Videos · Cole Finch · TAGS: SIEM
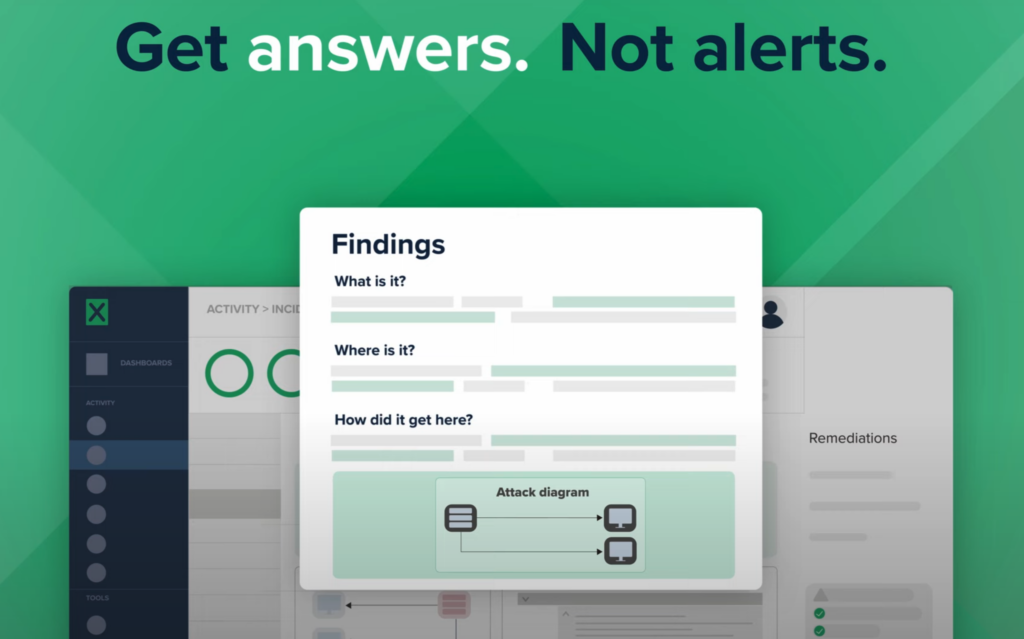
With Expel Managed Detection and Response (MDR), you can transform alerts into answers for decision support with your existing SIEM investment.
Reduce alert fatigue and increase the value of your SIEM
So you’ve invested in security information and event management (SIEM) to access alerts in a unified source. SIEMs can be a powerful asset for SecOps teams, but they alert on everything. And that creates alert fatigue.
What can you do to transform SIEM alerts into answers for decision support? You could build custom rules, but they need to be continuously tuned, adding even more work. Or you could augment your SIEM with managed detection and response (MDR) to cut through the noise and make sense of your data.
If you go down the MDR path, you have a decision to make. You could abandon your SIEM and choose an MDR provider that requires their own. Or you could select an MDR that integrates with your current SIEM to maximize your existing investment.
At Expel, we are all about using the tech you already have
From endpoint to network to cloud to help you get answers, not alerts.
Within days—not months—we integrate with your existing SIEM to reduce false positives and enrich alerts with context, so you’ll get all the value of your SIEM alerts without all the noise and additional rules to tune [out].
When the inevitable incident arises. Our average alert-to-fix is 22 minutes for critical alerts, so you can feel confident we’ll resolve it fast. And if you don’t have a SIEM, no problem. We work with the tech you have!
Reduce alert fatigue while increasing the value of your SIEM with Expel—security that makes sense™.