MDR · 4 MIN READ · LEO SZALKOWSKI · NOV 14, 2024 · TAGS: SIEM / tech stack
Understanding the Cyber Kill Chain, the attack lifecycle, and where MDR and SIEM come in
TL;DR
- This is part two of a three-part blog series on how MDR can transform your SIEM investment
- Understand the Cyber Kill Chain, the attack lifecycle, and how MDR and SIEM play into each
- Where in the Cyber Kill Chain and attack lifecycle you should be taking action
This is part two of a three-part blog series: How MDR can transform your SIEM investment. You can find the full series here:
- Part I: understanding the difference between a security incident event management (SIEM) system and managed detection and response (MDR)
- Part II: the Cyber Kill Chain, the attack lifecycle, and where SIEM and MDR come in
- Part III: how Expel MDR can transform your SIEM investment and strategy
Now that we’ve covered the basics of MDR and SIEM tools in part one of this blog series, we’re ready to dive into where and why we apply SIEM versus MDR tools in the attack lifecycle. But before we can understand the where and why, we have to cover the what.
What is the attack lifecycle?
When we mention the attack lifecycle, at Expel, we’re referring to the Lockheed Martin Cyber Kill Chain, which identifies seven stages of an attack. These seven stages also align with the tactics and techniques of the MITRE ATT&CK Framework. Here’s an overview of the Kill Chain:
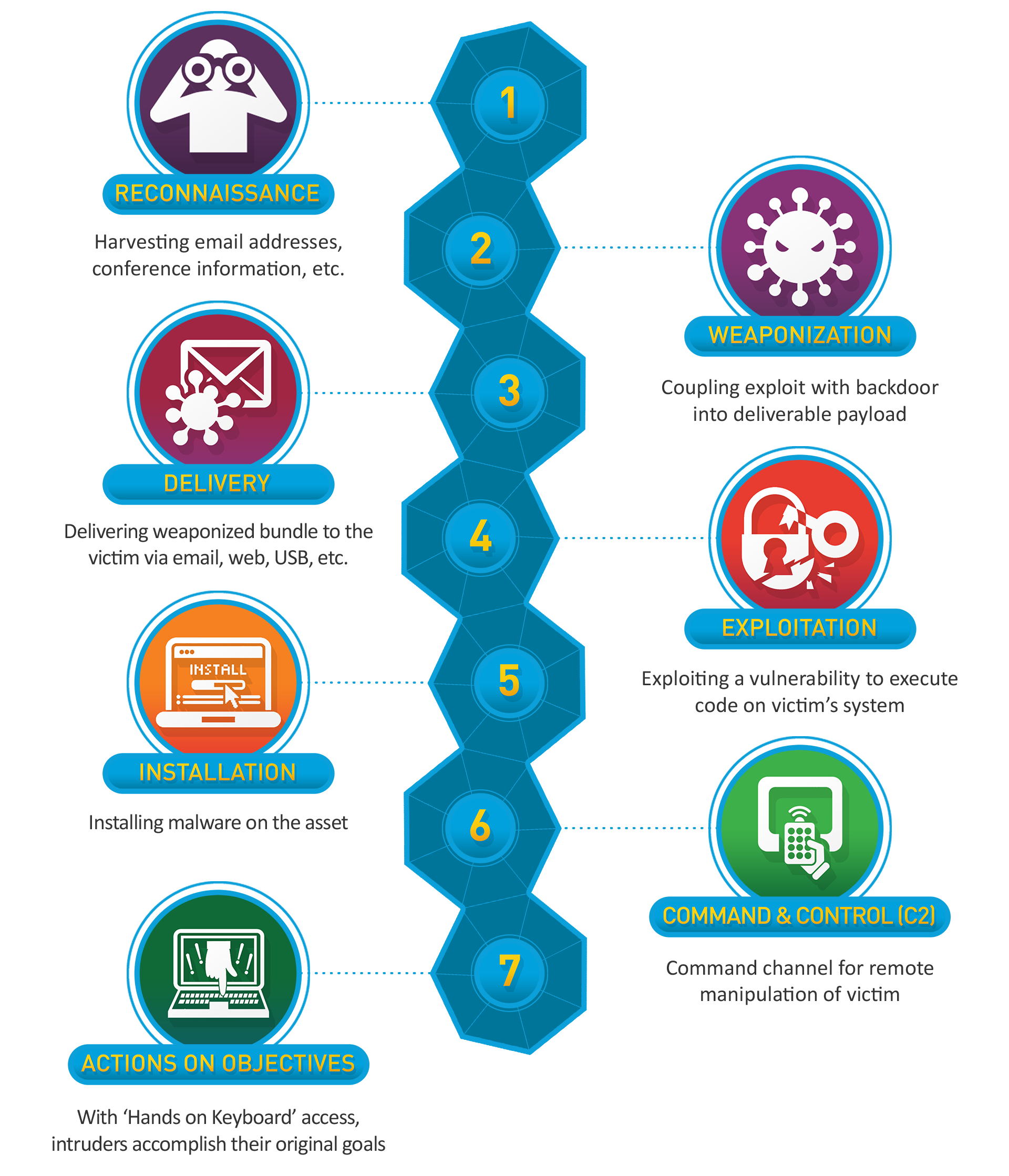
Where do we use SIEM in the attack lifecycle?
