MDR for endpoint security
Fast and deep endpoint threat detection
Go beyond standard alerts. Our 24x7 experts enhance your EDR/XDR to find and stop the hidden attacker activity that others miss.
Our difference
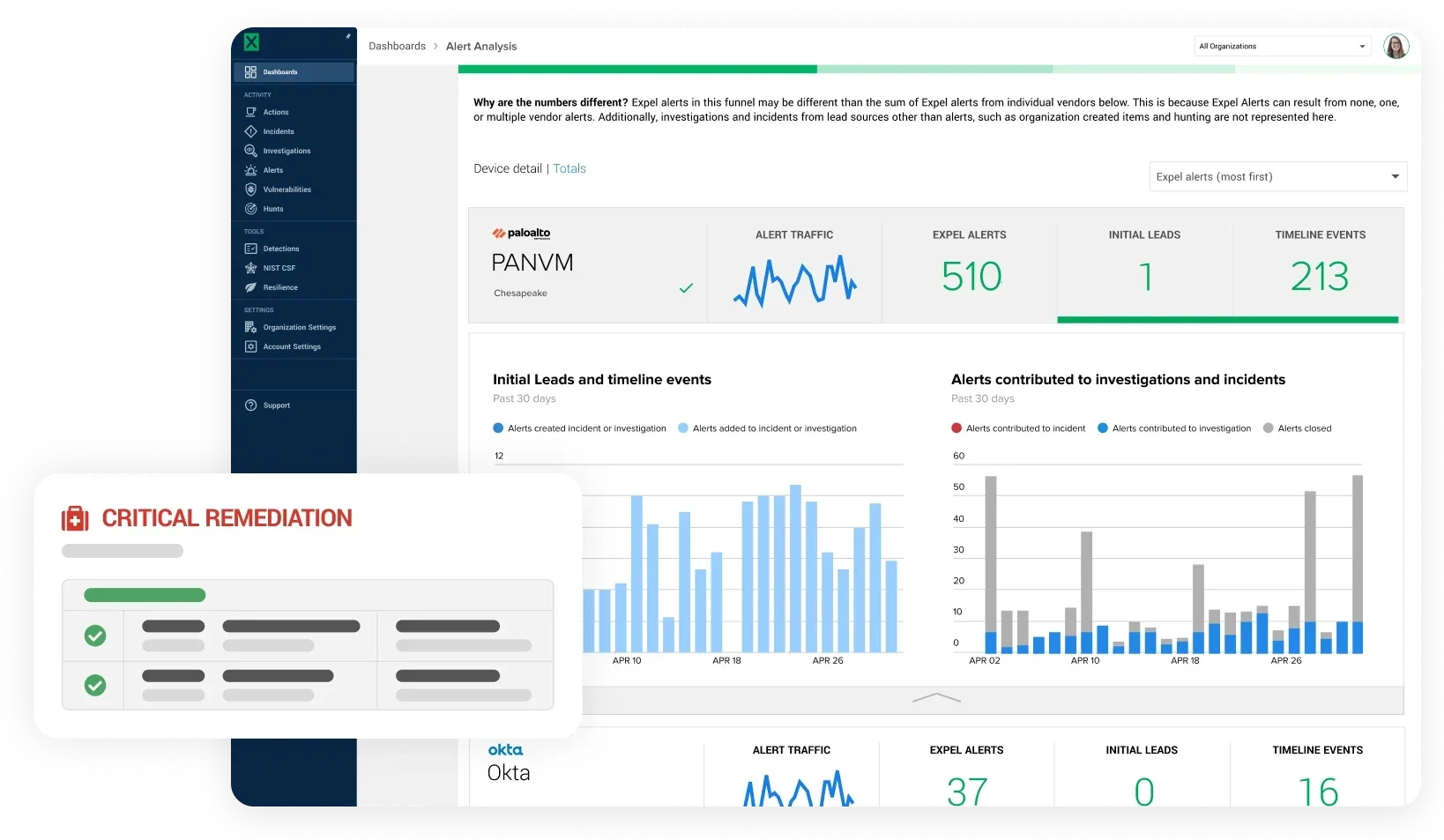
Find incidents in a sea of alerts
Make your endpoint threat detection even smarter. Expel helps you see what’s actually happening on your network and devices.
Expel MDR
Our approach to
endpoint security
Expel transforms a flood of endpoint alerts into clear, simple findings. Our endpoint threat detection strategy involves applying custom Expel-written detections to find even the most complex threats. From there, we connect that information with what’s happening across all your other security tools – in your cloud, identity, and SaaS apps, and more. Plus, if we spot suspicious activity, Expel can automatically kill processes or contain hosts to prevent damage.
MDR Benefits
Why Expel?
Expect more than just better endpoint threat detection. We help your entire security program grow stronger, starting with your existing endpoint tools.
A smarter security stack
Unlock the full potential of your existing security tools with layered, high-fidelity detections built to deliver the outcomes you expect.
Stop attacks at the source
We detect the specific tactics and tools used to introduce malicious executables, to stop threats before they can detonate.
Continuously improve your detections
Your detection coverage is continually refined based on real-world threat experience to keep you ahead of attackers.
Connect the dots between attack surfaces
Your team gets the full story, using endpoint data to enrich other alerts, like seeing the process behind a suspicious network connection.

Get answers, not just alerts
You receive comprehensive findings with clear instructions on what to do next, so your team can move faster with all the context they need.
Customer love

We were looking for a trusted partner. We weren’t viewing this search as simply getting a point solution, but rather bringing in a company that could grow alongside us, and help us to improve and learn. We wanted to transition from making fear-based security decisions to making risk-based ones.
Threat research
Expel Quarterly Threat Report, Q1 2025: Endpoint threats
Learn what endpoint threats are common (and how to spot them).