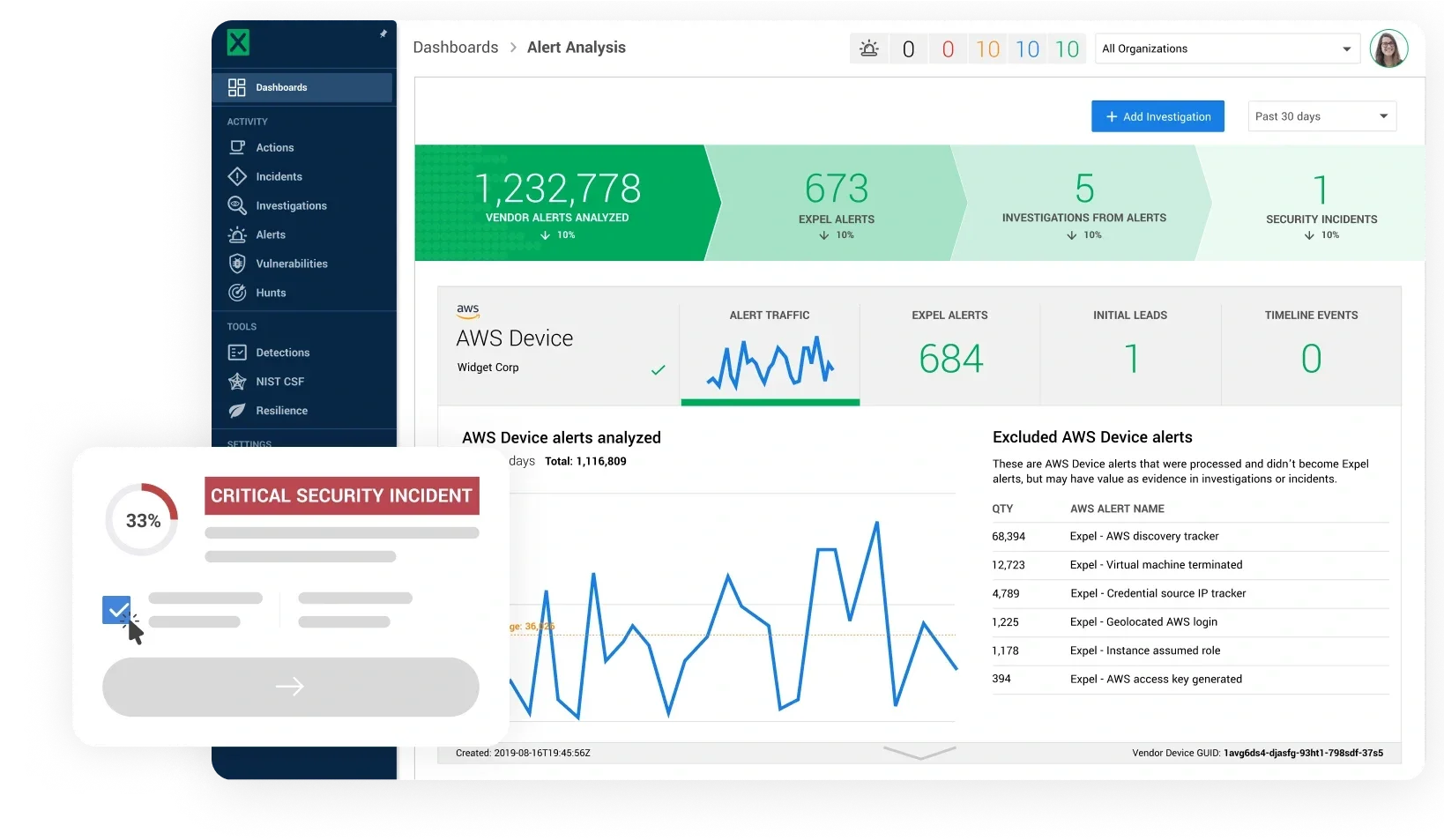
Managed Services
MITRE-aligned transparent threat detection
Gain comprehensive protection across your entire tech ecosystem, including endpoints, cloud, Kubernetes, SaaS, SIEM, and networks. Our expert security team triages and fully remediates threats for you around the clock.
Receive detailed reports with actionable recommendations to strengthen your security posture.