Unlike MDR, SIEM is less lifecycle-focused. At its core, a SIEM tool logs what’s happening within your environment, and can log actions at any step of the attack lifecycle as long as it’s programmed to do so.
Like other MDR providers, Expel surfaces SIEM alerts that focus on detecting post-exploitation activity. However, in addition to alerting, we’re able to leverage your SIEM tools to gather additional decision support using Ruxie’s (one of Expel’s bots) investigative actions. With the plethora of log sources SIEM tools typically include, that means we’re able to provide context on your environment from across the entire attack lifecycle.
Where is MDR focused?
Expel MDR leverages the MITRE ATT&CK Framework to categorize and prioritize its detections so our customers can focus on the most impactful threats, while we target detecting attacks that have the highest likelihood of representing active, post-compromise attacks. In general, we focus on post-exploitation activity, but this does vary slightly according to the signals we pull in from various parts of your tech stack, as shown in the diagram below.
Each tech category is looking for different types of alerts based on the highest risk type. This includes:
- Endpoint, which looks for exploitation of hosts. This includes services and other machines that run workload hosts in your environment.
- Cloud apps, which look for exploitation of user identity. This includes tools like Google Workspace, Microsoft 365, GitHub, and so on.
- Cloud, which looks for exploitation of administrative permissions. These alerts are often, Did you know this? alerts, also known as DUET alerts.
It’s critical to remember that SIEM and MDR are not mutually exclusive, but when used together they can help elevate an organization’s security posture. A SIEM tool can offer organizations a holistic and centralized view of their environment based on the telemetry it collects. However, this comes with a significant amount of overhead in terms of detection engineering, and responding to identified threats. MDR helps organizations by providing human expertise—rooted in defined frameworks and processes—to expand detection and response capabilities.
Why do we focus on specific areas of the Cyber Kill Chain?
So why do we focus on these specific alerts? Because our MDR detection strategy is intricately crafted to balance three key considerations:
- Where can a customer detect malicious activity? By leveraging extensive threat intelligence and behavioral analytics, Expel MDR ensures that customers are alerted to potential attacks at the earliest possible stage.
- Where does it make sense to respond to an activity? Not all detections warrant immediate response. Expel MDR utilizes risk-based prioritization to focus on the most critical threats, minimizing unnecessary alerts and allowing security teams to efficiently allocate their resources.
- What options do you have to respond to that activity? Expel MDR empowers customers with a range of response options, from automated containment measures to tailored incident response plans. This flexibility enables organizations to swiftly and effectively mitigate threats based on their specific security posture and risk tolerance.
By focusing on these considerations, we can take an endless sea of alerts and narrow them down to strategically focus on what is likely to carry the most risk. And just in case, we have the support of your SIEM tools to return to if we need to re-evaluate logs in other places to continue adapting to emerging threats.
Delivery
Focusing on delivery through the command and control areas of the Cyber Kill Chain provides detections with higher fidelity, meaning the alerts we focus on represent the area where malicious activity is more likely to appear. We don’t waste our efforts on lower fidelity areas, such as the pre-attack phase, where noise is more prevalent and observed risks haven’t matured into active threats.
For example, port scanning falls in the pre-attack phase. Port scanning happens constantly, and while it may represent risk, it hasn’t matured into an active threat that requires a response. Action you can take: If this type of activity is a concern for your org, there are improvements you can make to increase its fidelity. Instead of simply alerting on port scanning activity, look into correlating those events with events from other sources, like successful authentications and command executions (to name a couple), to produce an actionable lead that your SOC can drill into.
The delivery phase is where Expel starts our detection process. In delivery, we’re looking for antivirus alerts, blocked executions, and so on. These malware types may not be an issue, but this activity can mature into a threat.
Exploitation
The exploitation step is where we see malware being executed in the environment. This exploit can include activity like a script running out of context, or being run under an elevated, privileged account when it shouldn’t be. These leads are often, but not always, higher-fidelity signals and allow time to act, if needed. Expel looks for multiple sequential alerts to determine if there is a threat.
Because our detection strategy focuses on where the fidelity is higher and we have time to act, the alerts we send to you are the signal pulled from the noise in your environment. It’s also why your devices can send an alert that Expel notes as benign, and closes it.
Coming next: In part three of this blog series, we’ll explore more how Expel MDR works, and how our approaches can enhance your current SIEM capabilities to reduce gaps and increase resilience—improving your security strategy.







