Security operations · 3 MIN READ · MATT PETERS · APR 20, 2023 · TAGS: MDR
In ancient Greece there was a monster called a Lernean Hydra. It had nine heads and, if you cut one off, two more grew in its place. Between that, Sisyphus endlessly rolling a rock up a hill, and Prometheus chained to a rock perpetually being eaten by vultures, the ancient Greeks sure had a deep bench of unending torments. Fast forward to today. In 2014, NIST had to add a digit to the CVE format because the number of vulnerabilities discovered in a calendar year could no longer be counted with 4 digits. The number has only grown–there were over 26 thousand vulnerabilities reported in 2022! But we can’t just put our heads in the sand. According to a recent Forrester report, software vulnerabilities are the second-most reported attack vector. There has got to be something we can do.
Figuring out which vulnerabilities matter most is important, but hugely difficult. Static methods like the Common Vulnerability Scoring System (CVSS) don’t solve the whole problem because they don’t take into account dynamic factors impacting the likelihood of exploit–things like “is there a public version?” and “do we have a compensating control?” are all things you may need to consider. Even if you do something like “just patch the criticals,” the problem is still intractably huge–those increased by 59% in 2022.
You may also be challenged because your team may not fully own the vulnerability management process. Other stakeholders may include risk management, IT operations, or line of business–and there may be multiple teams within IT based on who “owns” the technology where the vulnerabilities exist. Because multiple teams share the vulnerability remediation process, it’s often difficult to coordinate the metrics and tracking of fixes. In some cases, organizations might not even get better security outcomes. For example, some organizations have goals around remediating a specific number or percentage of vulnerabilities, without qualifying whether those vulnerabilities pose an actual threat to the business.
Here we find ourselves–fighting a monster or chained to a rock–pick your favorite ancient Greek torment. We have to do something and, as a first step, we want to figure out how to prioritize better.
That’s why we’re now offering Expel Vulnerability Prioritization, our newest managed service that takes the burden off security teams by doing the triage and investigation of unresolved security issues for them–to identify the vulnerabilities that are putting customers at the highest level of risk.
