EXPEL MANAGED RESPONSE & AUTO REMEDIATION
We stop threats before they stop you.
When threats hit, every second counts. Expel stops attackers before they can cause damage, disrupt business, or interrupt your sleep cycles.
STOP LIVING ON HIGH ALERT
We respond so you don’t have to.
Imagine sleeping through the night knowing if an attacker tries to encrypt your files or steal your data, they'll be stopped by our team—no midnight phone calls required.
HOW IT WORKS
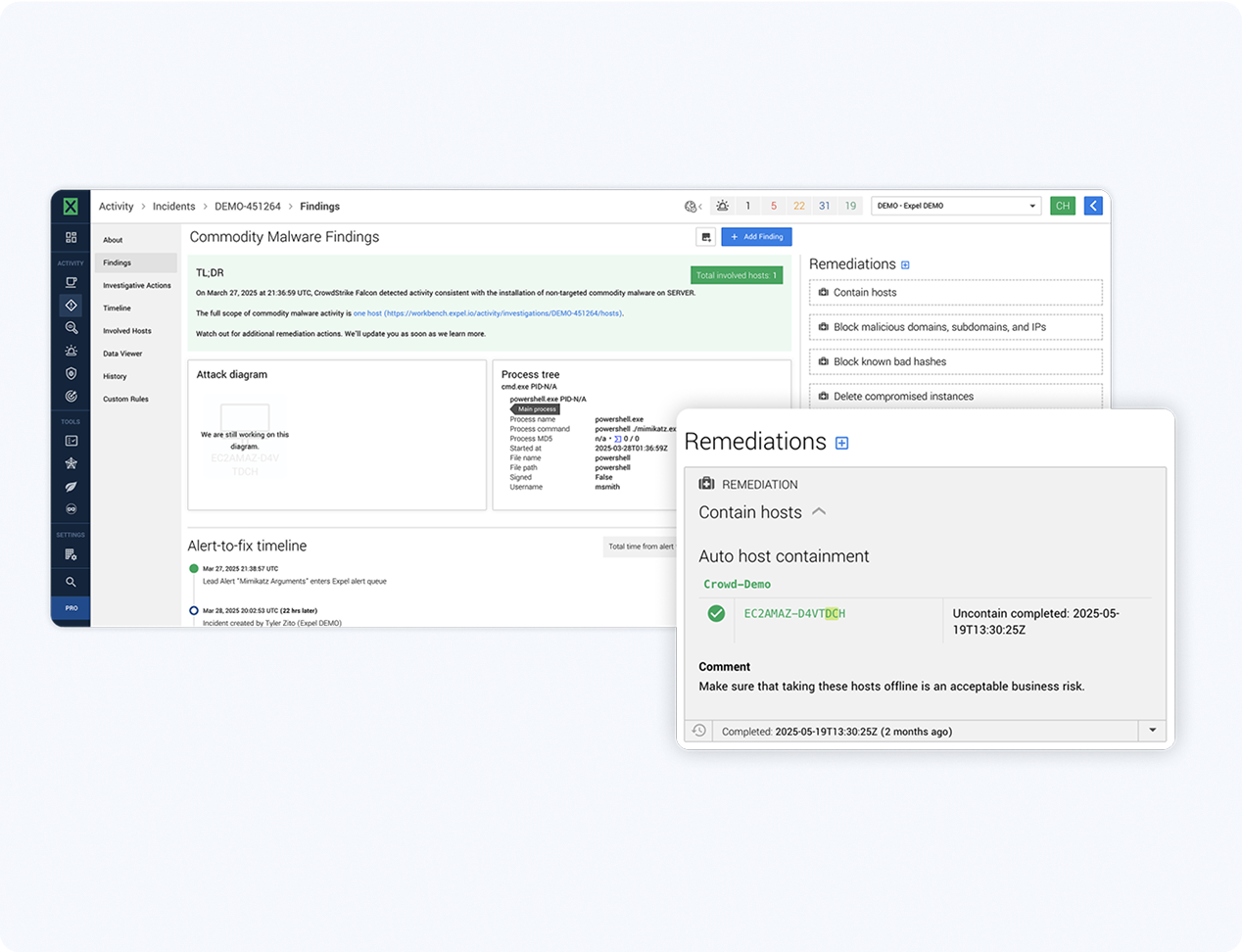
What’s in Expel’s managed response?
Once our SOC validates a threat, our analysts take auto remediation actions to respond on your behalf. Security disasters like malware, infected machines, and compromised credentials are fixed in a flash, without your team lifting a finger.
THE SCOREBOARD
Talk is cheap. Here are the receipts.
It all comes down to speed and accuracy. And when it comes to auto remediation, the data speaks for itself.
14
minute MTTR
on critical/high incidents with auto-remediation
87%
MTTR reduction
with auto-remediation
8
attack surfaces
covered by Expel auto remediations
18
integrated tools
with response workflows
HOW WE’RE DIFFERENT
Expel auto remediation
vs. other MSSPs and MDRs
Most MDRs will give you homework, like still making you push the response button. At Expel, we act for you. That way, your team can get work done, instead of chasing all the fires.
Expel MDR
Other MSSPs & MDRs
Tailored response
Flexible control
Take it or leave it
Endpoint
Network
Identity & Users
Cloud
SaaS apps
AUTOMATION THAT WORKS
Response so fast, you’ll think we’re cheating
When it comes to the bad guys, we’ve got your back. With 24×7 response, you have time to plan your next move (even if that means waiting until Monday morning).

Having Expel allowed us to beat our mean time to remediate (MTTR) by more than 60%. And more importantly, since Expel has eyes on these alerts, our team had the flexibility to get out of the alert queue and focus on maturing our security capabilities.

Expel allows us to target and resolve issues before they can take out our IT infrastructure, with automated tools and expert human advisors that point us in the right direction, regardless of the situation.
THE LINEUP
All the auto remediations that put the bad guys in a bind
We present to you our library of auto remediations. This is how we kick out attackers and lock the door behind them.
Kill process
Terminate malicious processes across endpoints before they make trouble

Contain host
Isolate hosts from your network and sever all communication with other business applications

Block bad hash
Block potentially malicious processes and files based on their hash values

Delete malicious file
Permanently delete confirmed malicious threat artifacts—no trace left behind

Delete registry key
Remove malicious persistence entries from Windows Registry

Disable user account
Prevent compromised identities from authenticating, with lockdown tighter than maximum security

Disable access key
Deactivate specific cloud access keys suspected of compromise

Reset credentials
Invalidate user passwords and terminates active sessions

Remove malicious email
Hunt down and purge confirmed malicious emails from inboxes
YOUR RULES, OUR EXECUTION
We’ll respond, but you’re calling the shots.
Our response is tailored to your environment. You decide what, when, and how actions get taken based on your tech stack, risk tolerance, policies, processes, and comfort level.