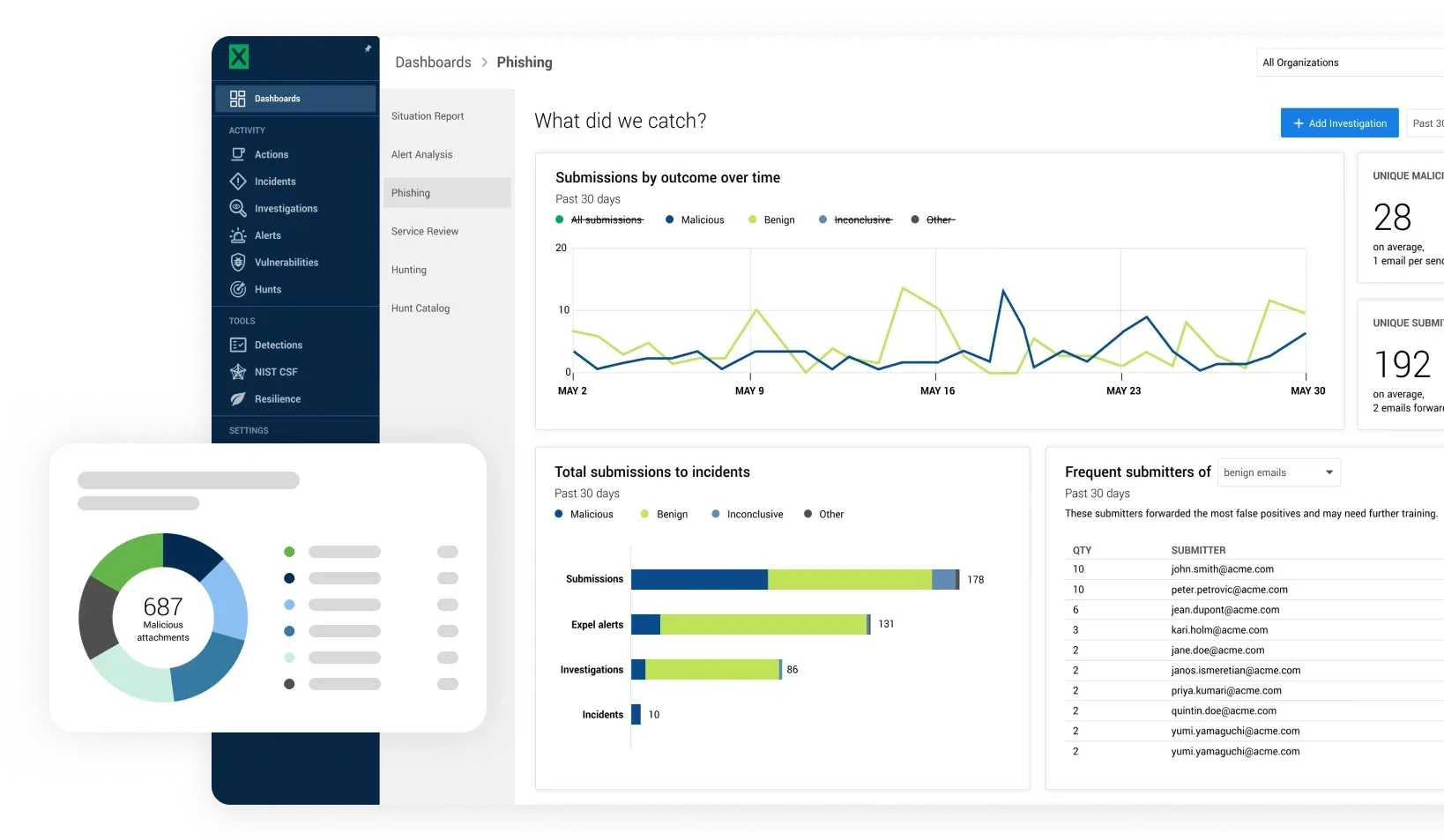
Seamlessly connect your email provider to Expel Workbench™ for efficient one-click email threat flagging. Suspicious emails are automatically forwarded to our specialized team who investigate attachments, URLs, sender IP addresses, and other threat indicators.
Get comprehensive reports with strategic recommendations to reduce your organization’s email security risk.