If you’re using a Tenable or Rapid7 vulnerability management solution, then Expel Vulnerability Prioritization is for you. We take these solutions a step further, accelerating your remediation process by letting you know exactly which vulnerabilities detected pose the greatest risk. By connecting the dots between your Tenable or Rapid7 on-prem vulnerability data, and priority assets in your Expel Managed Detection and Response (MDR) environment, we assess your risk and the potential impact of your vulnerabilities against external threat intel and what attackers are actually exploiting in the wild. You get a prioritized list of vulnerabilities with recommendations on next steps for immediate action. This reduces the burden on your SecOps and IT teams with:
- Risk-based prioritization, by matching internal context for the risk with the degree of exploitability
- A dedicated team to investigate and provide guidance
- A clear assessment and prompt reporting of criticality and potential impact if the issue stays unresolved
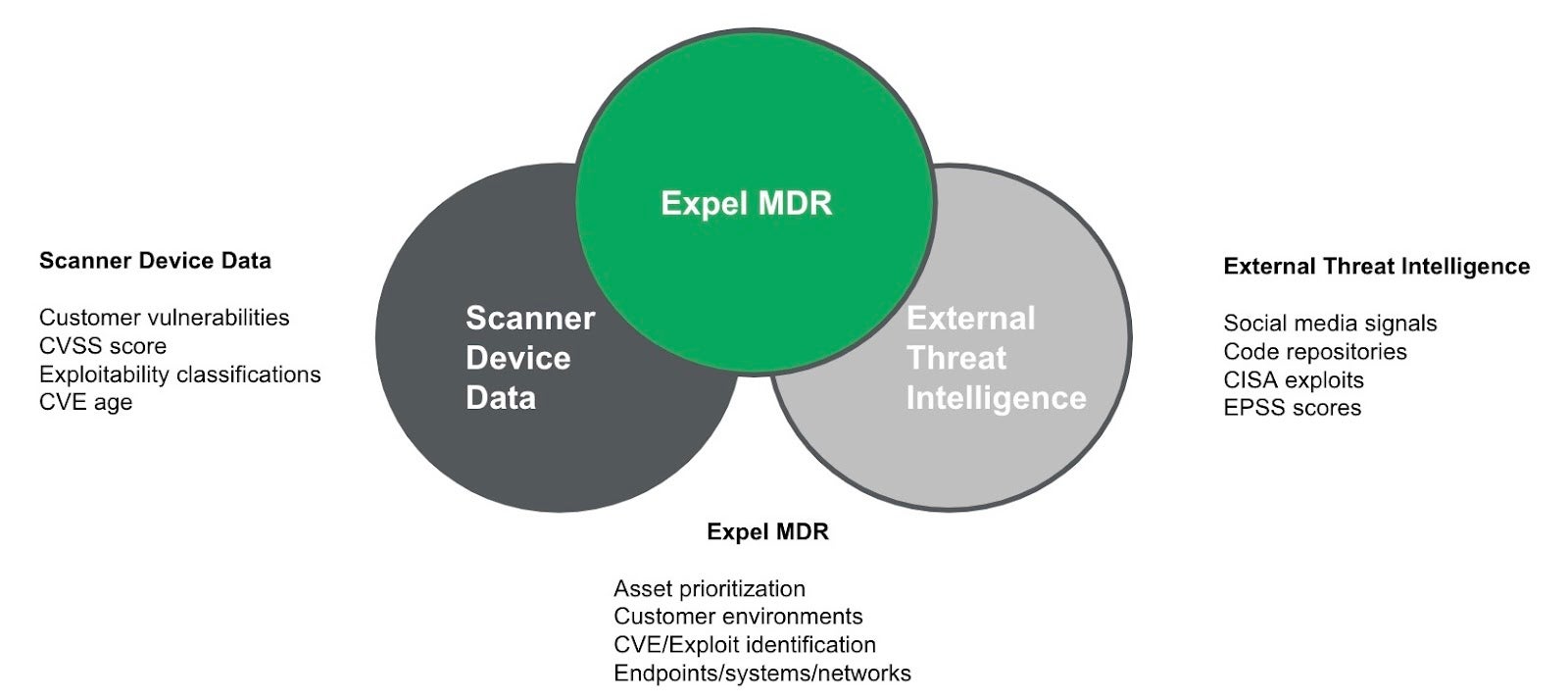
Expel Vulnerability Prioritization employs a risk-based prioritization model that starts with ingesting endpoint vulnerability scanner data from Tenable.io Vulnerability Management and Rapid7’s InsightVM. We then match that data to external threat intelligence, and what our SOC is seeing across our MDR customers’ environments to get more context and narrow down the list of vulnerabilities most likely to impact your organization.
Like all Expel products, we use a software-first approach, ingesting information from your existing security devices and technology, and applying our own automations (or bots) to investigate and triage. Then our Vulnerability Analysts further investigate and analyze to qualify what vulnerabilities are urgent, and what’s recommended for remediation during the next patching cycle. Our team then notifies you about urgent and recommended vulnerabilities with remediation guidance.
Here’s another look at our risk-based prioritization model:
Expel Vulnerability Prioritization aims to accelerate your prioritization and remediation process so you can improve visibility and decision-making, spend less time triaging and investigating vulnerabilities, and more time patching. It can also strengthen your detection and response processes by shutting down attack vectors that could be exploited.
Expel Vulnerability Prioritization is another solution powered by our security operations platform, Expel Workbench™, complementing our market-leading MDR, phishing, and threat hunting offerings. We enable you to take a proactive approach to investigation and remediation, and eliminate critical risks early in the cybersecurity kill chain.
If you’re attending the RSA Conference in San Francisco next week, feel free to stop by for a demo at booth #954 in the South Hall. If you’re not going to RSA, feel free to contact us for more details.