming emails related to the attacker activity, which is something threat actors often create to hide their tracks.
It turns out this index case, who we’ll call Student 0, sent out a phishing email that predated what Student 1 had sent. The subject line was the same, but this one pointed to a Google Form demanding similar personal information.
It looks like the threat actor used the account of Student 0 to test out their attack, then pivoted to Student 1 to send out mass phishing emails. Threat actors often do this to avoid detection and attempt to stay one step ahead of defenders.
How it happened in real time
Let’s look at this attack again chronologically to get a better sense of how the attack played out:
- The attacker compromised Student 0, then sent out an initial phishing email containing a link to Google Form requesting personal info.
- a. The attacker also set up an inbox rule to delete emails related to the phishing activity.
- Student 1 clicked the link, and we believe Student 1 shared their personal info.
- The attacker logged into Student 1’s account and sent out 4,800 phishing emails containing a link to another phishing site.
- The vice president received the phishing email and clicked the link, alerting us to the malicious activity.
What to do about it
Identity-based attacks are commonly seen in the SOC. According to Expel’s Quarterly Threat Report (Q2 2025), these attacks make up about two thirds of incidents that we see. Threat actors frequently create phishing campaigns urging users to take action immediately—preying on people’s instinct to respond quickly as they scroll through dozens of emails throughout their day. The stakes are high because it’s easy to make mistakes and not read thoroughly through emails when you’re under pressure.
To combat this attack, we prioritized blocking the threat actor’s access—temporarily disabling the accounts of anyone who interacted with the phishing email, and then resetting their credentials.
We recommended the university remove any phishing emails sent by the originally compromised student, as well as block access to the malicious domains we identified.
It’s also important to monitor for emails sent to thousands of students, checking for commonalities like subject lines, body text, and the sender’s address. While there may be legitimate reasons for sending emails to large groups of users, this ability should be limited to specific, trusted mailing lists or email addresses.
Additionally, monitor the locations where user accounts are being logged in from. For example, if a student has logged in from a location on campus, only to log in from another country shortly thereafter, this activity should raise an alert.
Why this matters
For security practitioners, this case demonstrates why correlation matters more than individual alerts. One click wasn’t the story—it was the breadcrumb that led to uncovering a multi-stage campaign. By pivoting from a single IP address and following the trail across the environment, our analysts were able to see the full scope of the attack and stop it before it could spread further.