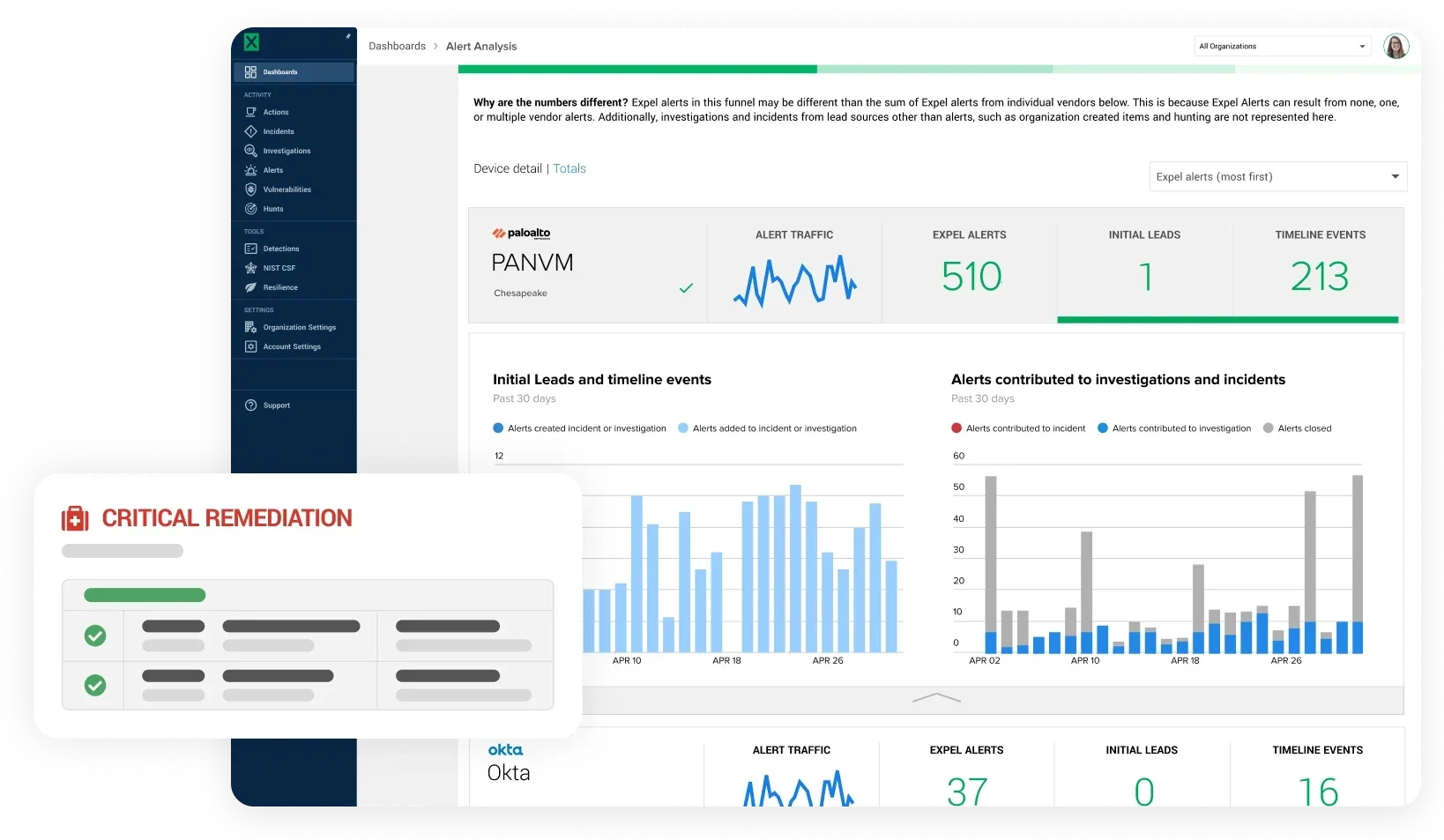
Uncover hidden threats lurking in your environment that conventional scanners simply can\’t detect. Our team conducts methodical monthly hunts based on known attack behaviors, emerging patterns, and other unusual activity.
Get post-hunt detailed reports highlighting prioritized risks, security gaps, notable findings, and recommended actions.
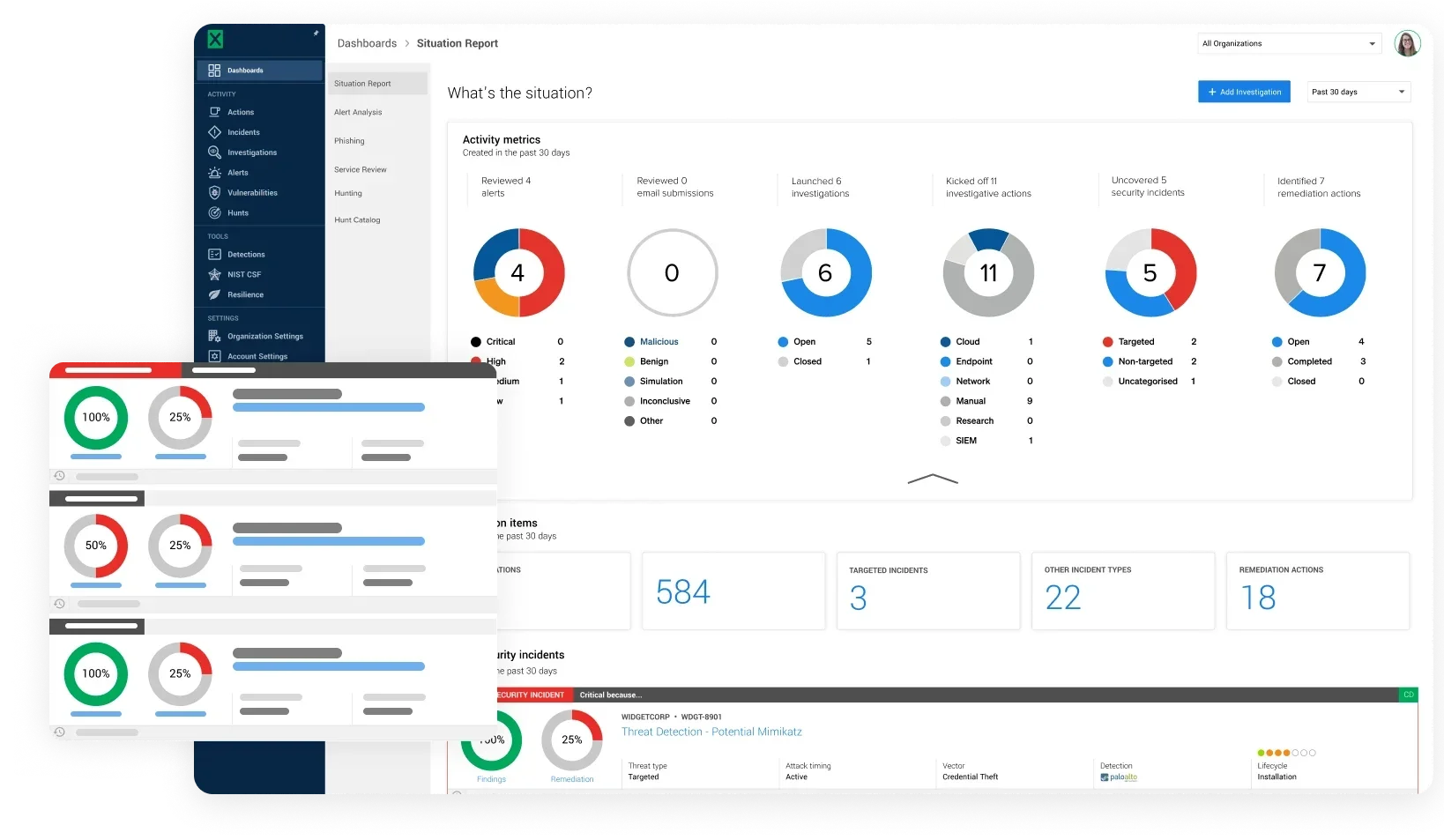
Let our security experts analyze your scanner data and intelligently prioritize vulnerabilities based on affected assets and known attack vectors. Compatible with leading platforms including Qualys, Rapid7, and Tenable.
Critical vulnerabilities can be automatically remediated, while you receive clear remediation guidance with practical next steps.




Integrations
Your entire environment: covered
From cloud to ground, detect risks across your tech stack, including endpoints, cloud, Kubernetes, SaaS, SIEM, and networks.







